After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

Unless you have unlimited cellular data, you probably connect your iPhone to every Wi-Fi network you come across. It could be a local coffee shop, public library, or just a friend's place. Wherever it is, you'll need to ask for the access point's password if it's a secured network, and that can be a hassle if the place is busy or the owner forgets the credentials. Luckily, Apple has a solution for this problem.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

In this clip, learn how to access and use the JAM! app for your iPhone or iPad to update your website from afar. Keep your visitors up to date on the go with this handy application. This tutorial will walk you through the steps you need for connecting JAM! to your computer and getting started.

All of us remember "Twinkle Twinkle Little Star" for a reason. As a fond part of our childhood, it was a song that taught us about the wonders of the sky while also connecting us with our parents, who learned the song from their parents before them. Continue the tradition by teaching your kids how to sing "Twinkle Twinkle Little Star."

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

Here are instructions to make origami bat. You will need 383 black, 47 brown, 3 white and 2 red triangles. In the video below you'll see a map.

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

For the most part, transferring files from your computer to your Nexus 7 (and vice versa) is a simple process. Just hook up your tablet to your computer with the USB cable and transfer. However, most of the time you'll need additional software on your computer to do this, and then, of course, you need the USB cable.

Whether you're in an airport, restaurant or waiting room, the insidious grip of televisions on human life is omnipresent. Sometimes it's nice to talk to other human beings while looking at them directly—actually hearing what they have to say.

A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

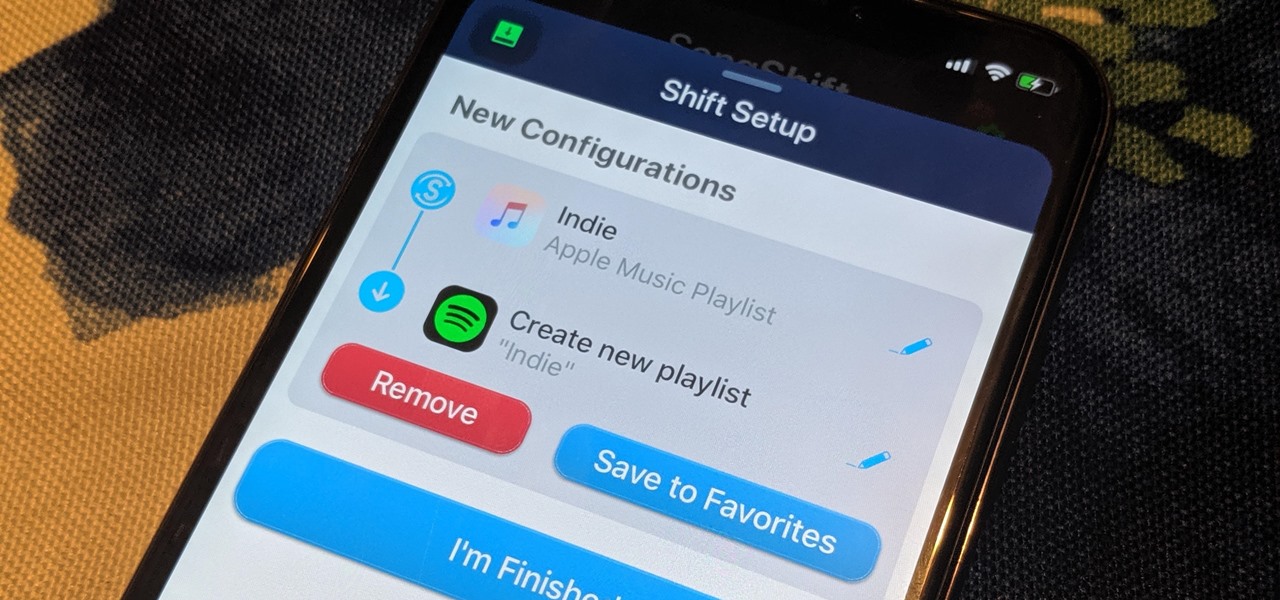
Switching from one popular music streaming service to another shouldn't have to be a hassle, but it is if you want to transfer all your favorite music over. No popular service offers a built-in feature to export or import playlists, so if you want to move your favorite Apple Music playlists over to Spotify, you'll have to use a third-party service.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. OTW made a brilliant article, but only touched on the surface of the possibilities. I hope this article will both show you many the possibilities and also allow you to start causing havoc, but I'm planning on making this ...

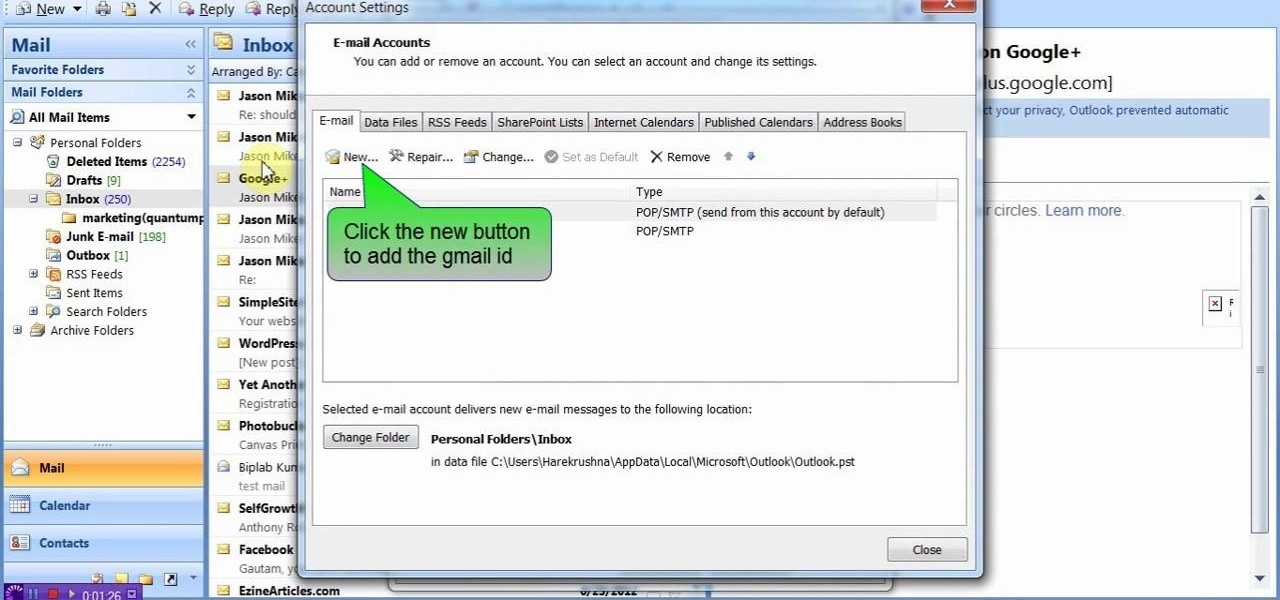
This video will describe you how to take your Gmail backup on your PC or MS Outlook express. By connecting Gmail with MS outlook a copy of each email from Gmail account will be received in MS outlook on your PC. So from now you could access your Gmail offline. Watch the video and follow all the steps carefully.

There are very, very few things better than a solid Hobbit songI mean, I was almost brought to tears when Pippin busted out this one in The Lord of the Rings: Return of the King.

In this video, we learn how to improve the quality of movement in a tango dance. Focus on the connection with the other person, the music, and connecting with the body as you are dancing with the other person. Be very strong and heavy into the ground as you are dancing and very light as you are moving around. Do a strong walk and make sure you are in touch with the rhythm but also make sure your body moves lightly around the dance floor, like it's effortless. Keep your body in contact with th...

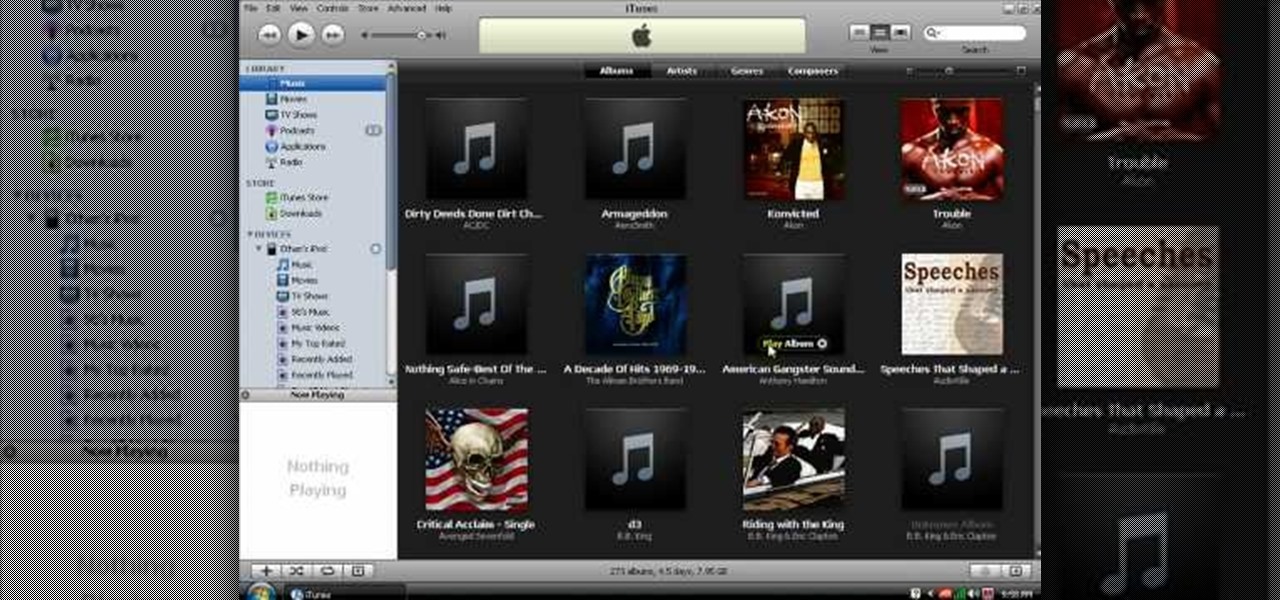
In this video tutorial, viewers learn how to transfer music from an iPod to the iTunes library. Begin by connecting the device to the computer. Then click on the Start menu and open Control Panel. Now click on the device. Click on Tools and select Folder Options. Then click on the View tab and check "Show hidden files and folders". Click OK. Now open the iPod_Control folder and open the Music folder. Finish by simply opening all the folders and importing the music files into iTunes. This vide...

In this video, we learn how to draw Mickey Mouse on a dry-erase board. Start off by drawing a circle on the left hand side of the board, then draw a half circle with another circle connecting to that on the right hand side of the board. Now, connect another half a circle around the sides, to help shape the face. Next, make an "m" shape on the top of the face going down to the sideburns and fill this in. Color in the ears as well, then make a rounded v-shape at the bottom of the face to make t...

luvk9ines gives a tutorial on how to tie a two-handed suture tie for veterinary purposes. To begin the two-hand suture tie, knot the two ties together and continue to knot but you will alternate the direction of each knot. One knot/tie will be interlinked from the top and the next knot will be interlinked from the bottom. In other words, pretend that you are making a knot on a tie and each time you make the knot, the tie on the left will be going in the bottom direction. The next knot, the ti...

In this video tutorial, viewers learn how to sync contacts between a Mac and Windows mobile device. Users will need to download and install the program, Sync Mate 2. Begin by opening the program and connecting the device to the computer. Under Synchronization in Plug ins, check the Contacts box. Then select the Synchronization direction, Surname and name order and select which contact groups to sync. Then click on Delete all contacts and select to delete the contacts on the computer or mobile...

This is a Sports category video tutorial where you will learn how to use your left arm properly in a golf swing. The video tutorial is from Golf Link and is presented by Jim Ballard. Keep the left elbow always pointed down to the ground. The club face is controlled by the left elbow. When the left elbow rotates, it also changes your radius and the arch. This can be achieved by connecting the left arm to the shoulder, feeling that you are holding a handkerchief under the left shoulder. Always...

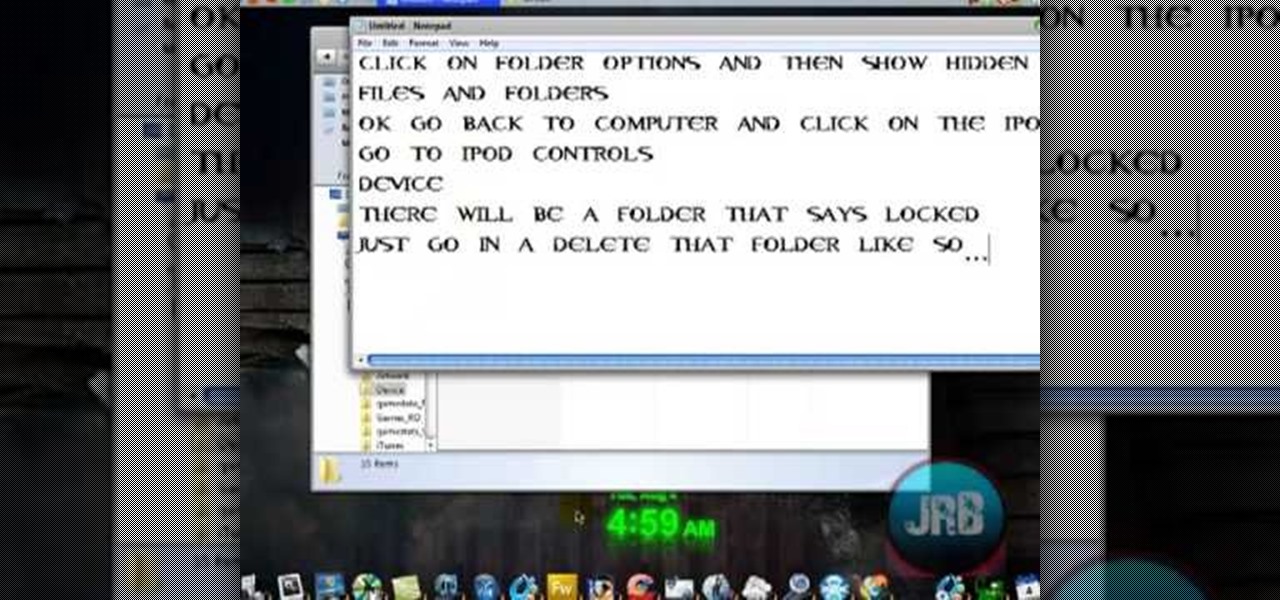
In this video tutorial, viewers learn how to unlock a locked iPod. Begin by connecting the iPod to your computer. It should fix itself automatically. If it doesn't press the Start button and select Control Panel. Click on Appearance and Personalization. Under Folder Options, select Show hidden files and folders. Check the box that says "Show hidden files and folders". Click Apply and then OK. Go to My Computer and open the iPod device. Select the Controls folder and click on Device. Delete th...

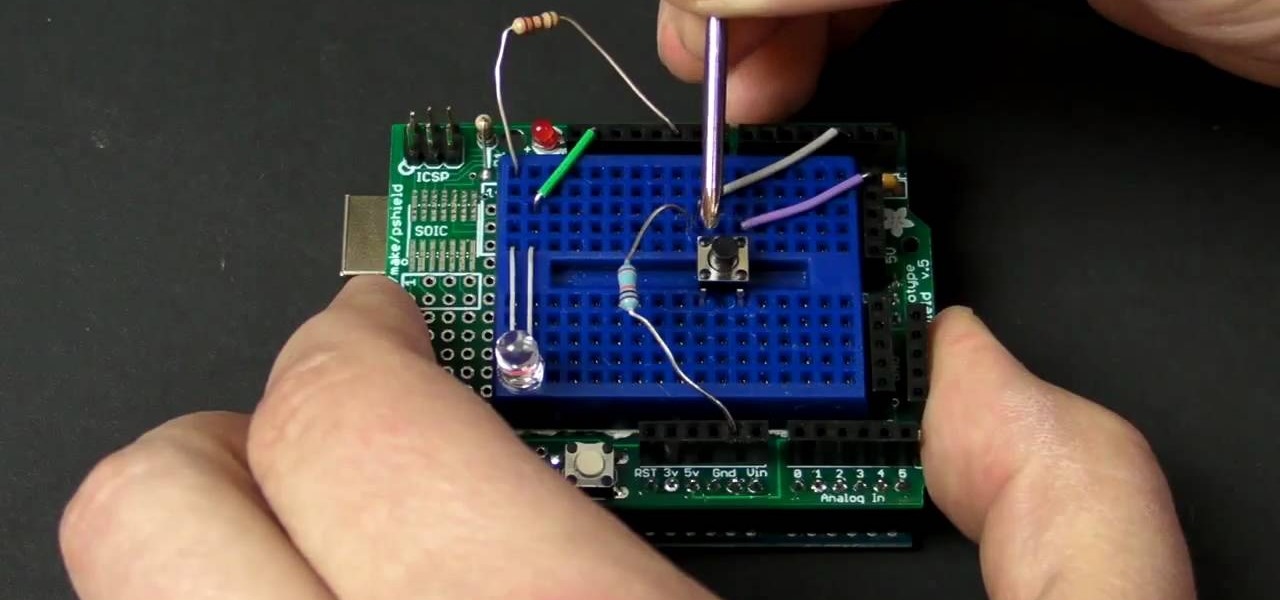
See how to a a button with Arduino with MAKE Magazine! This is a video tutorial on a favorite little micro-controller, the Arduino. This is a really informal how-to, and is meant to show you just how fast and easy it is to work with the Arduino.

An alternative to origami, here’s a very easy paper design strp icosahedron by Heinz Strobl. Here's a very easy icosahedron to origami. For the strips, use an A4 format paper and cut it in the middle lengthwise. Do so to get 8 strips and then fold strips of 6 squares. It requires 20 strips of 6 squares for the triangles and 30 strips to knot them together (strips of 5 squares also work). Only the knotting strips will stand out, but it is still better to use two colors. You can make a bigger m...

MrfixitRick demonstrates the Shake Flashlight Shaker, as it generates electric power out of faucet water pressure. A Tesla CD Turbine is used to convert the kinetic energy of water into rotation. Then, a connecting rod and magnets charges the built-in battery of the shake flashlight.

You're out and about, and nothing on your iPhone will load. A glance at the settings shows a saved Wi-Fi network with full bars that your iPhone had connected to automatically, but you're not getting any internet. If you've experienced this, you're not alone, and there's something you can do about it. You'll even increase privacy and security on your iPhone in the process.

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

In 2018, notches are the hot trend with smartphones. Essential was first to release a phone with a notch in mid-2017, but Apple kicked off the fad in earnest with the iPhone X. Unfortunately, unlike the iPhone X, every Android phone with a notch has a noticeable bottom chin. Let's take a deep dive to find out why.

Using just the airbrush in MS Paint you can make a cartoon dog on your computer. Start off by making a circular shape using the airbrush, keep at it until it is dark and prominent and then color in the lower half of the circle, this is the nose. Now start making a line from the bottom of this circle downwards, slowly start curving the line at a ninety degrees angle. At the end of this line attach a semicircle to it so that it is perpendicular to the line. Above this line also make three small...

Dragons are very popular storybook characters, especially with the release of "How to Train your Dragon" in movie theatres. Check out this tutorial and learn how to draw your very own fire-breathing buddy!

The Department of Biological Sciences at the University of Alberta brings you this video tutorial specifically relevant to your student laboratory courses, specifically microbiology. If you're a student at any school of biology, this information will be helpful for learning how to mix gradients with a gradient mixer in the lab.

Fireworks are the best part about the Fourth of July and other celebrations, but they can easily cause accidental injuries. It's both safer and more fun to set them off remotely, so we'll hack some standard fireworks with nichrome wire, a relay, and an Arduino to ignite remotely over Wi-Fi using any smartphone or computer.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.