
How To: Make fresh rolled sushi
Learn how to make delicious sushi like a real chef. You may think sushi is just raw fish, but you’d only be half right. It’s actually the combination of fish and rice – and how it’s combined is an art form in itself.


Learn how to make delicious sushi like a real chef. You may think sushi is just raw fish, but you’d only be half right. It’s actually the combination of fish and rice – and how it’s combined is an art form in itself.

Your ability to control exposure in the Camera app is much better in iOS 14. Instead of setting the exposure for a single shot, you can also lock an exposure compensation value for an entire session while you take photos and videos. A session ends as soon as you exit the app, but you can also remind your iPhone to use your last used ECV the next time you open Camera.

A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.

The results of Microsoft's $480 million contract with the US Army are on display and users continue to test the suped-up version of the HoloLens 2.

The end of year surprises keep on flowing from the Plantation, Florida offices of Magic Leap. This time, it's yet another game from the company's old partner Insomniac Games, and it's called Strangelets.

Over the past year, Magic Leap has teased its cross-platform vision of the AR cloud, which it dubs the Magicverse. While the company shared a timeline for its debut next year, it also served up new developer tools for the present.

Apple slowly rolled out its new credit card, Apple Card, throughout August, but announced on Aug. 20 that it's now available to all qualified users in the US. Here's the problem: it's not totally obvious how to apply. Without any notification, directions, or clear settings, how do you even fill out an Apple Card application? Luckily for you, we're here to show exactly how to find it.

The $35 Raspberry Pi is an amazingly useful single-board computer (SBC) with a good balance of price, performance, and connectivity options. But for some projects, it just isn't enough. Whether you need more computing power, a smaller size, or better machine-learning capabilities, there are other options available.

During the recent Augmented World Expo (AWE), we had a chance to try out the Lenovo ThinkReality A6 AR headset. Unfortunately, the experience was all downhill from there.

While the 49th Annual Gay Pride Parade and Festival will take place on Santa Monica Boulevard and West Hollywood Park, revelers will also be able venture Northeast to the TCL Chinese Theater on Hollywood Boulevard to continue celebrating via Snapchat.

If you need some help expressing how you feel to your mom for Mother's Day, Snapchat and Facebook are here with some augmented reality help.
The marketing team for Marvel Studios is doing "whatever it takes" to make sure you see Avengers: Endgame when it hits theaters in a couple of weeks, including offering an updated set of augmented reality Playmoji for the Playground app on Google Pixel.

To borrow from the canon of Game of Thrones, what is dead may never die. And while the Meta Company that we knew this time last year is no more, the patent infringement lawsuit filed against the company lives on.

While the betting lines on iPhones with depth-sensing, rear-facing cameras in 2019 have already been established, a new report adds some certainty to the notion that the iPhone will get new AR superpowers later this year.

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

This week, we continued our NR30 series highlighting the leaders of augmented reality space by profiling the venture capitalists and strategic corporate investors that sustain the industry.

Have you ever wondered what it would be like to try to survive The Purge as depicted in the popular movie series? Well, thanks to augmented reality, now you can.

The spirit of Google's Tango augmented reality platform lives on at Vivo, a China-based company that has developed its own 3D sensor for mobile devices.

A new set of APIs for Unity promise to make it easier for developers to publish apps that support both ARKit and ARCore.

Pixar's Incredibles 2 has entered the fray as the latest sequel in a summer of highly anticipated follow-up films and, like its peers, it also has an augmented reality experience to promote its presence in theaters.

The Essential Phone was undoubtedly one of the most underrated phones of 2018. It launched with buggy software and camera problems, but the company worked diligently to push out updates. Many Android enthusiasts were anxiously waiting for the Essential 2 release later this summer. Unfortunately, news today from Bloomberg indicates that Essential will not release a phone in 2018.

On Thursday, Osterhout Design Group (ODG) revealed a new, specially-crafted oxygen mask that uses the same augmented reality technology from its smartglasses to assist FedEx Express pilots navigating dangerous conditions.
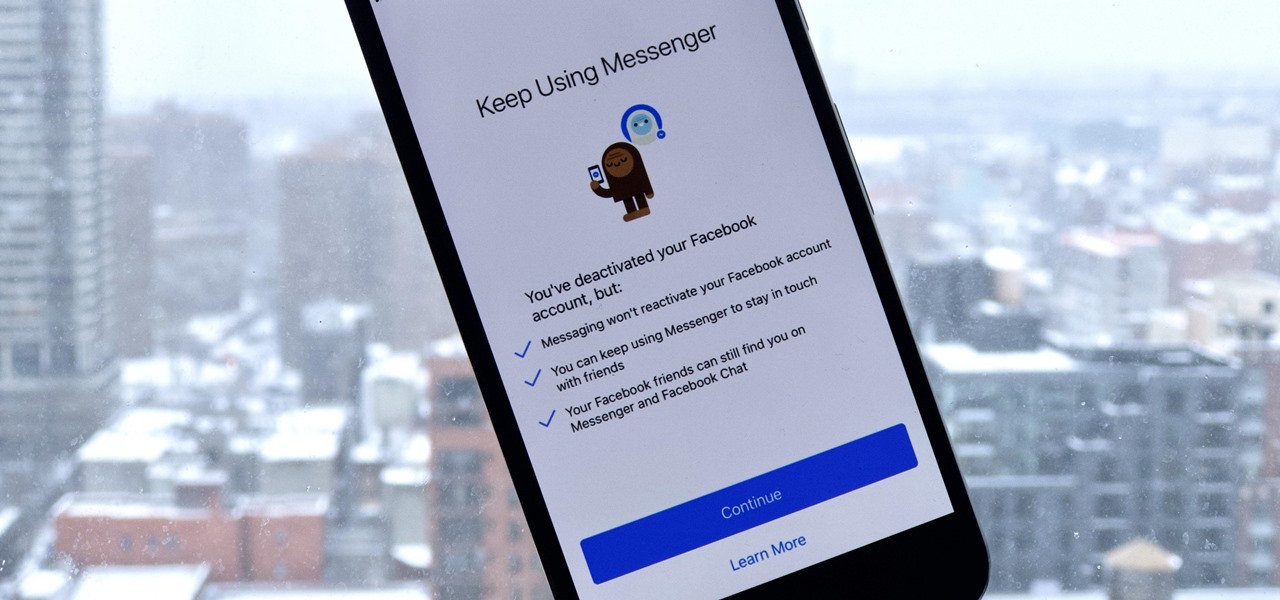
If you finally decide to take the plunge and delete your Facebook, you should know that your Messenger account may also go missing if that's how you log into it using your Facebook account. You can make a new Messenger profile without tying it to a Facebook account, but if you want to keep all of your old chats, you're going to want to deactivate rather than delete.

After pouring out $10 million for 60 seconds of Super Bowl advertising time, Doritos and Mountain Dew continued their Sunday marketing binge on Snapchat.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Now that it has buried the legal hatchet with Meta Company, augmented reality startup Dreamworld has announced plans to open up pre-orders for its Dream Glass AR headset.

Samsung just began rolling out the Oreo Beta 2 to registered users of the Galaxy S8 and S8+. The update's changelog promises the inclusion of the October 2017 security patch. Unfortunately, after downloading the update, we've noticed this is not the case. Omission of the more recent security patch is notable in that it leaves devices vulnerable to several known exploits, such as KRACK.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

It's the end of an era. Facebook's WhatsApp just announced that older Android devices equipped with the Gingerbread operating system will no longer be able to use the messaging app as of February 1, 2020.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

With many of the companies working in augmented and mixed reality focused on the Augmented World Expo, the finance side of the industry has been relatively quiet.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

Apple's iPhone is one of the most popular, most expensive smartphones in the world, yet with a broken Home or Sleep/Wake button, it might as well be a doorstop. There are many different DIY ways to fixing a busted Home button, but the Sleep/Wake button (aka Power button) is a little more averse to DIY trickery.

A few years ago I went hog-wild trying to achieve a zero-waste lifestyle. I didn't succeed, but the experiment taught me that we throw away things we could—and should—be using more.

It's hard to believe it's already been a year since I was frantically searching every Best Buy in the Los Angeles metropolitan area to find one with a Chromecast in stock.

Google I/O 2014 is currently going on in San Francisco, but as the conference rolls on, the Android Gear smartwatches continue to be one of the hotter topics.

I love Android, and I think its apps are great—the polish that came with the Ice Cream Sandwich update truly put Android design on the map. That being said, one of the more frequent complaints from iOS fans continues to be that apps just "run smoother" and "look better" on iOS than they do Android.

Mermaid Braid Hair Style Tutorial For Beginners!!!!

If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely.