There's no better way to learn then by visual media, and that's what makes this video lesson on performing a chest exam so great. It's perfect for any future doctor, and great for nursing students to understand the proper procedure for examining a patient's chest. Medical students can easily learn how to perform a general chest exam, because ever step and technique is outlined and shown. A chest examination is very important to determining what's wrong with your patient, and you will be able ...

As a doctor, sometimes it will be necessary to perform a neurological examination of your patient to rule out any neurological disorders. Your objective is to identify abnormalities in the nervous system, to differentiate peripheral from central nervous system lesions, and to establish internal consistency. This is a great video less that outlines the complete neurological exam procedure. It's great for medical students or doctors, and even nursing students can learn a thing or two.

Any patient with pain in the abdominal area will require you to perform an abdominal examination, and this video lesson outlines in great detail, how to perform a general abdomen exam. This is great for any medical student or up-and-coming doctor — even nursing students could benefit from this exam procedure. You'll learn about inspection of the abs, auscultation, percussion, palpation, the liver, the aorta, and the spleen. After watching the full procedure, you should be able to identify the...

The key to being a good doctor is great patient care and thoroughness, and those are exactly the skills you will learn in this video lesson, as you learn to perform a cardiovascular examination on your patient. This is a great, step-by-step resource for the proper examination procedure. Every medical student should know these techniques, and nursing students could benefit from this knowledge, too. Every cardiovascular exam should include inspection of the pulse, blood pressure, carotid pulsat...
Whether your training to be a doctor or a nurse, there is no doubt that this video lesson will help you better understand the procedure for musculoskeletal examinations. Musculoskeletal exams rely exclusively on inspection and palpation and tests using a combination of those techniques. The main purpose of this exam is to identify in your patient any signs of musculoskeletal disease, by way of pain, redness, swelling, warmth, deformity, and loss of function. Watch this video to see the entire...

One of the most important considerations you should have when getting your hair cut is your face shape. Round shapes in particular look good with long, face framing layers and angles, as can be created with a side part.

In this video tutorial, Chris Pels will show how to read, write, and delete cookies in an ASP.NET application. First, learn the basic operations for manipulating cookies. Then learn approaches to storing multiple values in a single cookie using name-value pairs called subkeys. Next, learn how to limit the scope of cookies to a particular application domain or folder. See how to modify values and expiration dates in existing cookies and how to delete an existing cookie. In addition, several co...

In this ASP.Net video tutorial, Chris Pels will show how to use nested master pages to create individual master pages that represent different standard content layouts for a web site. First, see how several major commercial web sites use a standard set of content layouts. Next, see how to nest a master page within another master page, and use the design time support in Visual Studio 2008. Then, learn the considerations for establishing a “page architecture” which represents the major types of...

The Real HT Info Podcast assembles a computer that has all the cooling and noise considerations to make an admirable HTPC. If you've ever wanted to build your own computer, this is a good place to start.

In this video tutorial, Chris Pels will demonstrate how to create a custom user control in ASP.NET that can be used throughout a web site or across many web sites. Start out by learning the basics of creating a user control that will be used in multiple pages including validation, controlling formatting using style elements, and loading/saving data for the user interface elements. Throughout the video considerations for building user controls that can be easily maintained and used across mult...

For both the bride and groom and the guests, beach weddings are a little messier to deal with. And when it comes to dressing and getting your hair and makeup ready, there are the additional considerations of practicality (you're going to be trotting on sand, after all) including how to do your hair so the wind won't whip it into a frizz cloud and how to apply makeup so it won't all slide off before the "I Do."

See how to spin images using Blender. First, you'll see how to use the UV-Textured plane rig and physically rotate the mesh. Next, you'll see how to use Nodes, and then the Sequencer. This clip discusses Orthographic camera scaling, animation, and considerations about clipping. Whether you're new to the Blender Foundation's popular 3D modeling program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free vi...

Scott from Spring Hill Nursery with Step by Step Gardening teaches you some basics about hydrangea plants. He talks about how to take care of the plants, how to ensure blooming, and some planting considerations. Hydrangea plants need at least five hours a day in order to bloom so they should not be planted in very shady locations. The blooms can be pink, blue, green, or white, depending on the variety and soil conditions. The blooms can be used in bouquets, or dried for use in crafts. The pla...

Microsoft is bringing its developer incentive challenge Dream.Build.Play. After a five-year hiatus, Microsoft has announced the 2017 edition of the game development contest with the largest prize pool yet of $225,000.

Kids love sports drinks, but are they healthy for them? This video answers that question, and dissects all of the information pertaining to the diet, nutrition and metabolism of a child playing sports. Healthy eating is important for any sports player, but there are some special considerations for young children. Variety is important, but you need about 40 different nutrients to keep the kid playing well. And believe it or not, chocolate milk is actually one of the best recovery foods.

Nothing has stopped you from taking a screenshot of a funny moment in a FaceTime video call before, and nothing probably will. But screenshots are old news. Apple has made it even easier to take capture FaceTime moments on your iPhone, and the results are more lively.

Two books were presented as suggested reading. One was by Bob Katz: Mastering audio; art and science. The other was Bob Alginski: the Audio Mastering handbook. Mastering takes a collection of songs and makes them sound like they belong together by making certain technical changes. The project page in Studio One is where the mastering is done. Drag in your sound content that you will be working with. Make sure you have the most recently updated version. If you are using multiple tracks, you mu...

Successful public speaking is a product of numerous considerations. Become a successful public speaker with tips from an award-winning speaker in this free communication video series.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

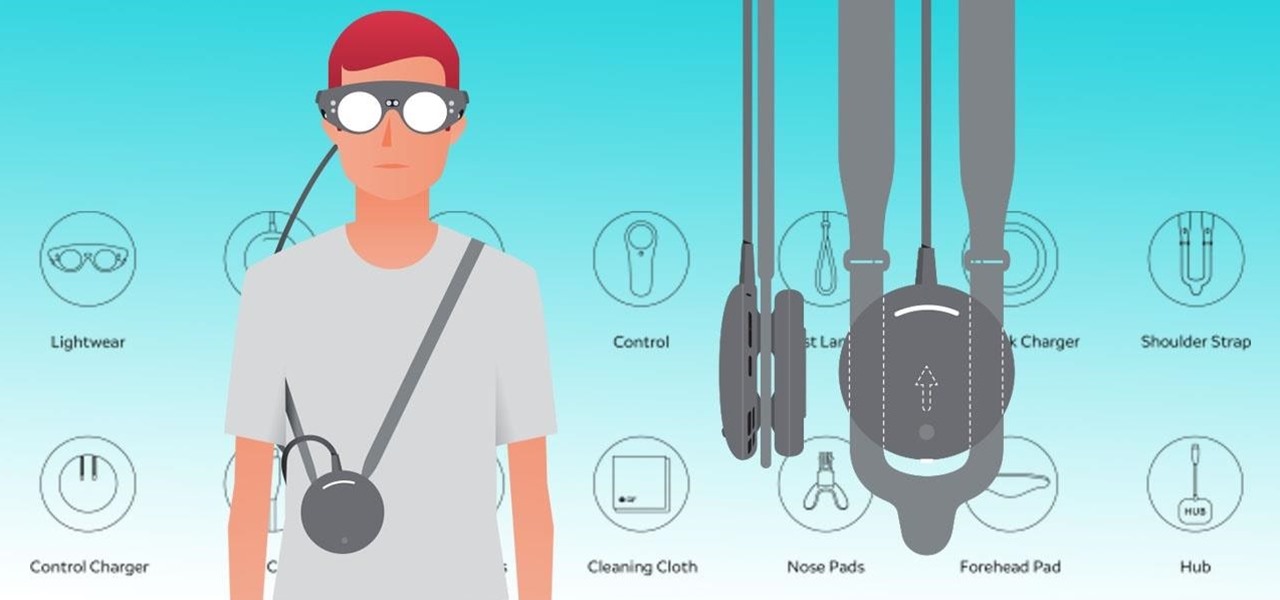
Smartglasses maker Vuzix made a big splash at CES 2018 with the inclusion of Amazon's Alexa voice assistant among the AR superpowers of its consumer-centric Blade smartglasses.

To build hype for the HoloLens 2 among developers, Microsoft is borrowing a page out of Magic Leap's playbook.

Adding water features to your garden can help to create an enviroment that more closely resembles nature. The sound of a trickling fountain can make your garden feel more peaceful and relax. Paul Tamate, a leading landscape designer working with water features and Asian-inspired garden designs in San Francisco says, "design spectacular water features as the centerpiece of gardens that serve as retreats from modern life."

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!

On Wednesday, in addition to uploading another batch of videos from its L.E.A.P. conference to its YouTube channel, Magic Leap also launched a new video series for developers called Spacebar.

From its official launch back in September, iOS 11 has been equal parts revered as it has been criticized. Even with all the great, new features we've come to expect from a major iOS update, plenty of bugs and glitches have forced users to overlook the positives. Perhaps that is why, four months later, 25% of iPhone owners are still running iOS 10.3 or earlier.

There are many considerations to make when choosing a web hosting plan. Storage space, performance, security, and reliability all matter. The cheapest option isn't always the best idea.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

A vulnerability in the design of LiDAR components in driverless cars is far worse than anything we've seen yet outside of the CAN bus sphere — with a potentially deadly consequence if exploited.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

In the summer of 1976, 4,000 American Legionnaires descended upon the Bellevue-Stratford Hotel in Philadelphia, Pennsylvania, for a four-day convention. Several days later, many of the attendees experienced symptoms of severe pneumonia. By the beginning of August, 22 people had died. The Centers for Disease Control and Prevention (CDC) estimate that about 180 people were sickened and 29 people died before this mysterious outbreak burnt out.

Mixing water and electricity is extremely risky and potentially lethal, yet that's exactly what I did with the Scariac. In its simplest form, the Scariac is just a glorified version of two wires in a bucket of water, but it's actually one of the cheapest power controllers you can make.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

Now that the Magic Leap One is officially out in the wild, users are already beginning to find out exactly how it works and what it might be useful for in the augmented reality space. But there are still other, more unique questions that remain unanswered.

A new study published by American University demonstrates how Pokémon GO and other augmented reality games can help city governments bring communities closer together.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

Mystery is a tricky thing. Used correctly, it can give onlookers the impression that wondrous and perhaps valuable things are afoot. However, once the veil of suspension of disbelief is removed in any significant way, that same mystery can quickly turn into not just skepticism, but outright anger at what may have seemed like an attempt to dupe trusting onlookers.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.