There are over 60-something Android apps cluttering my app drawer. While I'm constantly on the look out for new mods and apps to install, the default way of managing them is cumbersome and just feels unintuitive. I mean, who on Earth would wants to individually manage each app on their device?
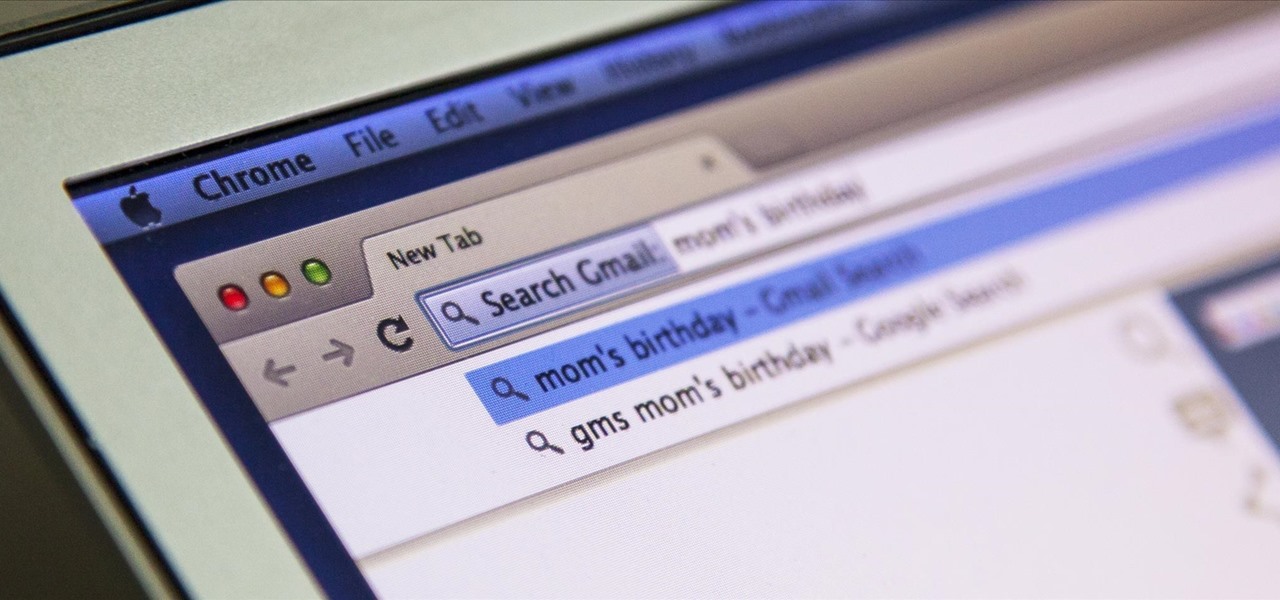
I'm all about saving time. If there's a quicker way to do something, I'm going to find it. For this reason, whenever I need to search through old emails or compose new ones in Gmail, I do it directly from Chrome's address bar, or as Google likes to call it, the omnibox—and you can, too.

If you're like me, you spend a lot of time on your computer, which can be damaging to your eyes in the long run. Studies have shown that staring at a computer screen or television up close for extended periods of time can have harmful effects on your vision.

Journals are a great source of hilarity and embarrassment, detailing everything from your elementary school crushes to those super awkward middle school dances. While rereading your old hand-scrawled entries might make you cringe, that old journaling habit could benefit you as an adult.

Google has finally announced the newest flavor of its mobile OS, Android L (Lollipop?), and I couldn't be more excited. While we won't see its official release until the fall, there are still some features we can get our hands on right now.

One of the best things about the Nexus line of devices is the ease with which one can achieve root. Plug your phone into your PC, download a couple files, type a few commands, and you can be rooted within 30 minutes. No muss, no fuss, no carrier-locked bootloaders.

Anyone who has rooted their Android device has likely used a tool called Android Debug Bridge, better known as ADB, at some point during the process. For most, that is their only interaction with the ADB, but to be a true Android power user, you need to really know the tools at your disposal.

Safari has some cool new features in iOS 8, but the app that seems to have gotten the biggest update so far is Messages. A lot of the new Messages features were discussed during Apple's developers conference, but we found many others and picked out our favorite hidden ones below.

I dabble in video editing, and when working on even the shortest of motion graphics clips, the exported files take up quite a bit of space. For all of you heavy Mac users out there, I'm sure you know my pain.

Apple just unveiled iOS 8 at the Worldwide Developer's Conference, and it has a lot of exciting features to play around with. Unfortunately, it won't be available to the public until this coming fall—but that doesn't mean you can't get it right now.

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.

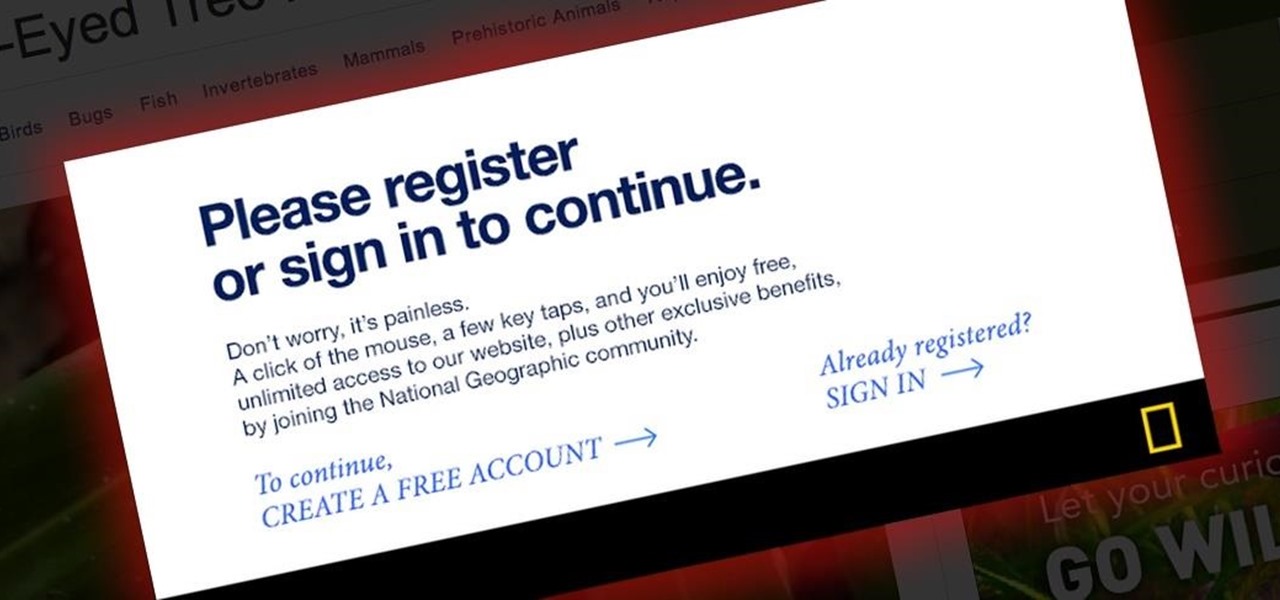
Last night, I was reading a riveting National Geographic article on the green-eyed tree frog, until I was quickly interrupted by an annoying popup asking me to "create a free account" or "sign in." Really, I'd like to do neither. I just want to read about tree frogs.

Are you searching for a homemade cat repellent solution? This article will cover natural indoor and outdoor deterrents for every scenario where cats are causing trouble. The first part will cover home remedies for training cats to stay away from furniture and other restricted areas inside your house. The second part will cover outdoor repellents for keeping cats away from your garden, plants and yard. Step 1: Indoor Repellents for Training Cats

The lengths people will go to for a grilled cheese sandwich are amazing. They'll use irons, wafflemakers, or whatever appliance that produces enough heat to produce the perfect combination of golden, grilled bread and oozy, melting cheese. I personally favor my cast-iron skillet or the oven for making a really great grilled cheese sandwich. If I'm feeling lazy, then a toaster oven will do. But what if you're at work or in a dorm and the break room only has a toaster?

Spiders are common pests that typically prefer to live outdoors. However, insects and warmth will eventually attract them into our houses. They like to spin their webs in corners, crevices and unused areas of your house. Most species are harmless and even act as a natural repellent for getting rid of other insects. However, in some cases, spiders can be very dangerous. Whichever the case may be, they are scary and people are always looking for natural ways to get rid of them.

Recently, Sprint announced a partnership with Harman Kardon to deliver exclusive sound FX technology to their variant of the HTC One M8. The joint effort between the two companies is both to entice customers to switch to Sprint as well as improve the overall audio quality coming from the already extraordinary BoomSound speakers. But while this is great for new and existing Sprint customers, it does leave the rest of us out in the cold.

Welcome back, my hacker noviates! In a recent post, I introduced you to Shodan, the world's most dangerous search engine. Shodan crawls the globe from IP to IP address, attempting to pull the banners of each web-enabled device and server it finds.

Update: May 7, 2014: Google's Camera has seen its first update, with a small yet important addition baked into the app—the ability to take pictures while recording a video. Now, when in video mode, simply tap on the screen to take a picture, while your recording continues as normal. The update to version 2.1.042 is set to hit today, but if you haven't yet received it, apply it manually by downloading the apk here.

You've unlocked your bootloader and rooted your HTC One running KitKat, but there's still one lingering aspect of security you've yet to rid yourself of—S-On—the extra security measure HTC implemented into Sense.

LastPass is a password manager that's been around for some time, and has finally made its way over to Android for use with apps, not just websites.

Okay, so you're rooted and need to return your Nexus 5 to its stock firmware. Whether it's because you need to send your phone in to the manufacturer to fix a defect or you just want to use the device's over-the-air updating feature, unrooting and returning your Nexus 5 back to its fresh-out-of-the-box state is a fairly simple process with the right tools.

I still remember when I had to get up from my comfy spot on the couch to change the channel on my old television. So for me, the remote control may be one of the most underrated inventions of the last century. These days, remotes take on all sorts of shapes, not just the typical brick, but also in the form of watches and cell phones.

If you've never played Cards Against Humanity, it's time to get initiated. Originally funded through Kickstarter, the free to download card game is basically an obscene version of Apples to Apples.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).
What is Programming? Why need to learn? How to get started? Which language to choose? While surfing web, you must be encountering various softwares, games, etc. and might be thinking to make one, but don't know where to start. Here, I am starting series in Programming.

The Problem If you are working on a car restoration project, then you are going to faced with rust damage. This problem can’t be overlooked, as the entire project depends on repairing and eliminating rust. This would be like laying down new carpet to a house that was flooded, without cleaning the mess and making necessary repairs before laying the carpet down. The problem will still be there and the new carpet will be ruined.

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

The flexibility within Android is pretty amazing. Unlike iOS, you can make a lot of modifications with nothing more than a download from Google Play, but to really step up your softModder game, you'll need to go a little further.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

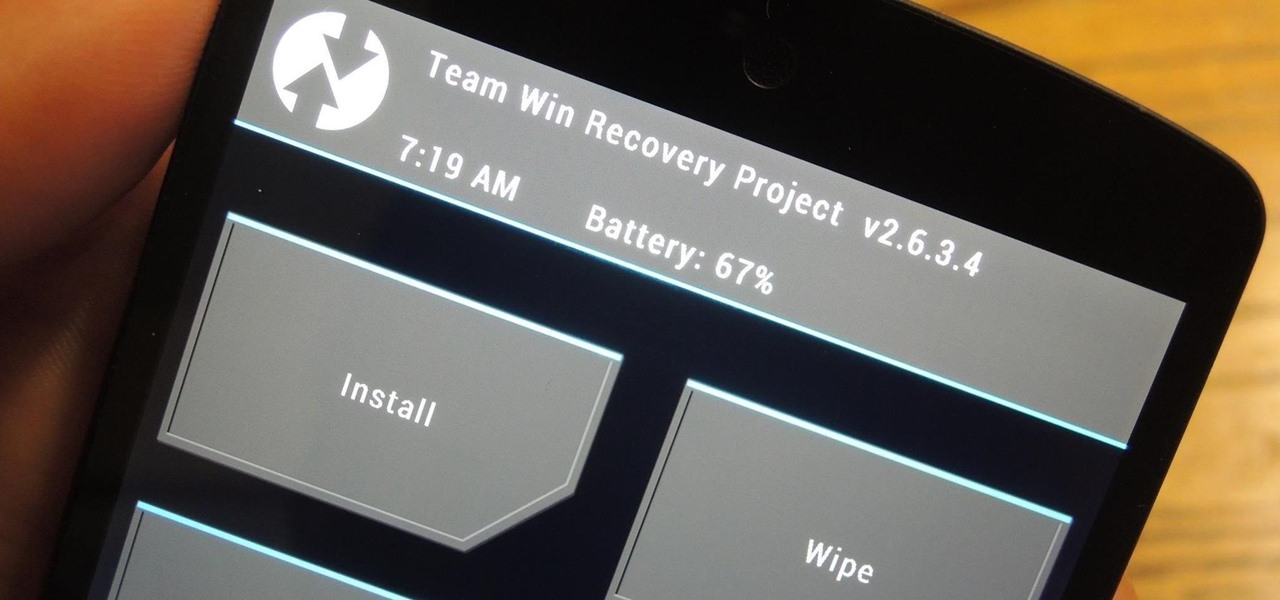
A rooted Android device means we're on our way to some truly amazing customization options. But there may be a few steps left to completing that journey, and a major one is installing a custom recovery.

It's time. You've experimented with apps from the Play Store, you've switched your lock screen, and maybe you've taken different launchers out for a spin. If, throughout your tinkering, you've found yourself chanting, "More. More. Give me more!" then now is the time. It's time to root.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Automation applications bring the future a little closer. If you've seen Minority Report or other futuristic sci-fi movies, the intrigue of having your electronics work independently is something we can all appreciate.

As an avid music fan, Spotify and Pandora only partially satisfy my needs on a day-to-day basis. When there's a certain obscure or underground band that I want to listen to, I'm relegated to using YouTube as my main music player source.

Sometimes... no, most of the time, I don't want to do anything, so I was excited to find a developer teaming up with Sir Isaac Newton to create an application that encouraged my slothfulness.

Welcome back, my budding hackers! In my continuing series on Linux basics for aspiring hackers, I now want to address Loadable kernel modules (LKMs), which are key to the Linux administrator because they provide us the capability to add functionality to the kernel without having to recompile the kernel. Things like video and other device drivers can now be added to the kernel without shutting down the system, recompiling, and rebooting.

The newest Android operating system, Android 4.4 KitKat, has been unleashed with the arrival of the Nexus 5, and soon to be rolled out to other Nexus devices and Google Play Edition smartphones any day now. Only problem is, the Samsung Galaxy S3 isn't getting 4.4 for a very long time. It doesn't even have 4.3 Jelly Bean yet.

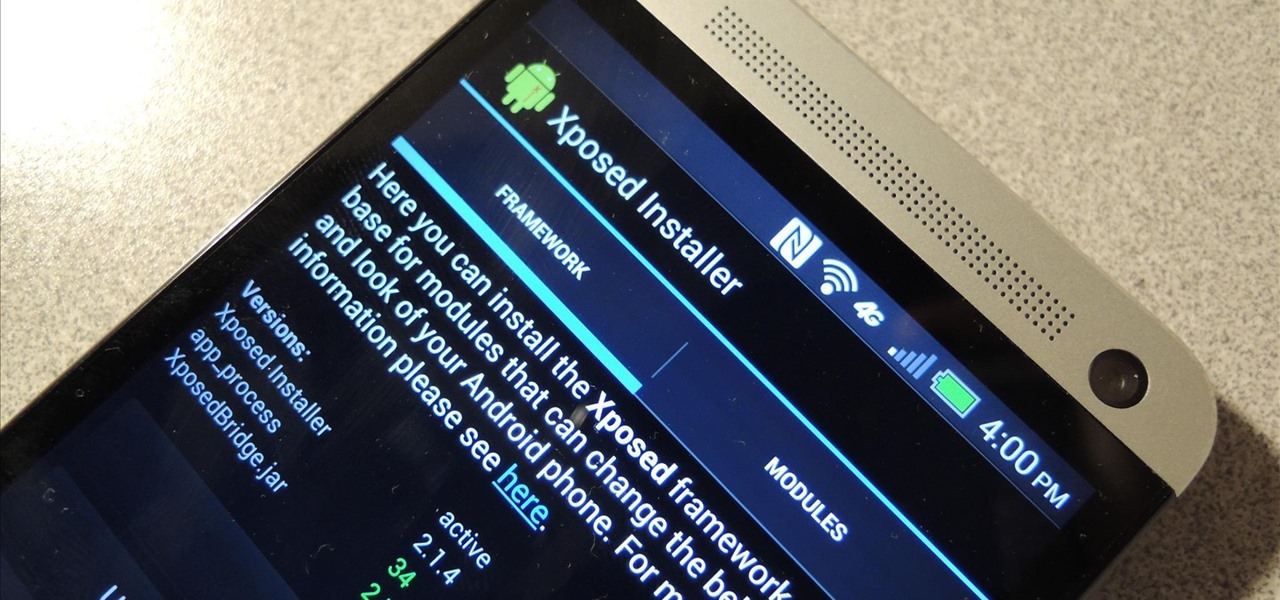
Update: The installation process for Xposed Installer is now dead simple—check out our updated guide!

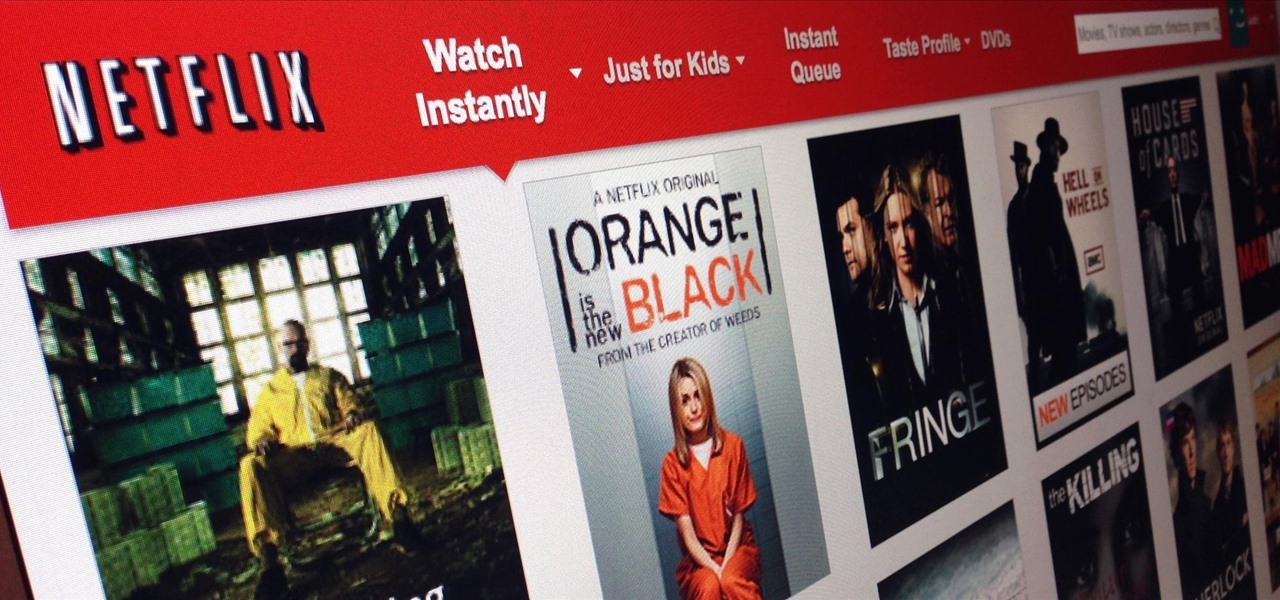
Considering that the average movie ticket these days is $8.38, it's not much of a surprise that Netflix is kicking ass. The same amount will get you a full month of unlimited streaming, and you don't even have to leave your couch. While no one's arguing that it isn't a great deal, the biggest issue most users have with the service is the limited amount of available content. Anything?

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.