PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

Three variants of the Pixel 2 have appeared in Google's Android Open Source Project (AOSP) code, confirming various suspicions about which processor will power the Pixel 2.

Google has added some fun Easter eggs to Hangouts that'll give you a few more ways to procrastinate throughout your day. All of them (except for one) work on the web browser version, the Chrome app, and the mobile apps for Android and iOS, and are activated by sending a specific message.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

Apple announced the successor to Mac OS X Mavericks at their Worldwide Developer's Conference 2014, and it's called Yosemite. Named after California's Yosemite National Park, it will be available as a free upgrade from the Mac App Store for everyone this fall.

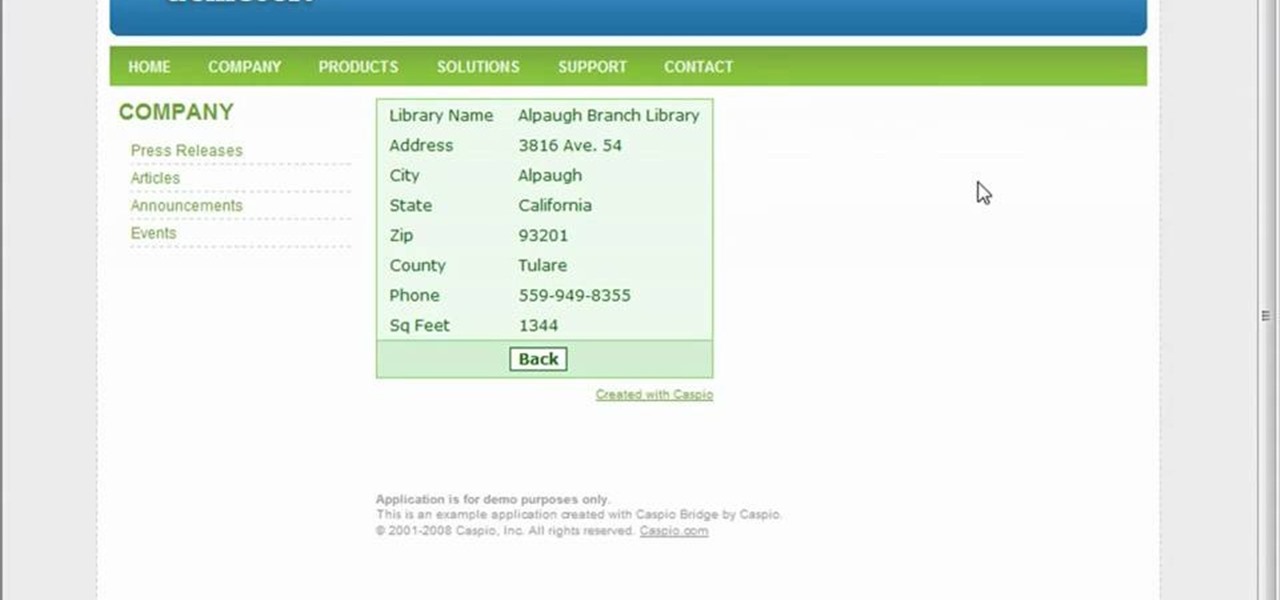
To start off the process of publishing your access database online we first look at a sample MS ACCESS database with typical formats and a online searchable application where users can search by library name or city and get details of the library. There are 3 steps to publish the database. The first step is importing data which can be done through clicking on the file menu and then click on import data through a Microsoft Access Database. Now select the file you want to import through the bro...

This is a great level hack for Pet Society, using, none other than, Cheat Engine. Try this out for yourself and see your levels rise like tides during a full moon close to an equinox.

Read This Must Need flash player 9!!

In this video, we learn how to add rotating banner ads to Wordpress Thesis theme. First, go to your Wordpress admin, then go to the thesis option. Now, click on custom file editor. After this, selection "custom_function.php", then go to the FTP path and open "launch.php". Now a notepad will open, copy the code inside where it says banner ad and past that into your Wordpress multimedia box. now, go to the drop down menu and click view custom code. Now you should be able to see banner ads on yo...

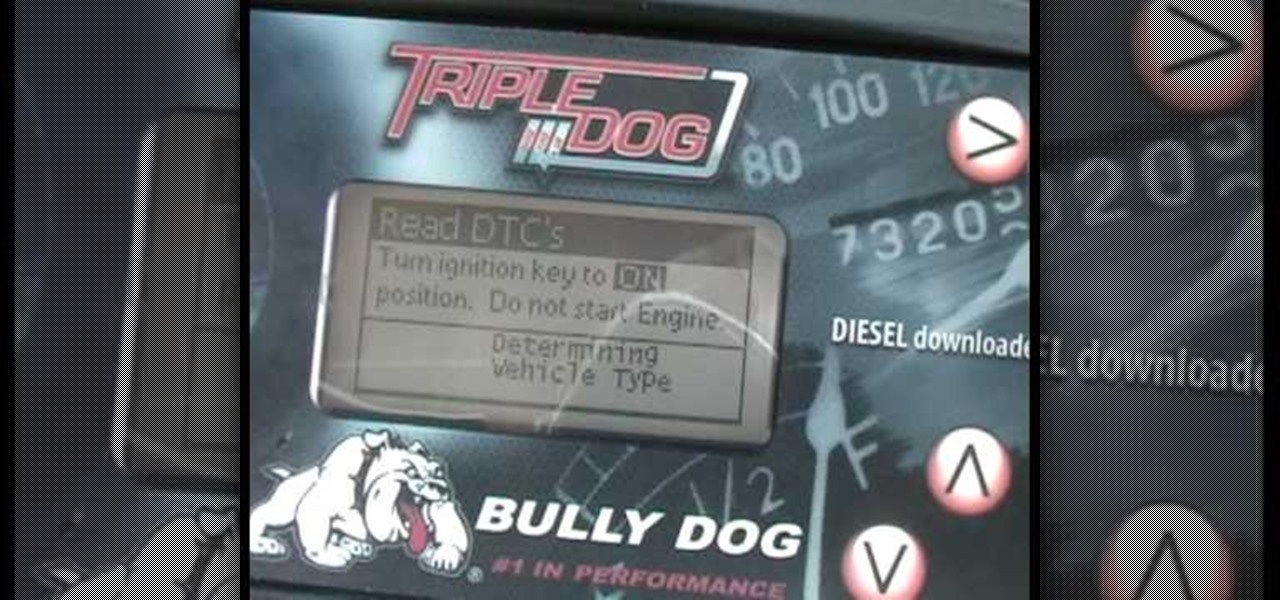
In this tutorial, we learn how to clear the check engine light on your dashboard. This could be caused from an over-boost from the turbo charger that the engine does not recognize. The solution is to grab a tuner device and plug it into the car. Wait for it to power up, then go to the main menu. After this, go to "read dtc's", then find the trouble codes. It will show you what unknown codes are coming up, then you can clear them by pressing the "s" key. Now your light should turn off and you ...

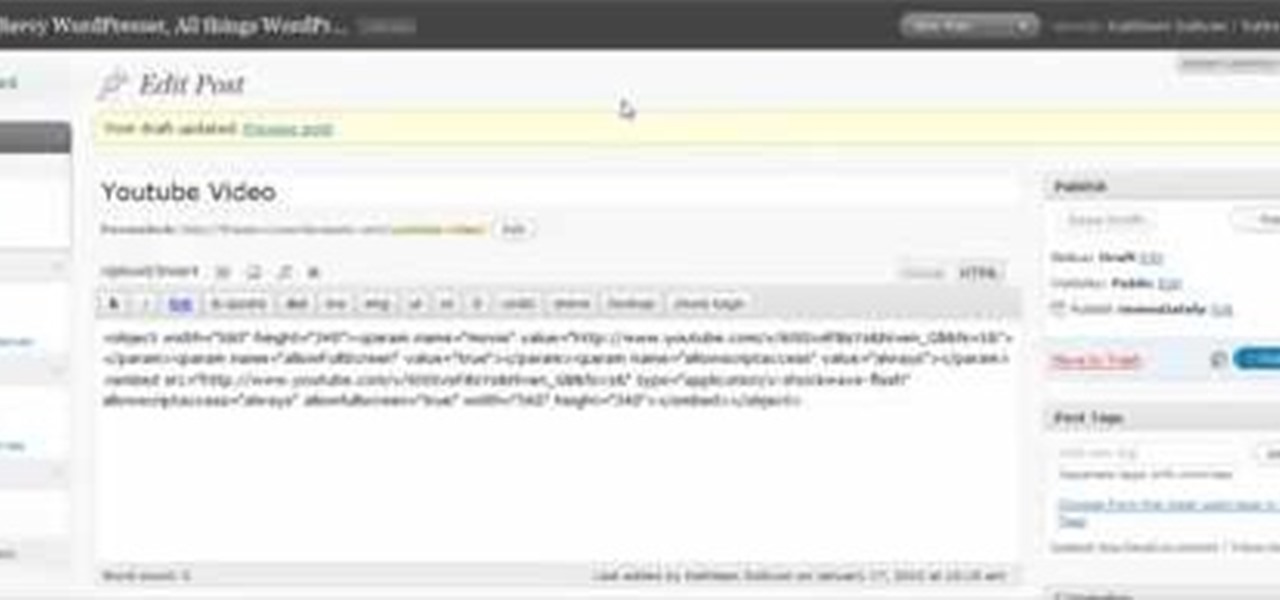
This clip presents a general tutorial on how to work with and embed HTML code into your WordPress posts and pages. Every version of WordPress brings with it new features, new functions and new ways of doing things. Fortunately, the very same technology that allows an open-source blog publishing application like WordPress to exist in the first place also makes it easy for its users to share information about the abovesaid things through videos like this one. Take a look.

This video in the Pranks & Cons category will show you how to create a non-destructive fake virus on Windows. This video is from Tinkernut. For this right click on your desk top, go to new and select shortcut. Now type in this code 'shutdown 's 't 60 'c "this computer is shutting down; save your work", click next. This code is actually for shutting down the computer. But, you type in the name of the short cut as something else, say for example 'songs ' and click next. What will happen is when...

You may have all the tools and people needed for putting up a fence, but something that should not be skipped is coding. Checking the coding and property lines to your place is important for making sure you don't cross into a place that you aren't supposed to be. This can result in bad blood forming and the removal of your hard work. So check out what you'll need to do in order to prevent that, in this tutorial. Enjoy!

In this video, we learn how to connect an Apple wireless keyboard to the iPad. This is great if you need to write something that requires a lot of typing. First, go to "system preferences" then click on "Bluetooth". Once you're in this, make sure the "discoverable" check box is not checked, then highlight your keyboard. In the bottom left hand corner click the minus sign, then click "remove". Now, on your iPad click "settings" then "general" then tap "Bluetooth". Almost right away you should ...

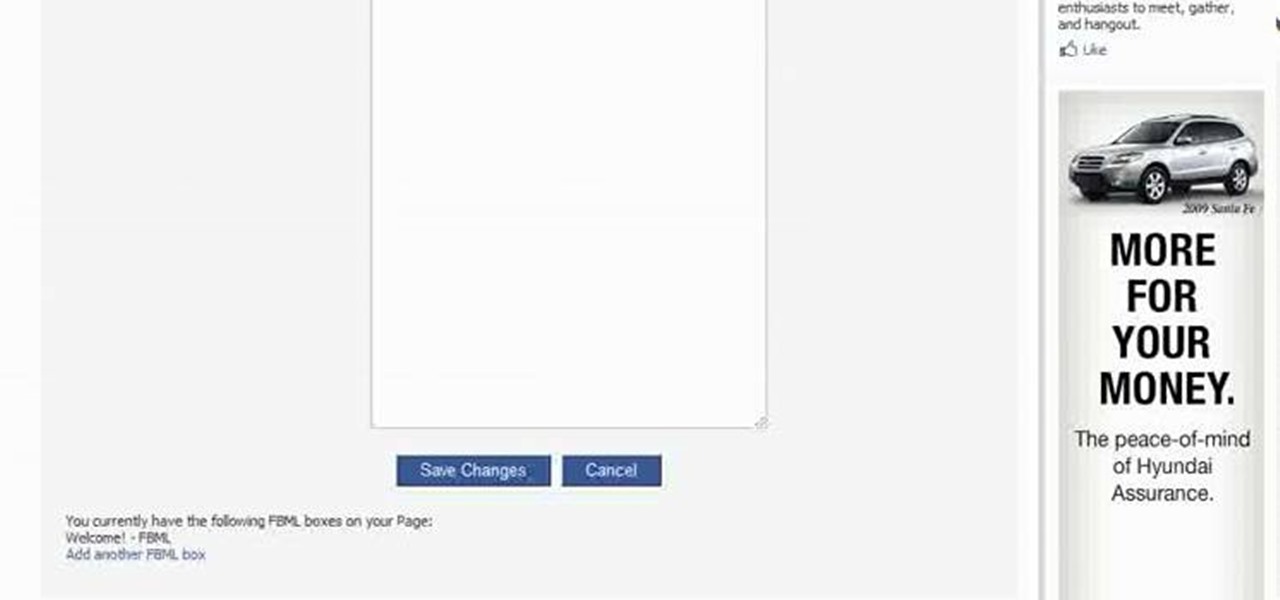
This videos is a tutorial for using custom FBML coding on facebook fan page.The video begins by logging into facebook account.Then go to the search bar at the upper right hand corner and tpe "static fbml" and hit enter.This takes to the application page and click on "add to my page" below the default fbml picture.A window opens up showing a list of user pages and after selecting the page click on "add to page".Close the window and go to your fan page and click on "edit page".This shows a list...

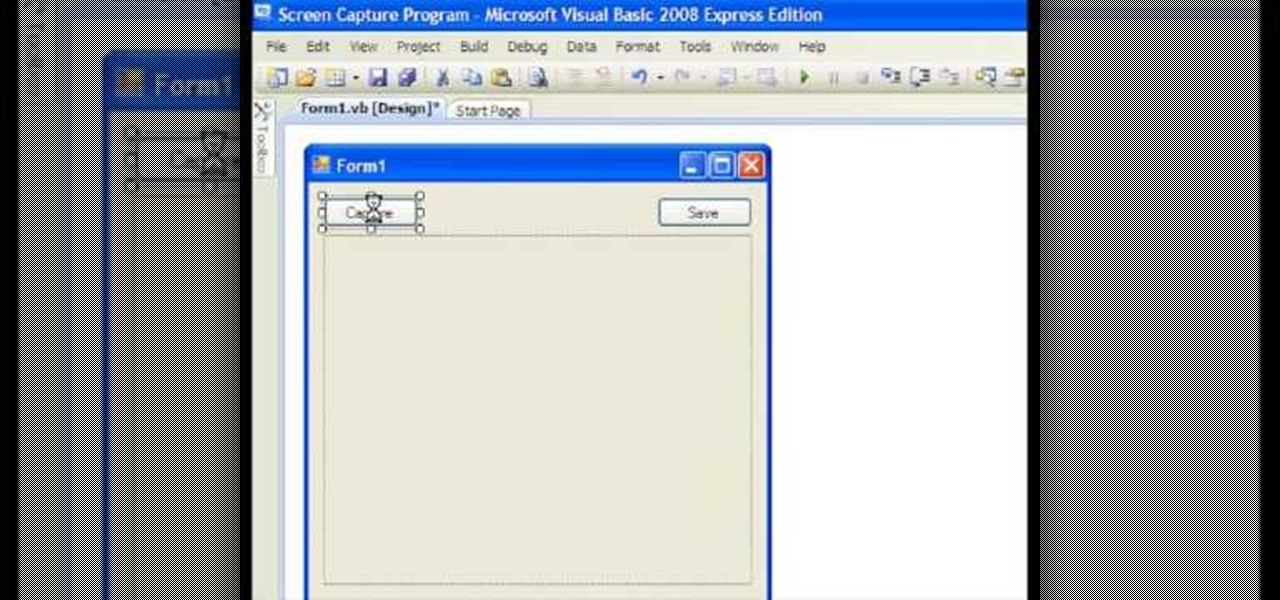
This video shows how to make a screen capture program in Visual basic. The first step to create a screen capture is to open a new project and open a new form window. The second step is to create to temples for either saving or capturing the picture you choose to select. The third step involves following the code structure given by the instructor to enable the correct function for the save or capture button options. The final step is to open the project as a finished work with the correct codi...

Are you curious as to how to jailbreak the 3.0 Beta 3 on your iPod Touch/iPhone? In order for the instructions in the video to work you must own a 1G iPod or iPhone as the 2G will not work. The instructions are very easy to follow and you will be able to access the 3.0 Beta 3 on your phone in no time at all. If you don't know what jailbreaking is it allows iPod or iPhone users to run any type of code on your device as opposed to only running codes that are approved by Apple.

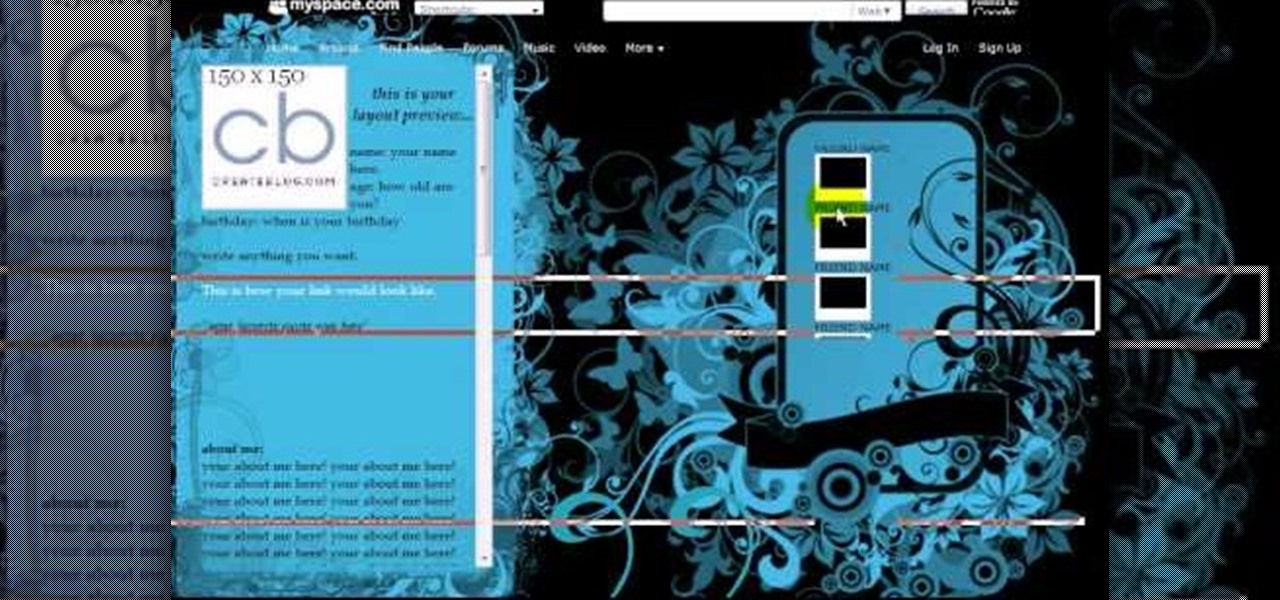
Here we will be making a website page layout for your Myspace account. A very common thing that people find difficult is the alignment of things such as text boxes and other DIV's. This video will demonstrate the proper meaning of alignment, as we have an already misaligned page to visually work with here. -To watch in high quality: http://www.youtube.com/watch?v=ItUhjfqcLo0&fmt=18 -For help with source code: http://www.fileden.com/files/2008/6/12/1956714/1divblueblack.txt -Insert this code t...

This video describes how to increase battery life on most of the LG phones", for that first we have to enter into the service by typing the numbers "##77647269700" and then clicking the call button. Now it will ask for 6 digit "service code" to enter into the service. Just type "000000" as a code and it will enter into the "services" Menu and from the menu click on the "Network Select" and from that choose "Mode Preference", by default "Digital Only Hybrid" mode will be in selected. Now to sa...

This instructional video shows you how to reboot your iPod Touch 2G after shut down. First shut down the device and plug it to a computer via USB. Use the links in the description if you have the newest version of OS X. Put the device in to DFU mode by holding the home and power key for 10 seconds, letting go of the power key keep holding the home key. Download the RSlite folder from the link in the description. Open the terminal, change the directory to the Rslite folder and type the code re...

In Access 2010 you can now create a navigation form (like a home page) for your database without writing a single piece of code or logic! Great for busy people who need to organize their database quickly, but who don't have code writing skills. It's just drag and drop. There are predefined layouts which help you design the form and then simply drag the information you want into the form. Reports can be added and accessed quickly from the navigation form so you can analyze the data simply and ...

The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn how to force a password to be entered in order to run a query.

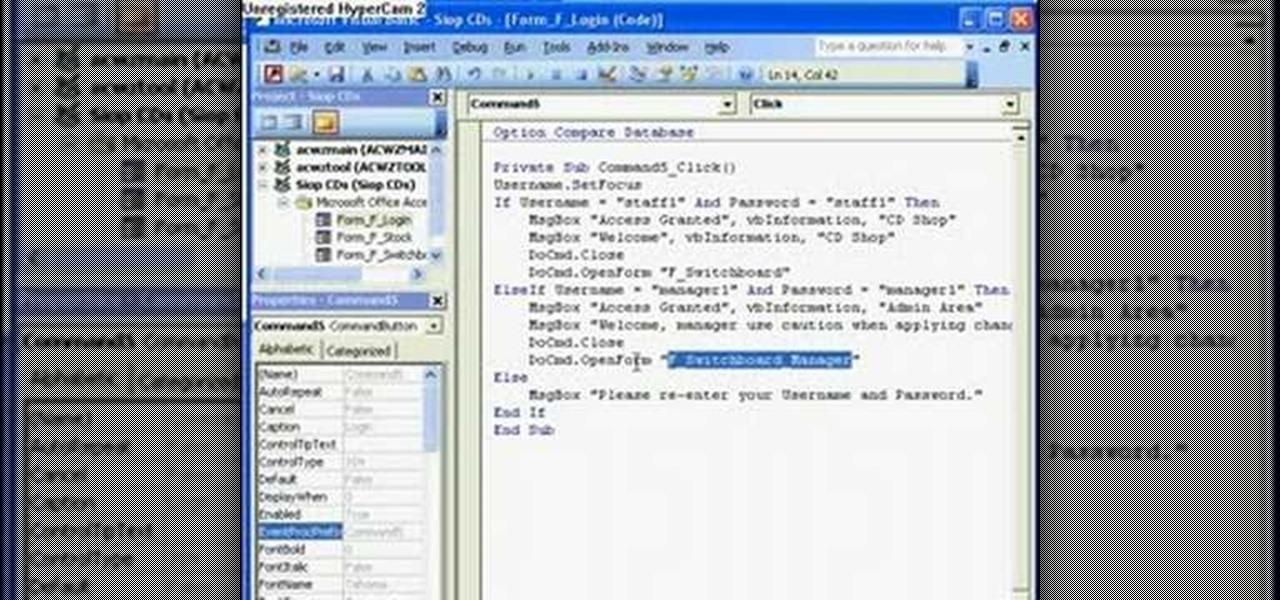
The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn about creating a login form and password protecting your database.

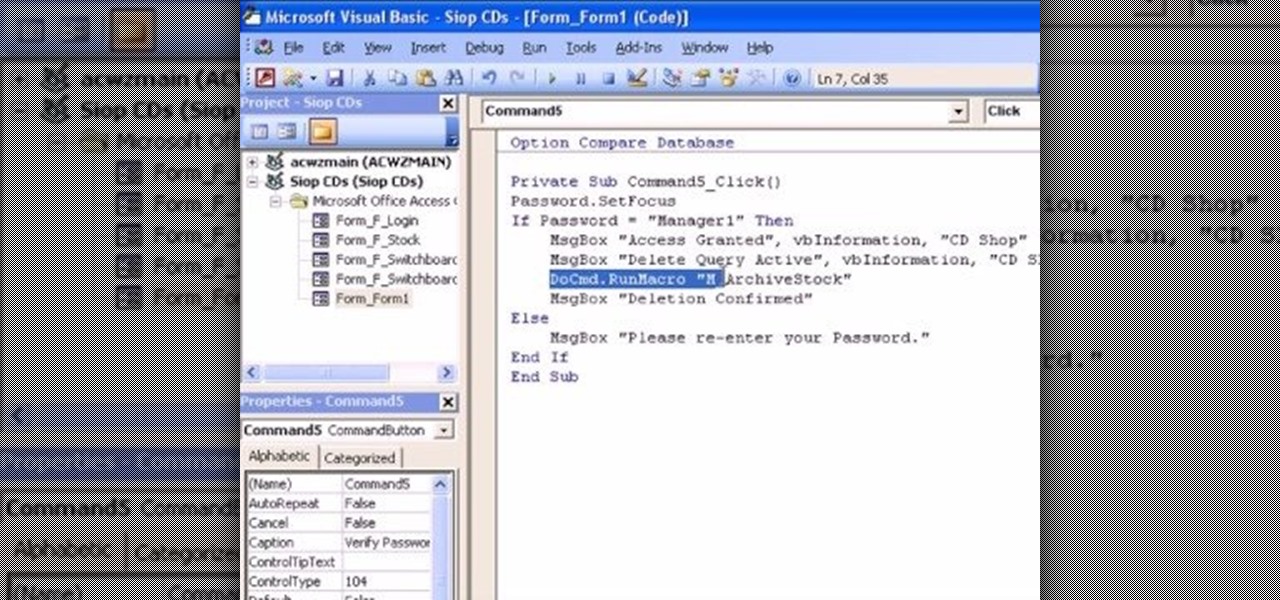
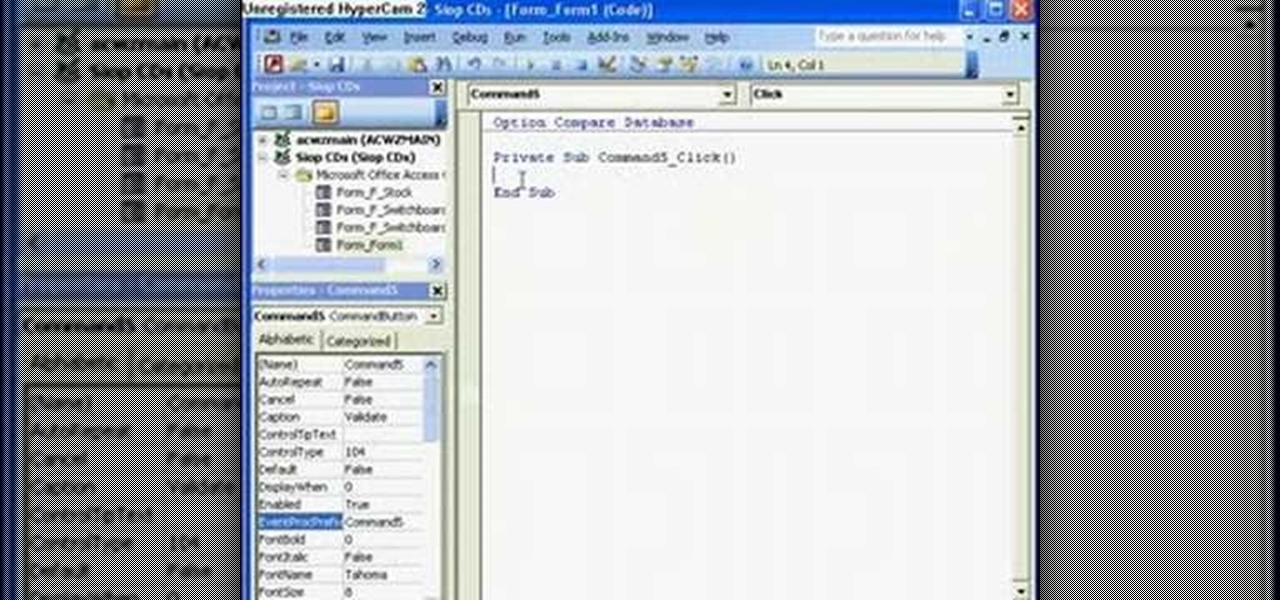
The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn about creating a multi-user login form to password protect different areas of your database.

Thanks to Yifan Lu, it's been discovered that the operating system running on the Kindle Touch is written mostly in HTML5 and JavaScript, unlike the previous models which used Java. This is exciting, because when a device is hacked or rooted, that means homebrew programs can be run on the device, maximizing its potential and getting the most for your money.

Sony's new Internet TV combines the power of Google TV and television into a neat and accessible package. And setting up your new Google TV is a cinch. This video walks you through the quick setup process for getting your Google TV system going. The player in this video is model NSZ-GT1.

Coders are accustomed to working remotely. The beauty of coding is that all you need is a laptop and a WiFi connection, which makes working anywhere a fairly simple transition. If you're looking for a career change, now might be the perfect time to give coding a try.

While conducting an OSINT investigation, it's important to be able to pull in information based on any clue you uncover. In particular, license plate information can turn up everywhere, from photos to live data to on your own street. You could use that data to find the VIN, see if a Tinder date has hit anyone, find out who's blocking your driveway, and so on. Skiptracer can help get the ball rolling.

Null Byte readers are no strangers to the powers and benefits that come from learning how to code. By knowing only a handful of programming languages and platforms, an intrepid developer can create everything from best-selling apps to spyware in the comfort of his or her own home.

From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

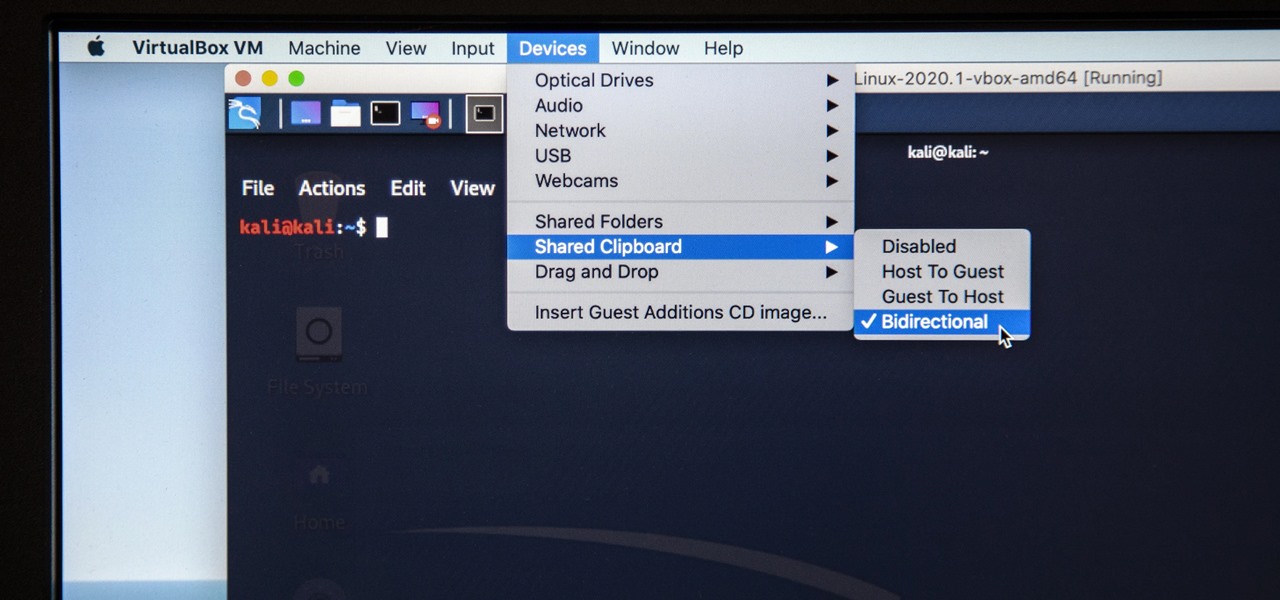
Last week, I updated VirtualBox on my computer since I had skipped a few versions, then I could no longer copy text or paste text from my Kali virtual machine to my host OS and vice versa. Installing the Guest Additions didn't seem to do anything, and the bidirectional shared clipboard was enabled, but there was one thing that did work for me that may help you out too if you experience the issue.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

Apple's annual iPhone launch is set for Sept. 10 and iOS 13 is expected to be released soon thereafter, but it appears that the likelihood of a "one more thing" reveal just got a big boost.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.