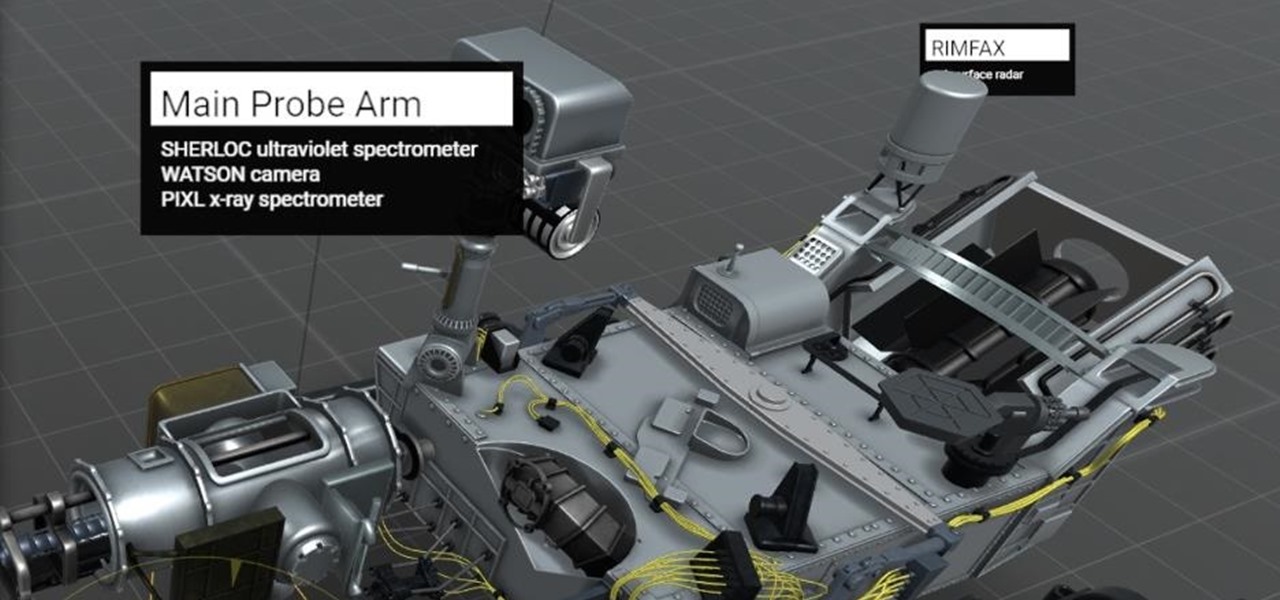
Defcon is the largest hacker conference with something for everyone, whether it be the talks, parties, villages, or any of the hundreds of events. In this guide, we'll take a holistic view at everything that goes into attending the con for the first time, from securing your electronics and making the most of your time to the logistics of getting there and finding the right place to stay.

Cleanliness is next to godliness. My interpretation of that age-old adage means that keeping your house clean is just as un-fun and boring as being a goody two shoes. That's why they call things like laundry and doing dishes "chores," I assume. Yuck.

There's nothing in this life that we love more than making one ingredient or one food tool do multiple things. It saves money! It saves time! It makes us look smart at cocktail parties!

Minor mishaps occur all the time in the kitchen, whether you cut your finger while dicing an onion, scorched your hand in a grease fire, or burned the roof of your mouth because you were to eager to taste-test your killer pasta sauce.

Marinades are among my all-time favorite tricks as a cook for several reasons. They're easy like Sunday morning, they let time do what it's supposed to, which is work for you, and you get a huge return for relatively little effort on your part.

Most of us have conducted an investigatory science project without even knowing it, or at least without knowing that's what it was called. Most science experiments performed, from elementary to high school students and all the way up to professional scientists, are investigatory projects.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

The story of the HoloLens has been a mix of work and play. But while many developers have devoted time to creating gaming and entertainment apps for the HoloLens 1, with the HoloLens 2, Microsoft has been encouraging everyone to focus more on the enterprise side of things.

San Francisco-based augmented reality company Scope AR has made building AR instructional content for mobile devices and AR wearables as easy as throwing together a PowerPoint deck, primarily via its WorkLink platform.

We are now in the age of 5G. Carriers worldwide are upgrading their networks to the newest standard for mobile, which will dramatically improve your phone experience. How? By giving it download speeds and latency that surpass Wi-Fi. But before you upgrade, there are few things you should know first.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

Sorry, Galaxys S11–19, Samsung's jumping straight to Galaxy S20 this year. They're also going with essentially three base models before accounting for niche variants. Of these three models, it's clear which one's the best: the Galaxy S20 Ultra.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

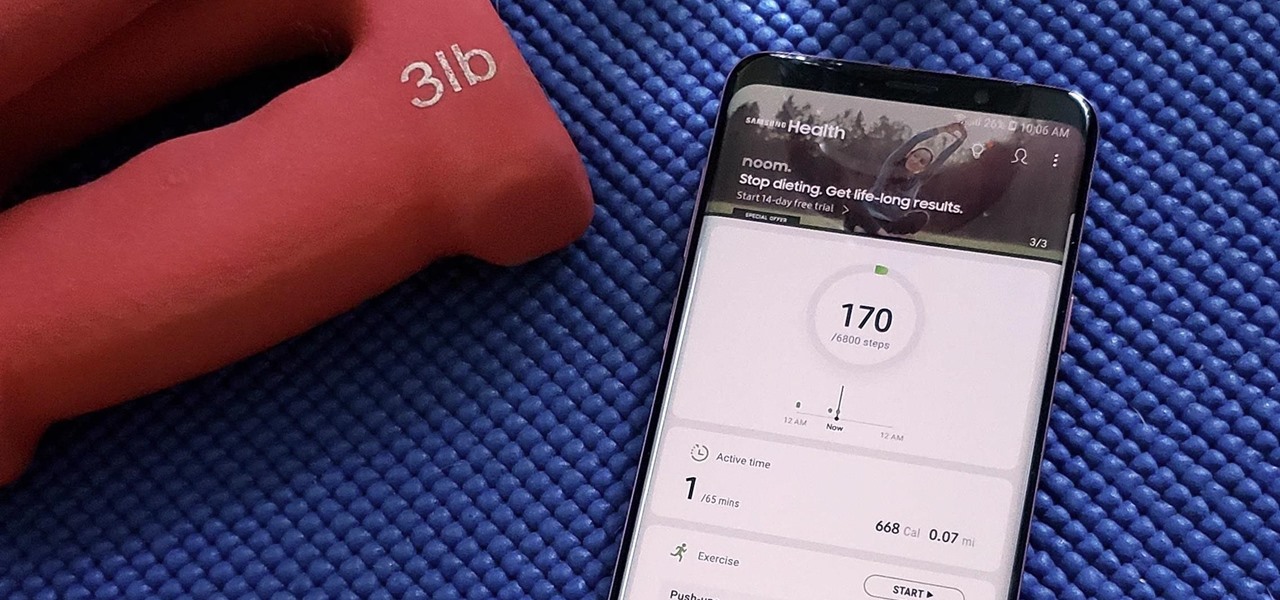
Samsung Health has become one of the most comprehensive wellness apps thanks to features that cover everything from step counting to nutrition logging and symptom diagnosis. But because the app has so much to offer, it can be easy to overlook some smaller, but useful features.

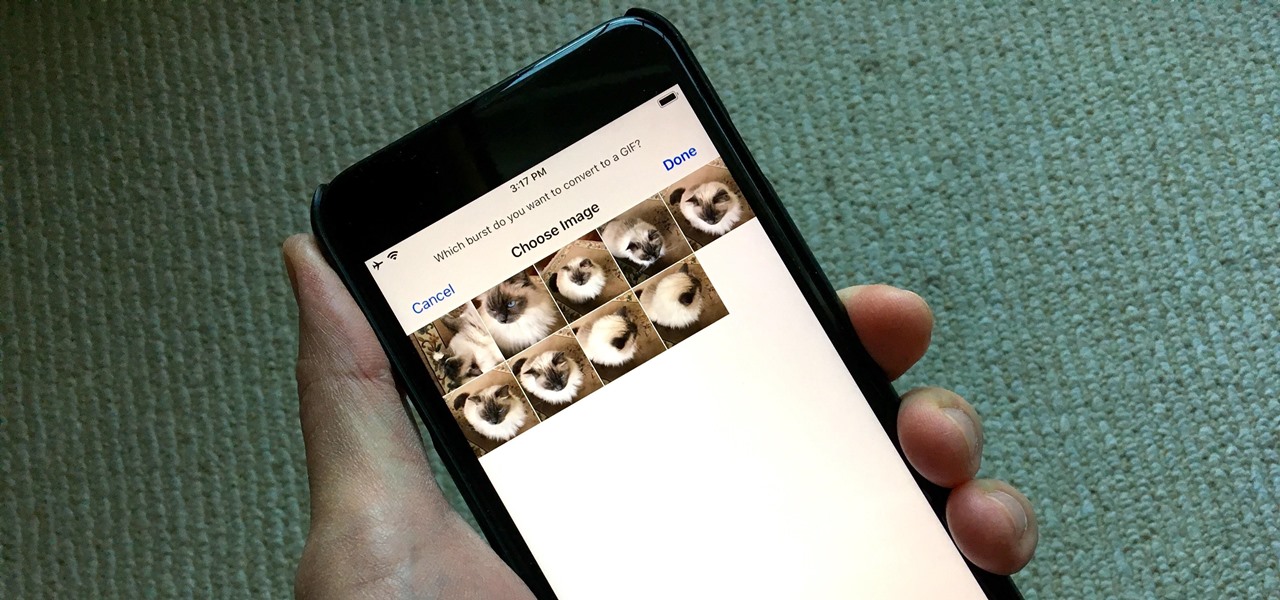
Creating GIFs of your own burst images has been possible for a while with third-party iOS apps, some of which cost money or include in-app purchases to utilize the full potential. Fortunately, with Shortcuts, Apple's automation workflow app, there's finally a native way to achieve this without spending any cash.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

I don't know about you, but I'm tired of hearing some of the same old jargon from people online who claim that all you need to make it on Instagram is to take good pictures and post consistently. Yes, for sure, but do you really think it's that easy?

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Tony Parisi, the global head of VR/AR at Unity Technologies, has been passionately working with virtual and immersive spaces for a long time. And while the internet world we live in now is very different than when Parisi was co-authoring VRML (Virtual Reality Modeling Language) — an early attempt at creating 3D environments that would work in a web browser — some of the questions that were assumed answered are being asked again.

Kuru is called the shaking disease, its name derived from the Fore word for "to shake." Caused by an organism that infects the part of the brain that controls coordination, people afflicted with kuru shake uncontrollably.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Eating out is great, but being able to cook the delicious ethnic foods you eat at restaurants is even better. It may seem daunting to put together a bunch of ingredients with which you might not be familiar (some with names you've never even heard of!), but with the guidelines below, you'll be making your own versions of ethnic favorites in no time.

Even those of us most comfortable in the kitchen can be daunted by the idea of cooking for a whole houseful of people. Whether you have a large, well-equipped kitchen or a small one with just the essentials, it can prove to be quite a task to prepare food for a dozen or so people. It takes a certain type of recipe that allows for mass production, in respects to both technique and ingredients. And what I've provided below includes several recipes that you might normally make for just a family ...

Most of us lead busy, work-filled lives, often clocking in a 9-to-5 five days a week. And when that clock signifies the hour to leave, the last thing on anyone's mind is: "Time to go to the grocery store to pick up more fresh produce!" (Well, to be fair... maybe more people are psyched about this, but I know with certainty that I am not one of them.)

Once upon a time in America, there was coffee and there was decaf. That's it. No capuccinos. No espressos. And certainly no Starbucks. Coffee was just coffee, something that you bought at a gas station or donut shop. If you made it at home, it was either in a metal pot or instant coffee.

The ability to make a meal for yourself used to be one of those life skills you had to learn or otherwise you would starve, but the rise of convenience foods, takeout, and other aspects of modern living have made it entirely possible to be a grown person and not know what to do in the kitchen.

Fall is my favorite time of year, yet I cringe every time it begins. Why? Because it seems like every business is in a frenzy to start the Christmas shopping season the day after Halloween ends. For those of us who are fans of pumpkins, that's a buzzkill.

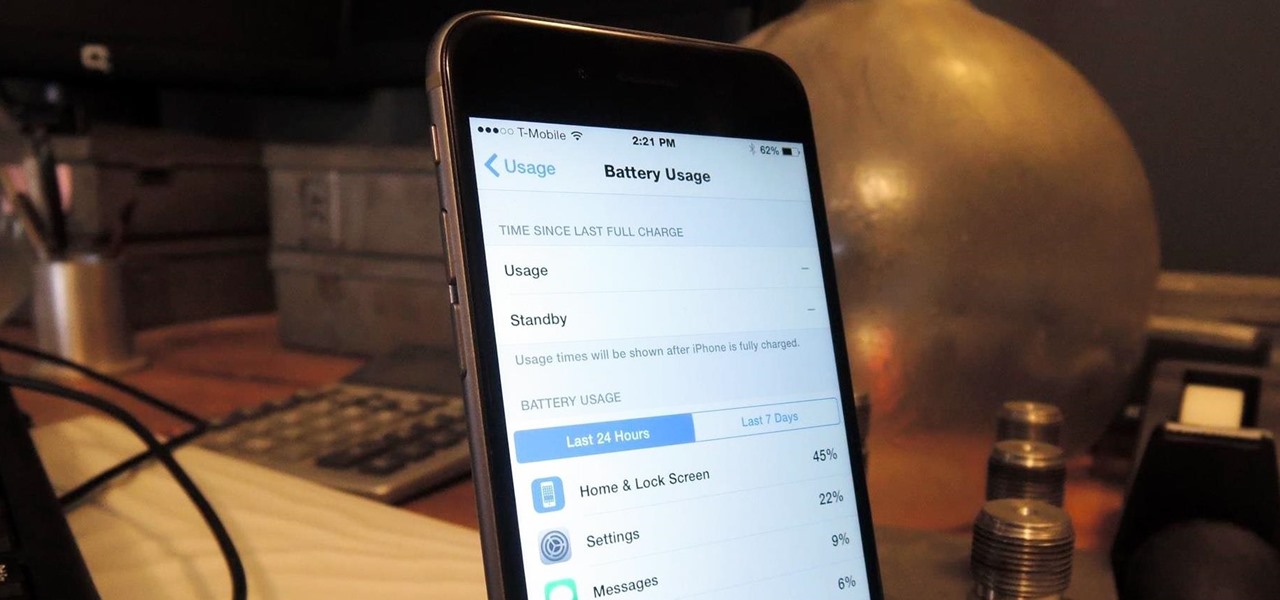
The new iPhone 6 and 6 Plus are supposed to last a lot longer in your pocket with improved battery life, but that doesn't mean that iOS 8 will be that friendly on your older iPhone model. All of those awesome new features could be killing your battery, but with some simple tweaking, your battery life concerns will be a mere afterthought.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

Foodies and big-time chefs like Thomas Keller go crazy for fleur de sel. This finishing salt appears in fancy eateries and cookbooks the world over, and in the early 2000s, it was not uncommon to see diners in a high-end restaurant sprinkle a pinch of fleur de sel on their plates from their own personal stash.

Jailbreaking gives you root access to the iOS file system, allowing you to install third-party apps and tweaks on your iPhone that aren't available in the App Store. It opens up a whole new realm for what your device can do, but it can also cause instability across the system and can dissuade you from getting future updates from Apple that have important features, bug fixes, and security enhancements.

Want to show all your foodie friends that you're really in the know? Then it's time to master the art of making edible dirt. Chefs out there are finding ways to take various foodstuffs and dry, char, and combine them to give the appearance of actual dirt—only with a rich, savory taste.

I grew up in a household where bacon was considered its own necessary food group. My mom saved the bacon fat in a jar and reused it in other dishes, which my friends considered vile, unless they were also from immigrant families or the American South, where saving bacon fat has never gone out of style.

About ten years ago, Western research figured out that green tea was a nutritional powerhouse. After all, in Asian countries where green tea is consumed throughout the day, cancer rates tend to be much lower, although there are probably other factors contributing to that fact, like less processed food and red meat in the standard Asian diet.

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

Even as someone with super pale skin that burns instead of tanning, I don't use sunscreen nearly as often as I should. Or, uh...ever. My skin cancer prevention routine mostly involves hiding from the sun as much as humanly possible. If you're like me and hate the greasy feeling of sunscreen, there are other ways you can protect your skin by increasing your sun tolerance. Your diet actually has a lot to do with how easily you burn, so by getting enough of a few key nutrients, you can decrease ...

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

This two-part series (second part here) will teach you literally everything you need to know in order to make pretty much anything out of leather.

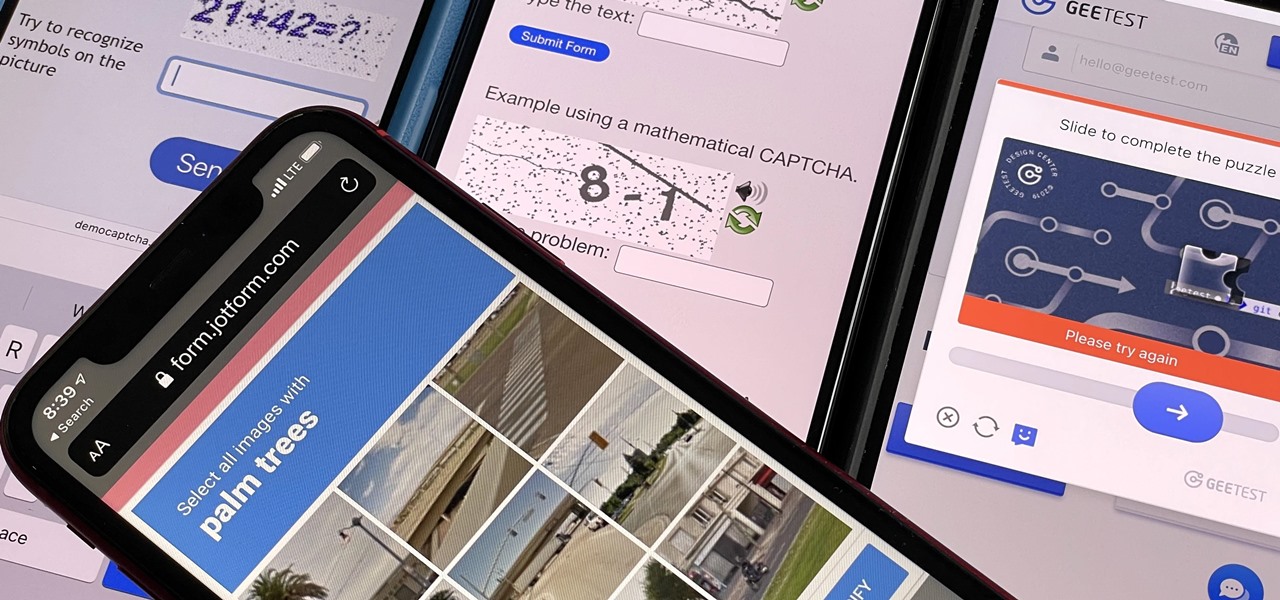
If you hate matching images, typing letters and numbers, solving math problems, and sliding puzzle pieces for CAPTCHA human verification, you'll love Apple's newest privacy feature for apps and websites.