Months before London-based Jonathan Moon would turn 30, he started musing over how to celebrate. While he had rung in past birthdays at home, he wanted to do something out of the ordinary as a farewell kiss to his twenties. A short ski vacation with friends felt like the perfect idea.
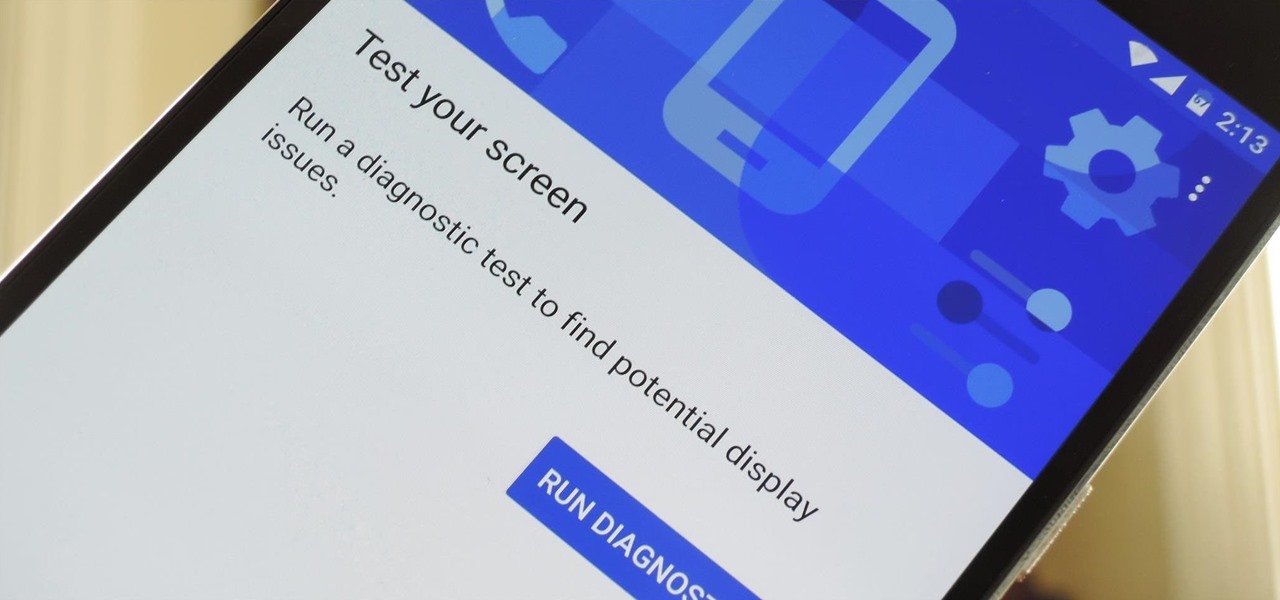
Google has a lesser-known Android app called Device Assist that might just be one of the most useful programs the company has ever published. It offers interactive guides and general tech support for Android, plus it can diagnose your device and help you fix any issues it finds.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

People like to cite the iPhone as the device that started the smartphone craze, but the truth is, smartphones had existed for years by the time Apple got into the game. The real groundbreaking feature that this device brought to the table was a multi-touch screen to go along with its "smart" functionality, and this is still the main method we use to interact with our devices today.

Eggs are a staple food for most Americans, which is no surprise, considering how necessary they are in savory and sweet recipes alike. On their own, they're usually not too eggs-citing. However, these clever egg hacks will make your egg-making easier, more fun, and more interesting.

Catching up with Windows 8, Apple has finally included a way in Mac OS X to use two apps side by side in full screen view. In the 10.11 El Capitan update, it's called Split View, and it works fairly well for the most part. It's not quite as intuitive as it should be, but easy enough once you get the hang of it.

Your iPhone's home screen is a tricky thing. You can sort your collection of apps in any order you'd like, but where you place those apps is a totally different story. App and folder placement follows a strict grid on iOS from left to right, top to bottom. No exceptions, and that's how Apple wants it. So you might think without a jailbreak you're stuck with this layout — but you're wrong.

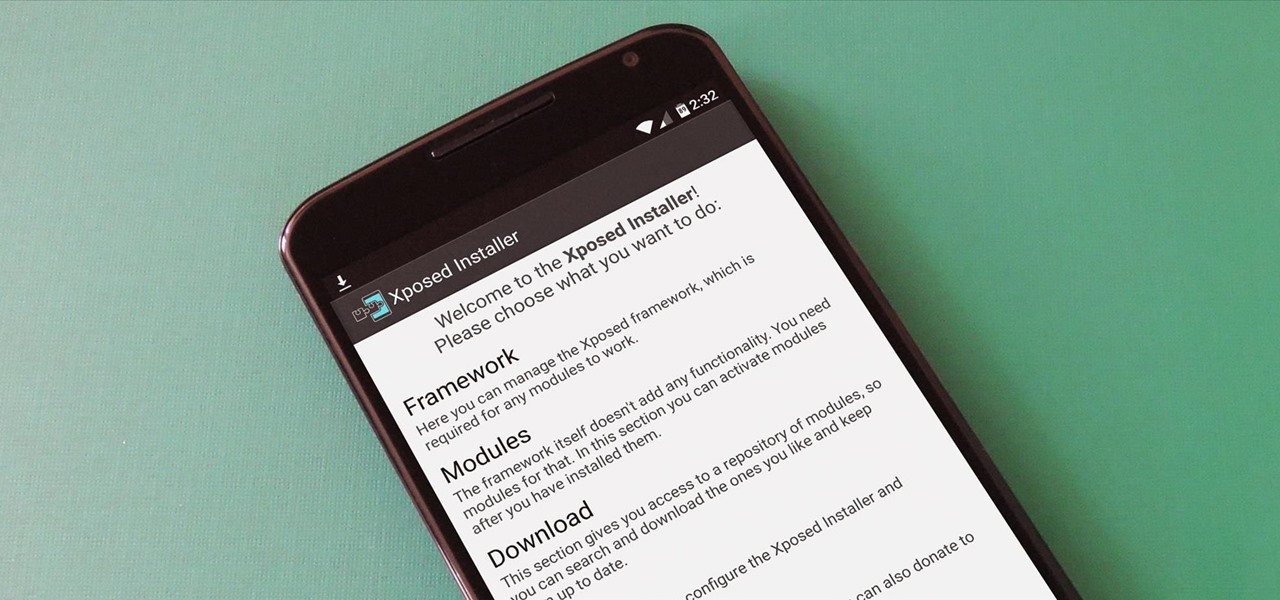
UPDATE 11/17/15 The Xposed Framework now officially supports Android 5.1 through 5.1.1 Lollipop devices as well. Everything will still work the way it has with Android 5.0 through 5.0.2, but there are a separate set of files for the newer Android version. I'll cover both below, but make sure to download the proper file for your particular version of Android.

This past year was a big one for WonderHowTo. Our biggest yet. In 2014 our writers, curators, and community members helped over 100 million people learn over 270 million new things. That's 40% more people than the total number of students enrolled in every single school from elementary through college across the entire United States. That's pretty awesome. I couldn't be more proud of our entire team, and of course you, the community members who've helped us grow to this point.

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

Staying healthy is a progressive challenge we all face throughout our lives, and figuring out just how to do that can be a challenge when it's not your job. For doctors, however, it is. Here's how they keep themselves healthy day to day.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

When it comes to give away or sell your iPhone, you can't just power it down, take out the SIM card, and hope everything will be okay. There's valuable data on your iPhone, and you need to get rid of it. Plus, if you don't perform all the necessary steps, chances are whoever ends up with the device won't even be able to use it. If you're selling it, that could ding your seller reputation.

Arcades have long faded away from popularity, but their legacy is being kept alive thanks to emulators and the avid fans who grew up loading quarters into all of those coin-op games. Although nothing beats an actual arcade environment, my favorite emulator from the early 2000s has found a new home on Android, and with it a second life.

Fish is delicious, and as the Harvard School of Public Health points out, incredibly good for you. There are many studies that show regularly consuming a couple of servings of fish per week can help prevent heart disease and may well reduce your chances of stroke, depression, and getting Alzheimer's. After all, there's a reason why fish is called "brain food."

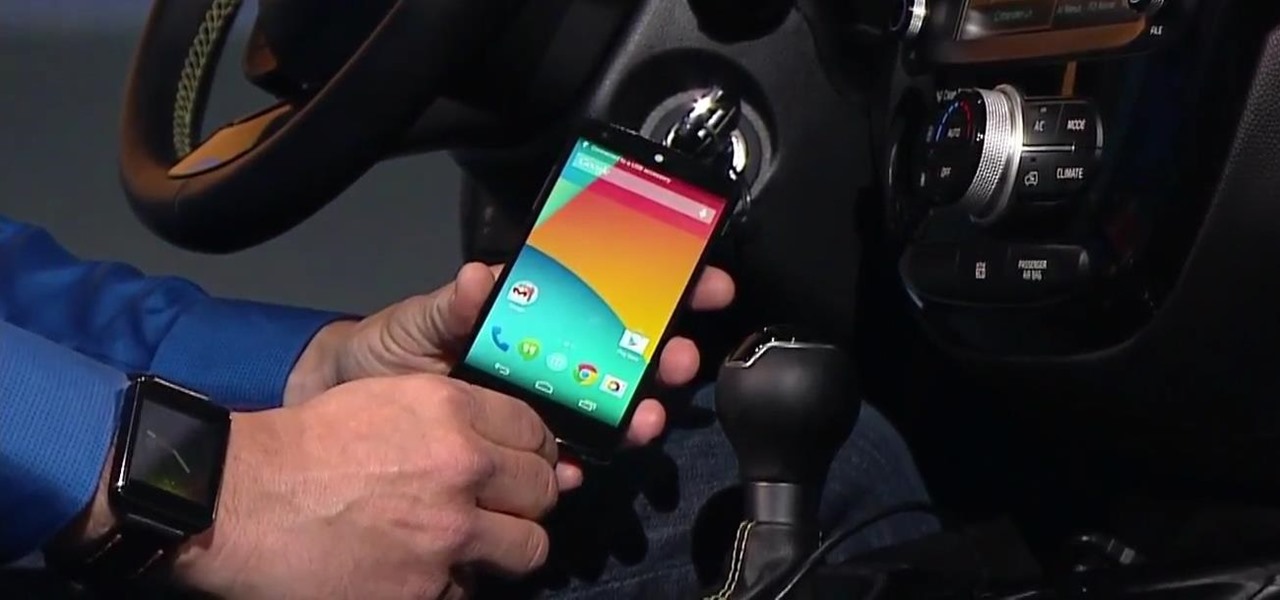
This year's I/O was all about bringing Android into the future and onto new devices. On top of announcing the upcoming "L" release of its mobile OS, Google showcased Android Wear, Android Auto, and Android TV.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

Facebook will let you do pretty much anything via a text message, but unless you still have a flip phone, it's more of a novelty than actually useful.

A long time ago, we recommended the Hover Zoom extension for Chrome as an easy way to blow up small image thumbnails without actually have to "click" on the images themselves. Over the past year, there have been reports that Hover Zoom now collects and sells your browsing data to third-party advertisers without your consent.

The holiday season is almost over, bringing the year to an end, and what better way to end it than with some tonsil hockey from the dime across the room on New Year's Eve?

Welcome back, my budding hackers! In my continuing series on Linux basics for aspiring hackers, I now want to address Loadable kernel modules (LKMs), which are key to the Linux administrator because they provide us the capability to add functionality to the kernel without having to recompile the kernel. Things like video and other device drivers can now be added to the kernel without shutting down the system, recompiling, and rebooting.

Why can't I see who is stalking my Facebook profile?

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

Unwanted advertising is everywhere. Annoying pop-up ads, overly loud late night commercials, spam...it never ends. And before spam, there was junk mail. Junk mail is even worse because unlike TV commercials and internet ads, it's physical. You can't just delete or ignore it—and it's an awful waste of paper. So what can you do about it?

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

After a two-month delay, Apple has finally released iTunes 11, which was initially slated to be released alongside iOS 6.

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

Summer is the best friend of poison ivy, oak, and sumac. When the weather is hot outside, people spend more time in the great outdoors, which means more people accidentally running face first into some poisonous shrubs, leaves, and vines. If that sounds like you, instead of suffering through the itch or spending money on expensive pharmaceutical solutions, try some of these home remedies out.

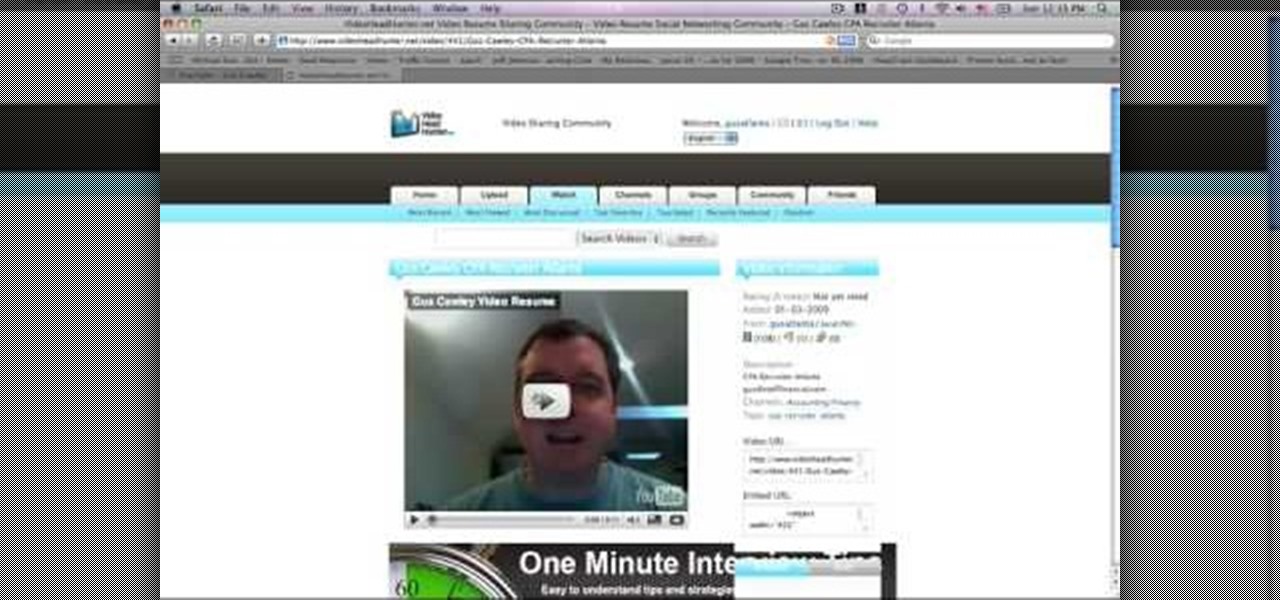
Gus Cawley shares the ways to make a video resume with the help of free online tools. 1. Log in to YouTube. 2. Click upload and select quick capture. 3. Click the record button (be sure to have good lighting, good background and a high quality microphone for a more effective recording) 4. State the information of your resume. 5. Click the red square button to stop the recording then choose publish. 6. Edit the information of the video. In the description, put your contact details and informat...

Touch rugby is a less intense version of rugby played without piling tackles. Learn how to play rugby, including rules and skills, in this video rugby lesson.

This Diet & Health how-to video explains what a urinary tract infection is, the symptoms and how to prevent the onset. UTI can be prevented by avoiding certain nutritional habits. However if urinary tract infection symptoms persist please contact your doctor.

Styrofoam is a polymer and when brought into contact with acetone the polymer breaks down into its monomers. This demonstration shows the process of depolymerization. It looks pretty cool.

Is your computer's power supply on the fritz? Learn how to install a power supply in a desktop PC with these easy steps.Before we begin, you should know that many brand name PCs use specially designed power supplies. So, make sure you contact them directly before installing a new power supply. Also, an unplugged power supply still can give you a powerful electric shock by put something inside an open vent.

Would you know what to do if someone ingested poison? Equally important, would you know what not to do?

Rumors, gossip, exclusion. Mean girls have a lot of weapons in their repertoire – here's how to combat all that nastiness.

Step1. Determine the type of job you want. Make sure that you have a detailed and complete profile on ‘linkedin’. You must also have a number of connections. Then decide which job you are looking for and the typical functions and titles. Also choose which type of industry you would like to work in and also choose what locations. You also need to write down specific names of organizations that you want to work for and who are they.

This video demonstrates how to install trailer lights on your boat's trailer. In order to determine what size replacement kit you will need, you must figure out the width of the trailier at the widest point. First, remove the old lights. Use a large slotted screwdriver to remove the cover. Don't forget to wear eye protection. Next, use vice grips and a wrench to remove the exposed stud. Using a wire brush, remove the salt and loose corrossion. Then grease the threads of the studs. You are now...

Betty, from Betty's Kitchen, explains how to make oven-baked pork chops with home style gravy! First, preheat your oven to 400 degrees. Betty explains that she will leave the fat trim around the pork chops before cooking. First, use meat tenderizer to season the meat. Shake the meat tenderizer over the pork chops on both sides, the top and the bottom. Get a skillet and pour peanut oil into it. Turn this on and make sure it sizzles. Pour one cup of flour into a large zip lock bag and put the p...