Considering Rovio Entertainment quite literally owes its existence to Apple and the App Store, it may ruffle a few feathers that the company has opted to aim the augmented reality debut of its blockbuster Angry Birds franchise at Magic Leap instead.

By far, one of the biggest advantages to having a jailbroken iPhone is being able to apply custom themes to Apple's user interface and truly set your device apart from the rest of the crowd. And if you want to change your iPhone's app icons from rounded squares to circles for an entirely unique look, there's nothing stopping you.

For the augmented reality hardware industry to progress towards the consumer segment, display technology needs to get better. Investors recognize that, and they are showing AR display makers the money.

Yesterday, I talked about what I think is the most immediately mainstream-friendly app on the Magic Leap One is (Screens), and now we'll touch upon the runner-up: Helio.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.
Following San Francisco-based Occipital's successful Structure Sensor Kickstarter campaign, the release of its Bridge AR/VR headset, as well as a string of technology and company acquisitions, the company has built a rather strong name for itself in the AR community. And now, with the first public release of its Bridge Engine on Thursday, the company continues to expand the features its platform has to offer, with hopes of bringing in more developers to utilize it.

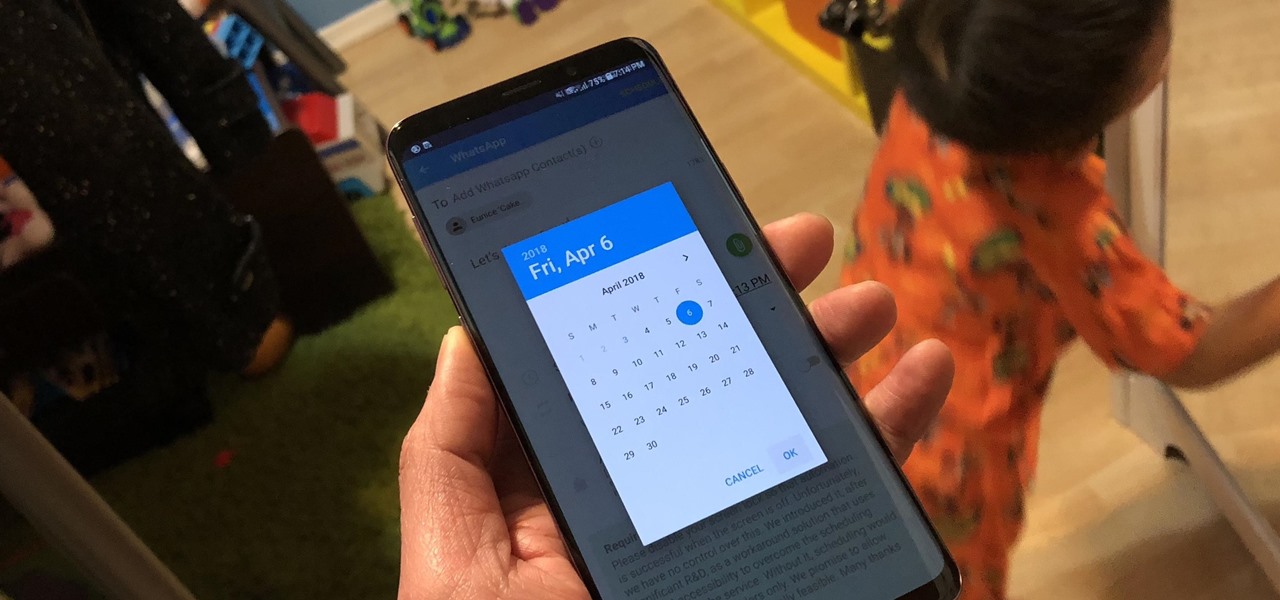
Great ideas often strike at random times, but messaging friends and loved ones at an inopportune hour not only risks their wrath, but also increases the chances of your message not being paid proper attention to. Thankfully, there's an app that lets you create and post WhatsApp messages at the time you wish for maximum effect.

Because augmented reality is still so new to so many people, there are a number of would-be experts opining online, often repeating basic facts anyone with a spare 15 minutes can find on their own. That's why it's important to point out when someone delivers what could be considered the ultimate cheat sheet for ramping up your AR IQ if you're unfamiliar with the finer points of the space.

After two years of poor sales, LG decided to shake up its mobile division. New executives are at the helm, and changes to their flagship lineups are already underway. Specifically, the V series is expanding, as LG announced the second new device in the series, the LG V35 ThinQ.

Augmented reality is beginning to leak out into the mainstream world. This is thanks, in part, to ARKit and ARCore. These releases turned the current smartphones owned by millions of Apple and Android users into AR-capable machines. And while there are definitely some awesome use cases for mobile AR, the real future in AR is headworn.

Snapchat has broken new ground in its augmented reality advertising efforts, as BMW has opted to show off its new X2 model in AR with the Augmented Trial Lens.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

If you have a taste for sweets, you have at least one thing in common with mosquitoes. While too much sugar is unhealthy for humans, a new product makes sweets deadly to mosquitoes.

Augmented and virtual reality continues to be a hot commodity among tech investors, with more than $800 million invested in AR/VR companies in the second quarter alone and global tech leaders like Samsung focusing their investment strategies on the emerging field.

That soil under your feet is not just dirt. It is teeming with life that may not change as fast as we would like when challenged by global warming.

We know that healthcare-related facilities can be fertile ground for antibiotic-resistant bacteria, but recent research suggests your produce aisle might be too.

The release of Unity 5.6 brought with it several great enhancements. One of those enhancements is the new Video Player component. This addition allows for adding videos to your scenes quickly and with plenty of flexibility. Whether you are looking to simply add a video to a plane, or get creative and build a world layered with videos on 3D objects, Unity 5.6 has your back.

When a new jailbreak method comes out, Apple is quick to patch the vulnerability it exploits by issuing a new iOS update. If you were to accept such an update, you'd no longer be able to jailbreak your iPad, iPhone, or iPod touch unless you could roll back your firmware to a version that could be jailbroken. But Apple even takes things a step further and stops signing older iOS firmware versions, which makes downgrading next to impossible. This is where your SHSH2 blobs come into play.

Colorado State University scientists have developed new tech that quickly identifies the presence of Zika virus in mosquito populations — and in human body fluid.

Antibiotics used to prevent diseases in livestock are creating a world of hurt for humans and the soil we depend on for food. Bacterial resistance to antibiotics is a global health issue. The overuse, underuse, and poor use of these life-saving drugs is rapidly removing them as a treatment option for serious infections in humans—plus bacteria are naturally adaptive.

When we talk about driverless technology, the go-to companies are usually Waymo, Uber, or Tesla. However, traditional automakers like Ford and GM are also staking claims to the driverless and advanced driver assistance spaces.

Typing on a mobile device has come a long way since the days of flip phones. Today, there are awesome keyboard apps like Gboard, which integrates Google search features and makes typing a breeze. But the whole experience still stands to improve if you take some time to learn a few useful tips.

As fun as it is to see Fido's face light up when you feed him table scraps, American dogs are getting fat. The good news is that research is homing in on nutritional strategies to boost canine capabilities to maintain a healthy weight.

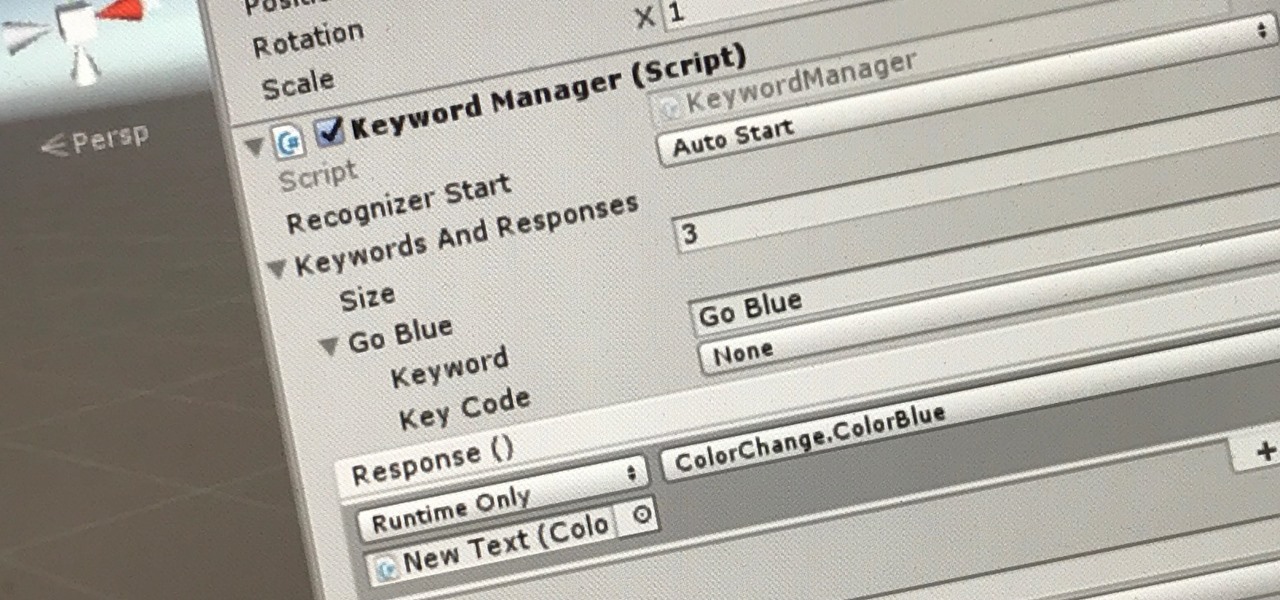
The HoloToolkit offers a great many, simple ways to add what seems like extremely complex features of the HoloLens, but it can be a bit tricky if you're new to Windows Holographic. So this will be the first in an ongoing series designed to help new developers understand what exactly we can do with the HoloLens, and we'll start with voice commands.

Augmented, mixed, and virtual reality are all a little bit different, but as many expect—including Metavision—the continuum of our next realities will converge and give us one head-mounted display (HMD) platform that can do it all. If Vrvana, a Canadian company building AR and VR headsets, succeeds, that convergence could begin as early as next year.

The future of augmented and mixed reality offers many possibilities, mostly because we're still figuring out everything it can do. While Meta is open to exploration, they've spent a lot of time thinking about what the future of this technology will be.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...

This is my first How-To on Null-Byte, so I hope it's not too complicated written, because I am not a native english speaker. I don't use pictures, but this Tutorial is a good supplement for my updated Tutorial here.

Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private detectives, and many other organizations.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

In the digital age, maintaining your privacy is a never-ending battle. All sorts of companies and agencies have access to your data, and quite a few can eavesdrop on almost every method of modern communication.

If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streaming services don't work on your Chromecast or Chromecast 2.

It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

Microsoft's new voice-enabled virtual assistant, Cortana, is a lot like a blend of Siri's personality and Google Now's predictive capabilities—but the best part is it's baked right into the taskbar in Windows 10.

Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house.

When a Houston mom got tired of her kids seemingly refusing to return her calls, she decided that she'd take action. Sharon Standifird's vision was to create an app that would somehow force children to get into contact with their parents. Having no experience with app development, Standifird quickly taught herself the ropes and hired an experienced developer to help with coding.

With Safestrap bringing custom recovery functionality to the AT&T and Verizon Wireless variants of the Samsung Galaxy S5, it's high time we covered this process for all other versions of the GS5.