Cami, theburntmatches, shows us how to unlock all songs on Rock Band! It is a simple way to unlock all the songs in XBOX 360, PS3 or Wii Rock Band . This probably doesn't work with Rock Band 2 (RBII or RB2). This is a simple glitch or cheat code for the guitar hero like game.
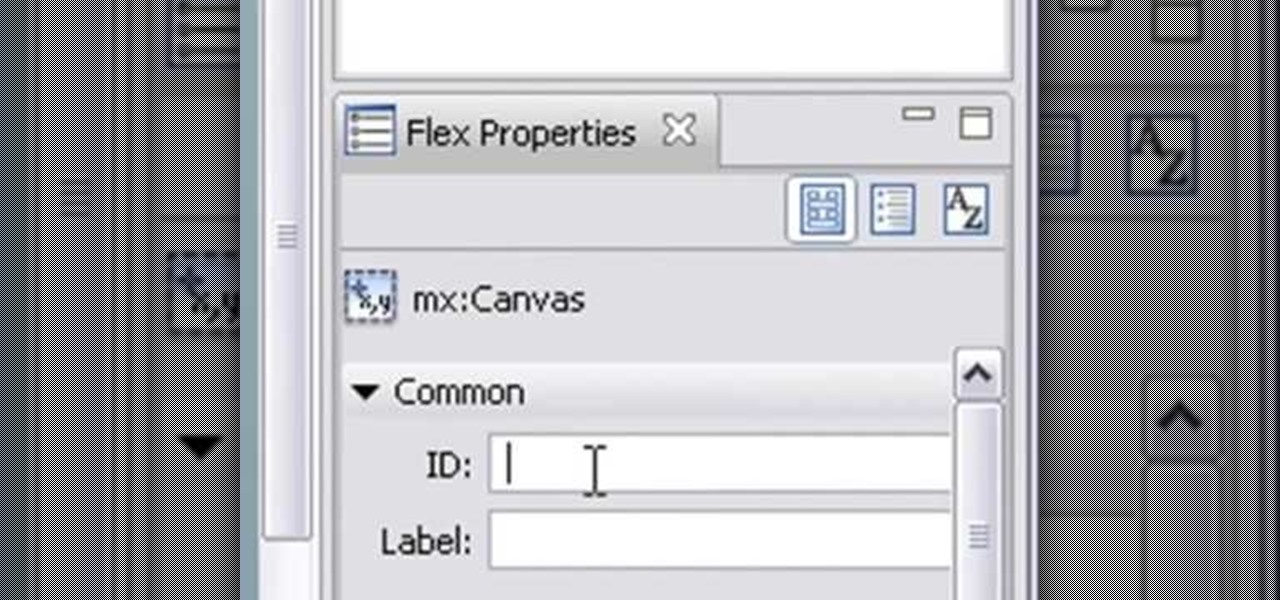
Mike Lively of Northern Kentucky University demonstrates how to create a 3D plotting program for the sinc math function. Part 1 shows how to convert a Flash Package into a Flex application. Part 2 shows how to get the sinc function running and add different textures. Create a cool interactive 3D plotter in thie Adobe Flex Builder 3 and Papervision3D tutorial.
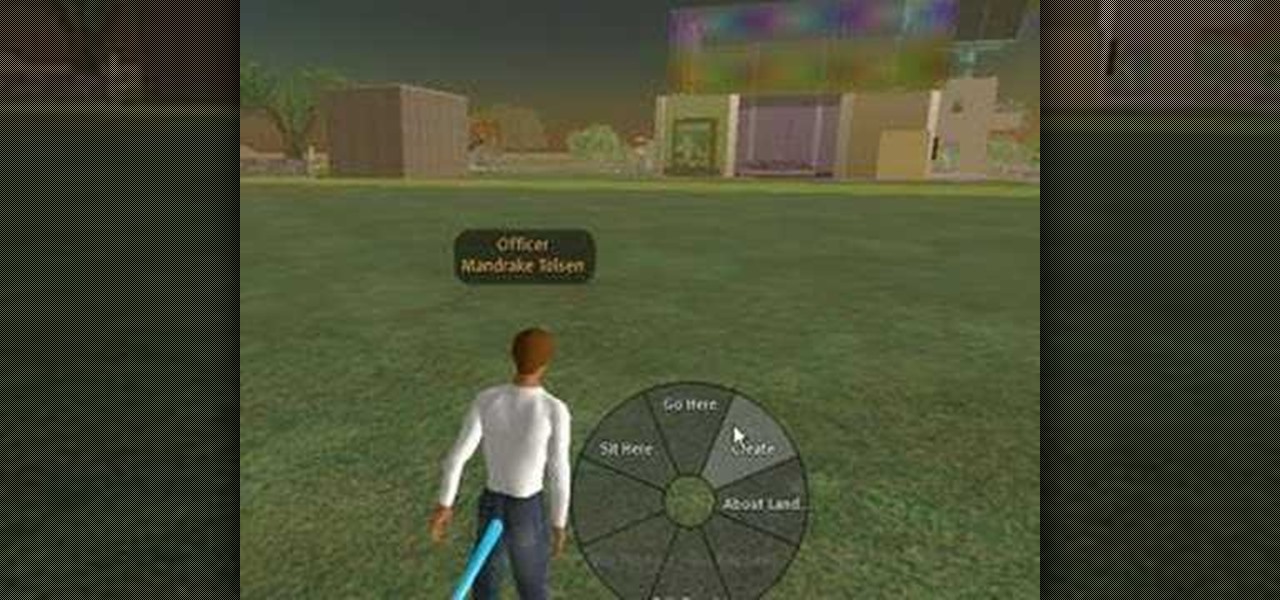
Mike Lively of Northern Kentucky University demonstrates how to build a jet band using Jeff Heaton's jet pack code. What is a jet band? Well, it's like a jet pack but smaller and allows you to go higher than 200 meters when flying in Second Life. Part one shows you how to create the code for the jet band. In part 2, the code is modified to remove the altitude reading below 70 meters.
There are a couple ways to include HTML when coding PHP. Learn two options that work equally well, then decide which one makes the code more clear and concise for you.

You may have seen a "check engine" sign on your car's dashboard when driving your vehicle. Maybe "service engine soon," or just "check". What does this mean if the alarm won't turn off, or comes on when you're driving? Find out in this automotive video tutorial how to read those trouble codes on your automobile.

Looking for some fun cheat codes to get some extra fun out of your game of Grand Theft Auto: San Andreas? These codes are specifically for Playstation users. Make cars fly or float away when they get hit, or enter into Chaos Mode!

If you have created a product that you want to sell, getting a UPC code for it will allow you to track purchases and give your business a more professional air. This video will explain how you go about getting a UPC code and using it to help your business.

Google loves their little Konami Code Easter eggs. The Konami Code is famous among gamers for letting you cheat in video games. The latest one they come up with lets you try it out on Google Docs. All you have to do is open up Google Docs, and type in with the following keys: up, up, down, down, left, right, left, right, B, A, and then enter!

Although most people won't see a penguin in its natural environment, they're still a wonderfully captivating animal that the kids just can't get enough of. So, make sure you and your kids get over to the zoo and check some penguins out, then go home and create some penguins of your own. It could be made in a cold or hot climate! This penguin stick puppet is perfect for an afternoon of fun crafts with the kids. You'll need the following materials:

Like A Flint demonstrates how to quickly make chainmail. First, find heavy gauge wire at a construction site or a craft store. Then, wrap the wire around a dowel or a tube until it forms a coiled spring. Remove the coiled spring from the tube and clip the spring into rings with a pair of wire cutters. Using two pairs of pliers, open up the ring and thread four rings inside of it. Close up the ring. Keep adding rings on top of rings until you achieve a chainmail like design. The process of mak...

This how to video is by a young girl Rida Sharief and teaches you how to construct a hat from simple construction paper. First step, you fold the paper in half and crease the paper with your fingers. Next step, you fold it again in half and crease with your fingers. Next open back up so that the paper is only folded in half. Then, fold triangles inward almost all the way down, but leave space for flaps. Finally, fold the flaps up and you have your own self-constructed paper hat. To wear it si...

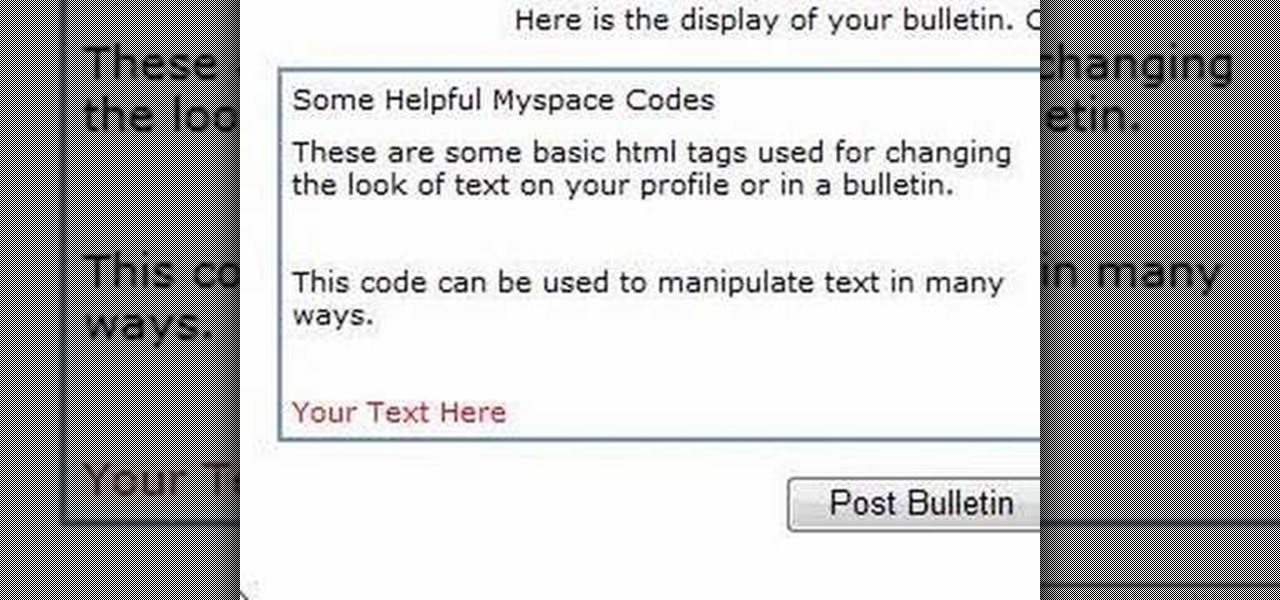
In this Computers & Programming video tutorial you will learn how to alter text on MySpace using HTML codes. Here are a few basic html codes used to change the look of text on your profile or in a bulletin. <b> for starting bold text and </b> for ending bold text. <i> this text will be italicized</i>. For underlining text use the code <u> </u>. <b><i><u> This text will be bold, italicized and underlined </b></i></u>. To change color of your text to ‘red’ use the code <font color=”red”> </font...

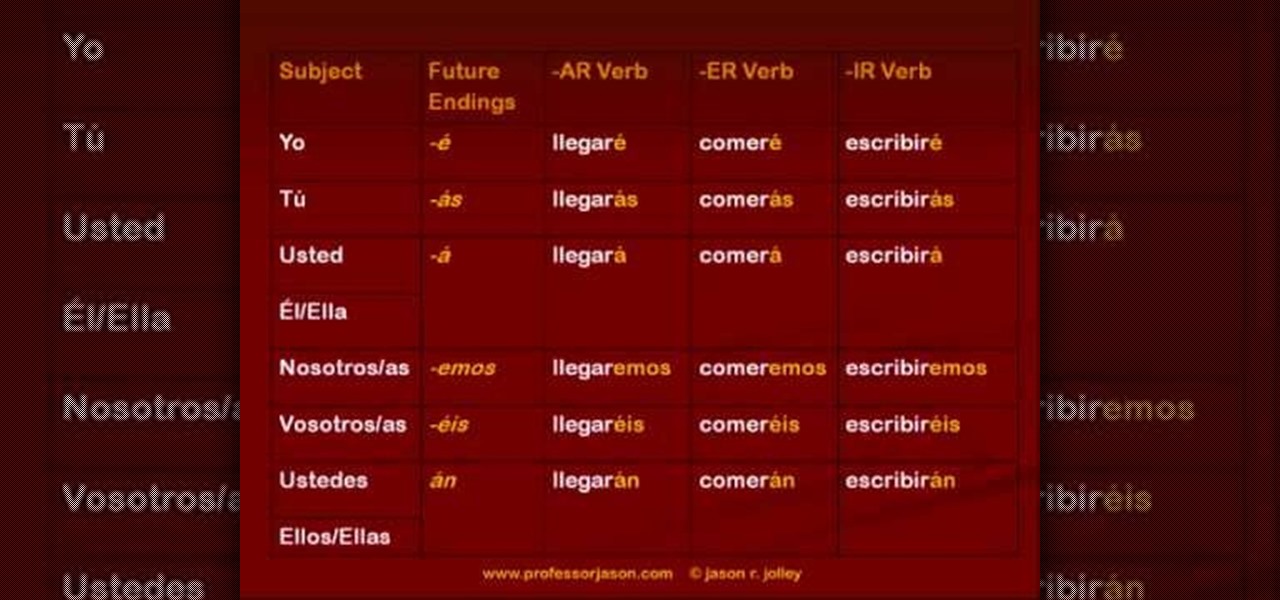
This lively video explains how to discuss future plans in Spanish. Professor Jason explains that it's not that difficult for English people learning Spanish as the same construction is used for 'going to'. There is also a separate future tense, using one set of endings that you simply add to the infinitive, but adding a stress on the final syllable, except for the first person plural. Of course, it's not quite so simple with irregular verbs, which have a special stem which has to be learned b...

Do you need a Venetian mask but can't afford to buy a fancy one? This tutorial teaches you how to make a Venetian style mask by yourself with some basic supplies you can buy from a craft store. You'll need a blank mask or some plaster strips, decorations (like ribbons, crystals, feathers etc.) and basic construction tools like X-acto knives, scissors, and glue. First, you need to lay out the materials, add the trim with hot glue and attach the feathers to the top of the mask. The feathers wil...

K'NEX is one of the most popular construction toys on the market, right next to Lincoln Logs and LEGOs, but what makes K'NEX stand out is the fact that children can build mechanically derived toys. Instead of blocks or little logs, kids use interconnecting plastic rods and connectors, which give them tons of contraptions to build and play with. Today, K NEX has even more possibilities with wheels, pulleys, panels and flexi-rods to make amusement park roller coasters, airplanes, animals, bikes...

K'NEX is one of the most popular construction toys on the market, right next to Lincoln Logs and LEGOs, but what makes K'NEX stand out is the fact that children can build mechanically derived toys. Instead of blocks or little logs, kids use interconnecting plastic rods and connectors, which give them tons of contraptions to build and play with. Today, K NEX has even more possibilities with wheels, pulleys, panels and flexi-rods to make amusement park roller coasters, airplanes, animals, bikes...

K'NEX is one of the most popular construction toys on the market, right next to Lincoln Logs and LEGOs, but what makes K'NEX stand out is the fact that children can build mechanically derived toys. Instead of blocks or little logs, kids use interconnecting plastic rods and connectors, which give them tons of contraptions to build and play with. Today, K NEX has even more possibilities with wheels, pulleys, panels and flexi-rods to make amusement park roller coasters, airplanes, animals, bikes...

This video demonstrates how to import XML code from the Internet into Movie Maker. The video shows you how to find the XML code on the Internet, how to download it, and how to import it into Movie Maker.

Managing your busy schedule just got easier in Entourage 2008 for Mac. Using the powerful Entourage Calendar feature lets you organize your time wisely. The Microsoft Office for Mac team shows you just how to organize your schedule with the calendar in this how-to video.

Being stuck inside for the near future is less than ideal, but at least you have the world of eLearning to sharpen your skills while you kick back on your couch. Case in point, The 2020 Premium Learn To Code Certification Bundle has all the training you need to start coding like a pro right at home, and it'll only cost you $39 today.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

For anyone interested in using cheap, Wi-Fi-connected microcontrollers like the ESP8266, the Arduino programming language can be a barrier to entry. Based on C++, Arduino requires knowledge of more computer science than languages like Python. Fortunately for beginners, setting up MicroPython on an ESP8266 allows anyone to write Python on affordable microcontrollers in a matter of minutes.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

QR codes have become a staple in our everyday lives. Companies use them for everything from marketing promotions to movie tickets thanks to security they provided for these types of transactions. But for years, Android users had to download an app to scan these codes. Well, not anymore.

A Series B round of funding, totaling $30 million, will enable Helsinki-based startup Varjo to launch its industrial-grade augmented and virtual reality headset capable of "human-eye resolution" before the end of the year.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

In case you didn't already know, augmented reality is here. It's no longer just an idea in a cyberpunk novel. And while augmented reality has been around for a long time, the actual technology is finally catching up to the idea.

One inventor wants to bring augmented reality to internet radio and home audio speakers. Meanwhile, a leading consumer electronics company has opened up access its deep learning tools for building augmented reality apps. In addition, analysts examine how augmented reality will impact the design and construction and profile the top developers in augmented and virtual reality.

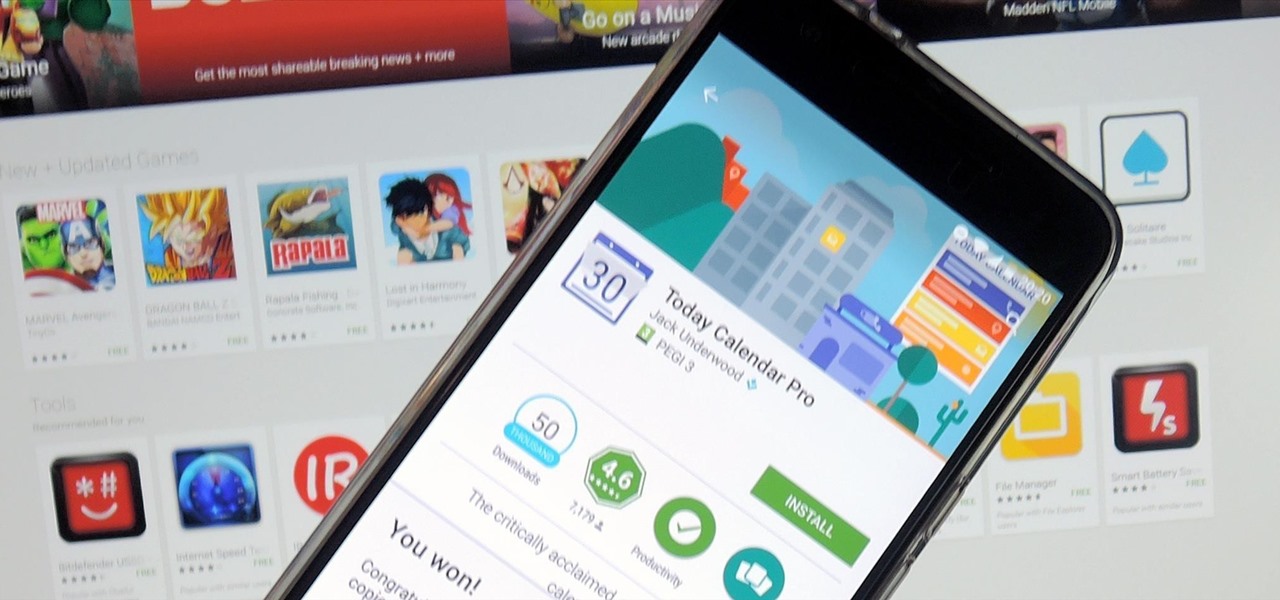
If you're a developer looking to get some exposure for your high-quality app, or if you're a user hunting for new apps and would like a chance to win a paid app at no cost, then Jack Underwood's new Promo Codes app may get you there, which you can install for free from the Google Play Store.

In the last tutorial, we learned how to make functions and how they work on the high level. This time, we will take a peek under the hood again, stare deep into its soul and see its ugliness face to face to see how it works in the lower level.

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

Like Costco's price codes or the tags on your bread, the numerical codes printed on those sticky little fruit and vegetable labels can reveal a lot of information to us consumers. Once you understand the codes, you can look at that little label (also known as PLU, or "price look up" label) and know whether the produce you're about to buy or eat was treated with pesticides, genetically modified, both, or neither. Before we go any further with deciphering the codes on these labels, let's take a...

If you want to embed a video on your website and customize the player so it doesn't look like crap, you've come to the right place:

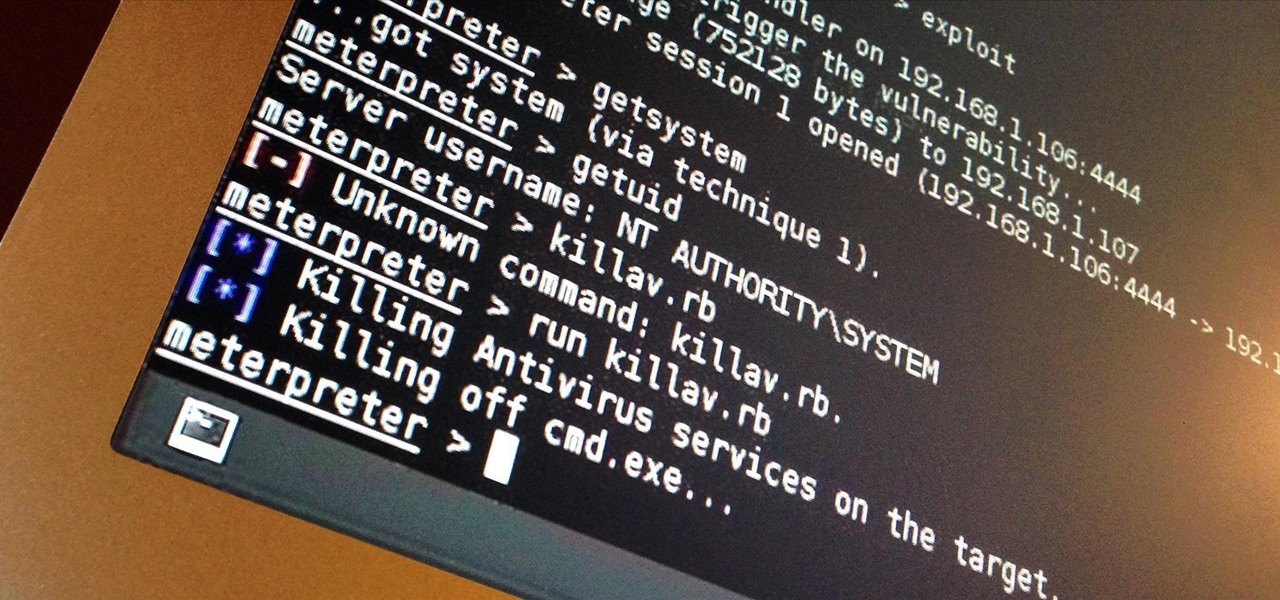
I've done numerous tutorials in Null Byte demonstrating the power of Metasploit's meterpreter. With the meterpreter on the target system, you have nearly total command of the victim.

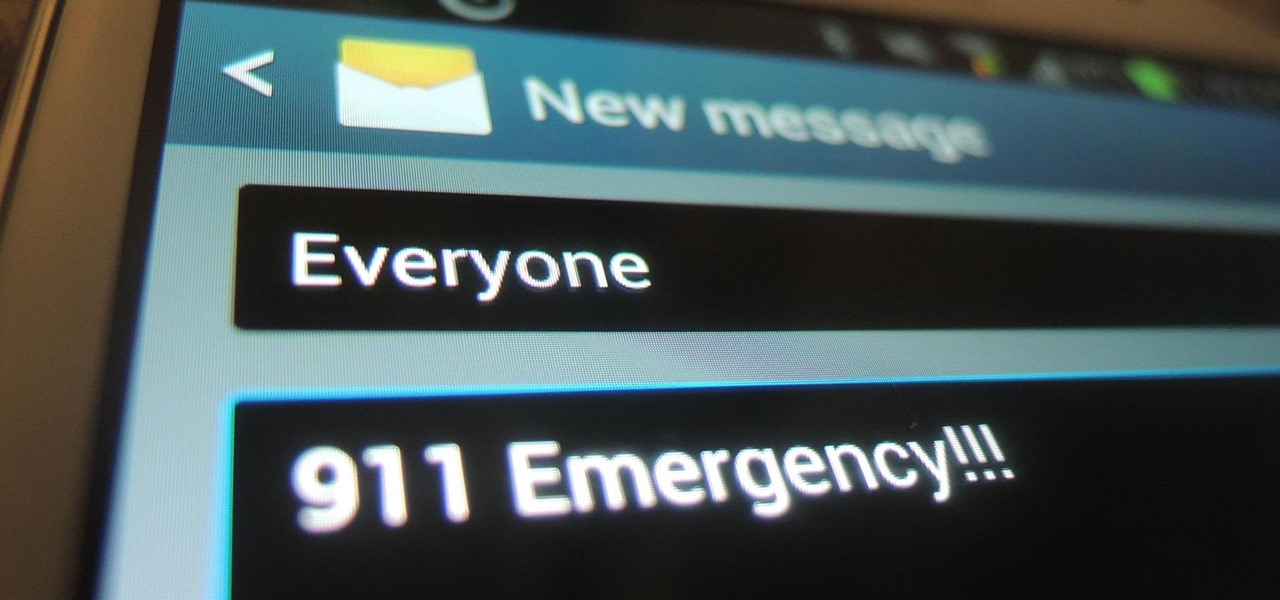
Just because your Samsung Galaxy Note 2 is on silent doesn't mean that the world stops spinning. Emergencies can pop up at any time, even when your phone is put away during a lecture in class, in the library, or at an important business meeting.

It's a real challenge to create exploding targets that can be set off by low velocity projectiles, yet remain safe to handle without risk of ignition during construction.

Cotton candy is a treat generally reserved for carnivals, fairs, and other events that don't come around often enough. Through some clever construction and about $45 in materials though, you can have all the sugary substance you could ever want with this awesome DIY cotton candy machine. All you'll need to construct your own are two dollar store stainless steel bowls, a fan motor, a few odd screws and bolts, a drill, and a propane torch. Check out the tutorial video below. As an added bonus, ...