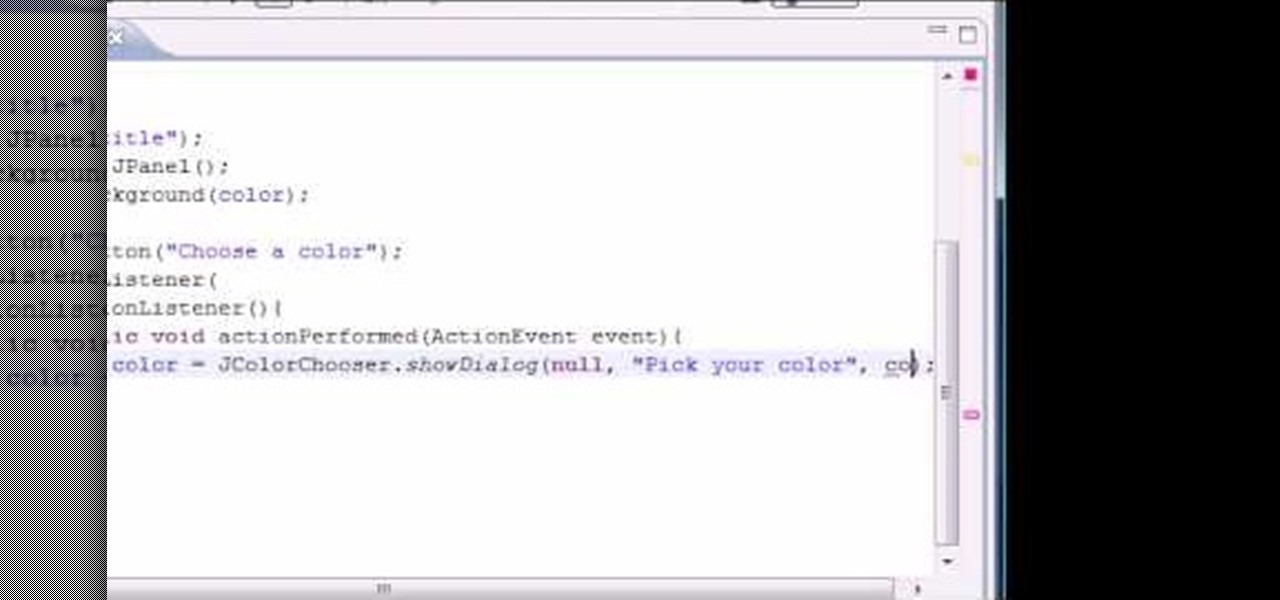
Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBostonian will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to implement and use the JColorChooser control pane when writing code in the Java programming language. For more information, including detailed, step-by-step instructions, watch this helpful programmer's guide.
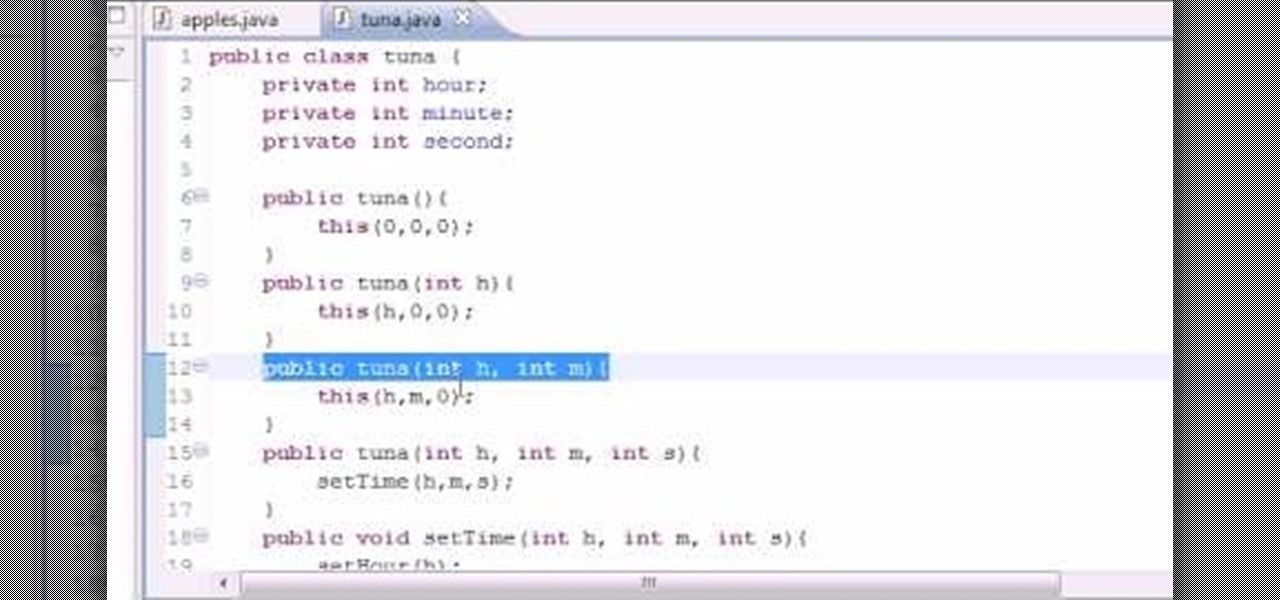
Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBostonian will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to build objects for multiple constructors when writing code in Java. For more information, including detailed, step-by-step instructions, watch this helpful programmer's guide.
Make sure you use FLASH Player 9 First: Deinstall Flash Player 10
Mike Lively of Northern Kentucky University shows you how to build an interactive Molecule Viewer in Papervision3D and Flex 3. This is a fun application building project for anyone learning Adobe Flex Builder 3 and a great resource for molecule viewer for students, educators, and researchers in chemistry and biochemistry.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

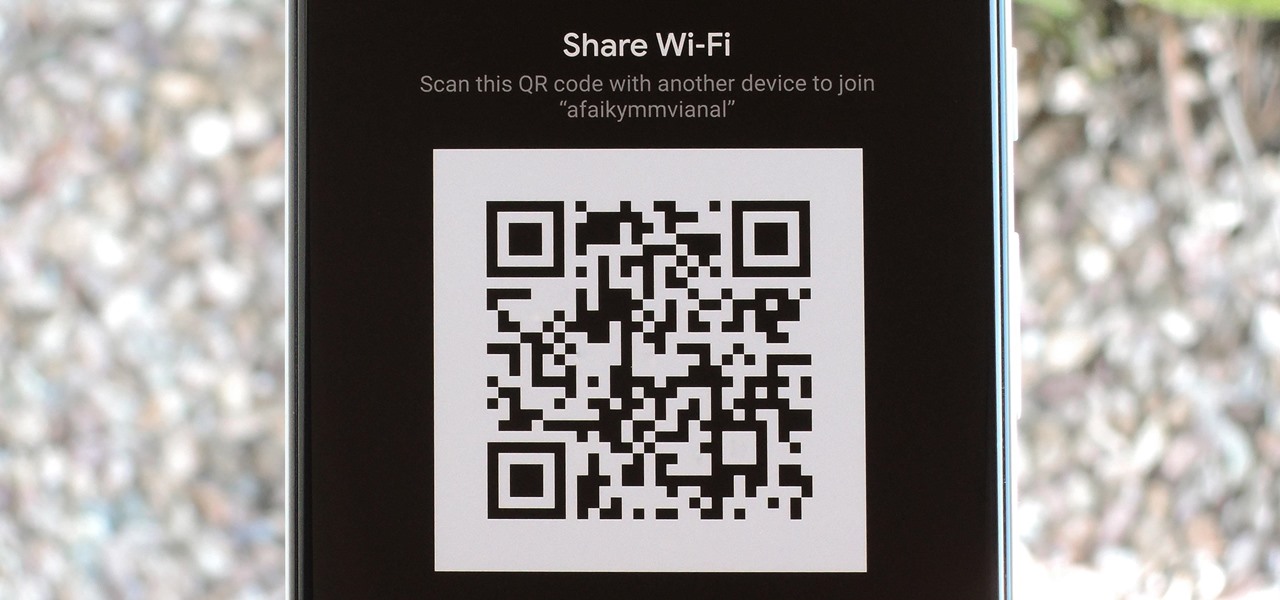
If your phone is running Android 10, you can now share your Wi-Fi network with friends using a handy QR code. The other person doesn't have to be running Android 10 — in fact, you can even share this code with iPhone users. In most situations, this is now the fastest way to share your Wi-Fi password.

If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

There's a feature in the Gboard keyboard that enables people who cannot talk, type, or swipe normally to still have a way to communicate in the digital age on their smartphones. While it's mainly an accessibility feature for those who actually need it, it's a good way for anyone to learn or brush up on their Morse code skills — and it works on both Android and iOS.

The first question people ask me when they come to my apartment is usually "What's your Wi-Fi password?" While I'm happy to give my friends free access to the internet, it's hard to walk each person through my secure password. Luckily, there's a way to create a QR code that will let people easily connect to a Wi-Fi network.

This is my first ever how-to so I apologize in advance for any grammar mistakes or spelling errors. Introduction

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters.

While becoming the next Mark Zuckerberg may be out of reach for someone just getting introduced to code, the skill has never been more valuable. Just understanding basic programming language is a great thing to put on your resume, and if you know how to code, you’re golden. Software developers and programmers have been the most resistant to the recession, as jobs in the tech industry continue to grow.

Nothing says you care like a hand-made card. Show that special someone what they mean to you or just have fun with this cute arts and crafts project. Get your markers and colored pencils. Get your glitter and glue. Get creative.

Why buy an ant farm? It’s simple and fun to make one from a few items you have lying around the house.

Need a way to keep the kids busy on a rainy day? Making a pop-up card is quick, easy, and will entertain them for hours! Watch this video to learn how to make a pop-up card.

In this stage design and construction video series, learn how to build one of those small “portals.” Our expert—a director, actor, and producer himself—will show you tips and techniques for building a small, mobile stage that can be set up anywhere you or your acting troupe decide to give a performance. This step-by-step guide to stage construction includes clips on what tools and materials to use, how to measure and cut the frame, what type of bolts to use for ease of tear down, and how to b...

Check out this video to learn the basics of building cabinets for your home or office. The video covers basic construction, woodworking, cutting of boards using a Festool and tablesaw.

Make a Spark frame ripper

Error code P0401 on a 2004 Ford Focus indicates EGR Insufficient Flow, which usually means your DPFE sensor needs to be replaced. If you're not sure though, and you shouldn't be, watch this video to learn how to perform a test that will make sure your DPFE sensor is actually broken before you replace it.

Facebook has provided developers with a whole library of code usable for creating applications. This tutorial shows you how to get the code, and then how to use it so you can start developing your own Facebook apps using Adobe Flash and Action Script

Add an extra level of security to your website by creating your own dynamic 'Buy It Now' button for PayPal-using visitors to your website. Coding this button is very easy, and you can even animate it to draw more attention to your webstore.

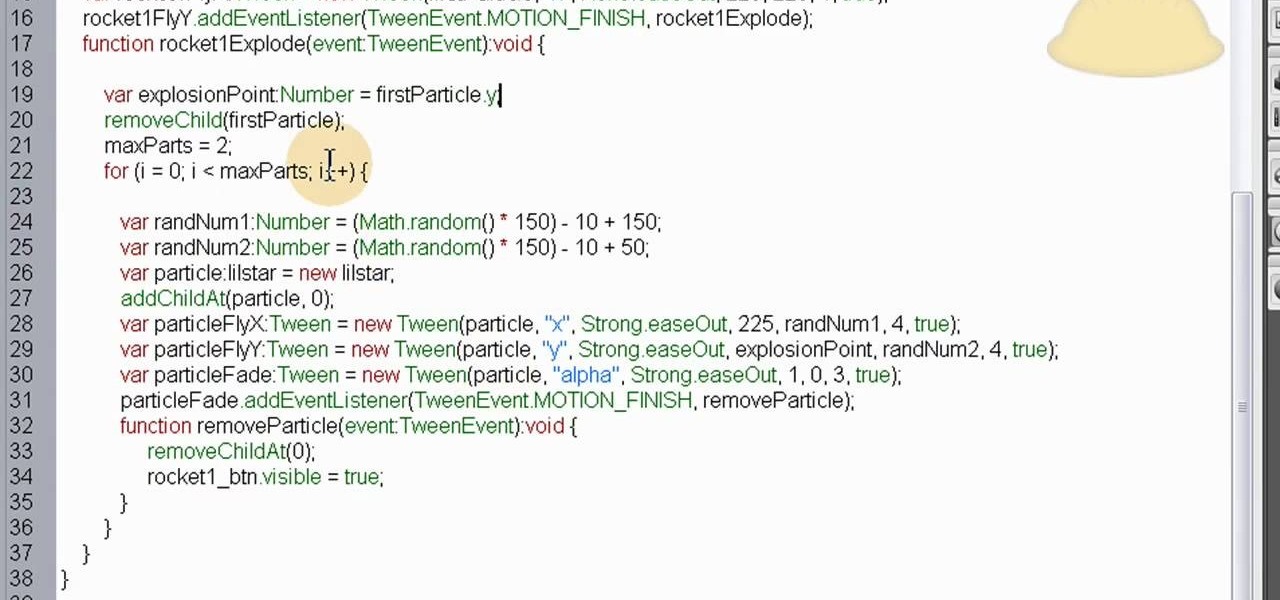
This is a custom particle effect, coded using ActionScript 3, that will recreate the effect of a rocket and fireworks explosion. The effect is also randomized, so you'll never get the same animation twice. This tutorial shows you how to code this effect using Fireworks.

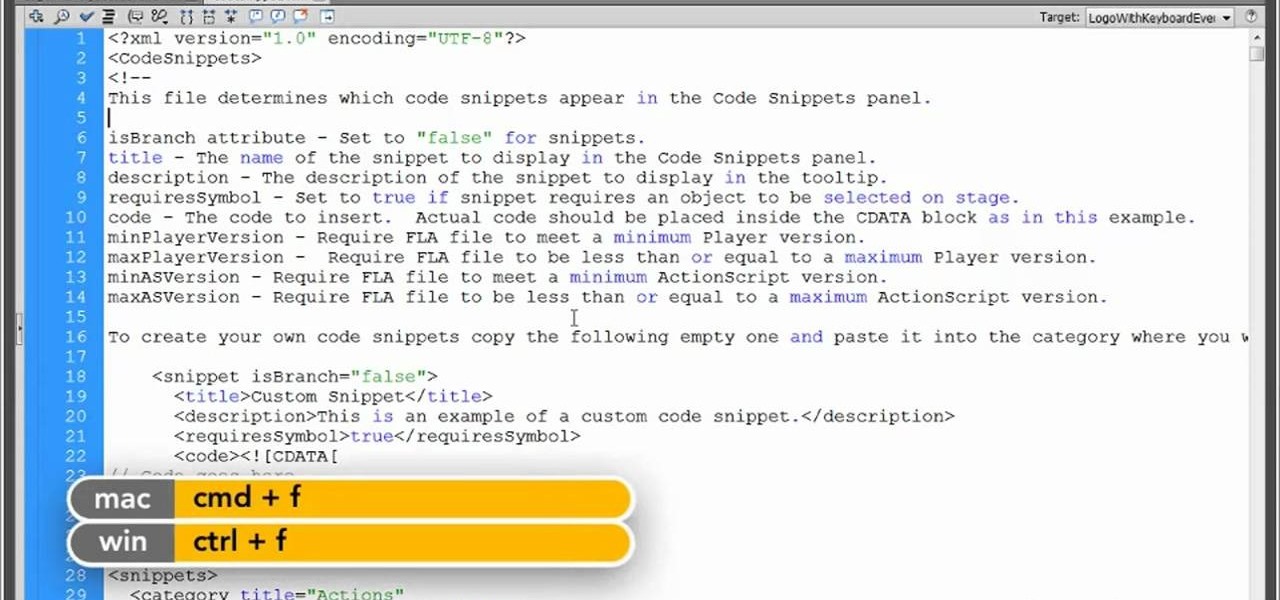
In this clip, you'll learn how to tweak any existing Code Snippet when working in Flash CS5. Whether you're new to Adobe Flash or merely unfamiliar with Flash Professional CS5, you're sure to benefit from this free video software tutorial from Lynda. For more information, including detailed, step-by-step instructions, take a look.

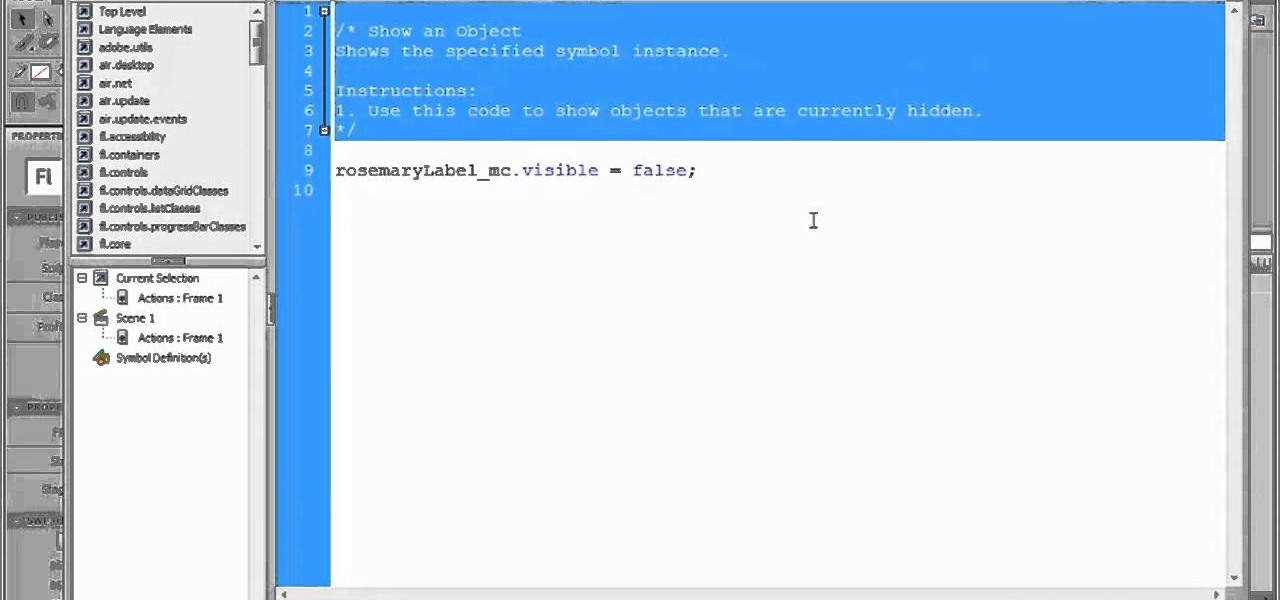
In this clip, you'll learn how to use Code Snippets to display and hide movie clips in Flash CS5.. Whether you're new to Adobe Flash or merely unfamiliar with Flash Professional CS5, you're sure to benefit from this free video software tutorial from Lynda. For more information, including detailed, step-by-step instructions, take a look.

Whether you're new to Adobe Flash or merely unfamiliar with Flash Professional CS5, you're sure to benefit from this free video software tutorial from Lynda, which presents a thorough, step-by-step overview on how to work with code snippets within Flash Professional CS5.

In this clip, learn how to program state codes and route buttons in Adobe Flash Builder. Whether you're new to Adobe's popular Flash IDE (previously titled Adobe Flex Builder) or simply wish to become better acquainted with the program, you're sure to find benefit in this free video software tutorial. For more information, including specific, step-by-step instructions, take a look.

See how to scan and read QR codes with your iPhone's camera. Whether you're the proud owner of an Apple iPhone 4G or perhaps just considering picking one up, you're sure to benefit from this free video tutorial. For more information, including a detailed overview, watch this iPhone user's guide.

It goes by many names. The RLoD (Red Lights of Death), the RRoD (Red Ring of Death), absolute disaster. Whatever you call it, the XBox 360 error that causes many console's front LED's to turn red in rage and cessation of function has caused all sorts of headaches for consumers and Microsoft. It can be caused by a couple of different cooling-related issues, and determining the error code that has caused your console to malfunction can go a long way to helping you fix it. This video will show y...

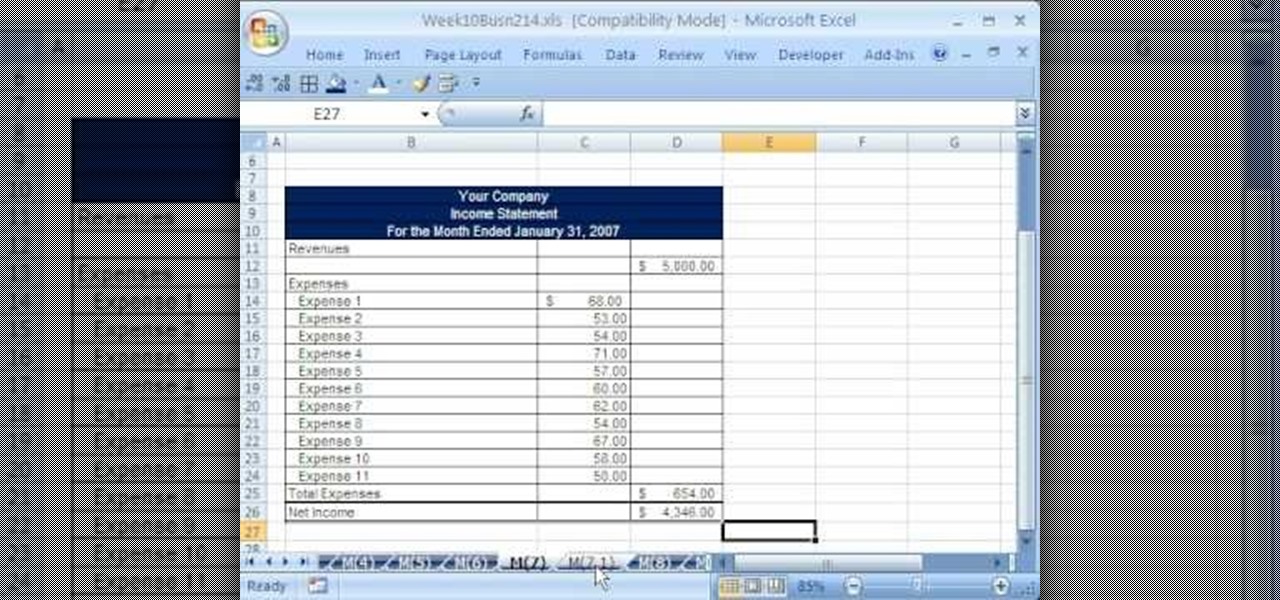
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you've come to the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 54th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn how to find, download and use VBA code in your MS Excel projects.

This Dreamweaver CS4 tutorial takes you on a step by step process for installing an automated comment box system for your website. The system is a great way for communicating and interacting with your website users. It has a great feature that automatically sends you an email everytime someone comments in your website. Also it will allow you to post a reply by email.

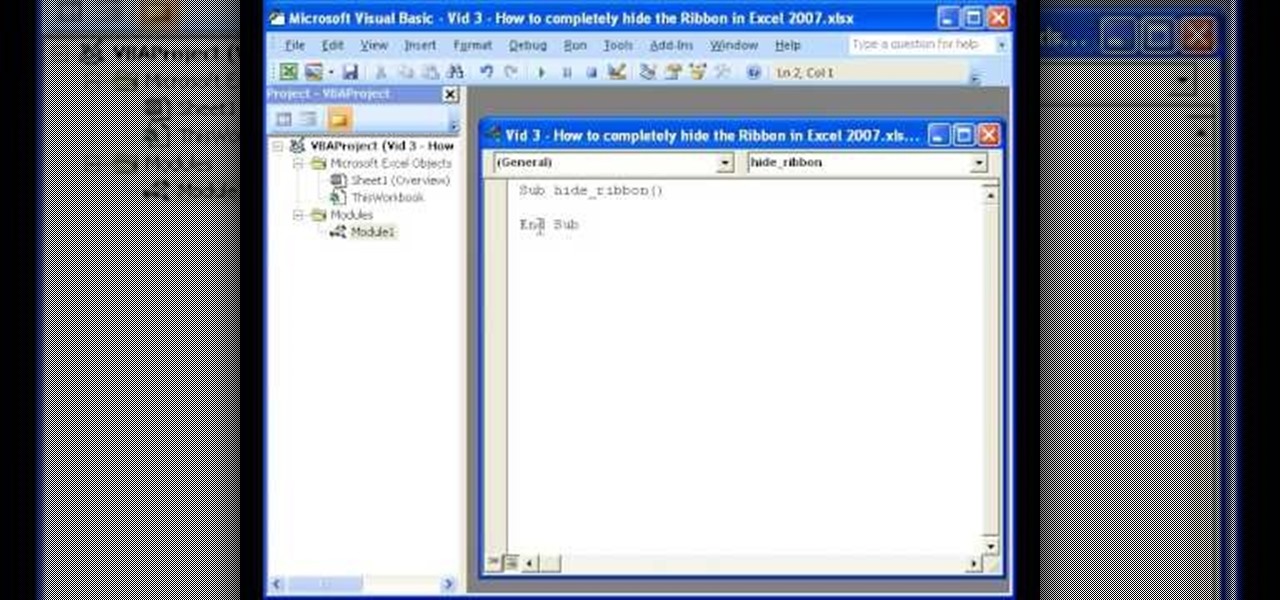
The instructor of this video shows you how to completely hide the ribbon, or the menu, in Excel. If you only want to partially hide the ribbon, you can use the shortcut control + F1. To completely hide the ribbon, though, go to the Visual Basic screen, hit Alt + F11. Then, go to insert, then module, and type in the macro "sub (Your name for macro)" then hit enter, then type in the code "application.executeExcel4macro''show.toolbar(""Ribbon"", false)''". To set up the code to show the ribbon a...