Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.
One of the biggest reasons to go with an iPhone over an Android device is Apple's interconnectivity. iPhones, iPads, and macOS devices are all connected in a way that allows seamless transition between devices. Android lacks such a feature by default, but that isn't the end of the story.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

When it comes to the business of augmented reality, companies that aren't already introducing new products or apps are focused on producing the AR technology of the future. But in the realm of real products and apps, Magic Leap continues to show off what its headset can do, this time via a new app that transports users to the ocean's depths.

For the first time, you can officially use a computer mouse with your iPhone, thanks to Apple's new Accessibility settings in iOS 13. It works for all types of Bluetooth mice, so if you have one, it'll already work. Plus, those with wireless receivers and even wired mice are supported by using a USB to Lightning adapter.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

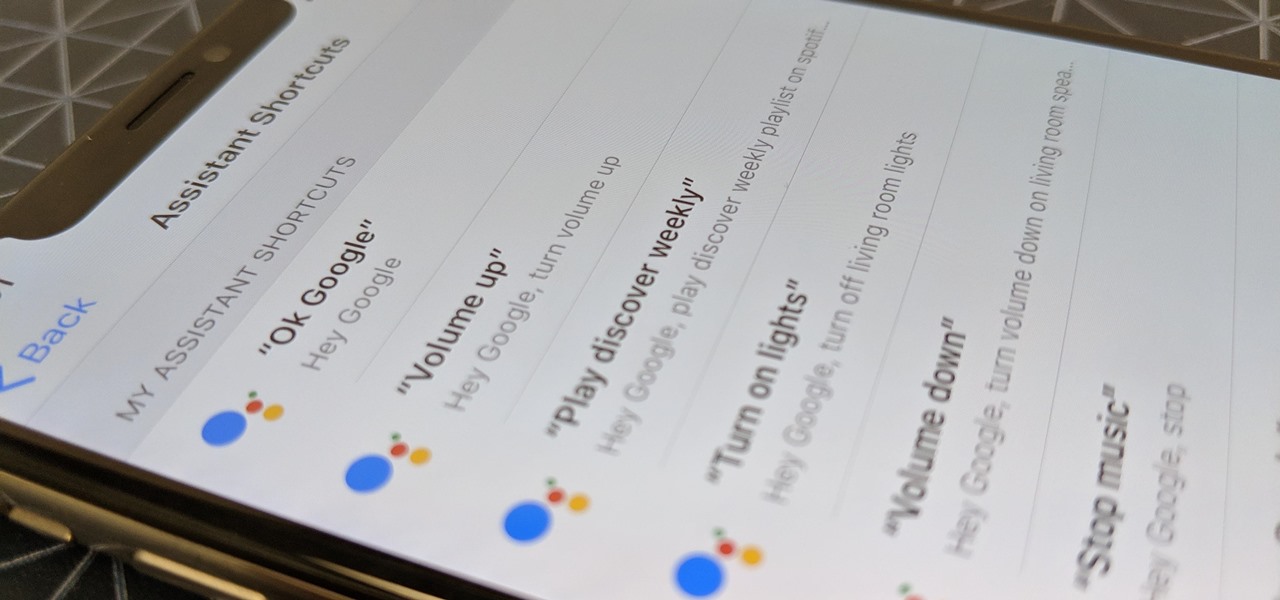
Using Siri to perform tasks on your Google Home device was never possible until Apple released Siri Shortcuts in iOS 12. Actually, it wasn't possible until Google added support for Siri Shortcuts for Google Assistant in Nov. 2018. No matter the timing, the important thing here is that you can use Siri to command Google Assistant which, in turn, can command Google Home.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a tiny Arduino Wi-Fi sniffer that saves Wireshark-compatible PCAP files and fits anywhere.

Every step in the evolution of computing brings an in-kind leap forward in user input technology. The personal computer had the mouse, touchscreens made smartphones mainstream consumer devices, and AR headsets like the HoloLens and the Magic Leap One have leveraged gesture recognition.

If you salivate at the idea of waking up to the Jarvis-powered smart window from the opening minutes of Marvel's Iron Man, then connected home appliance maker CareOS is here to make your playboy billionaire philanthropist dreams come true.

Although the Essential PH-1 got off to a rocky start, thanks to steady updates, it has slowly become one of the best Android phones to come out in recent years. For $499, the Essential Phone is a cheaper Pixel, receiving updates almost as soon as the Pixel lineup does. What's more, you get a phone with an easily unlockable bootloader, which is the first step to rooting.

The new iPhone XS and XS Max have more issues than just their hefty price tags. Customers have only had the phones for a handful of days, but some are already complaining of cellular and Wi-Fi connectivity issues on both models. If your experience is the same on your XS or XS Max, there are steps you can take to get your iPhone reliably back online.

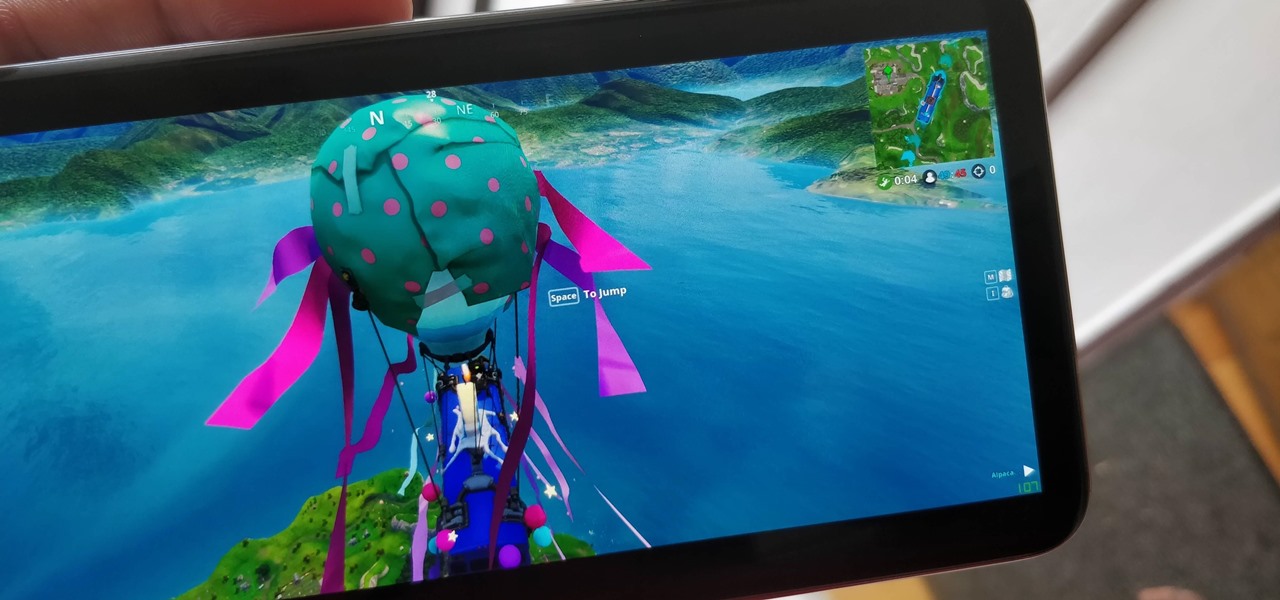
Since early March, iOS users have been able to enjoy the most popular video game sweeping the rounds. Android users have been left envious as they wait for a "few months," the only vague release date given by Epic Games. In the meantime, there are a few ways we can still satisfy our urge to play.

Extra hardware buttons have become a trend with smartphones lately. Often, these are unmodifiable buttons designed to launch a voice assistant. That isn't the case with the BlackBerry KEY2. Making a return from the KEYone is the Convenience Key, which also received an upgrade.

Earlier this year, with the Developer Preview, we got a tantalizing glimpse of Google's upcoming Android 9.0 Pie and a whole slew of new features that comes along with it, such as iPhone X-like gestures and improved security features, to name a few. With its announcement at Google I/O, Android Pie just got a lot more accessible.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

For some of you, whether or not to delete Facebook is a daily struggle. One reason you might not have pulled the trigger on your Facebook account yet could be because of Messenger, which provides millions of people with different devices an easy way to communicate with each other. But here's a secret you might not know: you don't need to have a Facebook account to use Facebook's popular chat app.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

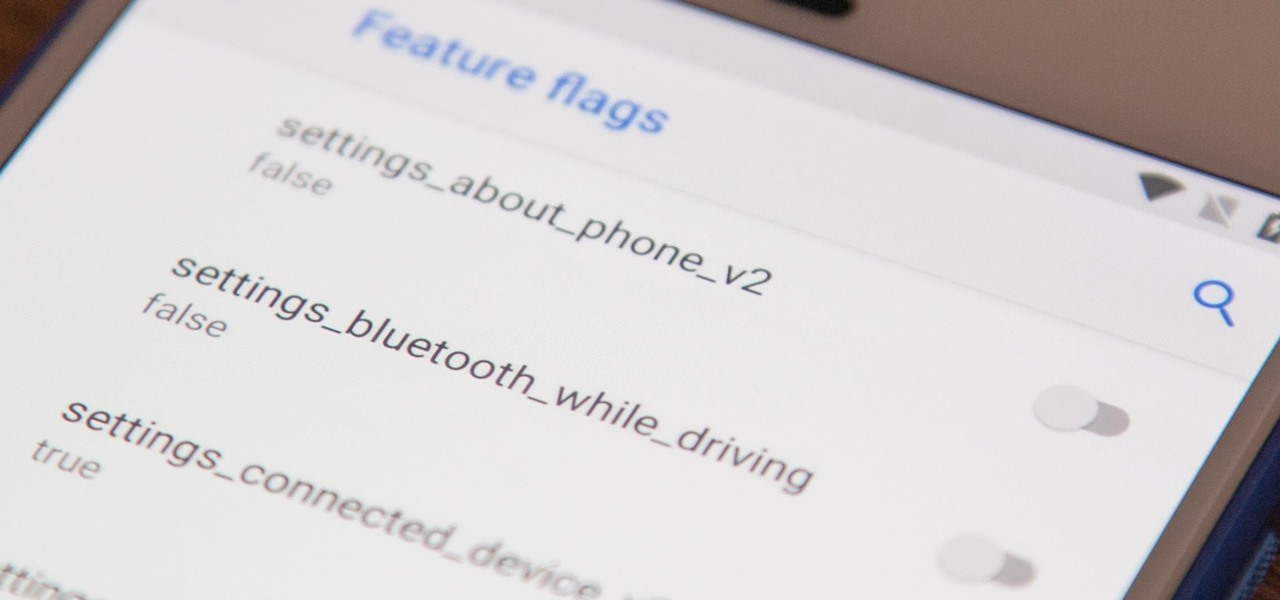
There's a new secret settings menu hiding in Android 9.0 Pie that offers Chrome-style "flags" to the overall operating system. Since it's currently the first Developer Preview and Public Beta versions, it's possible that this menu could disappear entirely when the stable version finally gets released, but it could also persist in its current hidden state where you have to unlock it.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

For years, PuTTy has reigned supreme as the way to establish a Secure Shell (SSH) connection. However, those days are numbered with the addition of the OpenSSH server and client in the Windows 10 Fall Creators Update, which brings Windows up to par with macOS and Linux's ability to use SSH natively.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

If you've spent countless hours scrolling through Instagram feeds full of selfies, then I'm sure you know that some are, well ... better than others. There are so many different things you can do to start taking better selfies to post on social media. One really easy way is to start shooting in VSCO.

On the surface, iOS 10.2 might look the same as iOS 10.3, but there's one big difference between the two versions: iOS 10.2 can now be jailbroken! Jailbreaking your iPhone means gaining access to thousands of tweaks and mods which greatly enhance the iOS experience, so this is great news for the power users out there.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

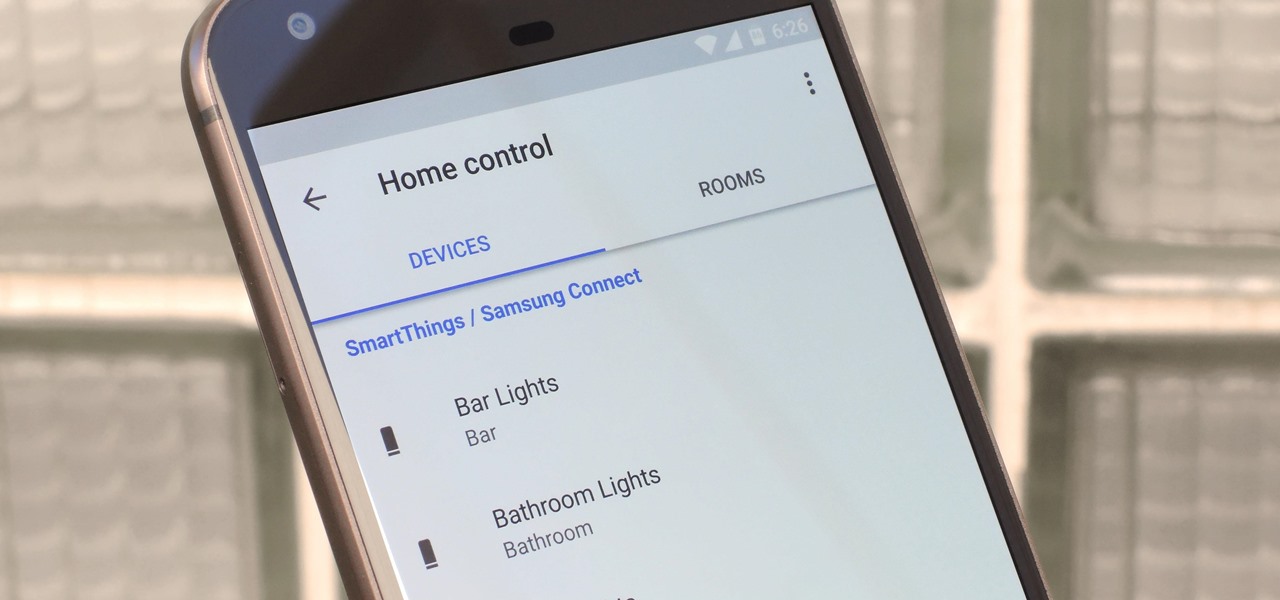
The world around us keeps getting smarter. Not only do we have advanced AI services like the Google Assistant, but now we've got the Internet of Things connecting physical objects to the digital world. It's amazing when you think about it, but the real sci-fi stuff starts to happen when these two technologies intersect.

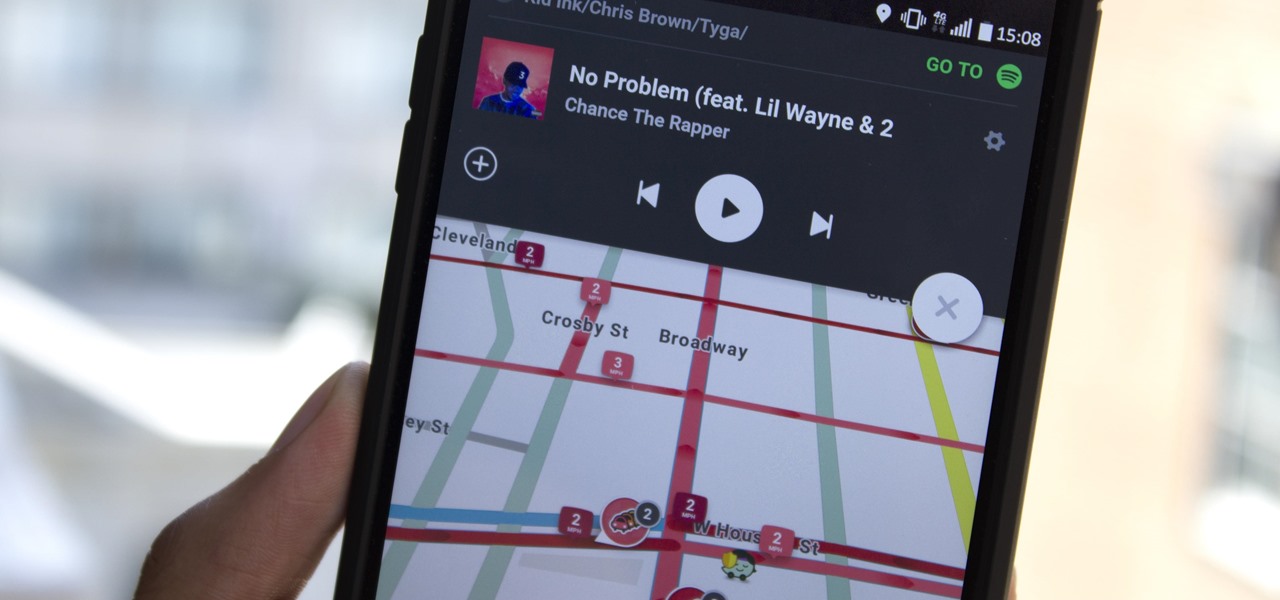
Who doesn't love listening to music or playlists when driving? The open road and an awesome playlist make for a perfect pairing, but it can become quite the challenge if you're trying to navigate at the same time. That's why Waze's built-in audio controls for compatible apps like Spotify and Pandora are so useful, so you can always keep your eyes on the map and road ahead of you.

If you haven't been on any sort of social media all day — which I seriously doubt — then you might not have heard that today, June 30, is Social Media Day. It's been trending on Twitter, but has also been making appearances on Instagram and Facebook. While major influencers are talking up a storm about this, most people are simply asking "what is social media day?"

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

A groundbreaking new Android feature called seamless updates was announced at Google I/O 2016. No longer would we have to wait for updates to download and install — instead, they'd be applied silently in the background, and the new Android version would be waiting on us the next time we restarted our phones.

The new iOS 10 won't be released to the public until September 13 via an OTA update, but the Gold Master edition is available right now. Essentially, it's the same version that Apple will release on the 13th, but only for developers so they can get their apps up to snuff before everyone updates. Users on the iOS 10 public beta will not be getting this GM update.

Counter-Strike is one of the most popular first-person shooters of all time, and deservedly so. What originally started out as a third-party Half-Life mod garnered such a cult following that Valve had to hire the developers and purchase the intellectual property to make it an official standalone release.

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.

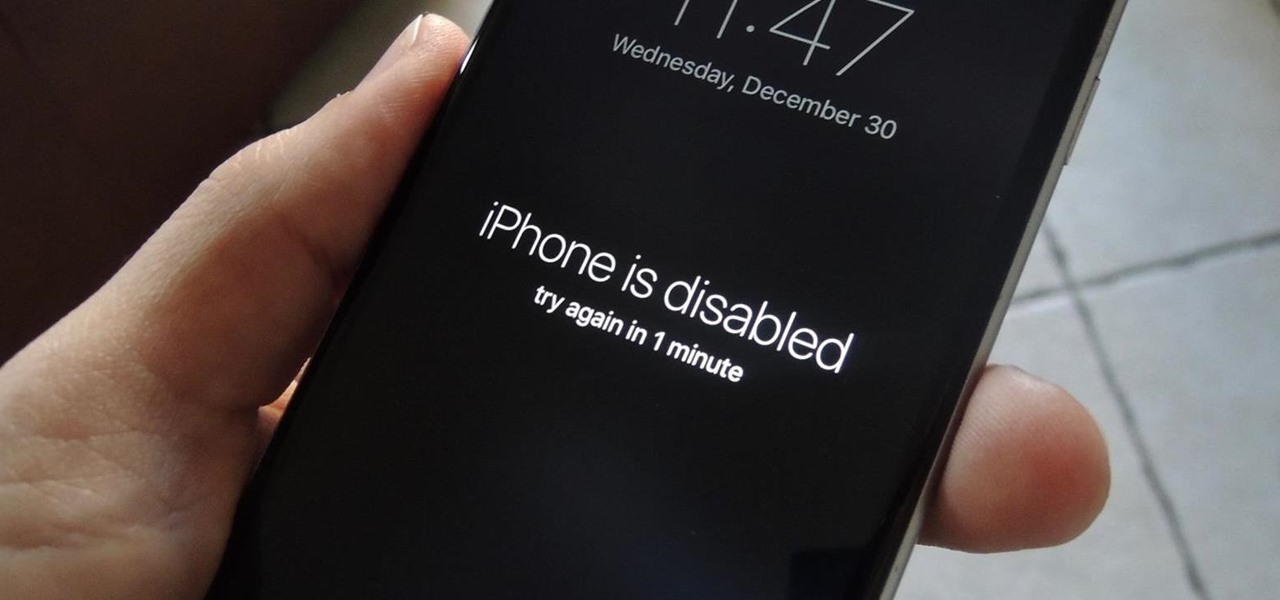
With Touch ID on iOS devices, it's a little more difficult to lock yourself out. However, it can still happen if you don't use it, have a busted fingerprint scanner, or use an older device that doesn't have Touch ID, which means you're passcode dependent (unless you have zero lock screen security).
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

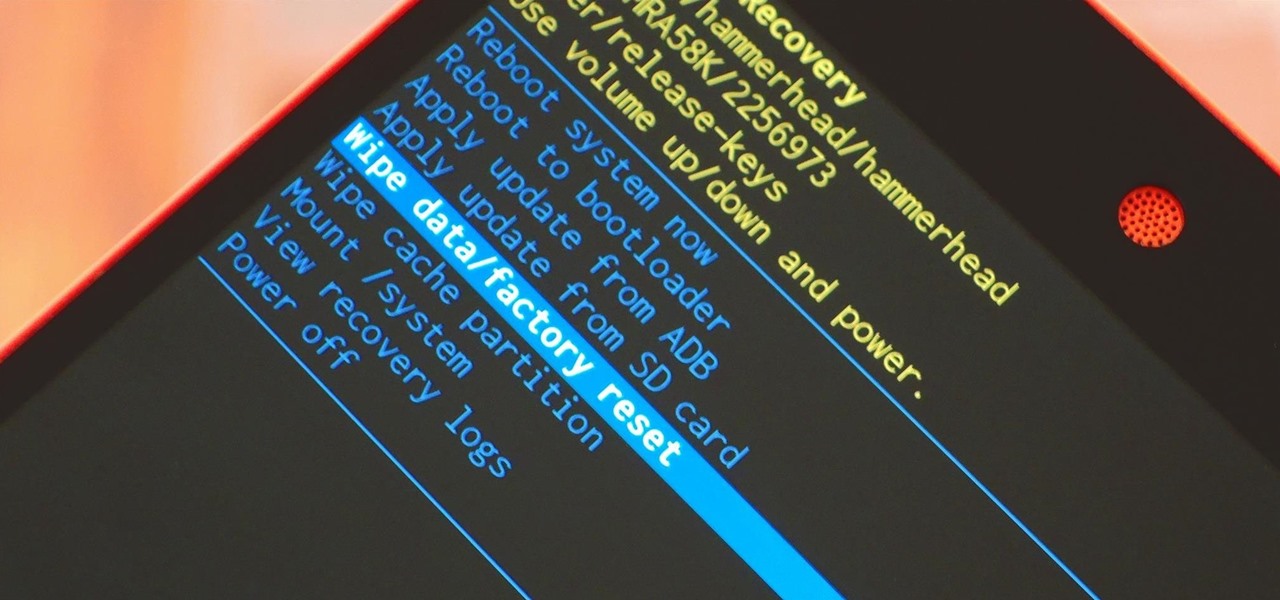
When it comes time to sell your smartphone or trade it in for your annual upgrade, you'll have to make sure that all of the sensitive data the device accumulated while you owned it is properly erased so that no one else can access it. This process is referred to as a "Factory Reset," and regardless of if you own an iPhone or Android device, like a Samsung Galaxy model, HTC One, or Nexus, I'll show you how to do it below.