Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.

How to use Teflon tape for plumbing applications. I know it sounds simple but there are a few tricks to applying the Teflon tape. Teflon tape is also known as PTFE Tape.

For the most part, transferring files from your computer to your Nexus 7 (and vice versa) is a simple process. Just hook up your tablet to your computer with the USB cable and transfer. However, most of the time you'll need additional software on your computer to do this, and then, of course, you need the USB cable.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Usain Bolt ran 100 meters in 9.58 seconds, an insane record-breaking time that might not ever get beat. As fast as that is, wouldn't it feel like a travesty if your Samsung Galaxy S3 took that long to open up Wikipedia?

Internet slowing down, requiring you to Press F5 several times to refresh a web page is one of the irritating thing a computer user can come across. It needs to be fixed asap.

There was a dynamic mic in my junk box, but without any stand or connection cable. I needed a high-quality microphone to narrate my project videos, so I had to think of a way to build a stand for the mic. This is what I came up with.

The app with the most significant update on iOS 17.5 is, by far, Apple News. While there are a few changes in Books and Settings, as well as minor changes in apps like Podcasts, Apple News has at least 11 new features and changes you should know, some of which are worth getting excited about.

Excited about experiencing blazing-fast 5G speeds on your iPhone 12, 12 mini, 12 Pro, or 12 Pro Max? Well, that brand new iPhone you just bought might not actually be using 5G, even when you see that 5G symbol in the top right. Unless you follow these instructions, your iPhone will use regular old 4G LTE more often.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

In this clip, you'll learn how to speed up the Internet connection on a PC running the Microsoft Windows 7 operating system by using custom external DNS servers. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.

Having a backup sump pump is integral in making sure your basement is always protected from water, and if you have the Basement Watchdog battery backup sump pump system, this video will show you the complete installation procedure. Find out how to build a pipe connection to the discharge pipe, install check valves, connect to the backup system and more.

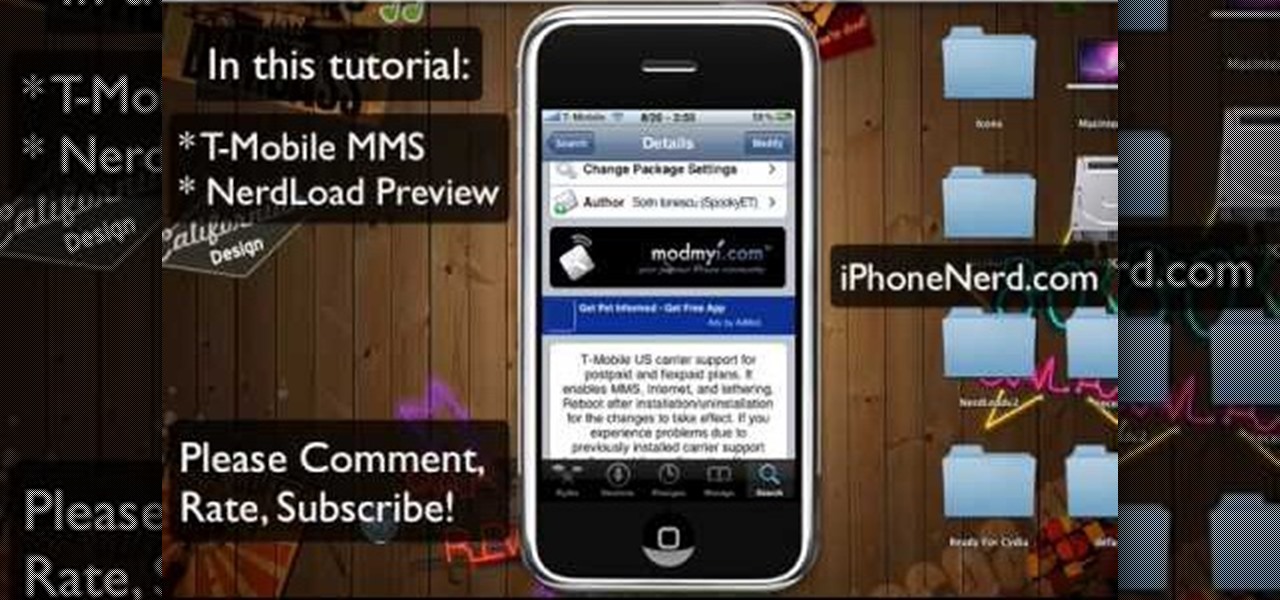
If you have T-Mobile and haven't quite figured out how to get MMS working with it on the iPhone, check out this video. This tutorial will cover activating the iPhones original MMS feature to work with t-mobile. This feature also allows you to share your iphones internet connection with other computers.

Need some IBM Lotus Notes help? Well, check out this video tutorial to learn how to connect to a Lotus Domino Server from Lotus Notes. This is a very quick connection to the Lotus Domino Server from Lotus Notes. Easy to follow.

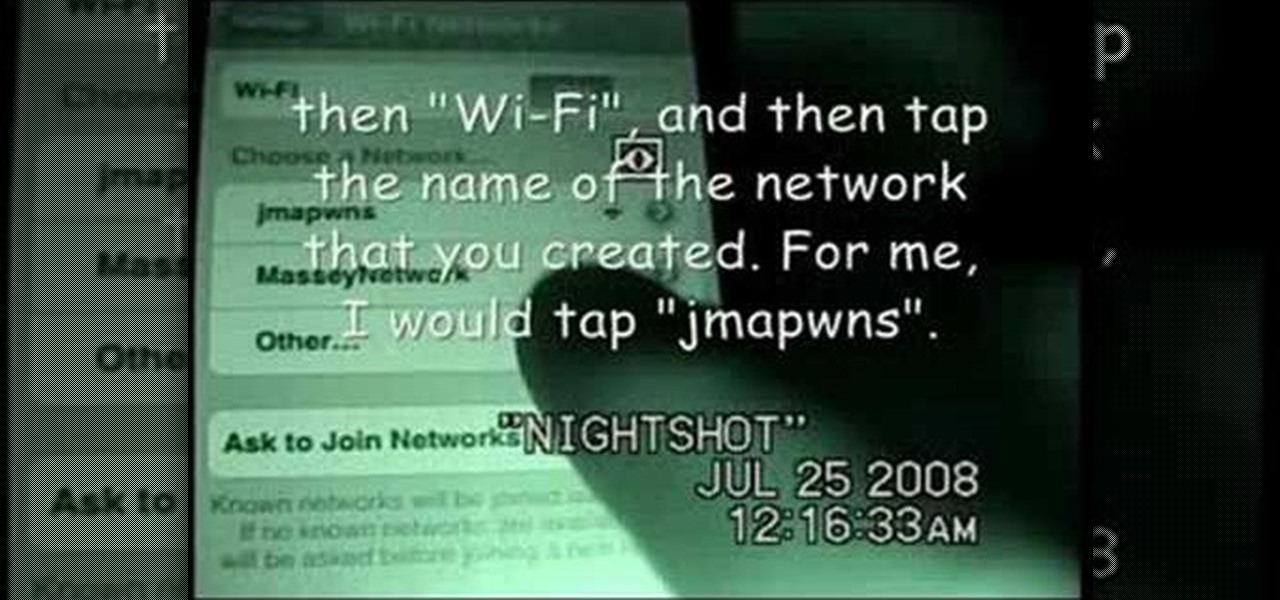
This is a nifty tutorial guide on how to tether your hacked iPhone or iPhone 3G to a windows computer for use as a high speed modem. Just Jailbreak your iPhone using one of the many tutorials on WonderHowTo, and install 3proxy. This video explains the rest of the configuration steps required to properly tether an iPhone 3G in Windows XP so that you can use its EDGE or 3G internet connection on your PC, for free.

This video will show you how to tether an iPhone 3G in Windows Vista so that you can use its internet connection on your own computer!

Watch this iPhone video tutorial to learn how to save those iPhone Web apps so you can use them even when you have no connection. This how-to video will help you learn how to use offline iPhone applications like a pro in no time. Perfect for new iPhone owners.

BPS golf instructor Steve Bishop discusses a particular technique used to improve your mental connection between what you want to do, and what you are doing.

When working in a network, you can't always see the connection lines if you are too zoomed out. This tutorial shows you how you can quickly connect nodes in Houdini.

Watch this video to learn how to use Google docs. You can view and edit your documents offline, without an active internet connection.

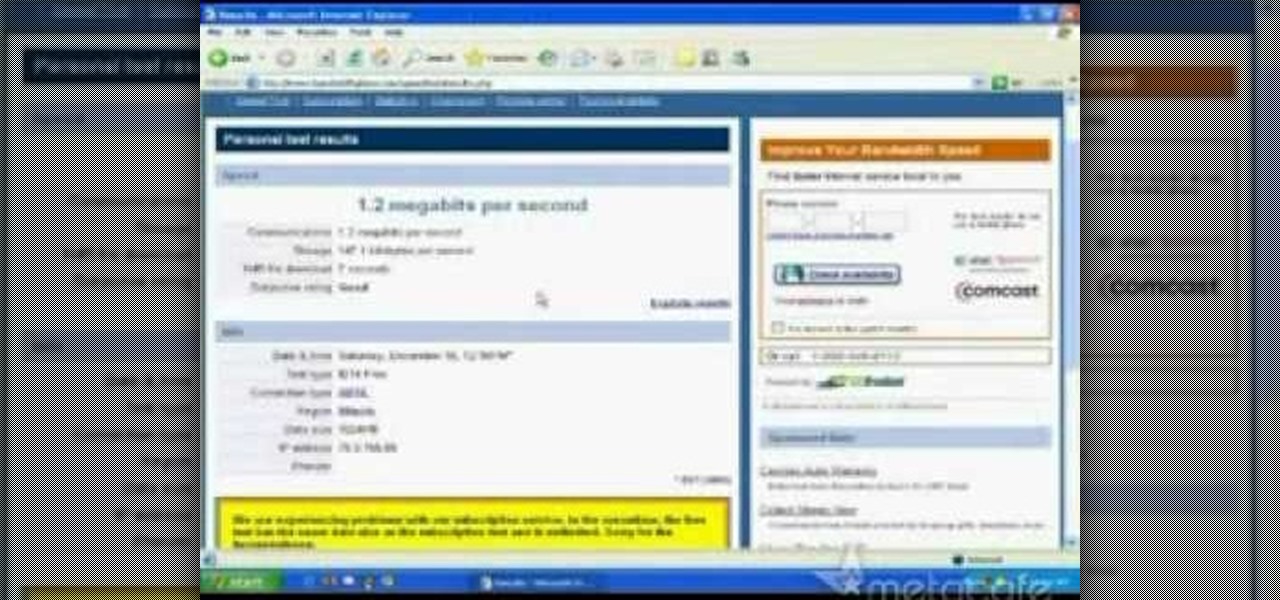
Learn how test and improve the speed of your DSL Internet connection.

You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how to program your PC to detect motion from dual input the Wiimote using GlovePie. You'll be able to connect two Wiimotes to your PC.

In this video, Rodney Yee shows us how to do the half-fish pose. This yoga pose primarily aids in digestion. It is also a common hamstring stretch done in most sports, with no yoga connection.

Android 11 is here. Prior to Google dropping the naming scheme, this would have been a dessert with an R name (maybe Rice Krispies Treat or Red Velvet Cake) — but nope, just plain ol' Android 11. And after months of betas and a global pandemic, it finally debuted a little over a year after Android 10.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Whether you're a professional mechanic, a hobbyist, or someone who just wants to know why their check engine light came on, your Android device and an OBD-II adapter can provide insight as to what's going on with your car. Most adapters sell for less than $10, and once you plug it into your vehicle, you'll just need a good app to help you make sense of all the data it can gather.

In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.

When attempting to gain access to a server, there may come a point when you need to get around file upload restrictions to upload something. If we can find a way to get around the restrictions, then we can upload anything we want to the server, effectively compromising it. That is what we'll be doing here today, so let's get started!

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

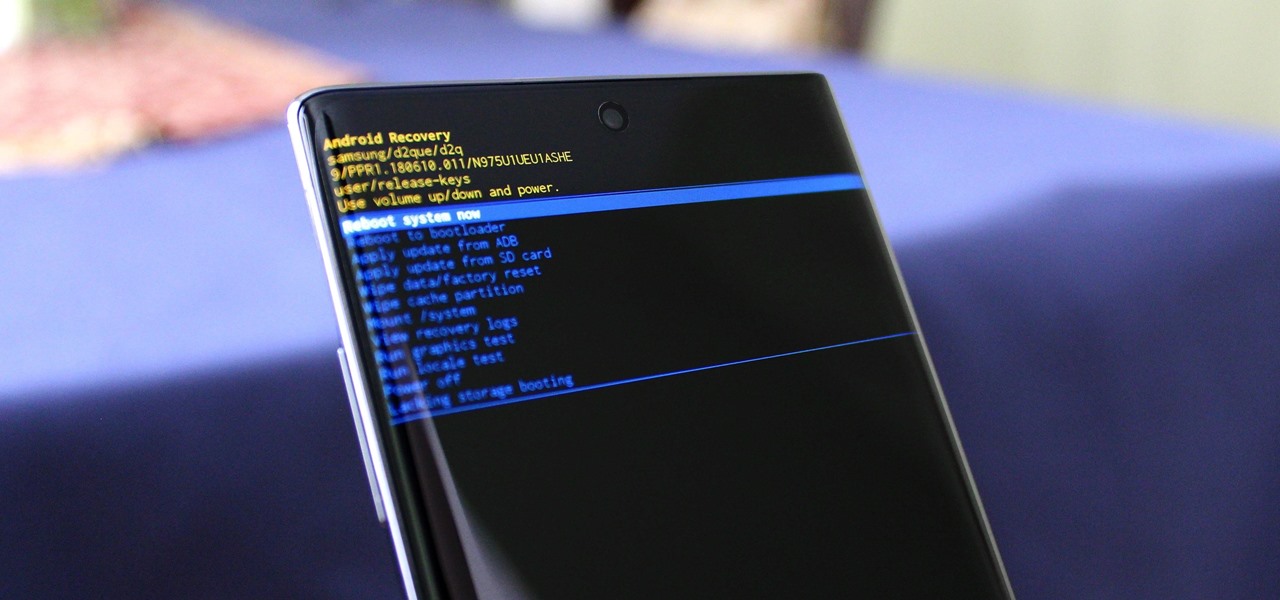
You can't call yourself an Android pro without knowing about Recovery or Download Mode. These menus are critical to do more advanced tasks on your phone, include sideloading software updates and un-bricking a device. But this year, Samsung changed the button combinations that will get you there.

While having no internet connection is definitely a bad thing when you need it, you can at least bide your time until you're back online with a hidden Easter egg inside of the Google Chrome browser. This gem unlocks a secret side-scrolling game that can keep you busy during your downtime.

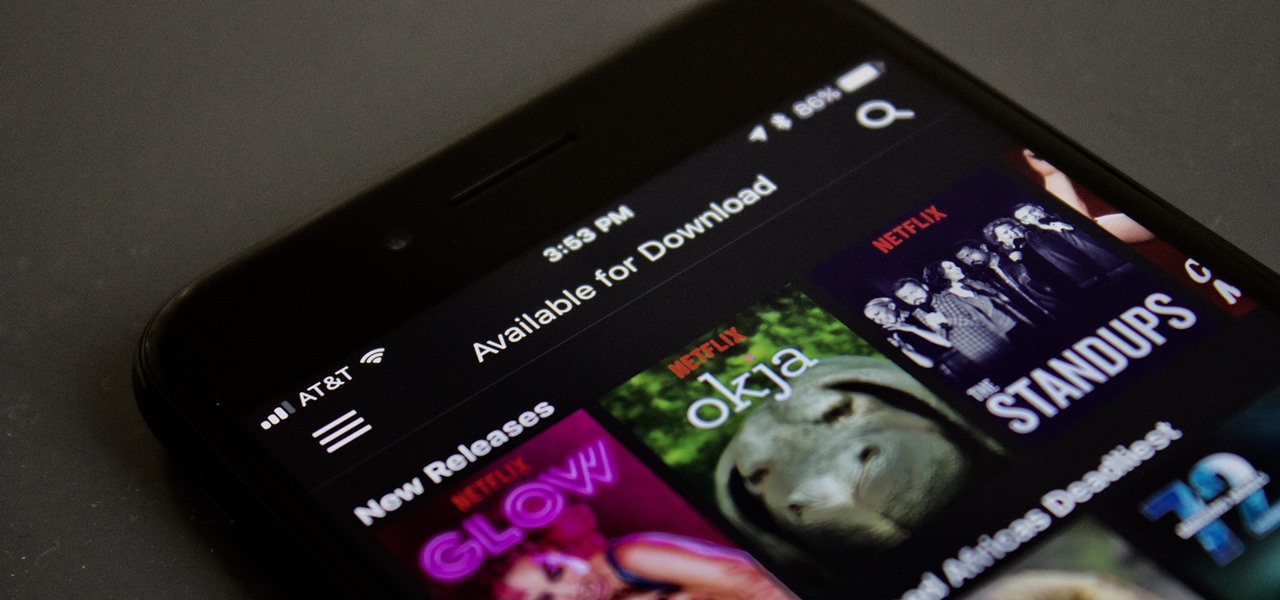
Netflix added the ability to download TV shows and movies on Android and iOS for offline binging back in Nov. 2016, and the process is the same as it is today. So if you anticipate having some downtime to catch up on Narcos or give Bright a try when you'll be away from a secure Wi-Fi connection, download videos onto your phone and save your data for more important things.

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.