While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Hello, budding augmented reality developers! My name is Ambuj, and I'll be introducing all of you Next Reality readers to the world ARKit, as I'm developing an ARKit 101 series on using ARKit to create augmented reality apps for iPad and iPhone. My background is in software engineering, and I've been working on iOS apps for the past three years.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

An awesome new feature appeared in iOS 11 that lets you easily share your Wi-Fi password to anyone else with iOS 11 or higher just by tapping "Share Password" on your iPhone when they try to connect to the same network. However, if your friend is using Android or another mobile OS, this feature doesn't help at all — but there's still an easier way than dealing with long, complicated passwords.

A massive leak appeared the web today, and it's got some huge security implications for every iPhone on the market. On the plus side, it also has some potential for enabling deep-level modifications and jailbreak tweaks.

As interest in augmented and virtual reality continues to grow, so does the need to bring objects from the real world into virtual space. With that, there's also now an increased need for solutions that bypass the time-consuming process of producing handmade 3D models.

If you've received a spam message in Signal Private Messenger, you know that anyone can contact you as long as they have your linked phone number. But when it comes to the people you're actually trying to have a private conversation with, how do you know it's really them?

Open your Spotify app, search for an artist, view its "Spotify Code," and display it to that friend lurking over your shoulder. Sound familiar? Probably not ... yet.

Customer service just got a lot more interesting. Construction equipment manufacturer Caterpillar just announced official availability of what they're calling the CAT LIVESHARE solution to customer support, which builds augmented reality capabilities into the platform.

When developing for the HoloLens, keeping a constant 60 fps (frames per second) while making things look beautiful is a challenge. Balancing the processing power to display complex models and keeping the frame rate where it needs is just a straight up painful process, but a solution seems to be on the horizon.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

This is a little c++ program that I thought would be handy in the future. Although, I apologize in advance for any errors in the code since I haven't had the chance to compile it yet. Anyway, please if you are a script kiddie please do me a favor and at least read this article fully. :)

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

With the explosive popularity of both Thor himself and The Avengers, Thor is an obvious good choice for a Halloween costume. But you don't have to opt for one of the pricey, pre-made costume choices found in every Halloween store in every city. Instead, craft your own in just a few steps, saving yourself money in the process.

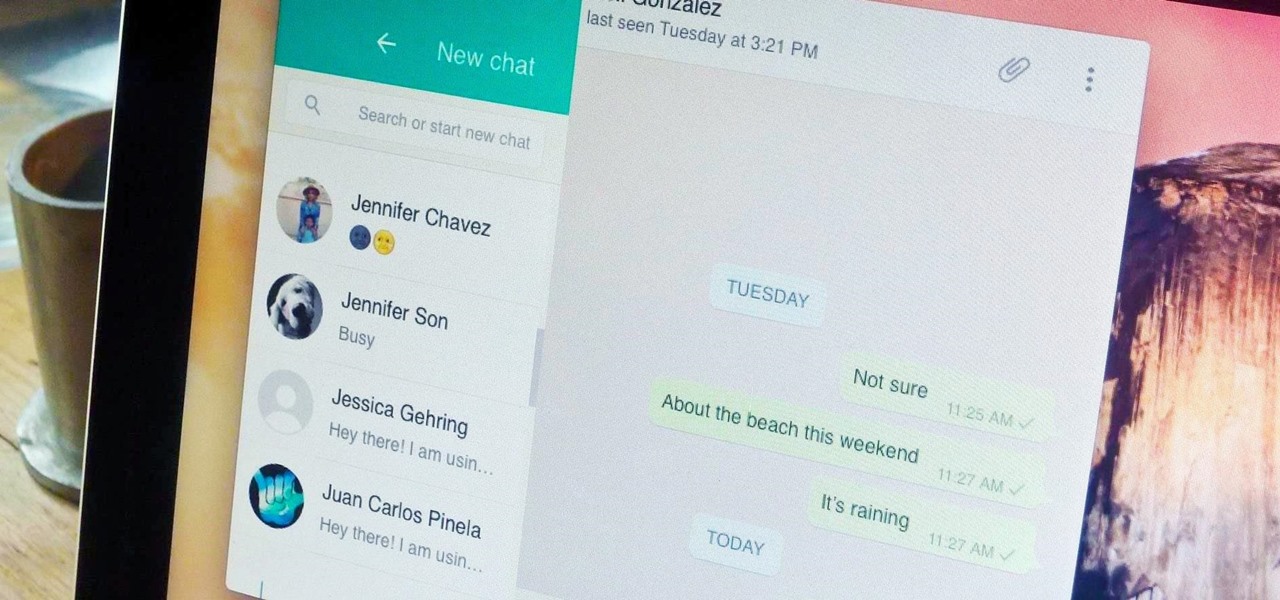
Boasting over 800 million users a month, WhatsApp has quickly become one of the most popular messaging services available today. Thanks to its low price, ease of use, lack of ads, cross-platform functionality, and great features, its popularity is well-deserved.

April Fools may be over, but any day is a good day to prank someone, and the best time to do it is when everyone's eyes are glued to the television.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

LEGOs are more than just a toy for young children— it's an emerging art form combining photography, stop-motion (i.e., brickfilms), and imitative models that portray today's pop culture as it is. It's something visual culture analysts are sure to be studying over the next decade, and Chris McVeigh, from Halifax, Nova Scotia, is sure to be studied for his LEGO mastery.

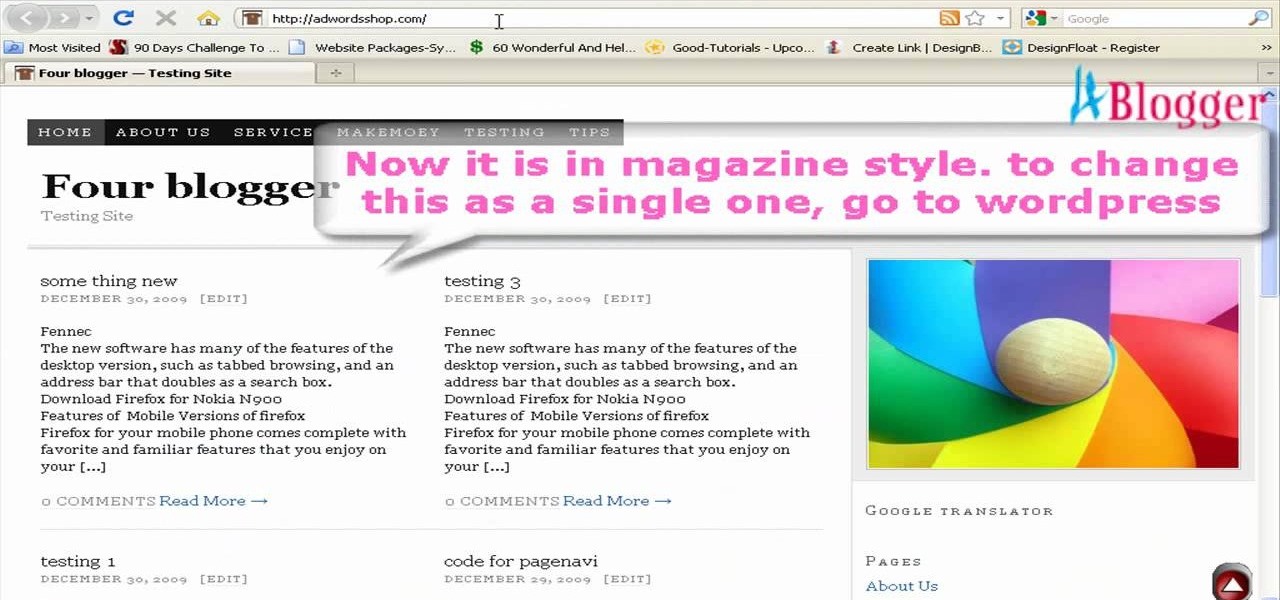
First go to your Wordpress admin and click the "custom file editor" in thesis options. Now copy that code which is showing in the video and paste it in the custom.css file and click on the big green save button. Now select

No downloads or extra programs needed! This video is pure cheat codes, all for playing on Poptropica! You can do fun things like change your skin color, change your hair color and even get the elusive pumpkin hat to wear!

This tutorial for PHP beginners introduces the viewer to the concept of class inheritance. As your coding career takes off, you'll need to know as many ways to work efficently and code with speed to save time and money. Check it!

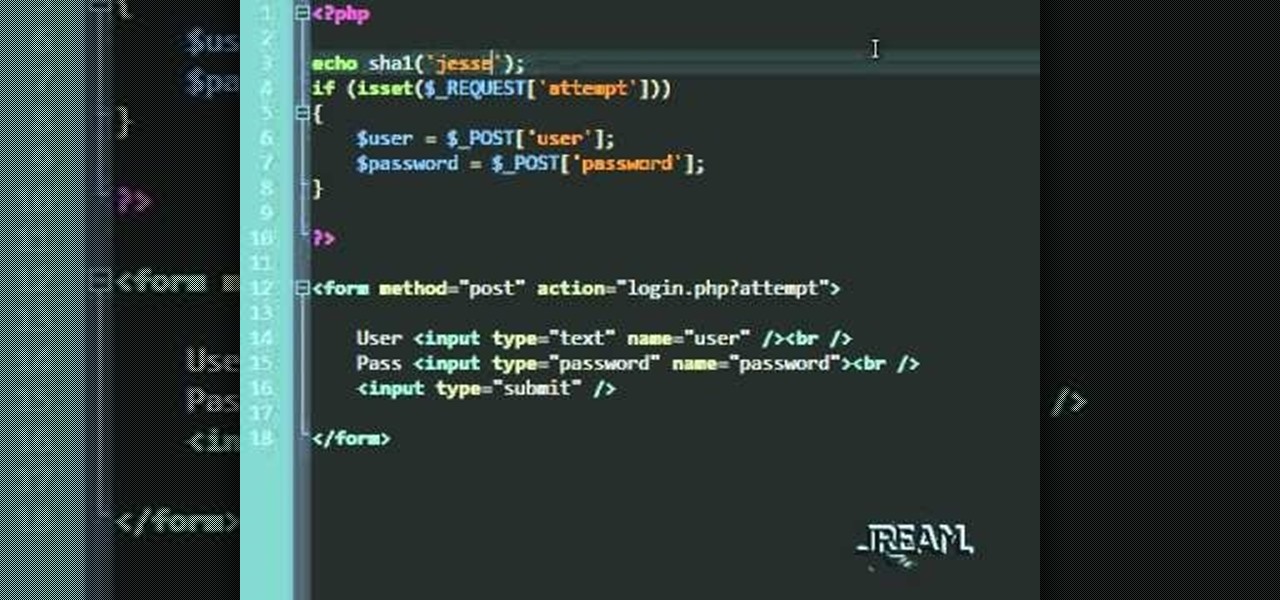
In this tutorial you'll learn about a simple PHP login script that serves to check your MySQL database against a user/password. The code in this video is a quick and dirty procedural code, but it's enough to get you going so you can try it out yourself.

A snippet is a piece of code which you may want to repeatedly use (like a login code). Snippets can also be global, which you can apply to every website you have. This tutorial shows you how to store and use snippets in Dreamweaver.

After running a diagnostics test on a 2002 Jeep Liberty, if you get the code P0442, that means you have an Evaporative Emission Control System (EVAP) leak detected, which is just a small leak, but a leak nonetheless. This video will show you how to smoke test the EVAP leak to find the problem spot inside the vehicle.

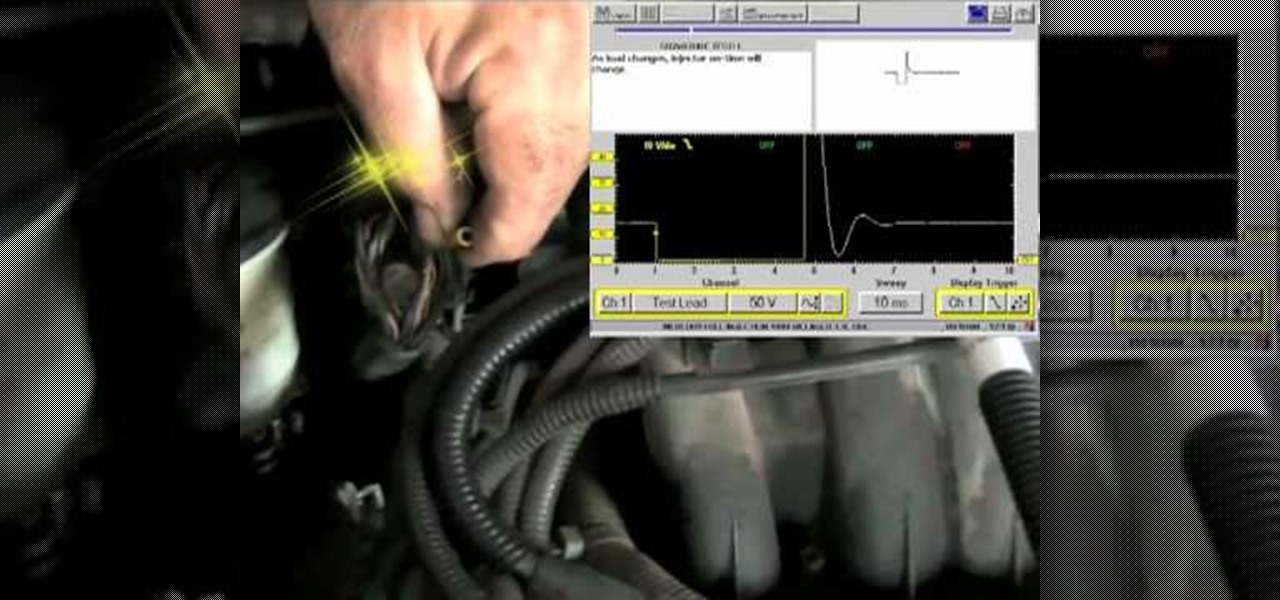
If you didn't find the solution to your misfire problem in this video, then the 1999 Mercury Villager 3.3L might have a code P0305 (Cylinder #5 Misfire). This is great troubleshooting advice from a professional mechanic to help you diagnose the problem. The vehicle is a '99 Mercury Village, 3.3L, with 150,000 miles on it. The chief complaint is the CEL (check engine light) comes on and it runs like it has a misfire. It feels like a steady consistent misfire, which is code P0305. Watch the vid...

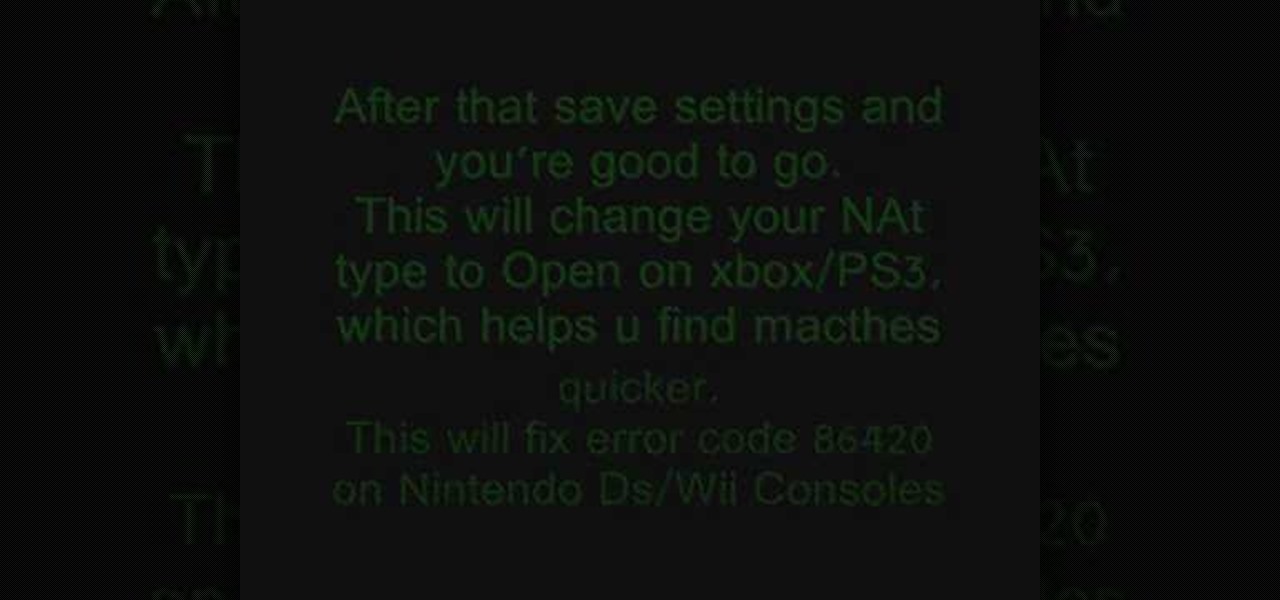
In this tutorial, we learn how to fix error code 86420 and change your NAT type to open. First, go to the website to change the settings for your Linksys router. Next, go to the applications tab that says "applications and gaming". After this, go to port range forwarding, then write in a name next to where it says "application name". Under "start" write the number 1 and under "end" write 6553, then keep "both" marked under protocol. Next, enter in the last 3 digits of your console's IP addres...

Are you a big fan of Japanese anime series, Code Geass? Learn how to draw the main character, Lelouch, from the series with help from Drawing Now. Search WonderHowTo for more videos from Drawing Now to learn how to draw a variety of characters and cartoons!

Google G1 users, want to switch your phone network? In this video, learn how to unlock the Google G1 HTC Dream Phone. All you need to complete this tutorial is your phone and a SIM network unlock pin code.

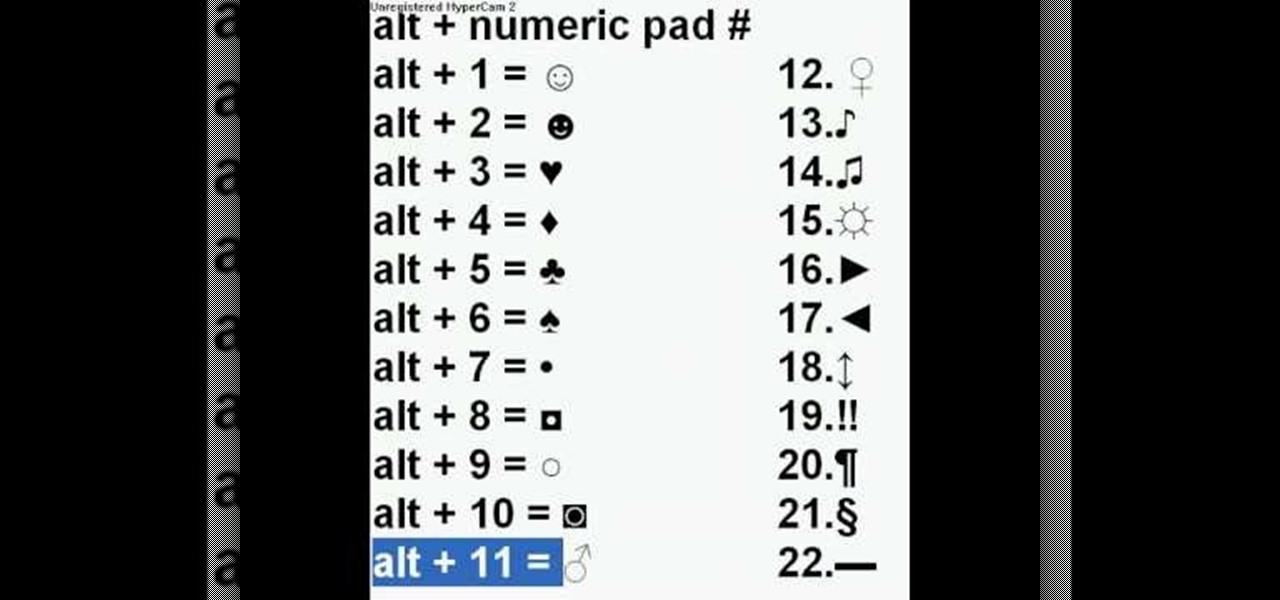
It is possible to add a little extra personality and ting to your facebook, myspace, or most any messaging system online by adding characters such as hearts, smiley faces and many more. With this video you will see the simple alt codes you can use to personalize your messages by pressing alt + a number.

In this how-to video, you will learn how to embed a social or fund raising widget on to your Facebook page. Look for static fbml on the Facebook search function. Click on it and add to page. Next, press add static fbml. Now you are finished. Go to edit page and click edit on the application. Now you can embed whichever code you need to paste into your Facebook page. Do not worry about what the code does, as you do not need to know it in order for it to work. Save the changes and go back to th...

If you're a Visual [blank] programmer heretofore intimidated by the thought of programming for the Linux operating system, take heart: this video tutorial will teach you how to visually code GUI applications with Ruby and Glade.

Before SOAP and REST, there were Remote Procedure Calls. Ruby on Rails ships with native RPC support and this screencast programming tutorial will show you how to build powerful remote API queries with 3 lines of Ruby on Rails code!

In this video tutorial, Keith Code walks you through how to set the sag on your motorcycle's suspension. If your sag is too loose or too tight, you can damage your bike and potentially damage yourself. Watch this video to become a pro at setting up your motorcycle.

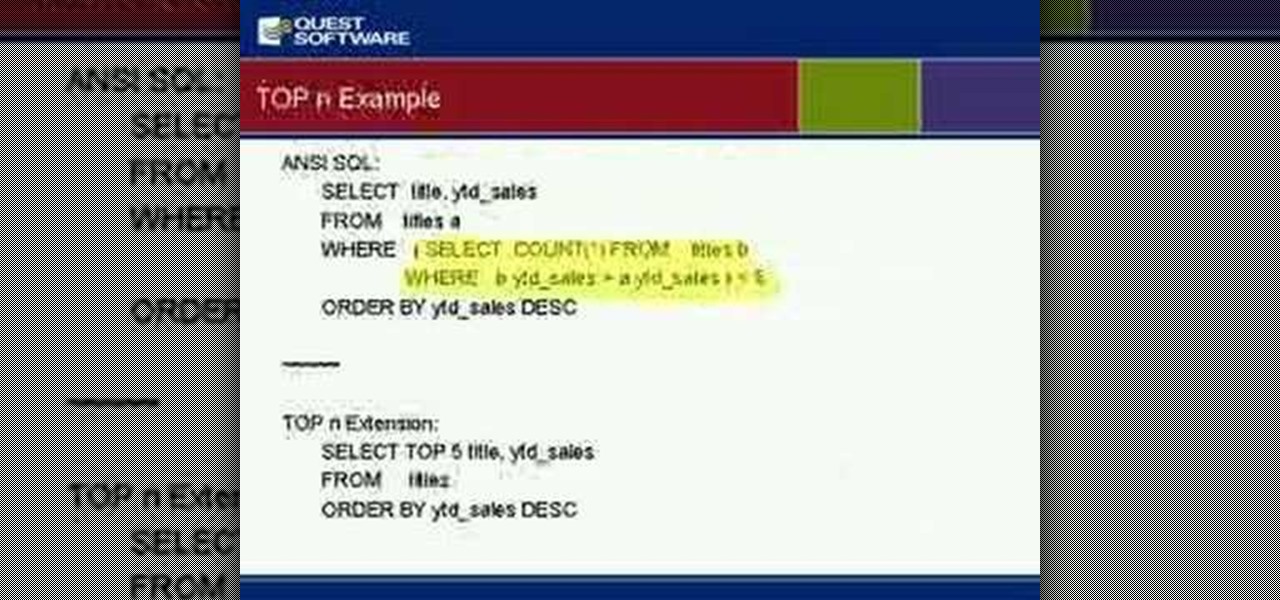
Gain insight into best practices for SQL Server optimization and ways to alleviate many root causes that can impact performance of your SQL Server database. Kevin also will discuss how to manage for planned and unplanned changes, speed time to implementation of your applications and ensure that your databases are running as they should.

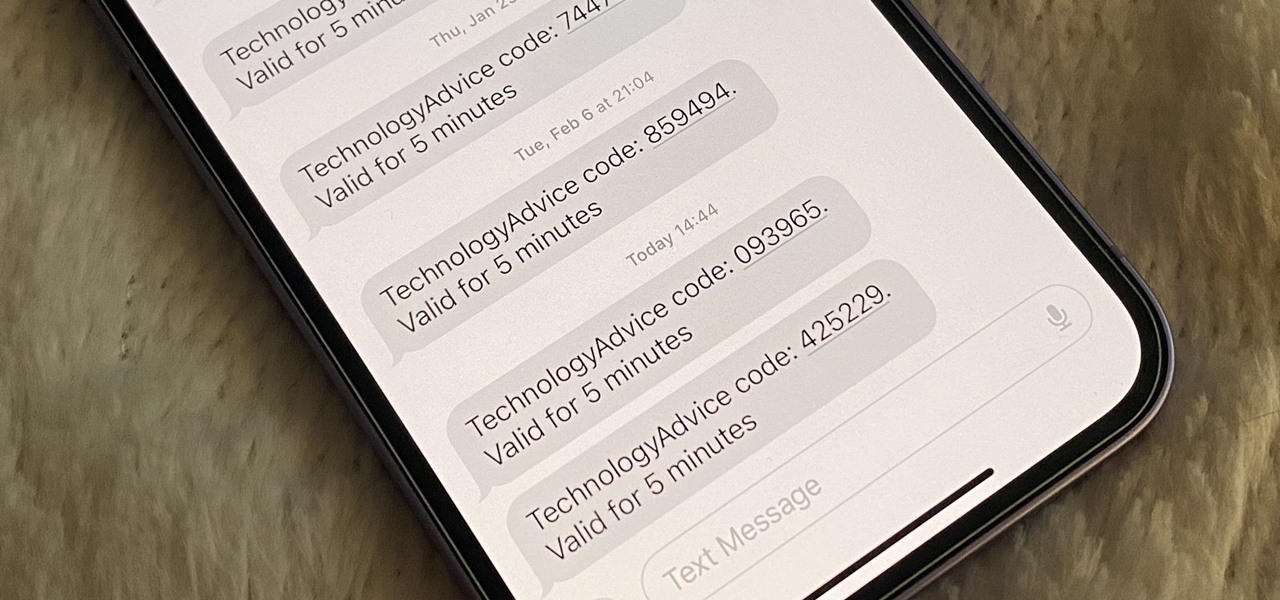
Many of your accounts online likely require two-factor authentication (2FA) or two-step verification (2SV) to confirm your identity when logging in, and there's a good chance the second factor or step for each is a one-time email or SMS verification code. If you get a lot of email and SMS codes, it can clutter your Mail and Messages apps with junk if you don't delete the messages after signing in.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

The only thing better than programming MicroPython is programming MicroPython over Wi-Fi. So once you set up MicroPython on a microcontroller and have it on its own power source, you won't need to use a data cable to connect to it whenever you need to interact with it, program it, upload files, or grab data.

It's no secret that the vast majority of Null Byte readers range from beginner to seasoned coding pros and developers. Regardless of whether you're interested primarily in building websites or creating best-selling apps and games, working with a wide variety of programming languages remains one of the best ways to make serious money in an increasingly app-driven world.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.