
How To: Make a Simple UDP_Flooder in C pt1.
Alright, this will be my first tutorial in C. Note that this guide is written for Linux.


Alright, this will be my first tutorial in C. Note that this guide is written for Linux.

A lot of things have been changing over at Microsoft recently. Not only did they acquire the ever-popular Android keyboard SwiftKey and give away Windows 10 for free, but they've started a Google X-like experimental division called Microsoft Garage, and they've actually released quite a few awesome Android apps.

Most of us lead busy, work-filled lives, often clocking in a 9-to-5 five days a week. And when that clock signifies the hour to leave, the last thing on anyone's mind is: "Time to go to the grocery store to pick up more fresh produce!" (Well, to be fair... maybe more people are psyched about this, but I know with certainty that I am not one of them.)

The end of a weekend can be depressing knowing just how bad Monday morning will be when you get back to work, but that feeling is tenfold when coming back from a lengthy vacation with zero work responsibilities.

Hola my fellow hackers! I promised you the tutorials on setting up RAT's and Botnets, but before jumping into those, i want you to know about the precautionary measures and detection of RATs which might be on the system without your prior knowledge. Of course the Anti-virus do most of the job but there are some RATs which slips past the Anti-viruses (This is where Hacker's skill come into play).

Just last month, Microsoft announced plans to take away a huge chunk of storage from the free tier of their OneDrive cloud service, and users are understandably quite upset. At the same time, they reneged on an offer to give Office365 users unlimited OneDrive storage, and instead, will only be offering 1 TB of storage.

Hello everyone. I've recently made the annoucement of the Null Byte suite of tools, and we've covered how to download and install it. Now it's time we cover how to submit a tool for inclusion into the suite. It's relatively simple, but we need to get a few ground rules out of the way.

Hackers are claiming money for a security flaw in Apple's new update. Quick Summary:

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

If you've been using Windows 10 for a while, you already know that Microsoft incorporated lots of new features into it. So you're probably familiar with Cortana (the new voice assistant), the Edge browser (their replacement for Internet Explorer), the newly resurrected Start menu, and all of the other big changes.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

If you've just ditched your Android phone for a new iPhone, you're in luck, because Apple has a way to make your transition as simple as possible with their Move to iOS app for Android. To help make things even easier on you, we've outlined the process of using Move to iOS to transfer images, messages, contacts, mail accounts, calendars, and more over to your iPad or iPhone running iOS 10.
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

Accidentally deleting important files can happen as easily as swiping left on something and watching it disappear into the ether. Of course, Apple allows automatic backups through iCloud, which ensures that your data is always stored safely in the cloud in case of emergency.
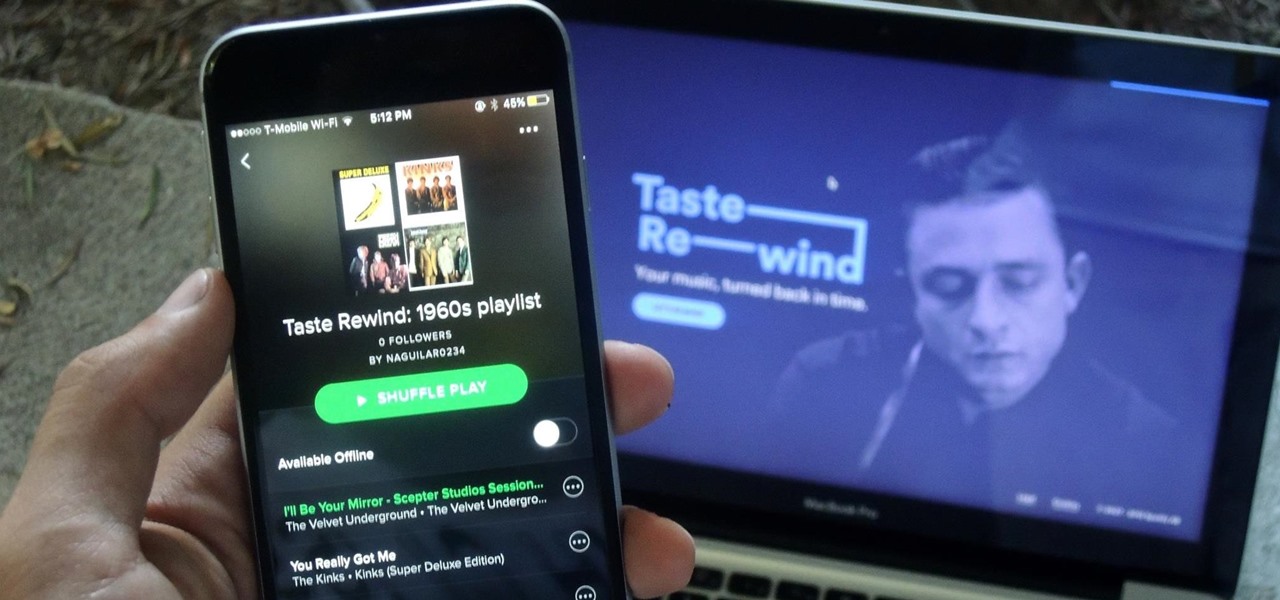
Spotify has a feature called Taste Rewind that claims to know what you would've listened to back in the '60s, '70s, '80s, '90s, and oughts ('00s), all based on your listening history and favorite artists. You can essentially time travel into the past and already have "favorites" songs to listen to! While I was skeptical at first, I tried the feature out for myself and was pleasantly surprised with the results. So if you want to create uniquely tailored playlists from the past five decades, st...

Google now has an iOS version of Android Wear, so if you own an Android smartwatch (Moto 360, ASUS ZenWatch, Huawei Watch, LG Watch Urbane, Sony SmartWatch, etc.), you can finally connect it with your iPhone.

Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my original script can download files, upload files, make changes to registry, create user accounts and more. I'm sure you could do it on your own too.

Flashing people in an oversized trench coat is both old-fashioned and exhausting (and also very illegal). But like the evolution from school-yard bullying to cyber-bullying, it seems as if the new trend is "cyber-flashing" (it's even has an official hashtag). In the U.K., police are now investigating what they are calling the first cyber-flashing case.
As familiar as it may look at first glance, there are still tons of subtle changes in Windows 10. Many options that existed in past versions have been moved, and virtually every system menu received at least a small visual makeover.

There is a huge myth that most Americans believe, and it might be the marketing triumph of the 20th century. We pay an absurd markup (Zero Hedge says as much as 280,000% for "designer" water) on something we can get for free because most of us believe that bottled water is healthier than tap water. But is it? Here are 5 reasons why tap water is probably better than that bottled stuff you drink. 1. It's Not Cleaner (& Might Be Dirtier) Than Your Tap Water
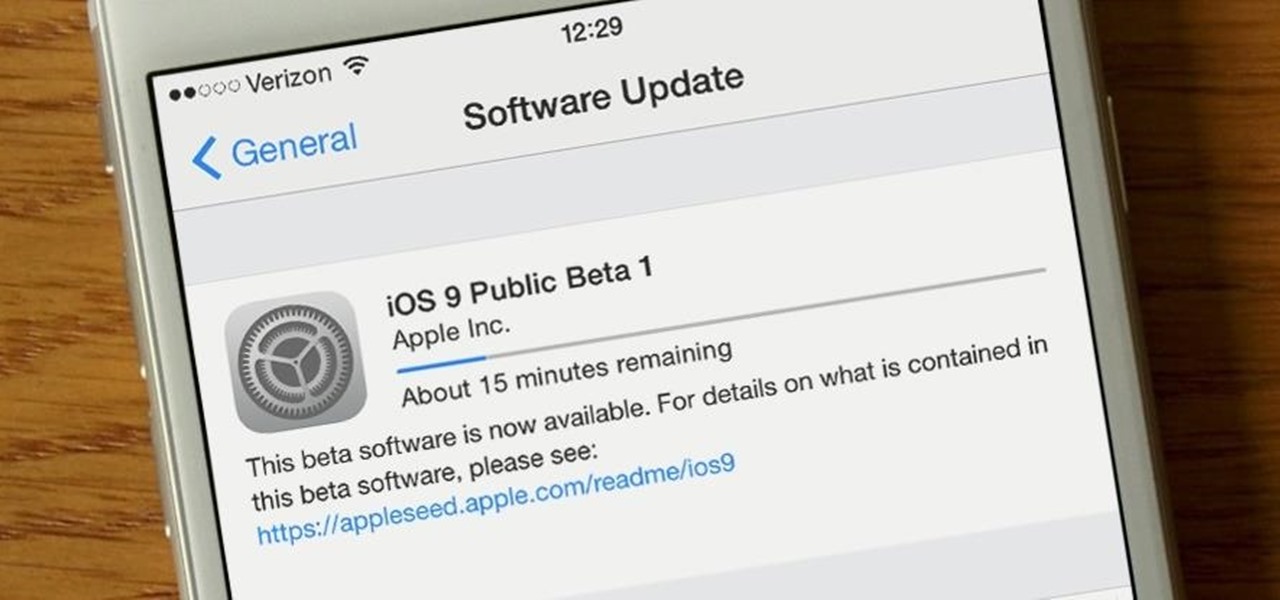
A month after its initial release to developers, iOS 9's Public Preview build is now available to everyone. If you signed up right from the start, you should receive an email or push notification letting you know of its availability. If you didn't, make sure to sign up for the Apple Beta Software Program.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.
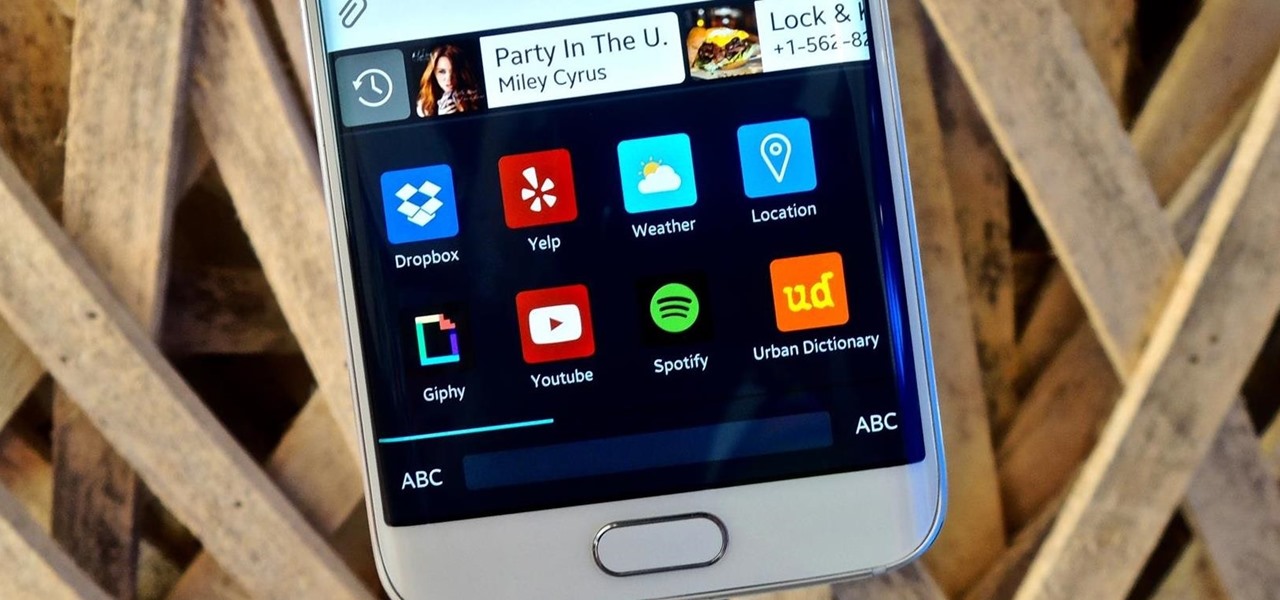
In addition to sharing emojis and GIFs, most of us also probably share various types of links through email or text, whether it be for a Google Maps location, a bar or restaurant on Yelp, or an awesome song on Spotify.

A recently discovered bug in iOS 8's Mail app by Jan Soucek can allow the maliciously-minded to quite easily phish your iCloud password without you ever thinking something has gone awry. Using a bug that allows remote HTML content to be loaded in place of the original email content, unsuspecting victims would be prompted for iCloud credentials in a popup that resembles the native one found on iOS.

To use Apple Pay in iOS 8, you had hold your iPhone to the card reader first, and then you could either switch to a different card or pay with your default one. Now, in iOS 9, you can access your Wallet (which replaces Passbook) on the lock screen before you get to the reader.
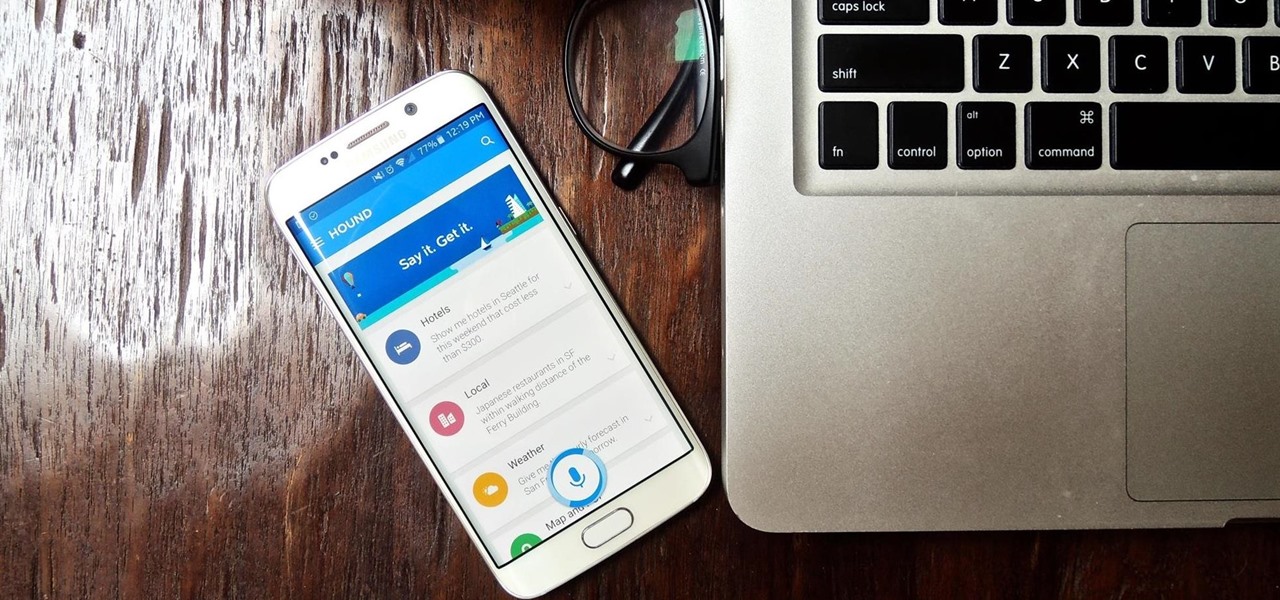
SoundHound's new virtual assistant application, Hound, is gaining a lot of buzz in the tech world—especially after a demo video showed just how awesome it works (it has amassed over 1.6 million views in under a week).

Android Lollipop, introduced an array of new features and aesthetics that pleased many loyal users. One of those additions being the new heads-up notifications. Taking subtle inspiration from iOS, these notifications are visually appealing and can be easily dismissed or expanded, but they do require that you take an action before they go away immediately. Of course, you can always wait 10 seconds for them to disappear, but that can be really annoying if you're in the middle of a game or editi...

If your iPhone is rebooting or your Messages app is constantly crashing, you might be the victim of an iOS exploit or just a buggy software update. While one problem sounds worse than the other, they both can get annoying real quick when you can't send any messages or even read new ones.
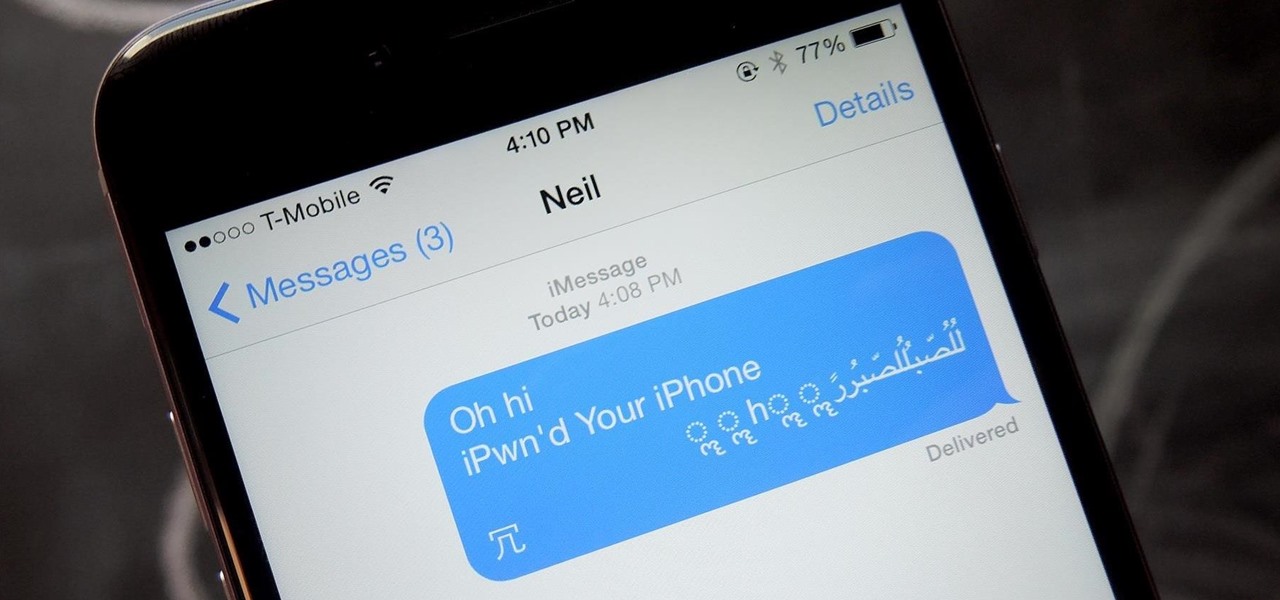
Thanks to a newly discovered iOS exploit, a text message can now ruin your day. It will literally cripple your iPhone, and the worst thing is that anyone with a phone that supports double-byte unicode can do it to you. While it initially sounded like bullshit, we tried it out several times here, and to our surprise, it worked perfectly each time.

Amazingly enough, some of us still have to worry about exceeding our monthly mobile data limits. You'd figure carriers would have given the customers what they want by now by offering truly unlimited plans, but with two conglomerates sitting atop the U.S. cellular market with fat pocketbooks that make for limitless lobbying, they can basically do whatever they want.
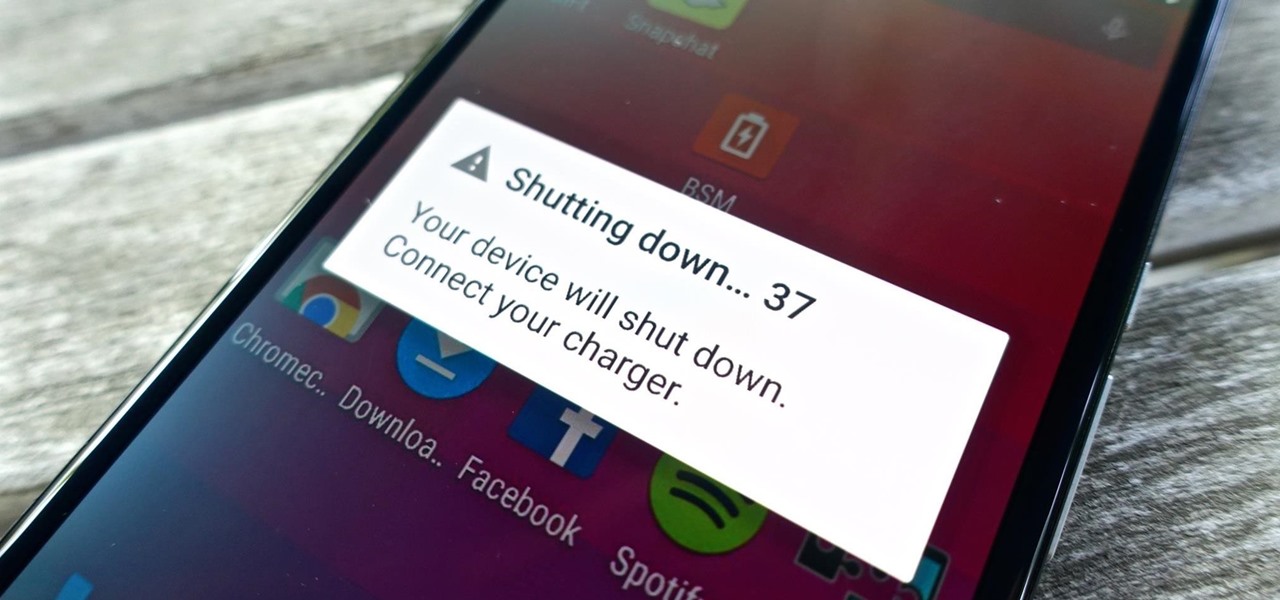
Even if my phone has only 1% of battery life left, I'll keep using it until I can get to a power source somewhere. Most times I never make it to a charger, and my device eventually powers down on its own.
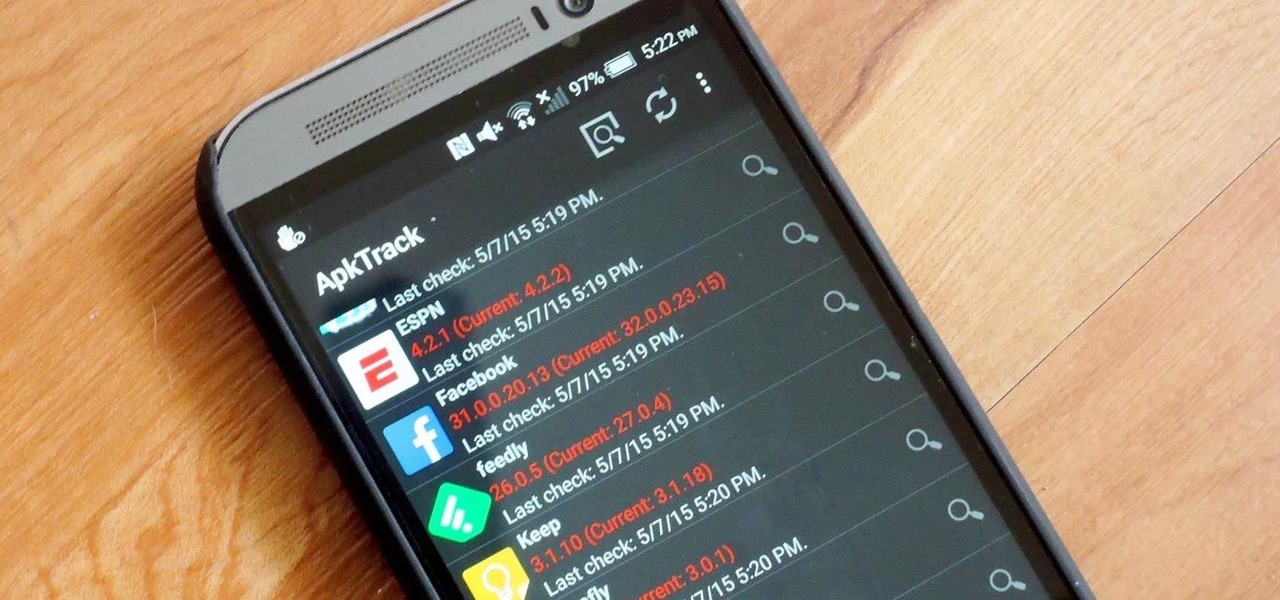
The Google Play Store may have fewer restrictions that its iOS counterpart, but that doesn't mean that all apps make the cut. Ad blockers and Xposed modules that bypass paywalls have never had a place on the Google Play Store, which makes tracking their app-updates a painful process.

While some of the additions to the emoji keyboard in iOS 8.3 have been criticized for actually doing the opposite of their intended purpose, they've been well received overall. But the biggest winner of the new emojis was one that actually wasn't even released—the "Vulcan salute" emoji.

As a Mac and Sasmsung Galaxy S6 user, I quickly realized that the two devices don't play well with one another out of the box, and using ADB commands to record my Android's screen isn't as simple as it is would be with a Windows PC.

Modern medicine utilizes cutting-edge technology more than ever, so it would only make sense that the powerful handheld computers we all carry around these days could play a big role in wellness.

As you're probably well aware by now, the Apple Watch isn't just for sending text messages and checking Instagram—you can also use it as your wallet. With Apple Pay compatibility, you can use your Watch to make purchases at any retailer that accepts the payment service.

If a tree falls in the woods and nobody is there to hear it, does it make a sound? If a person makes calls but doesn't have a Facebook account, are they even really a person? Yes, of course they are, but it just makes life easier when you're part of the world's biggest social network, as proven with Facebook's latest application, Hello - Caller ID & Blocking.

Smartphones are great at keeping us busy with games, social media, and messaging apps, but there has been a recent push for them to also help keep us safe (and I'm not talking about from hackers, though that is equally important).

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Show your significant other just how much you love them by surprising him or her with one of life's most precious, romantic gifts—bacon! Best thing is, this passionate treat works for any day of the year (Valentine's Day, a first date, anniversary, etc.), since love and bacon go hand in hand.