For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

In 2018, augmented reality went from the vague promise of interesting things in the near future to tangible developments in software and hardware, proving that immersive computing is indeed the future.

For many, phones are starting to replace televisions as the primary device for watching videos. Thanks to their portability and easy to use apps, it's often simpler to watch Netflix, Hulu, YouTube, or Prime Instant Video on the smaller screen. But not every phone is suited to fit this need, so we did some testing to find the best of the best when it comes to streaming videos.

All of the new iPhones from 2018 were released with dual-SIM support, but none of them were capable of actually using the eSIM in iOS 12, only the physical nano-SIM. But on iOS 12.1 and later, you can finally take advantage of eSIM so you can have, say, a business and personal plan on your iPhone XS, XS Max, or XR at the same time.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

Perhaps you've thought about rooting your OnePlus 5, but thought again when you heard SafetyNet would prevent you from using apps like Google Pay, Pokémon GO, or Netflix. Those are valid struggles when you root using traditional methods. There are no such worries when using Magisk, as it masks the fact that your device has been modified.

If you've ever been on the receiving end of a threatening phone call, you'll immediately know the value in being able to record phone conversations on your iPhone. Beyond that extreme example, however, recording calls is still an extremely useful feature to have for important conversations like business meetings and verbal agreements, and it's totally doable with a third-party app.

You don't need an obsessive ex stalking you to benefit from the ability to record calls on your iPhone in a pinch. Besides protecting yourself from nefarious intent, recording important conversations like verbal contracts and agreements can help you cover all your bases and ensure you're insulated from any potential liabilities that may appear down the road.

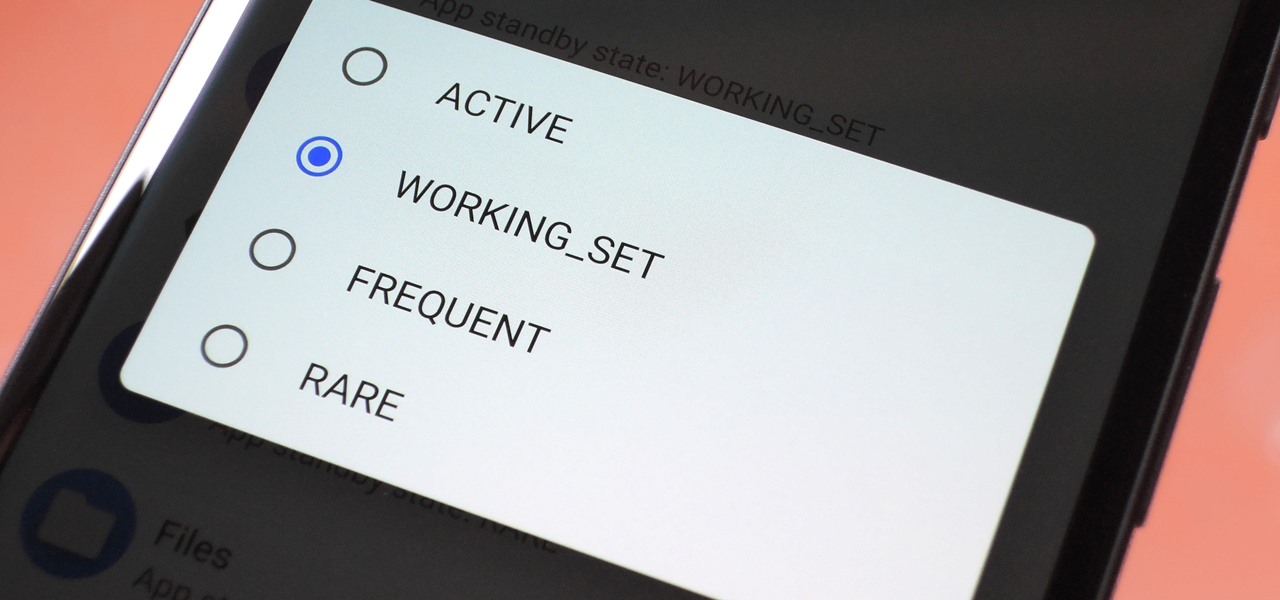
Battery drain is a major pain point for Android users, though that promises to change thanks to Android Pie's new Adaptive Battery feature. But Google hasn't said much about the inner workings of this feature, only publicly stating that it uses AI to boost battery life. So we dug in to find out what's really going on under the hood.

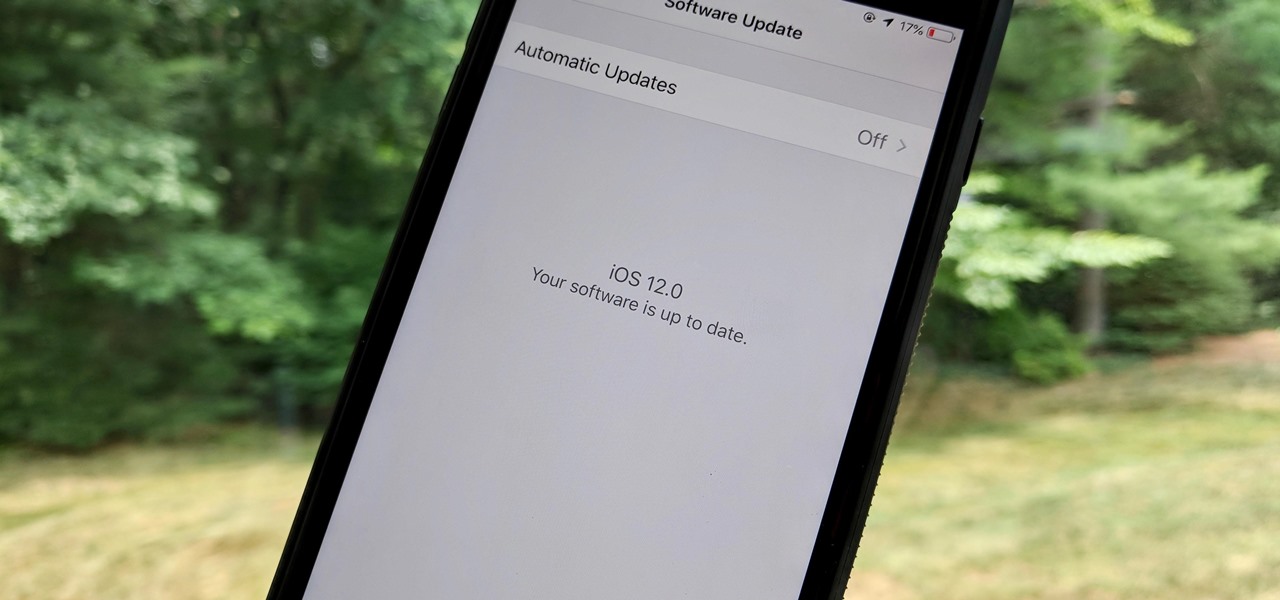
Apple's latest mobile operating system for iPhones, iOS 12, was released to everyone Monday, Sept. 17, and it's the same exact build that developers and public beta testers received as the "golden master" on Sept. 12, the day of Apple's 2018 special event. Install it to start taking advantage of the 100+ features iOS 12 has to offer right now.

The world finally received its first official look at the iPhone XR, XS, and XS Max, Apple's 2018 suite of smartphones, on Wednesday, Sept. 12. If you're someone looking to get their hands on one, two, or three of these new iPhones as soon as possible, you'll need to know all of the important dates so you don't end up missing out to others ahead of the line.

When rumors first emerged of Sony's Xperia XZ3, many of us wondered why. With the Xperia XZ2 just releasing in April of this year, why is Sony already releasing its successor? But now that it is officially announced, it makes a bit more sense, as what Sony is calling the XZ3 is actually more like the XZ2S.

One of the primary marketing tactics used by Magic Leap in promoting the Magic Leap One was selling early adopters on the "magic" contained within the device. On Thursday, some of that magic was uncovered as the Magic Leap One was completely disassembled by repair engineers, revealing the delicate innards of the device and detailing how it delivers its augmented reality experiences.

For the second time in a row, Apple pushed out a new iOS 12 developer beta on a Monday, and for the first time this round, they've done it only one week after the last one. While the August 6 release of iOS 12 developer beta 6 doesn't contain a wealth of updates, there are still a few things you'll want to know about.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

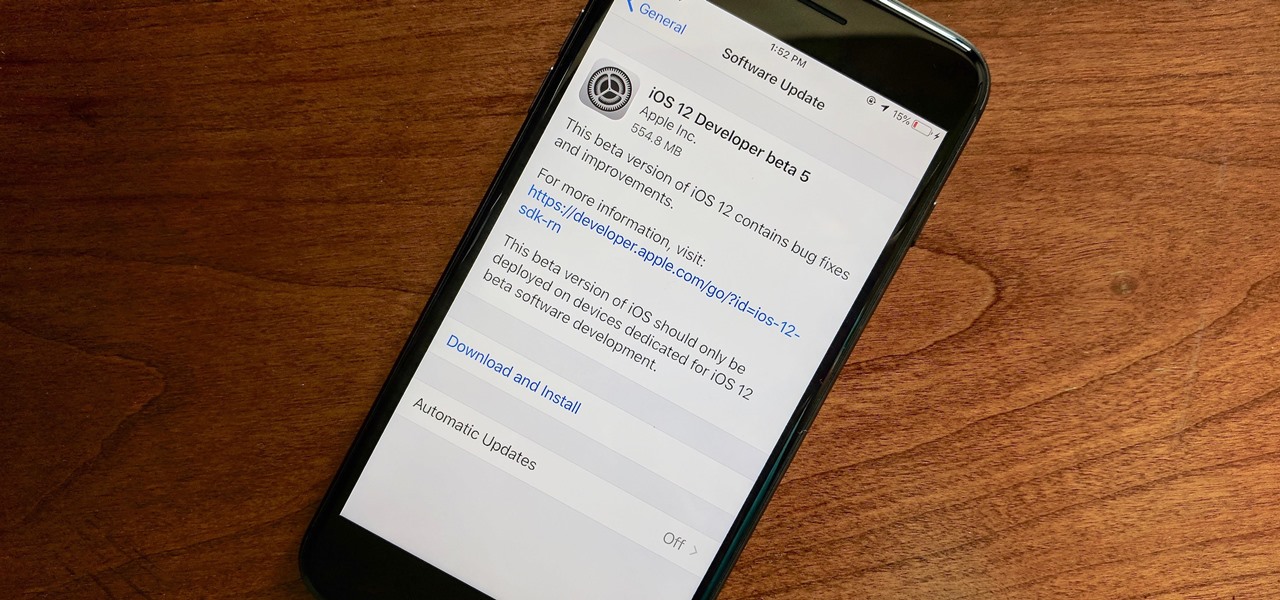
Apple released the fifth developer beta for iOS 12 on Monday, July 30, only 13 days after the release of dev beta 4 and 12 days after public beta 3. Until this release, Apple kept a consistent two-week schedule for developer beta updates, so we were a little surprised to see this one drop one day early.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

As the official release of iOS 12 nears closer each day, Apple continues to update its betas. The company released the fourth beta of the upcoming software to developers Tuesday, July 17, exactly two weeks after the release of the third developer beta which came out just a few days before the second public beta.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

A new study published by American University demonstrates how Pokémon GO and other augmented reality games can help city governments bring communities closer together.

It always helps to be prepared for the worst. This applies to our phones now more than ever, as we depend on them to be our record keepers for text messages from friends, family, and coworkers. If you ever lose or severely damage your phone, having a backup of your precious texts gives you the peace of mind of knowing that you can always get them back.

Apple's own Photos app received some pretty amazing updates in iOS 11, but does iOS 12 have what it takes to one-up last year's Photos improvements? We think so.

Apple knows their products can be addicting, and with iOS 12, they are doing something about it. With the help of Screen Time and few other new tools, it should now be a lot easier to get off your phone and enjoy life in the real world.

Apple released iOS 12 on Sept. 17, and most of the announced features have been released for the iPhone's latest available operating system. However, some brand new features can be accessed with Apple's latest beta, iOS 12.4. If you want to try out all its new features before everyone else, you can install the developer or public beta on your iPhone right now.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

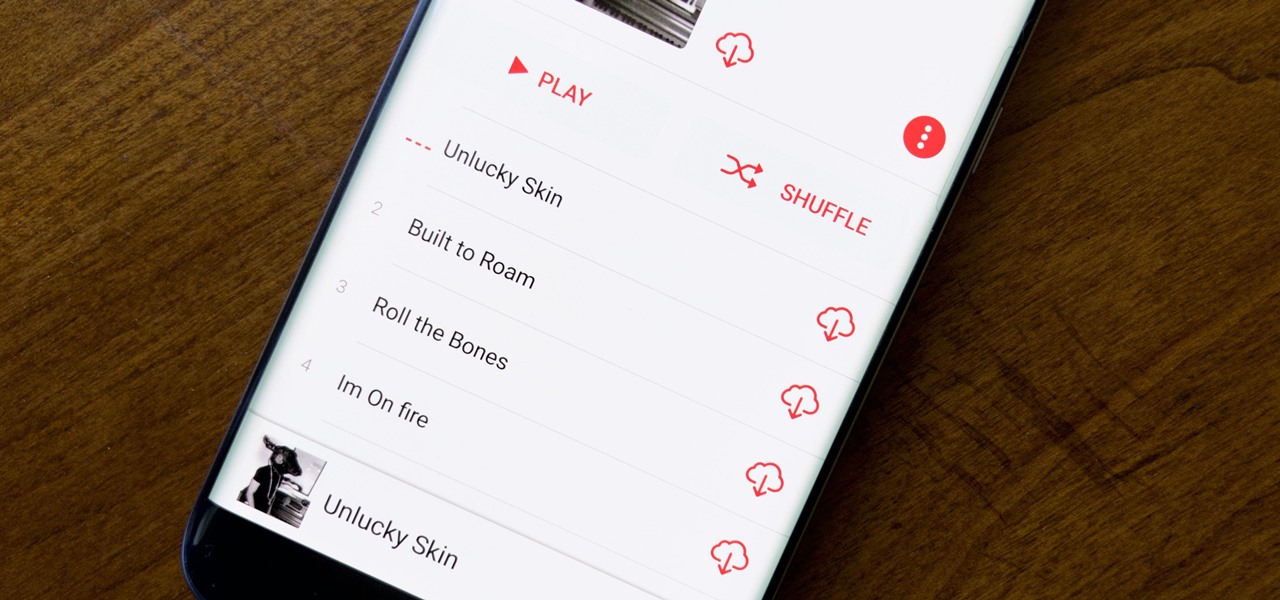
For most carriers, "unlimited" data plans aren't really unlimited, and they still cost more than data limited plans. So while subscribing to music streaming services and storing your own music library in the cloud may be more convenient, it may eat your data up like candy. To keep that from happening, try downloading tracks from Apple Music for offline playback.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

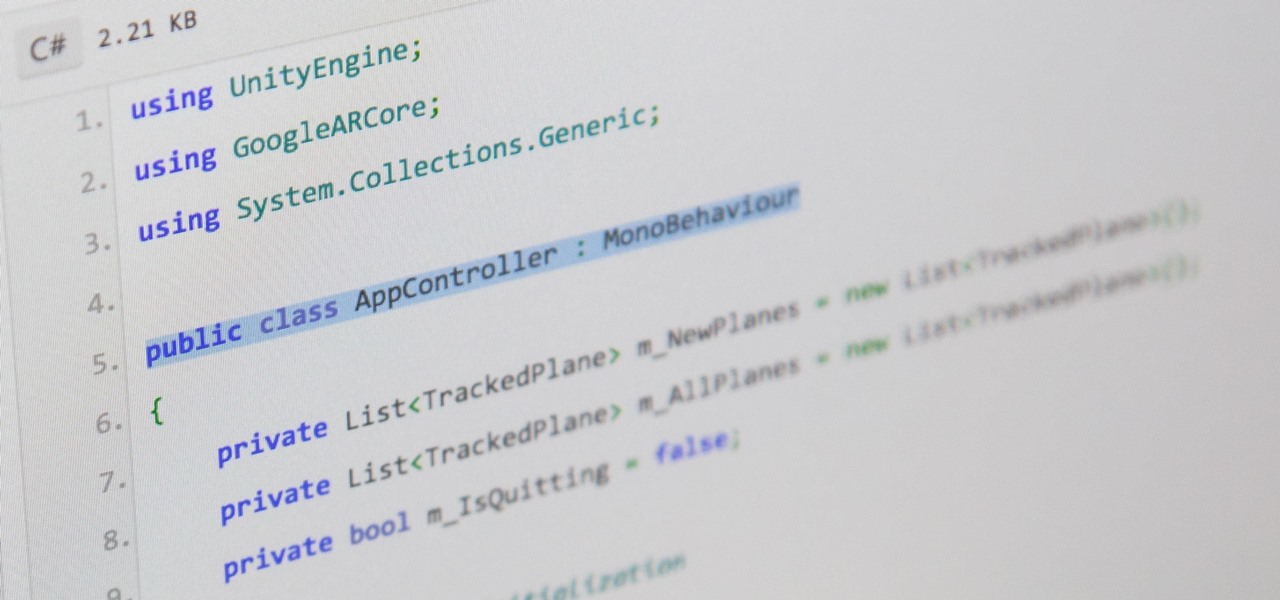
There are hundreds, if not thousands, of programming languages and variations of those languages that exist. Currently, in the augmented reality space, it seems the Microsoft-created C# has won out as the overall top language of choice. While there are other options like JavaScript and C++, to name a few, C# seems to be the most worthwhile place to invest one's time and effort.

| Update: ZTE's issues with the US government have finally been resolved. Check out the details below.

After more than a year and a half of silence, the rumors have morphed into reality: Microsoft has finally released an update for the HoloLens. And with that update comes a collection of new features that hint at big plans for the HoloLens this year.

Update February 25: The Nokia 9 PureView was announced at Mobile World Congress! Read all of the official specs and details at our full rundown of Nokia's latest flagship.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

If you recently received your new Galaxy S9 or S9+, you're probably excited to try out all of the features the flagship offers. While many of the features are self-explanatory and easy to access, there are a handful of very useful items that Samsung has buried in the settings menu. Enabling these hidden features will help you unlock the true power of your new device.

Unless you own an Exynos model, there won't be much development on the custom ROM front for the Galaxy S9. But that doesn't mean you have to put up with all of the UI quirks from Samsung Experience (née TouchWiz). With a little work, you can give your S9 a stock Android makeover, even without root.

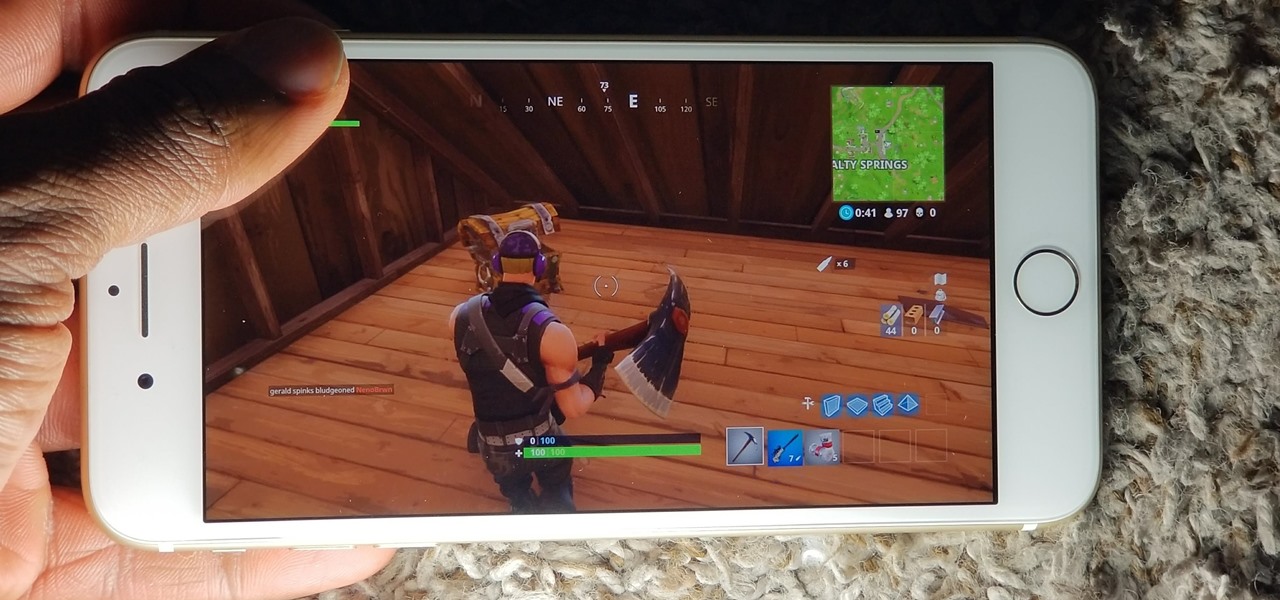
While playing Fortnite Battle Royale, you may have noticed a few players wearing different outfits or using fancy dance moves. These are cosmetic items that can only be obtained by unlocking them. However, unlocking items in Fortnite is a little different than many free-to-play games.

After two years of poor sales, LG decided to shake up its mobile division. New executives are at the helm, and changes to their flagship lineups are already underway. Specifically, the V series is expanding, as LG announced the second new device in the series, the LG V35 ThinQ.

They're finally here — Samsung has officially revealed the Galaxy S9 and S9+, which run Android Oreo out of the box. Since we've spent plenty of time with the Oreo beta for the Galaxy S8, we already know about some of the best new software features coming to the Galaxy S9. Like previous updates, Samsung has enhanced its software with a fresh look and brand new functionality.

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.