Eye contact is key in conversations, job interviews, and honesty, and it can help you access others' thoughts and spot heavy drinkers. Locking eyes with someone can even help you fall in love, whether you know them or not.

An attacker can create three, five, or even ten new Netcat connections to a compromised MacBook with one command. Performing complex post-exploitation attacks might otherwise be difficult from a single shell without this essential trick.
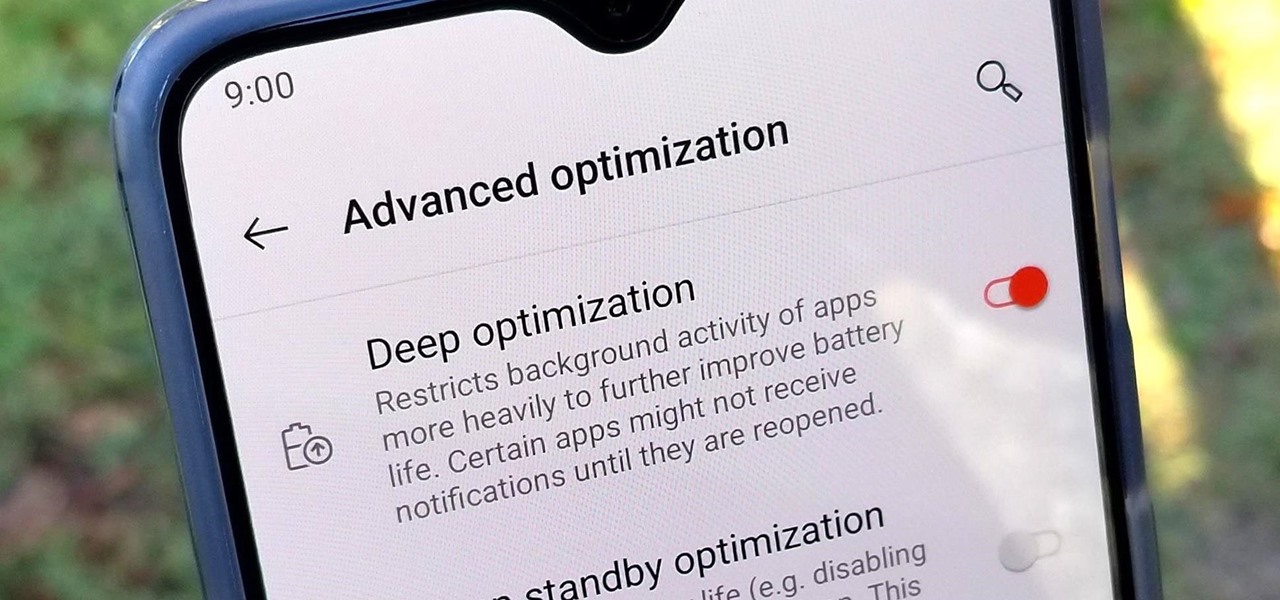
OnePlus is known for pushing the boundaries of what we thought was possible for a mid-range price. One of the best things about OnePlus phones is that their battery life is fantastic in general, but to achieve this, Oxygen OS will disable or delay notifications by default once your phone goes into deep sleep mode. You will not be notified until you wake the phone up — this could be an issue for some.

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

This tutorial is for those who've purchased an account with Private Internet Access to hide your VPN and would like to set it up in Kali. Please note, you can chose to run your PIA service from your Windows computer without configuring it in linux as long as you'll be using a NAT connection. Using a NAT connection will allow your Windows machine and Kali Virtual Machine to use the same IP address, hence if your IP is hidden on one, it will be hidden on the other.

Thanks to the popularity of casual gaming on smartphones, handheld gaming consoles like Sony's PlayStation Vita have been on the decline. But if you own a new PlayStation 4, the Vita is a nice thing to have, since you can easily connect it to your PS4 for Remote Play.

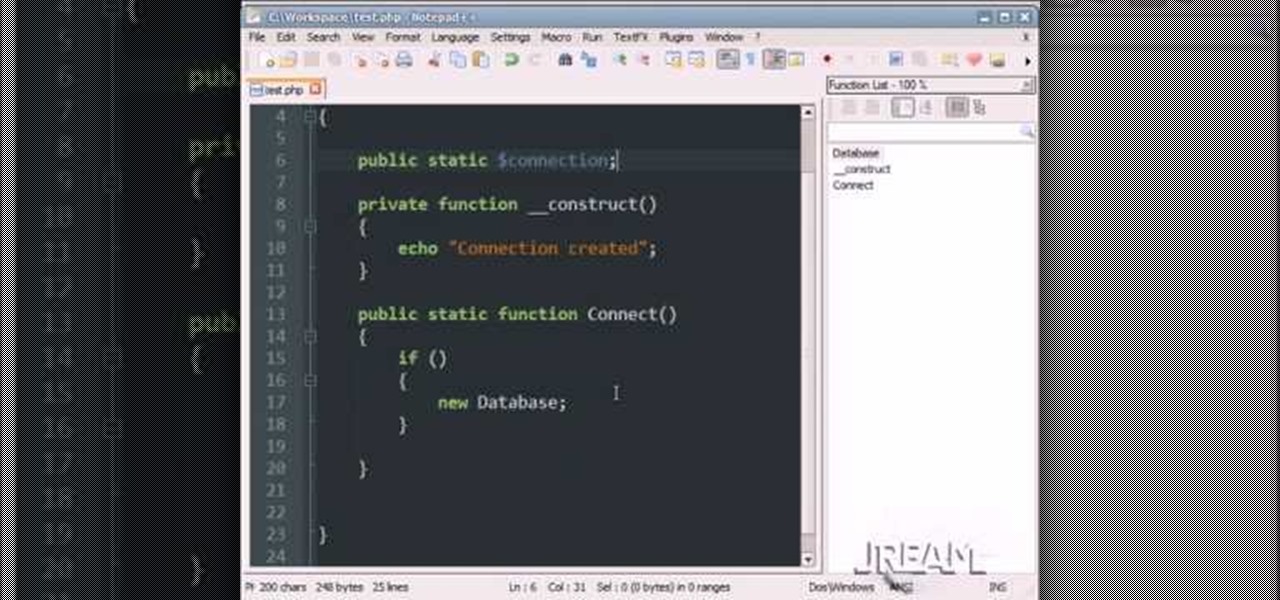
This PHP newbie video with teach you what a Singleton Pattern is and how to use it in your PHP programming. PHP OOP Singleton is great for a database connection when you only want one consistent connection in your application. So, to prevent wasting space accidentally by calling it twice in different areas, this is good way to protect it. Singleton is very popular and used often in Database Connections.

Here is a detailed video on how to setup and use WinSCP, which works with 1.1.3 and 1.1.4 iPod Touch and iPhones. This will fix all errors "connection timeout" and "connection refused".

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

When flashing files through TWRP, ADB, or Fastboot, there's a slight chance for things to go wrong. Whether it's user error related or something else entirely, it's always good to have a backup plan. In most cases, you'll be dealing with a semi-brick or soft-brick, which can usually be solved by wiping the data of the device using TWRP. However, it can be more severe than that in some cases.

The new iPhone XS and XS Max have more issues than just their hefty price tags. Customers have only had the phones for a handful of days, but some are already complaining of cellular and Wi-Fi connectivity issues on both models. If your experience is the same on your XS or XS Max, there are steps you can take to get your iPhone reliably back online.

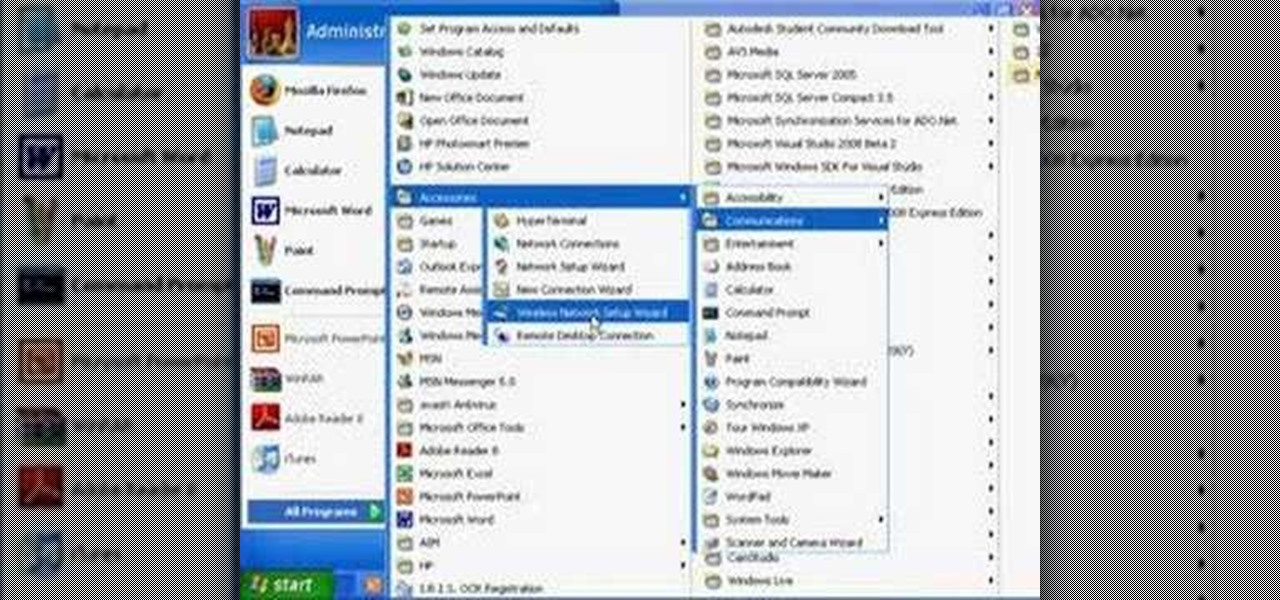
Wartex8 demonstrates how to use remote desktop in Windows XP. Remote Desktop is a useful utility that you can use to control another computer and its applications.The necessary steps that are adopted to activate remote desktop are:1) Right click on my computer icon (either the icon on the desktop or the one on the start menu list) and select properties, and a new dialog box called system properties will pop up on the window.2) In the System Properties, select the computer name tab and write d...

This video will show you in eight steps how you can get and use wifi and dsi to use with your Nintendo. This is a helpful tool because it can be a little confusing to get started using different technologies without clear instructions.

Welcome back everyone! It's been awhile hasn't it? Sorry for being so quiet, but my CCNA courses have really picked up recently. In the last article we covered how to import modules and how we can use them. In this article, we'll actually be covering a module that is essential to the hacking aspect of Python, sockets.

You're at your friend's house. All you've heard about all day is his new laptop. He's got a brand new top-specced MacBook Pro, and he won't stop going on about it. It particularly annoys you as all you've got is a 4 year old cheap laptop, even if it is running Linux.

I may not be a parent just yet, but I've dealt with enough worrisome mothers to know that keeping a watchful eye over your child is of the top-most importance. Since most people cannot afford to stay right by their child's side 24/7, developers are always looking for ways to make the pain of stepping away a little less stressful for parents.

Anything from work or a missed flight to a worldwide pandemic (COVID-19, anyone?) can make it difficult or nearly impossible to see your loved ones. You can make phone calls or send iMessage, text, or email messages, but nothing compares to seeing family and friends right in front of you. That's where FaceTime comes in.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

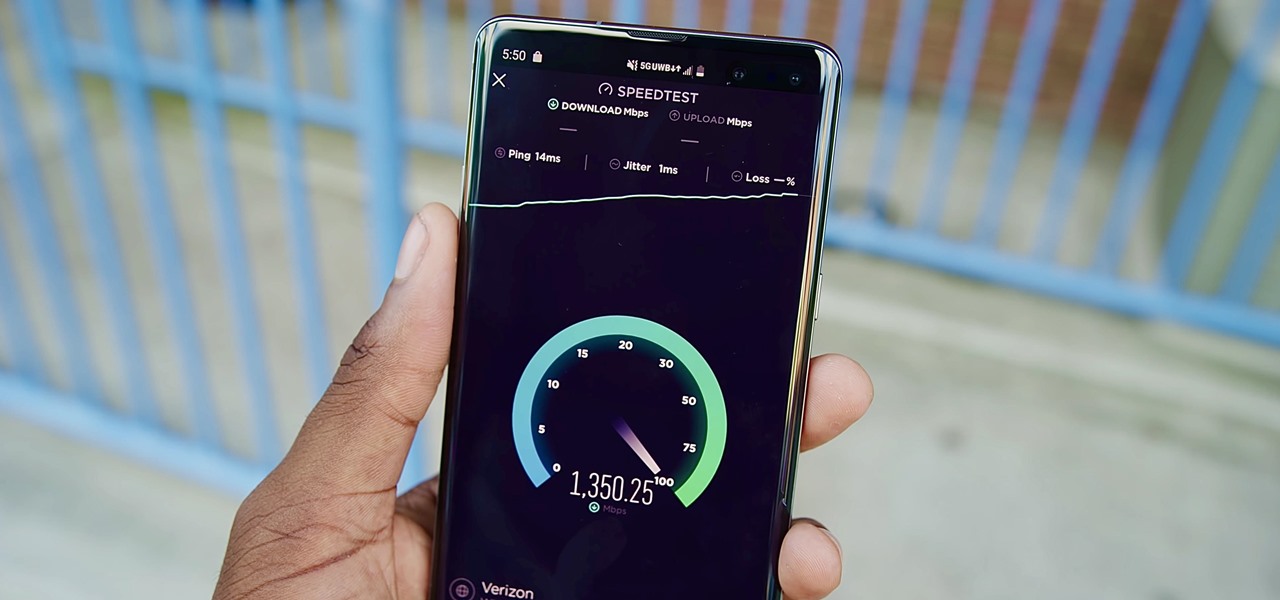
Not all 5G is equal. Even if you dropped the cash on a true 5G phone and you see it's connected to 5G in the status bar, that doesn't mean you're surfing the web, streaming Spotify, and binging Netflix faster than your friends with LTE phones.

The Google Cast feature that serves as the primary interface for the Chromecast and comes bundled with Android TV devices like the Nexus Player is a marvel of modern technology. But as these things go, troubleshooting issues can be difficult with something so groundbreaking, especially when you consider that there are two parts to the equation—the casting device (your phone, tablet, or computer) and the receiver.

I have Verizon, America's largest 4G LTE network, as my cell service provider, but there are times when I find myself with a pretty shitty signal, rendering my upload and download speeds substantially slower than usual.

Flappy Bird is the extremely difficult, overly frustrating, strangely similar, yet highly addictive smartphone game from .GEARS STUDIOS that has catapulted its way to the top of the charts on both Google Play and the iOS App Store—seemingly out of nowhere.

There are several ways to get around location restrictions on subscription sites like Netflix and Hulu using apps, extensions and proxies, but they tend to only work on laptops and computers. Users who want to access content from mobile devices and gaming consoles are usually out of luck.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

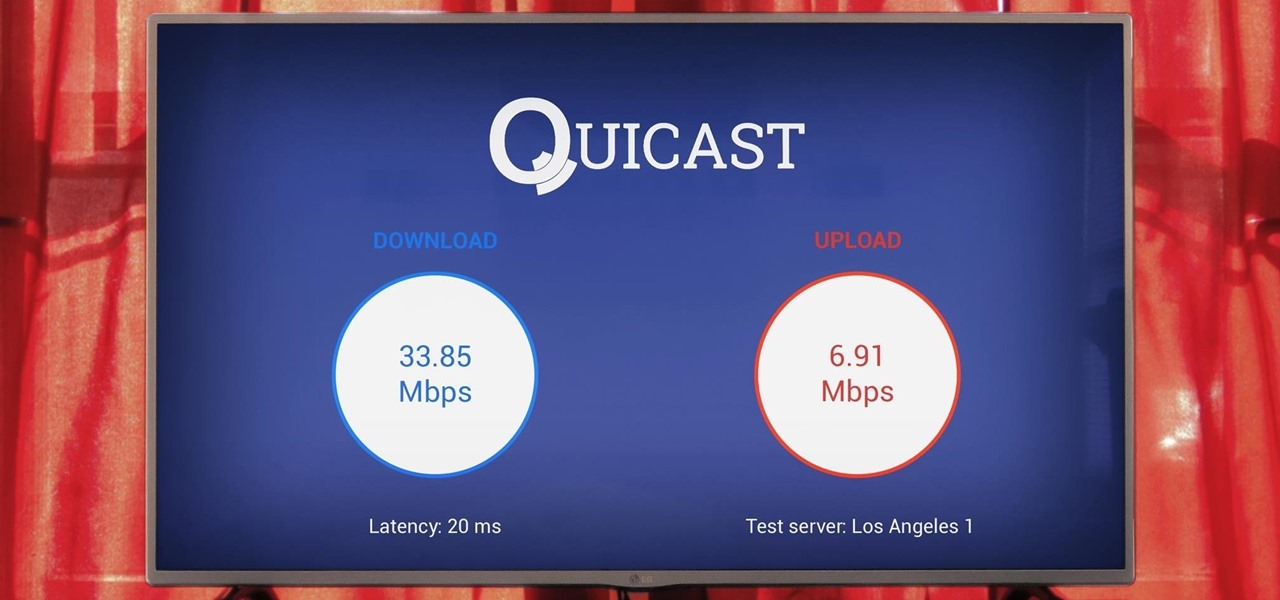
Did you know that you can improve the Wi-Fi in your home without the stress of changing providers or using a costly professional? The answer lies in a simple app you can use yourself at home, and right now, the NetSpot Home Wi-Fi Analyzer With Lifetime Upgrades is on sale for just $39.99. That's 41% off the regular price of $68.

While the portability of mobile phones makes gaming convenient, it isn't a perfect playing experience. With touch controls, small screens, and limited specs, smartphones lack the comfortability of dedicated gaming devices. But with a few tips, you can enjoy games as if you were playing on the Nintendo Switch.

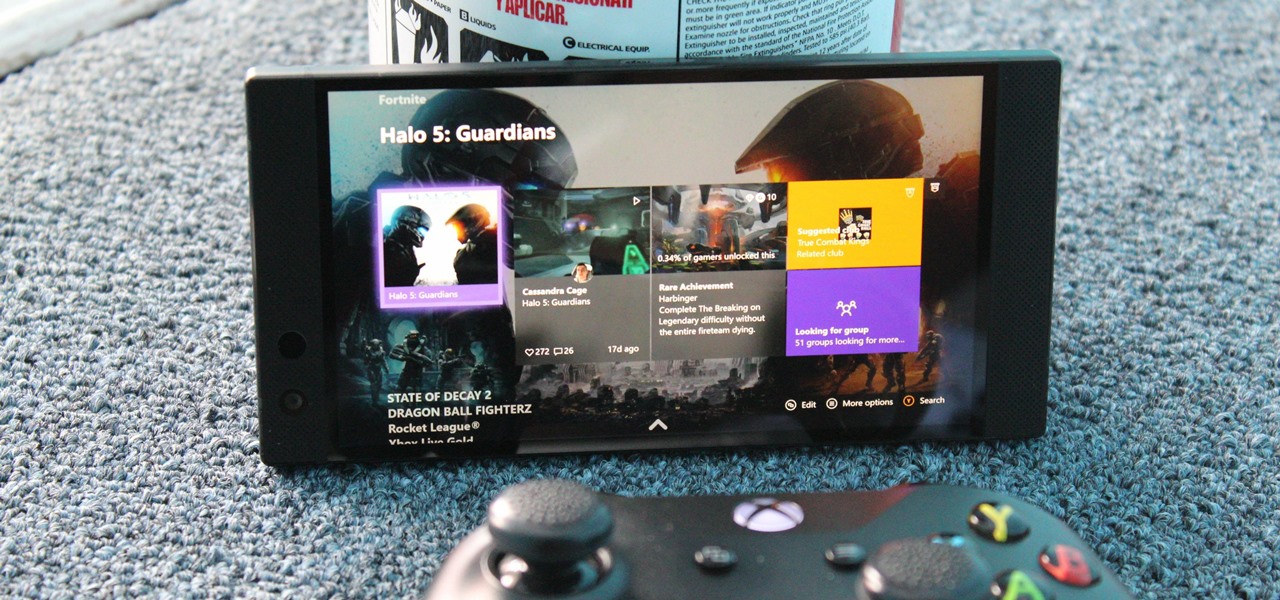
Game streaming has never been better. Not only can you watch your favorite Twitch streamer play, but with the new tools being added to YouTube, you can even play along with them. And now, with a solid internet connection, you can stream your Xbox One games to your phone to enjoy console games on the go.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

If you want to connect your XBOX to your ISP's Wi-Fi network, there is a simple way to do it.

In this tutorial, we learn how to clear the ARP cache. First, go the command prompt on your computer and type in "C:/>netsh interface ip delete arpcache Ok". Press 'enter' on your keyboard and then it should be cleared out. If you want to view your ARP cache, type in the command "C:/>arp -a". If this fails, then you will need to use Microsoft Windows to repair the network connection. If this doesn't work, talk to the person that manages your connection. If successful, this will help make your...

In this video we learn how to use a proxy server to hack PS3 store. First, go to settings and then internet settings. From here, go to the custom method and then click continue until you see the option for a proxy serve. Then, enable this with it and make sure all your connections are automatic. Then, your internet connection will be tested. When it's finished, test out the connection to see if it's working. Then, go to the PS3 store and you should be able to hack it using your proxy server. ...

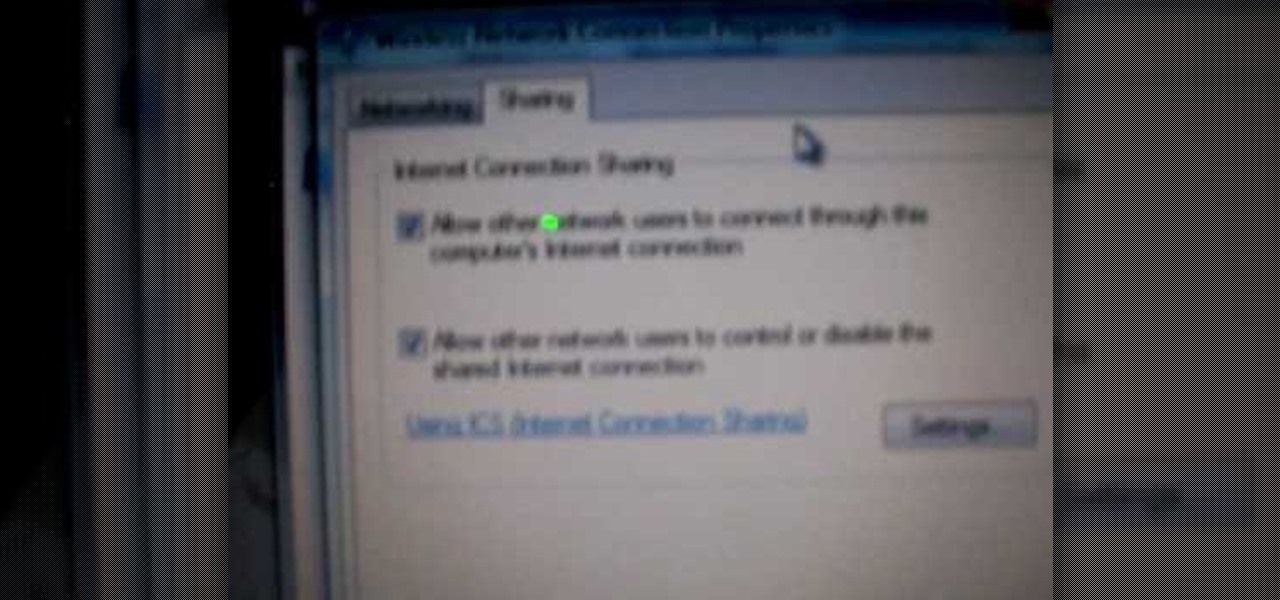
In this tutorial, we learn how to connect to XBox live through WiFi on a laptop. First, you will need to connect the ethernet cable from your laptop onto your game console. After this, go into your start menu on your computer, then go to network connections through the control panel. Go to the wireless internet connection and then click on your internet. Now, go to advanced and click on the button that allows other devices to connect to your internet connection. When you are finished, you wil...

In this tutorial, we learn how to connect to Xbox Live using a laptop with Windows Vista. First, connect the Ethernet cable to your computer and to the back of the game console. Next, Click on the start menu, then go to the control panel and view network connections. Next, click on manage network connections. After this, click on your local connection and hold down control until you see your wireless internet. After this, right click on your connection and then go to bridge connections. Next,...

Teflon tape or pipe dope can be used to create a seal on black iron pipe. Tim Carter of AsktheBuilder.com demonstrates how to do the job right and shares some helpful tips. This black iron pipe is used to transport natural gas to your furnace, water heater and stove. This pipe has threaded fittings at the connection point which need to be sealed with pipe dope or Teflon tape. Teflon tape should be wrapped onto the male end of the pipe in a clockwise direction. Pipe dope has the consistency of...

The PlayStation 4 has been around since 2013 and has brought with it countless game releases since then. One thing that hasn't changed, though, is the strict device restrictions on the PS4 Remote Play feature for streaming your games. The capability has always been there, but you still had to have an iPhone or Sony smartphone to get the best experience possible — until now.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

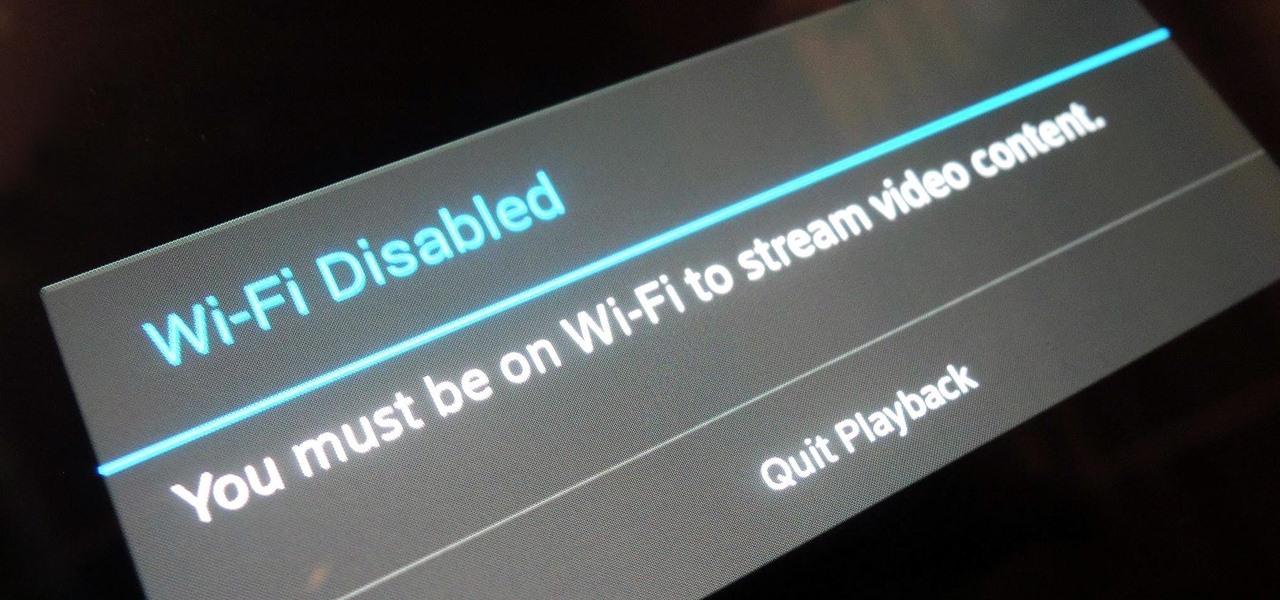
For any multitude of reasons, some apps require you to be connected to Wi-Fi in order to function properly. This could be because they would rather you have a stable connection to enjoy their content, or that they don't want users complaining about the amount of data being guzzled from carrier data plans.

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.