Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.
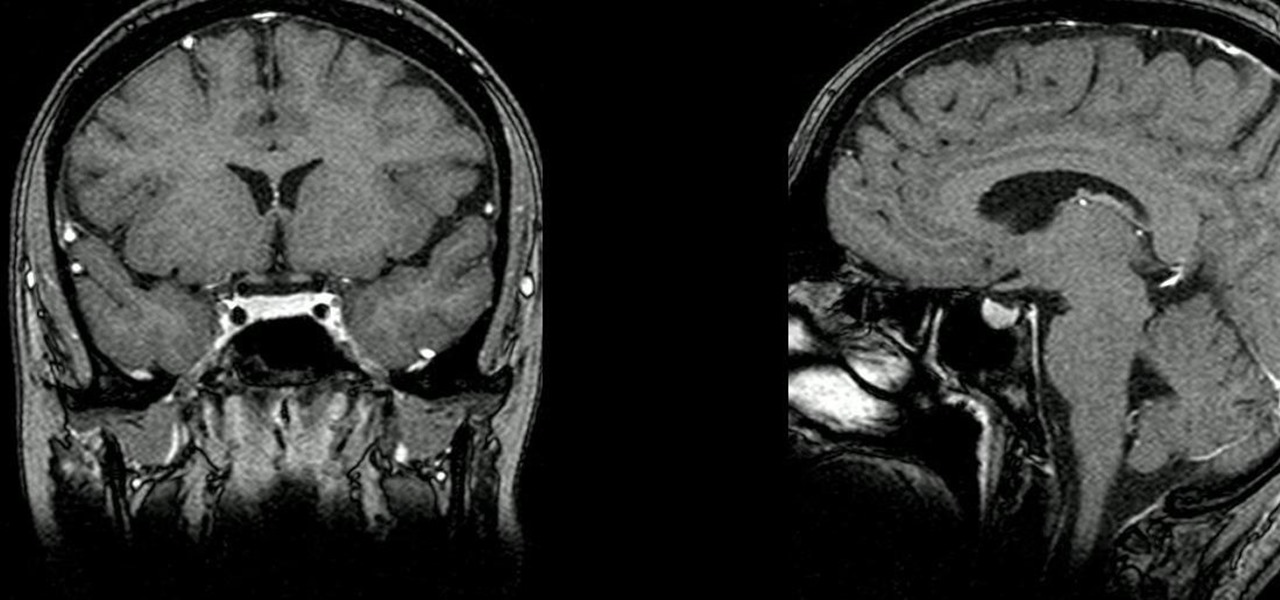
The community of bacteria that lives in our gut has a lot to tell us. It can give clues to what we eat, the environment we live in, and diseases and disorders we may have. Now, scientists have linked these bacterial species to how we feel. A new research study found an association between women's gut bacteria and their emotions.
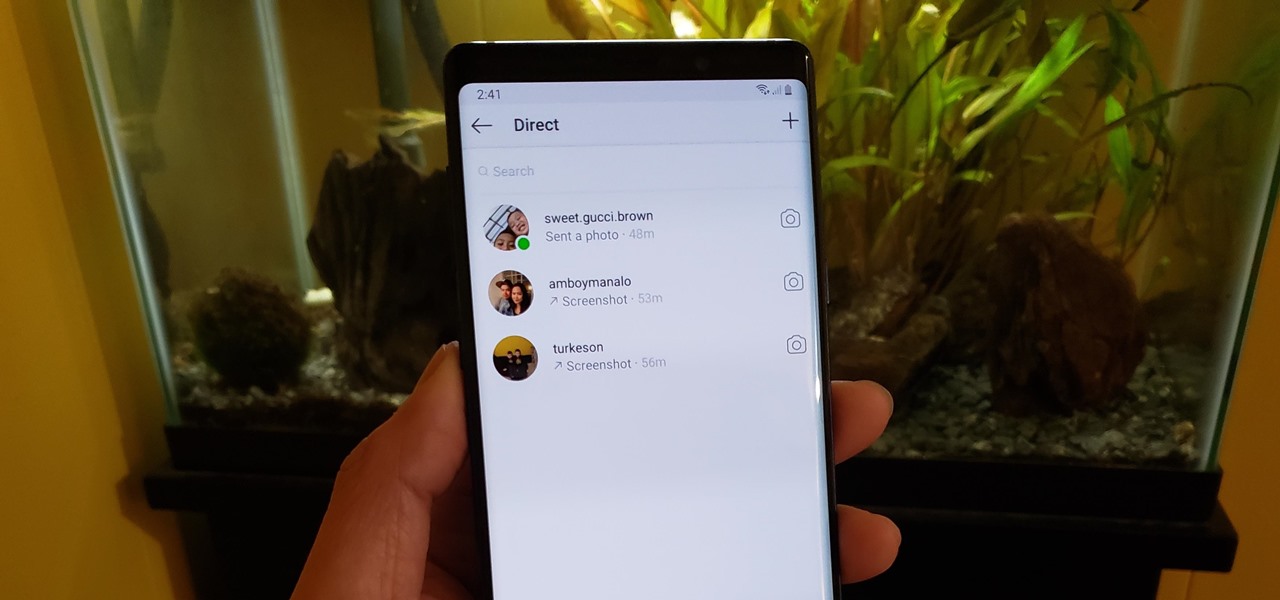
If imitation truly is the sincerest form of flattery, then Snapchat must be blushing profusely as Instagram continues to shamelessly copy its features and dig into its wallet. Instagram has also managed to copy some of the security aspects — or lack thereof — of one of Snapchat's hottest characteristics.

SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting for newbies to get down, and that's where Punchabunch comes in.

The NSA's massive internet spying efforts will continue. In President Obama's latest press conference, he went public to (in so many words) say that the NSA's spying efforts will continue uninterrupted. This, coming just weeks after the Amash Amendment which would have defunded the program, was narrowly defeated in the House (you can check if your congressmen voted against it here).

I obviously do a lot of Steampunk projects, but there are a ton of things out there that I haven't tried yet. So, in an effort to broaden my horizons, I recently taught myself how to use Arduinos, which I plan to incorporate into some of my future Steampunk builds.

Check out this Do It Yourself (DIY) RV maintenance and repair video to learn how about RV battery maintenance. Know how to do it to keep your batteries running strong in your recreational vehicle with this RV tutorial video.

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

The new iPhone XS and XS Max have more issues than just their hefty price tags. Customers have only had the phones for a handful of days, but some are already complaining of cellular and Wi-Fi connectivity issues on both models. If your experience is the same on your XS or XS Max, there are steps you can take to get your iPhone reliably back online.

The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely.

Many of us rely on our smartphones for all our media needs. Now more than ever, we're using Bluetooth connections to play audio over speakers, headphones, car sound systems — the list goes on. If you own a Samsung smartphone like the Galaxy S9, there are a number of Bluetooth tweaks and hidden tricks that can maximize your audio experience.

Realizing there's no voice to guide you while using your iPhone to navigate can be problematic, causing serious headaches from getting lost to unscheduled pit stops or worse. And while this problem can hit Apple Maps like other navigation apps out there, there are a number of fixes you can try to get navigation audio working again.

Apple has introduced a special edition iPhone 8 and 8 Plus to bring attention to the ongoing worldwide battle against AIDS. As the second iPhones to carry the (PRODUCT)RED name, these rare iPhones may quickly sell out when preorders open up on Tuesday, April 10, at 5:30 a.m. (PDT), so we'll go over some tips to help you secure a red iPhone before it's gone.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Apple just unveiled a red iPhone and iPhone 7 Plus, dubbed the iPhone 7 (PRODUCT)RED Special Edition, to commemorate the ongoing global fight against AIDS. Apple fans the world over are sure to swarm in and gobble up the initial stock shortly after the new color is released at 8:01 a.m. (PDT) on March 24, 2017, so we'll go over some tips to help you secure a red iPhone before it's sold out.

When a new version of iOS comes out, everybody gets caught up in the craze of finding features and playing around with new functionality. But this generally leads to a lack of coverage on the finer aspects of the update—things like bugs, minor tweaks, and pain points that users discover along the way.

When attempting to gain access to a server, there may come a point when you need to get around file upload restrictions to upload something. If we can find a way to get around the restrictions, then we can upload anything we want to the server, effectively compromising it. That is what we'll be doing here today, so let's get started!

As someone with a pretty nice TV, I've never found the allure in purchasing a projector. While they're certainly smaller and sleeker than a television, and more portable, they can be pricey and produce a less than stellar image. And who really buys a projector anyways? They're for school, they're for work, they're for theaters, but they're not really for my apartment, right?

Though many students spend four years of high school learning a foreign language, most of us probably retained very little. Chalk it up to the carelessness of youth, but chances are you've since been in situations or places that left you wishing you paid more attention in class or had continued practicing long after you graduated.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

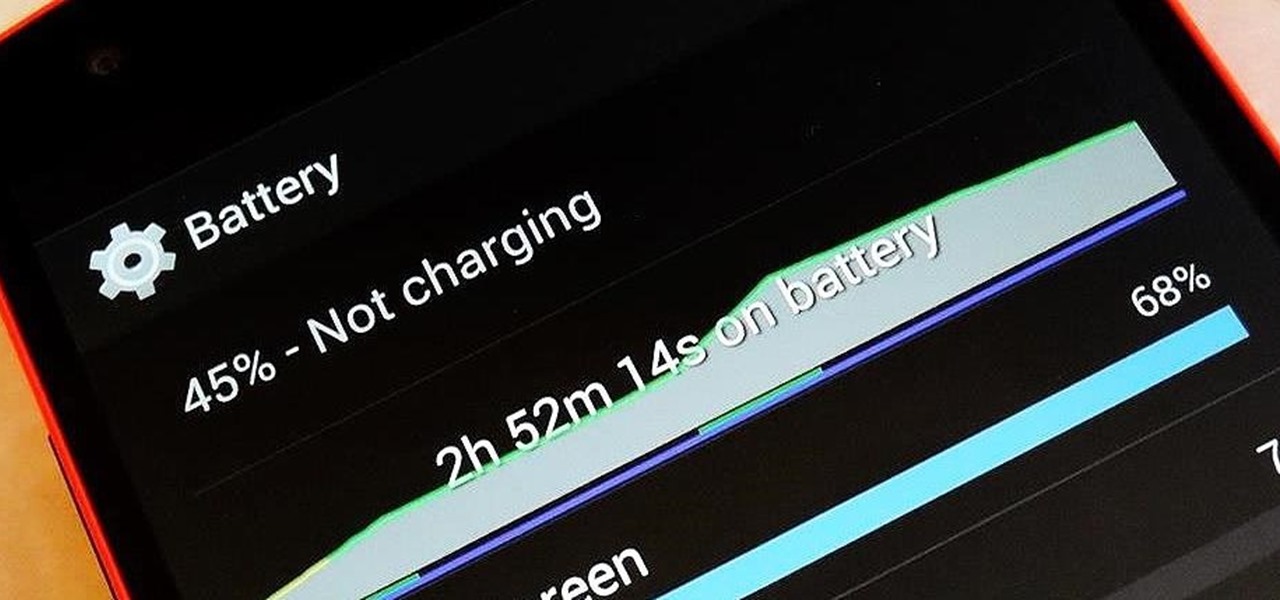
There are so many things to love about the Nexus 5, from timely updates to newer versions of Android to a terrific blend of price and specs. But while mobile phone tech keeps churning along, battery technology isn't quite up to snuff yet, and I find myself wishing that my phone's battery lasted longer on a single charge.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

It may not be as large as the Samsung Galaxy Note 2, but the Galaxy S3's screen size is still big enough to make iPhone owners cry themselves to sleep. The 4.8-inch AMOLED display with 720 x 1280 pixels makes the GS3 a great mobile companion—and an even better portable gaming device.

Last time, I showed how to start putting together an AC arc welder from scavenged microwave parts, focusing on the transformer modifications. Now, I'll show you how to finish up your DIY stick welding machine by fixing up the electrical system and performing the finishing touches.

Curve stitching is a form of string art where smooth curves are created through the use of straight lines. It is taught in many Junior High and High School art classes. I discovered it when my math students started showing me the geometric art they had created.

There is so much information in the world that trying to make sense of it all can be daunting. That's where data analytics comes in. By learning how to inspect and model data, you can take large data sets and transform them into highly valuable information that can take any business further.

Your phone is loaded with contacts you've collected over the years. They're an asset, and you should use your library of connections outside the confines of your mobile device. Luckily, your Pixel uses a standardized medium to store contacts that can be used by the likes of LinkedIn, Outlook, Hubspot, iCloud, and more.

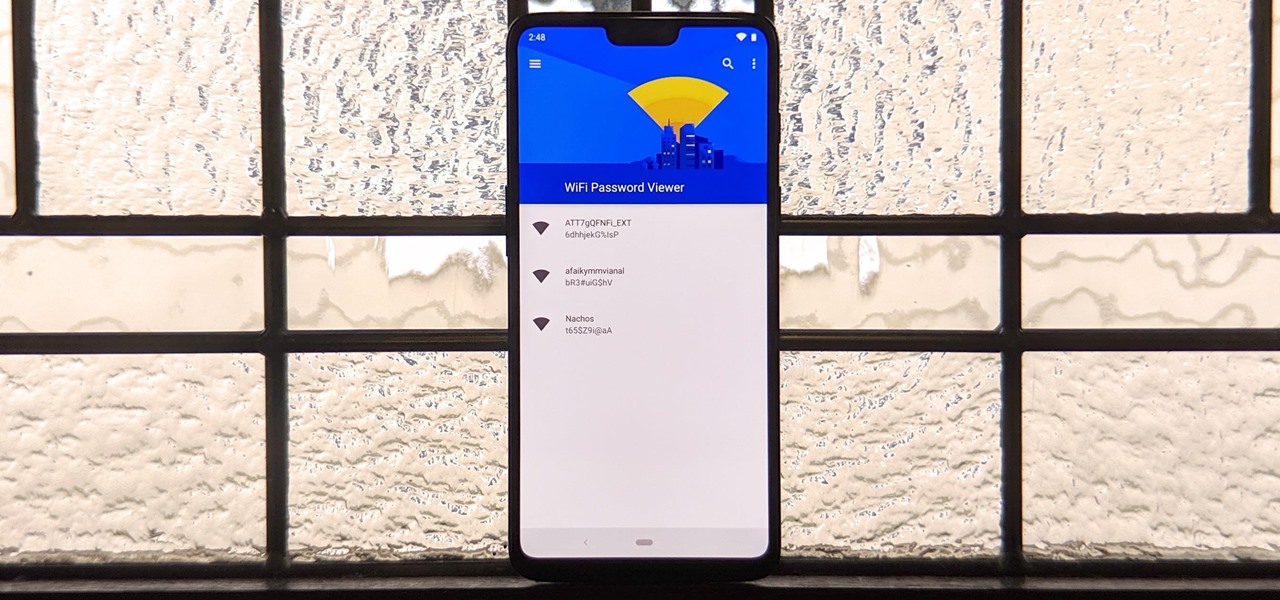
You've probably connected your Android device to dozens of Wi-Fi networks since you've had it, and your phone or tablet remembers each of them. Whether it's a hotspot at home, school, work, the gym, a coffee shop, a relative's apartment — or even from a friend's phone — each time you type in a Wi-Fi password, your Android device saves it for safekeeping and easy access later.

Let me paint a picture for you. You're on a long flight home, and while listening to music on your Samsung Galaxy S10, a great song comes on. You want your friend to hear it too, who's also listening to music using a pair of Bluetooth headphones. Thanks to Dual Audio, you can easily share your experience.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

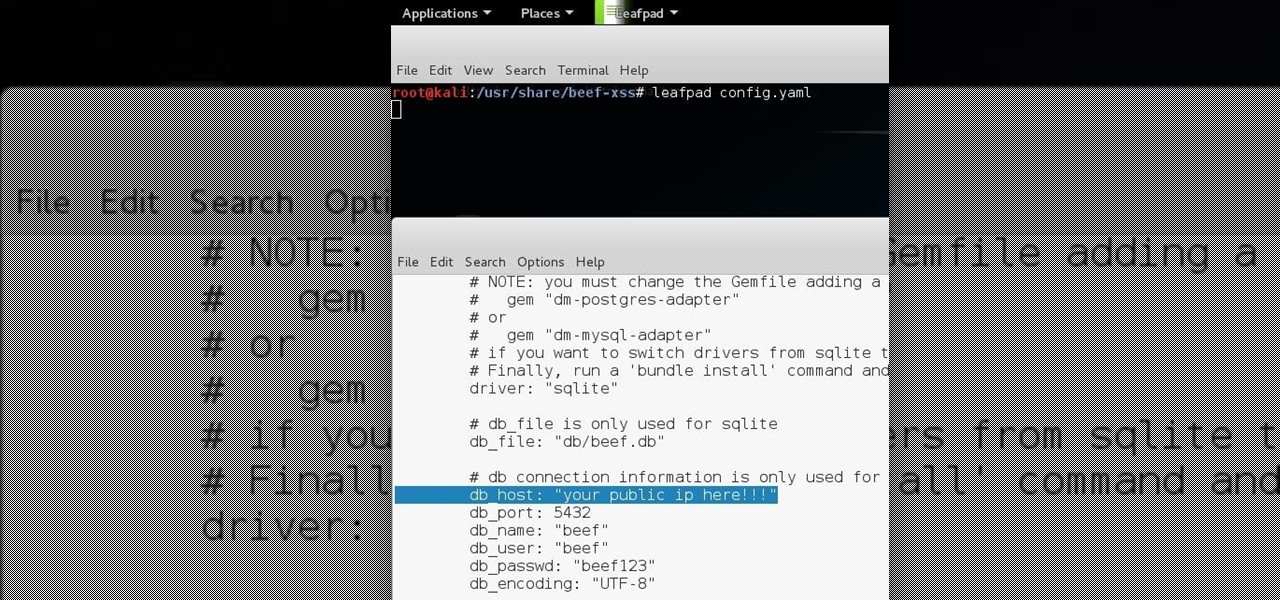
Hello all Just thought id share how ive managed to get beef working over the internet.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

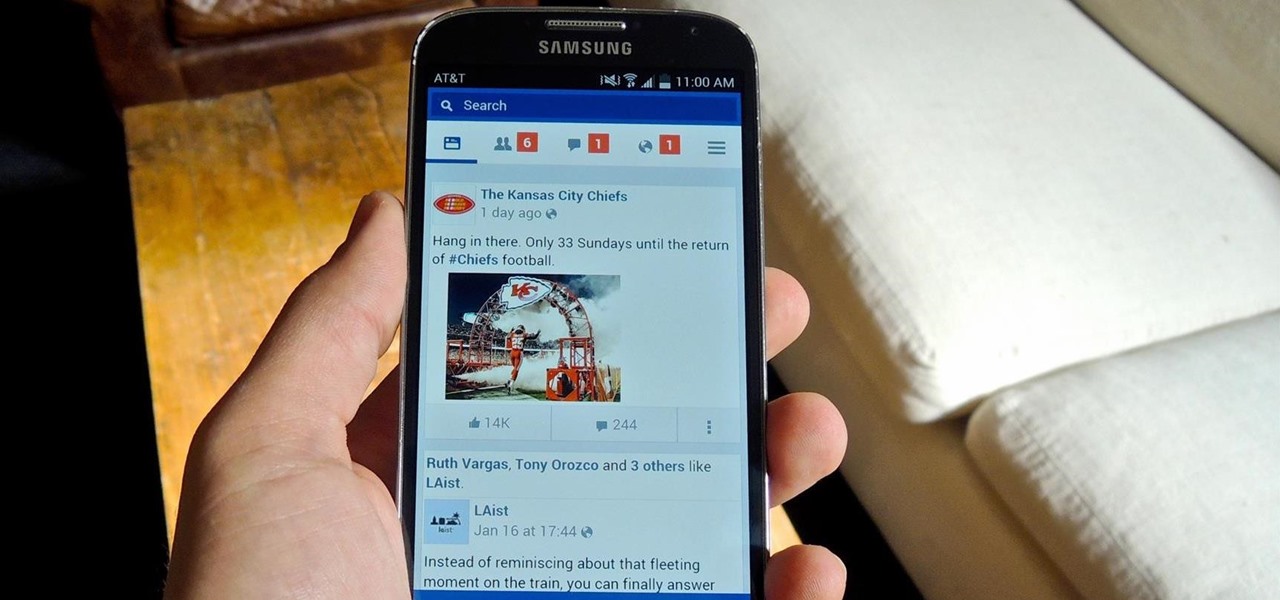
As one of the most frequently used and popular applications available, Facebook is now attempting to be a little more considerate for those Android users that don't have a bleeding-edge device or fast data connections.

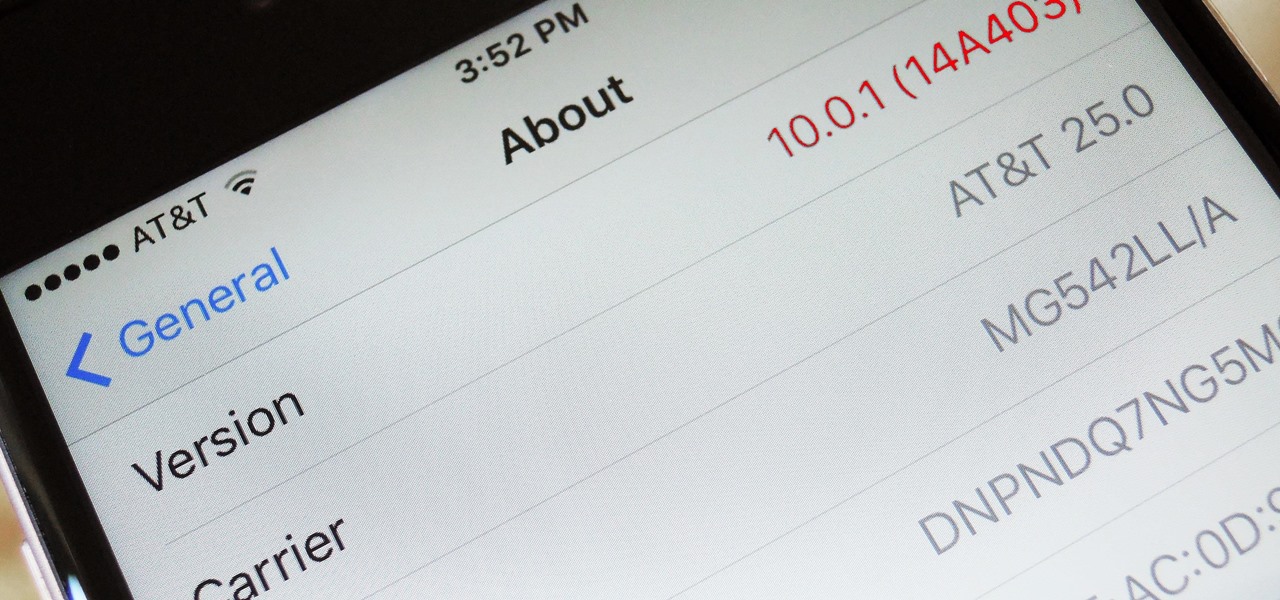
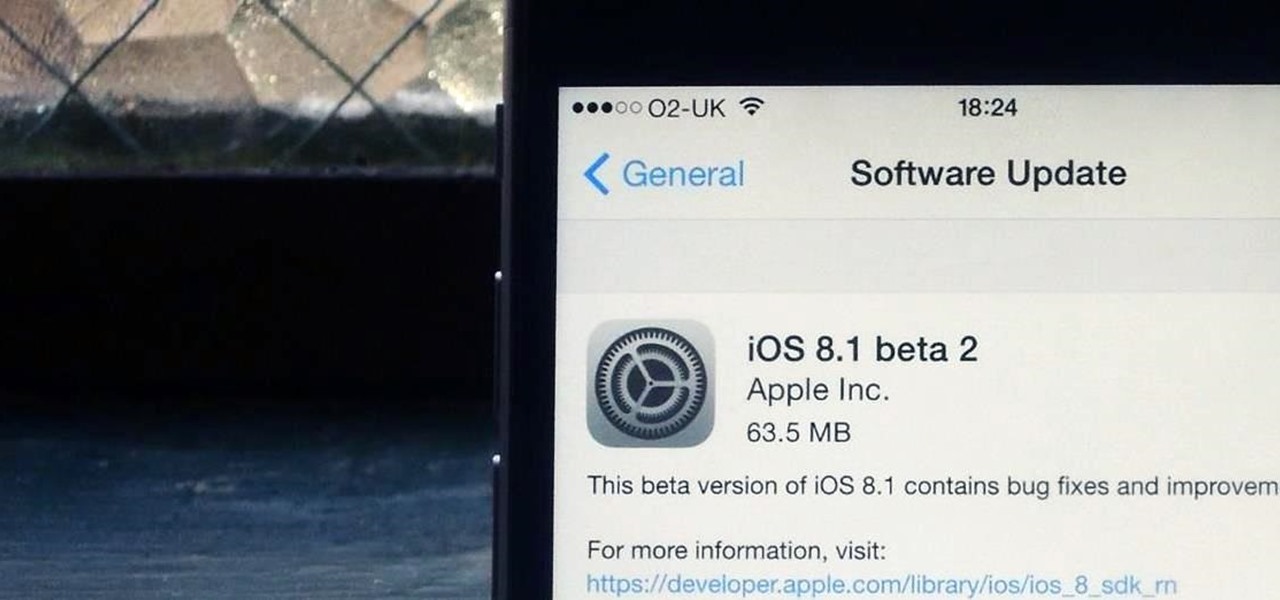
Shortly after Apple's iOS 8.0.1 update fiasco ruined many iPhone users' cellular reception (which was fixed with iOS 8.0.2), developers were treated to the first beta release of iOS 8.1, which will be the next big update for iPad, iPhone, and iPod touch.