It's that time a year when winter storms begin causing havoc across the United States, and when "rotating outages" are common to help sustain the electrical grid during intense cold periods. That means pretty much anybody with snow and ice in their backyard can succumb to power outages. And no electricity means no electric heat.

SCRABBLE. To some it's just a game, but to me it's life or death. Well, not really, but it feels that way anyway. On a normal weekend, a game becomes much like Jon Thomas' "friendly game of death Scrabble."

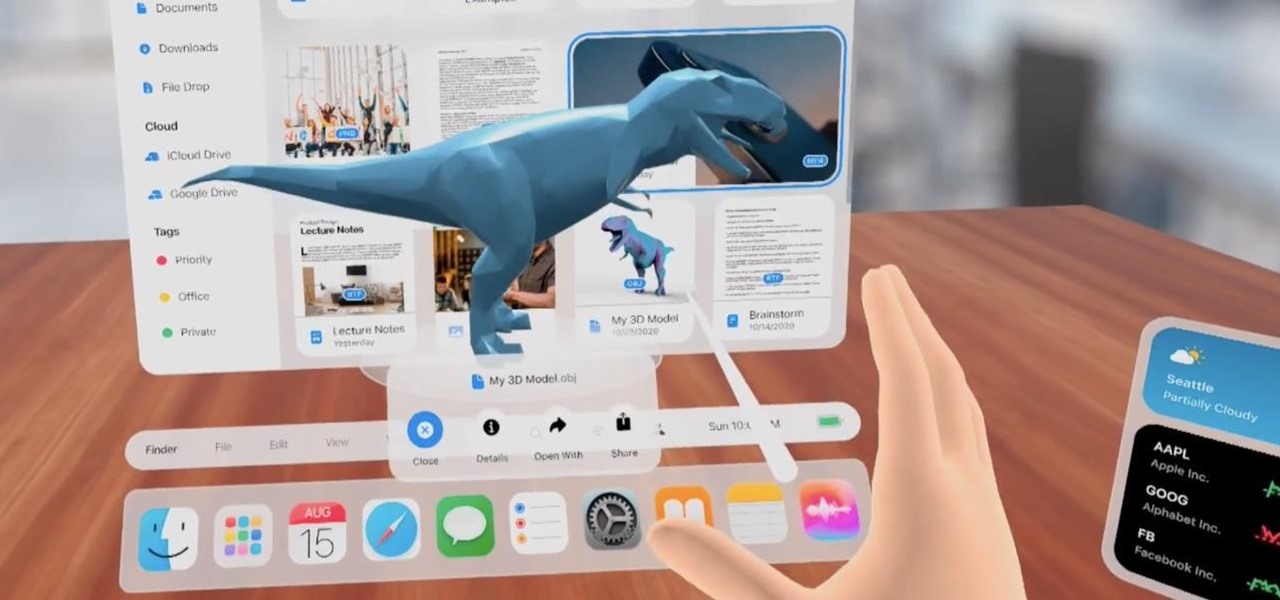
The Apple rumor mill never stops churning and when it comes to augmented reality smartglasses, the chatter has been particularly hot in recent months.
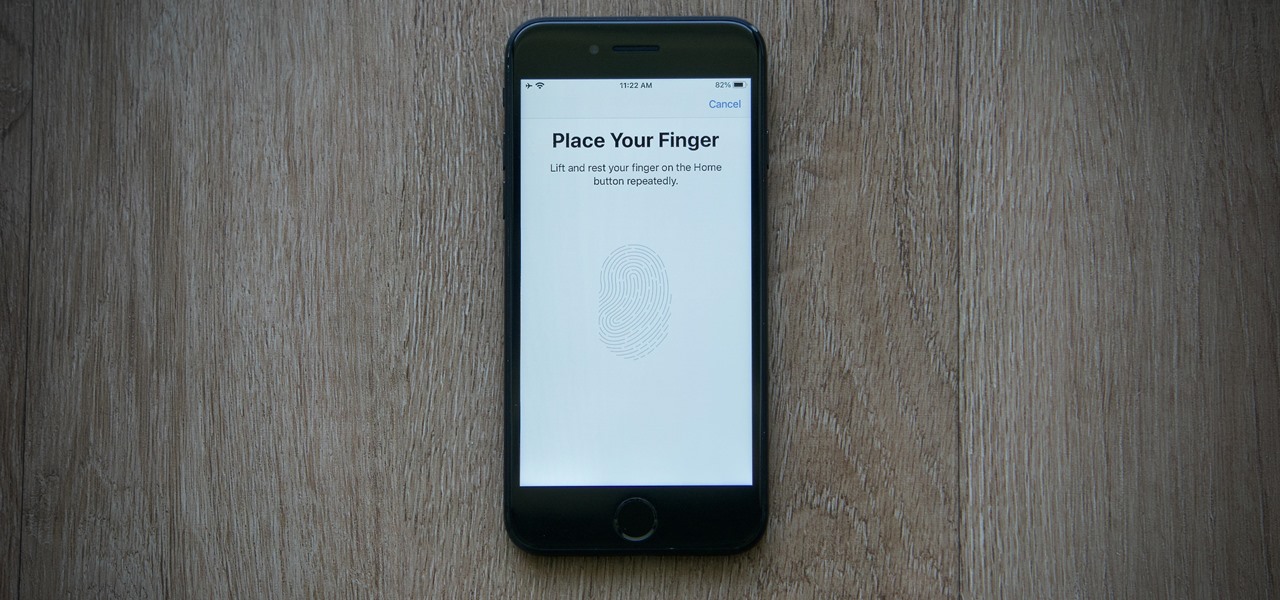
While Face ID might have taken over as Apple's favorite authentication method, Touch ID is still very much alive. The tech is usually speedy and accurate, but you might have noticed that it's been a bit laggy recently. If that's the case, you should know that Apple actually fixed this issue. Here's what you can do.

After integrating Snapchat into its latest Galaxy A Series smartphones, Samsung is trying out a new AR camera app for its army of mobile devices.

With everything the last year has thrown at us, the odds are good that you've had to start working from home, complete with all-new challenges both for you and the technology you use.

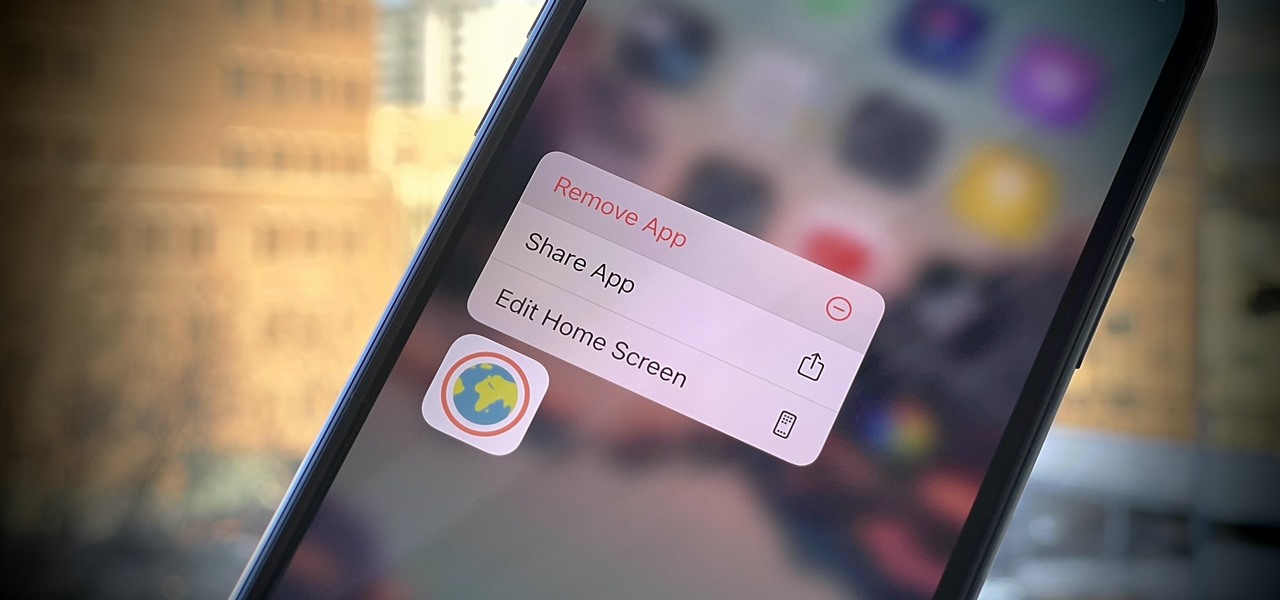
The benefit of going all-in on the Apple ecosystem is that your stuff is connected across all of your Apple products. That said, I really don't need every app I download on my iPhone appearing on my iPad, and vice versa. That's why addressing this setting is crucial for maintaining some level of order across your multiple iOS devices.

There's no better time to reset, improve yourself, and develop new skills than at the start of a brand new year, where you're stuck at home with nothing better to do. Thankfully, this amazing deal on The 2021 Career & Self Development Master Class has come at a perfect time. Right now, it's on sale for just $39.99 — that's a whopping 98% off the regular price of $2,000.

The focus on augmented reality over at Apple is, so far, restricted to the iPhone and the iPad. But if some of the most reliable analysts in the business are to be believed, we'll probably see some kind of AR or VR wearable from the company later this year.

Have you ever admired those individuals that get so much accomplished in a day and wonder how the heck they do it? Now's your chance to learn their secrets. The Productivity & Motivation Master Class Bundle brings you everything you need to life-hack your way into leading a more productive lifestyle at home and work.

Google, you have something that I want. You may think you have some idea of what you are in possession of, but you do not. In a few moments, it will be mine...and it can be yours, too, dear readers.

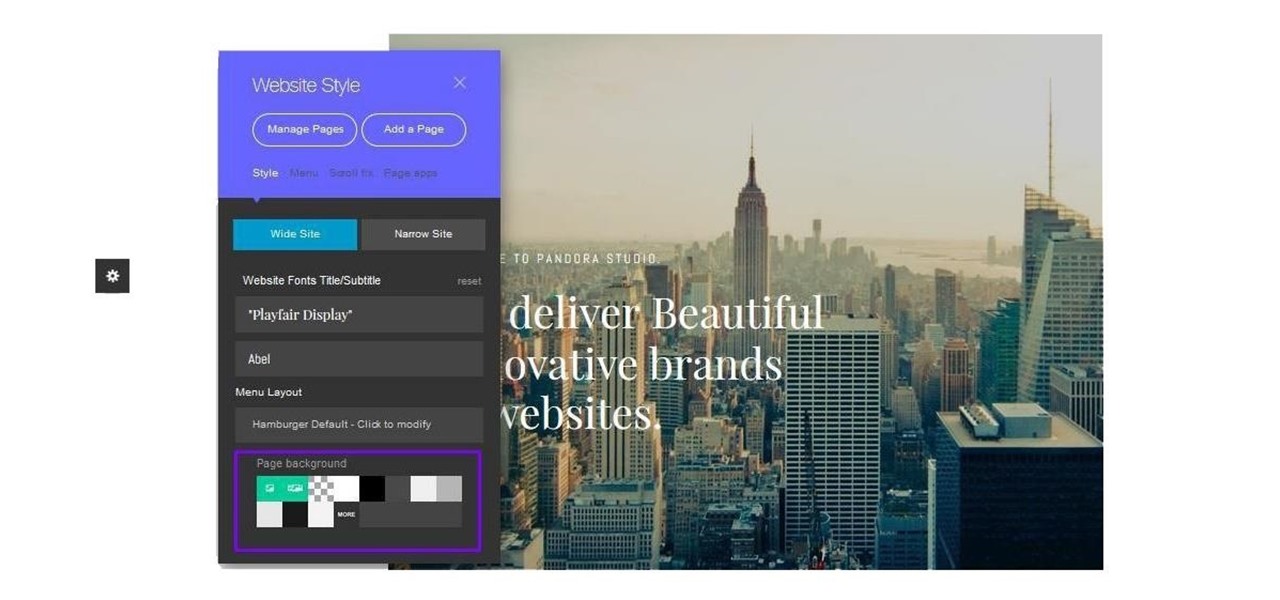
Cultivating a strong online presence can have a huge impact on your employment prospects or help you get that dream store up and running in no time. Whether you're looking for work or building a brand, being able to create and maintain a professional website is essential in the modern workforce.

With over 164 million adults in America playing video games — there are only 209 million adults in the country — this industry is one of the hottest around. Game developers and designers are always in need.

Between sending iMessages, jotting down notes, and crafting emails, you do a lot of typing on your iPhone. No doubt, you've been in the middle of an important task when everything comes to a screeching, obtrusive halt, where a rogue "Undo Typing" pop-up forces you to close it before continuing with your typing. Don't put up with the BS anymore — here's how to stop it.

Cloud computing has come a long way since the days of simple online storage and server networking. Virtually every major company in the world now relies on complex cloud computing infrastructures to reach customers, innovate products, and streamline communications. Their reliance on advanced cloud computing platforms is only going to grow in the coming years.

If you have a limited mobile data plan on your iPhone, you know how tricky it can be to stay within your given allotment. Large app installs and updates, 4K resolution videos, and photo backups can waste precious data resources in no time. And apps like Apple News, Facebook, Mail, and Netflix eat data like it's candy. But you can nip the problem in the bud by restricting data hogs from your cellular network.

This year, over 2.7 billion gamers will spend nearly $160 billion dollars. That number is predicted to increase to over $200 billion in just three years. If ever an industry had growth potential, this is it.

There are many considerations to make when choosing a web hosting plan. Storage space, performance, security, and reliability all matter. The cheapest option isn't always the best idea.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.

AirPods are starting to show up everywhere, and with more and more people owning them, it can be fun to make yours a little more personalized. One way you can do that is by giving your AirPods a unique name, something a bit more fun than "John's" or "Jane's AirPods." With just a few taps, you can change your AirPod's name right from your iPhone or Android phone.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

If you've tossed around the idea of turning your interest in white hat hacking into a career in cybersecurity or IT, now's as good as time as ever to invest some time and energy into improving your skill set.

It feels like just yesterday Apple unveiled iOS 13 to the world, introducing game-changing features like system-wide dark mode and enhanced editing tools in Photos. But WWDC 2020 is rapidly approaching, which means iOS 14 is as well. As it turns out, we don't need to wait for an official announcement to get an idea of what new features and changes are coming to iPhone this year.

With the nation facing a shortage of ventilators for COVID-19 patients and no apparent ramp-up in the production of new ones, engineers, medical resistents, and do-it-yourselfers are sharing plans for homemade versions.

Your smartphone is likely full of COVID-19 news and coronavirus panic. These are scary days, and there doesn't seem to be any end in sight. If you're having trouble coping with the stress and anxiety the virus brings with it, know that your iPhone or Android device can actually help you, rather than just bring you further down.

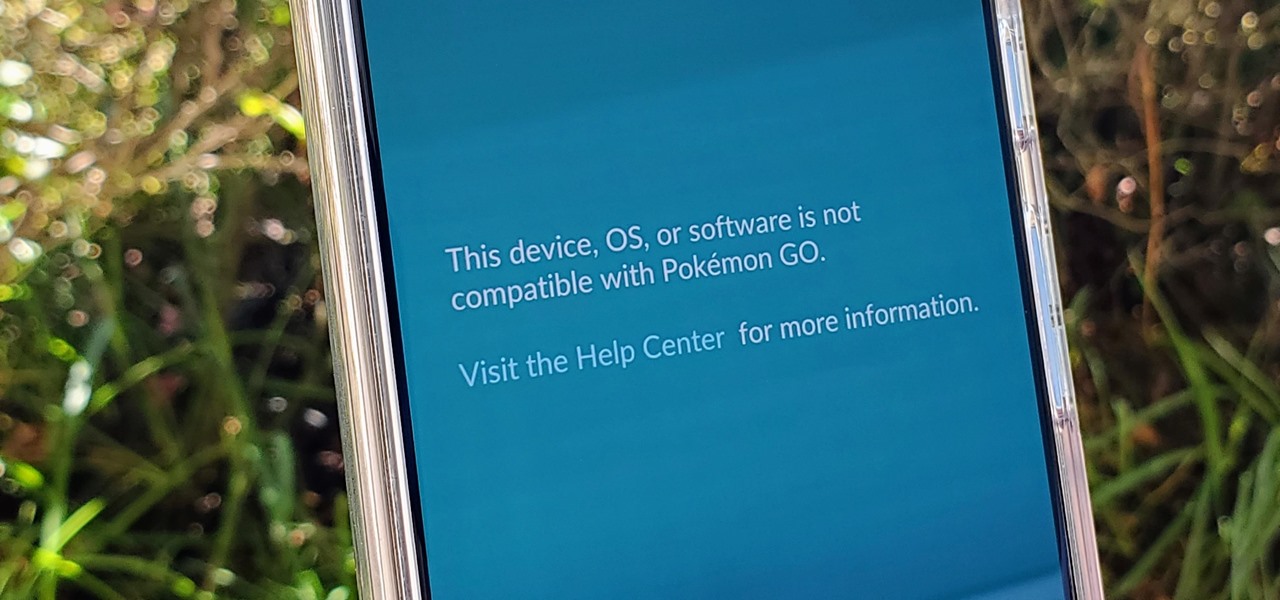
If you're a root user who has played Pokémon GO over the years, then you're probably familiar with the detection methods used to spoil your fun. The game's developer, Niantic, has publicly mentioned their ongoing battle with rooted Android phones and are unwilling to let up. They have a no-nonsense approach to try and keep you from playing, and they've stepped their game up once again.

On March 13, President Trump announced during a briefing in the Rose Garden that Google was building a COVID-19 screening website to help Americans understand if they might have the new coronavirus. If likely infected, the site would also include the location of a local drive-through testing site to visit. So how can you access the screening website?

Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

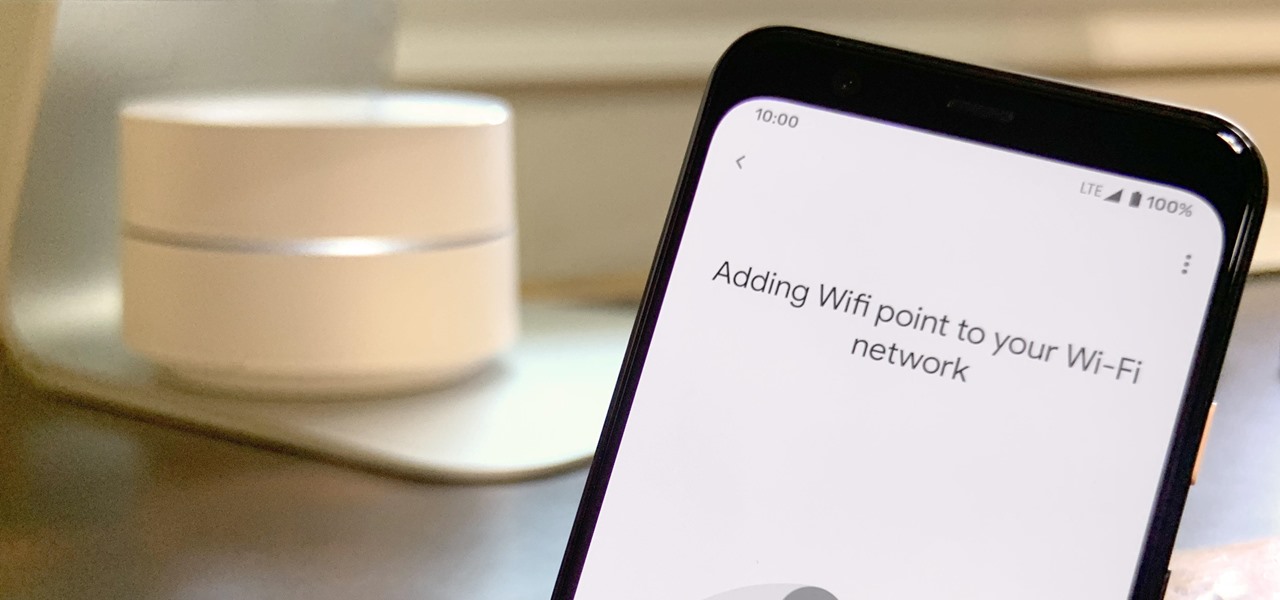
Google is known for merging older products into a new one's ecosystem for ease of use. The transition can take time, and that's the case with the old Google Wifi system now that Nest Wifi is out. Google is working on phasing out the dedicated Google Wifi app in favor of using the Google Home app for all your IoT needs.

Congratulations, you've made it deep into the middle of flu season! If you're reading this, you're either a very smart preemptive sick day prepper, or already in the throes of fighting off a cold or flu situation.

It's pretty much a given at this point that Facebook has a lot of data on us. While you might be conscious of the data you share with Facebook when you post, upload photos, or chat with friends on Messenger, you might not be thinking about all the data it receives from websites and apps you use outside the social media giant. Now, you can actually do something about it.

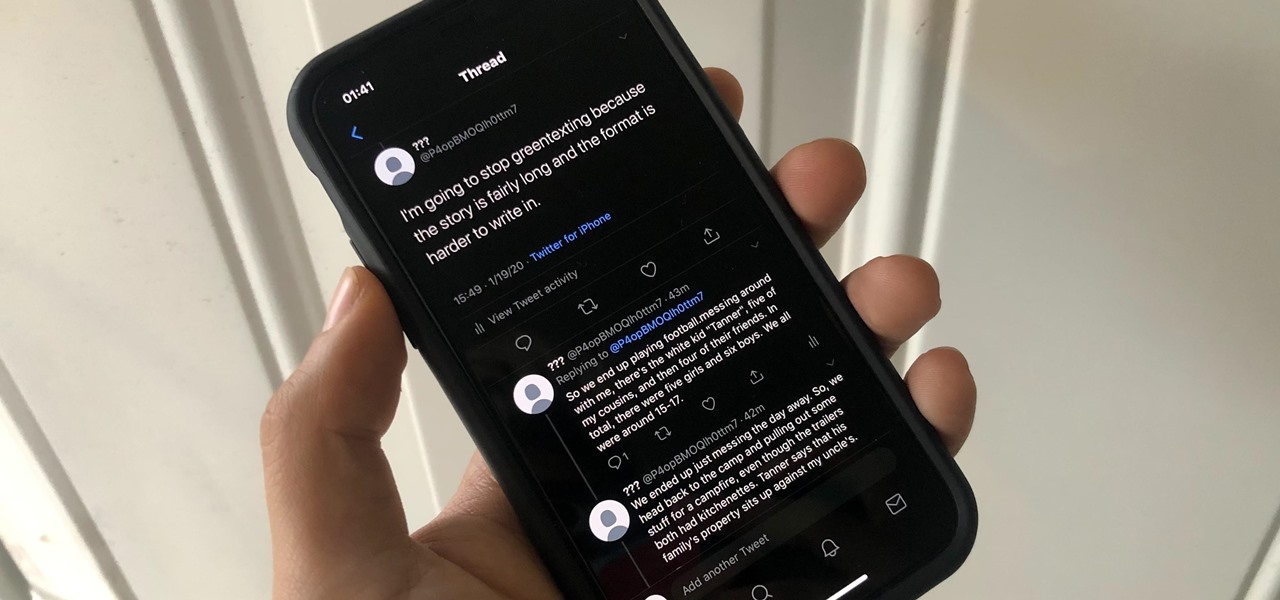
The 280-character limit for tweets on Twitter is double what it used to be back in the day, but it's still not enough to express in-depth thoughts, ideas, commentary, rants, blogs, stories, and the like. These tweetstorms, as they're called, are the reason why Twitter created its threads feature.

In years past, the Consumer Electronics Show (CES) mostly dabbled in the future as far as the long-term vision for augmented reality was concerned. This year, however, objects in the future are much closer than they appear.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

As the year comes to a close, we've invited some of the leaders of the AR industry to take the time to look back at the progress the AR industry has made while looking forward to what's ahead in 2020. A report on the top apps of 2019 — and the decade — also offers some insights on the progress and direction of mobile AR.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

Augmented reality plays a key role in the evolution of adjacent technologies, such as 5G connectivity and brain-control interfaces (BCI), and the business news of the week serves up proof points for both examples.

The recent Oculus conference in California revealed just a bit more about Facebook's secretive plans to compete in the augmented reality space with its own wearable devices.

Apple might not be ready to unveil its rumored-yet-unconfirmed smartglasses. But the iPhone's current depth-sensing hardware is proving to be useful for both smartglasses makers and mobile AR apps.