Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.

You want to become anonymous, and dont want your IP to be logged on websites? Well read along here. Continuing This Series:

One of the best things about cold weather is soup, and there's nothing more comforting than a great chicken noodle soup. But I've often grabbed a can from the grocery store and found the chicken dried out and over-processed... and the noodles soggy and tasteless. What's worse: there's never enough of the stuff you like (such as the vegetables) and too much of what you don't (the nasty stuff I mentioned above).

Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester.

Sushi rolls, known as makizushi in Japanese, are only limited by your imagination—and your ability to roll them neatly, of course. While it may seem like a lot of effort, rolling sushi is a snap if you have the right tools.

Hi everyone! In the previous part of this series we introduced remote code arbitrary execution via buffer overflows using all of our past experiences.

Cooking with animal blood is as old as civilization itself. I promise that your ancient ancestors, no matter where you're from, didn't have the luxury of throwing away any part of the animal, including the very lifeblood that used to run through it. Animal blood, along with everything but the skin, would invariably end up in the stew.

Welcome back, my novice hackers! This is the third installment of my Python scripting series. If you haven't read the previous two articles, take some time now to go back and read Part 1 and Part 2 before you proceed here.

Lasagna, that layered, creamy baked pasta dish, is a lovely comfort food that's great for a crowd. But if you've ever made it, then you know you're usually left with some leftover lasagna noodles. (Although that's always better than the frustration of running out of the noodles while you're still making a traditional lasagna.) Still, what do you do when you're still left with a bowlful of the wide ribbons?

Though many students spend four years of high school learning a foreign language, most of us probably retained very little. Chalk it up to the carelessness of youth, but chances are you've since been in situations or places that left you wishing you paid more attention in class or had continued practicing long after you graduated.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

The world of root is upon us, folks. While the LG G3 has be available for purchase for a couple of months now, rooting had been a shaky subject. International and T-Mobile variants enjoyed root from day one, while various security patches left the AT&T and Verizon Wireless variants as a mixed bag, and Sprint completely out in the cold.

One of the best things about summertime is that there's lots of outdoor cooking, whether you're on a camping trip or grilling. And what better way to end your meal than with the classic dessert, s'mores?

When it's most important for me to browse the web incognito, I always seem to forget to enable private browsing. If that sounds like you, it's time you stop making that mistake for good. Manually deleting the cache and browser history is a thing of the past, and as it turns out, so is manually switching to incognito mode.

When the Nexus 5 debuted, one of its coolest features was the fact that you could say "OK Google" any time you were on the home screen to launch a Google Voice Search. This feature was ultimately made available for other devices by way of the Google Now Launcher.

Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.

With apps and games getting bigger and more memory-hungry every year, storage space is at a premium. High-definition videos and photos of innumerable pixels certainly don't help the matter, either.

You did it! You got your hands on the much coveted all new HTC One (M8). Last year's M7 model, also named the One, was very well received critically, and HTC continues its smashing design here with stereo speakers that kick and curves that don't quit.

Welcome back, my rookie hackers! A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.

WhatsApp is one of the most well-known and most utilized cross-platform chat applications available today. It's free for one year, and only $0.99 a year after, which is chump change when you realize there are no hidden costs like international charges. Basically, it creates an easy to use forum for you and your friends to chat, regardless if they're an Android or iPhone user.

If you've seen our guide on the 18 coolest features in iOS 7, you know that there's a lot to like about Apple's new mobile OS, but there's also a laundry list of grievances to go with it. One that bugs me is the lack of Home screen customization, something that has always driven me to jailbreak in the past.

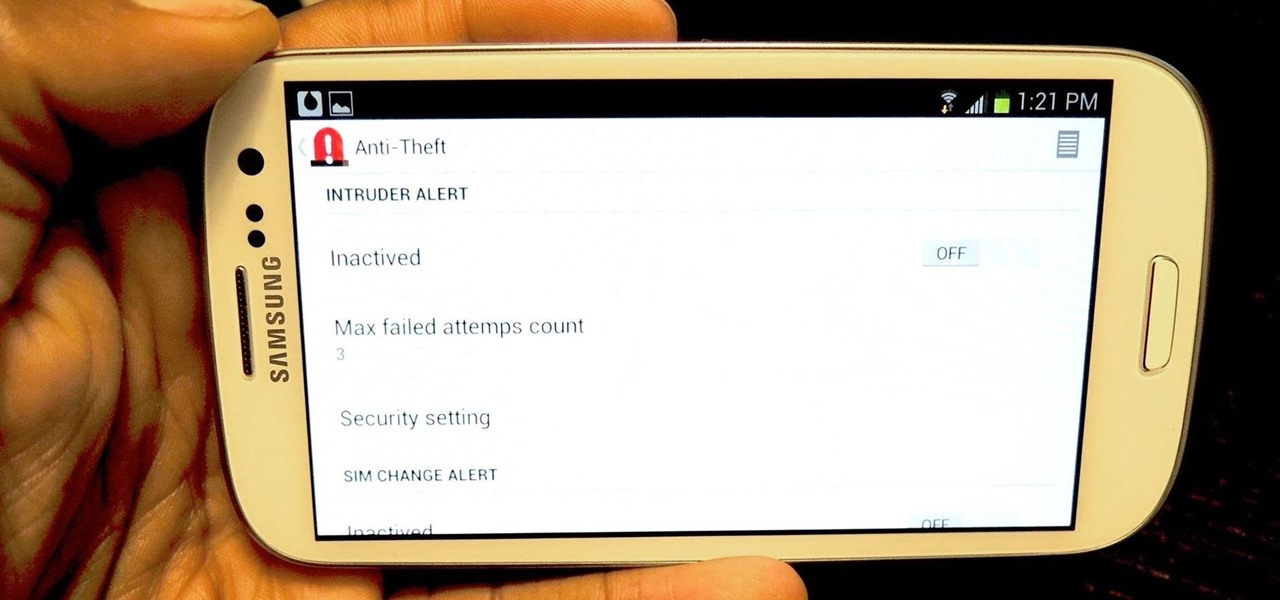
I love surprises. Surprise parties, surprise visits, surprise Patrick... But there are times when a surprise is the last thing you want, like reaching into your pocket to find that your Samsung Galaxy S3 is not where it should be.

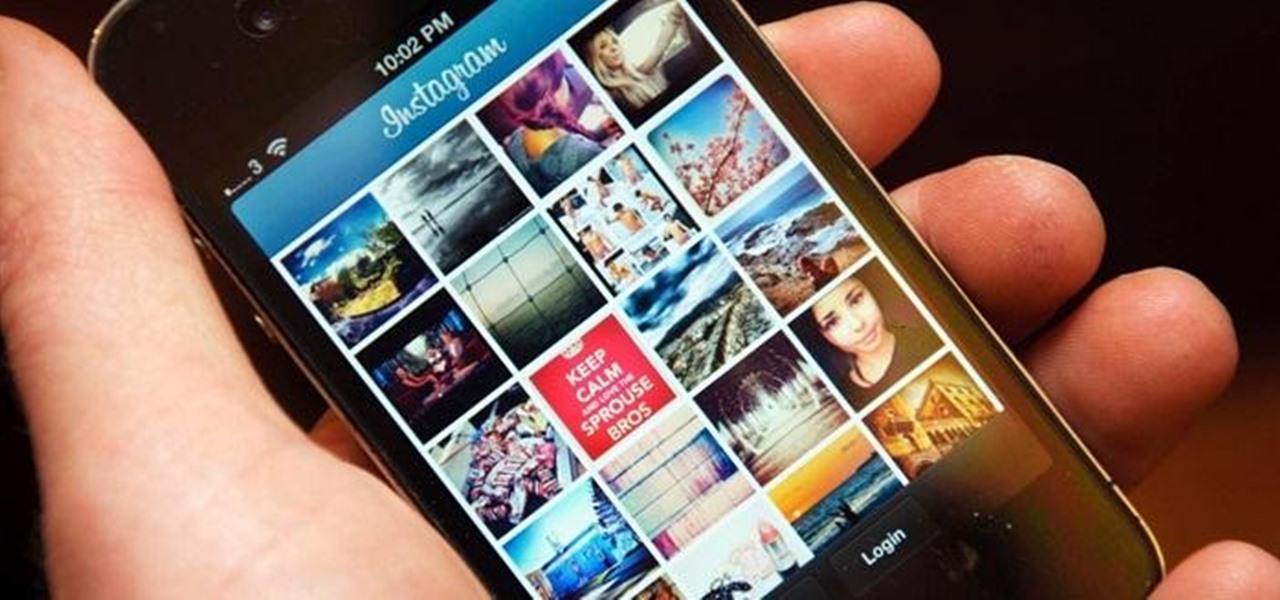
It might be time to move those Instagram photos to another service. It seems that Instagram has never heard of the phrase, "If it ain't broke, don't fix it." In a very big WTF moment, the extremely popular photo sharing and editing app decided that it has the right to sell its users photos to third parties without pay or notice. Yep, you heard that right. That photo you took of your girlfriend laying out on the beach could be in the next stupid Corona commercial without your consent and witho...

If you have children, then you know firsthand how many crayons parents end up buying. There is no such thing as using a crayon until it disappears. Kids use crayons until they are a nub, and then they toss the crayon aside, never to use it again.

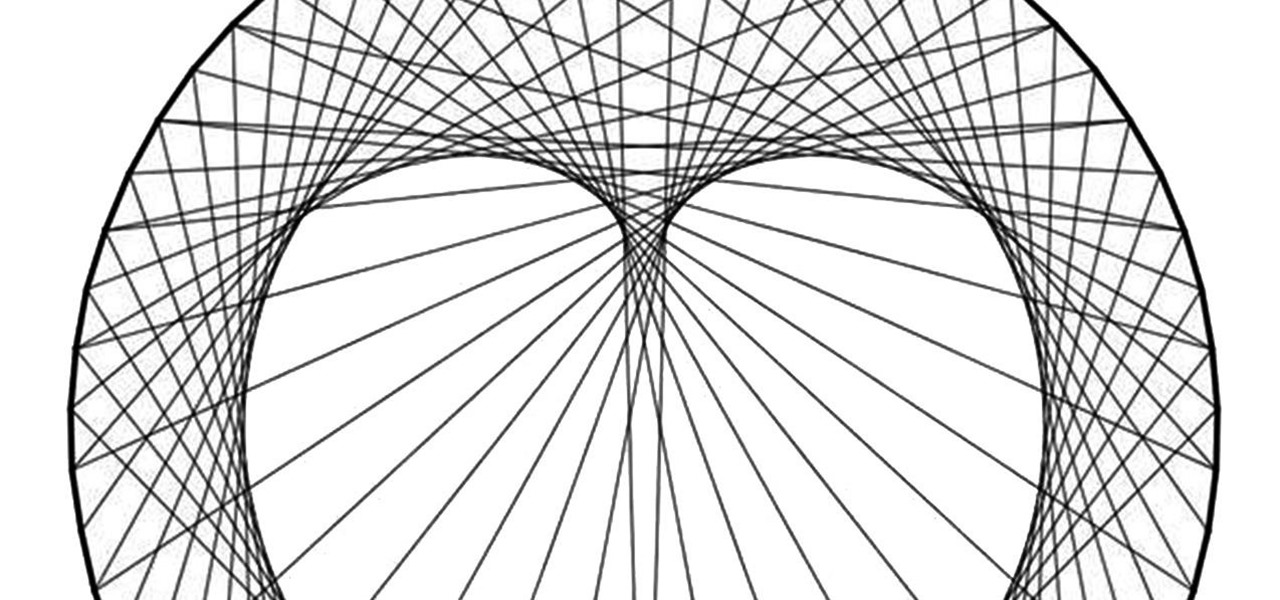
Using only a circle and straight lines, it's possible to create various aesthetic curves that combine both art and mathematics. The geometry behind the concentric circle, ellipse, and cardioid dates back centuries and is easily found in the world around us. From an archery target to an apple, can you name these geometric shapes?

Beer can turkey? Sounds like a joke, right? Well, it may have started off as one, but now shoving a beer can up the butt of a turkey is a much favored cooking technique in lieu of the traditional Thanksgiving turkey. With the beer can up its butt, it helps steam the turkey to keep it moist and tender, all while giving it that perfect aroma and taste.

Deaf people are just like everyone else, and they have a responsibility to save lives just like the rest of us. Those with hearing impairments might not be able to benefit from most online first aid training, but this video is signed to give those with hearing problems the info they need to help out.

Gwen Schoen and Paul Carras share with you in this video how simple it is to save money by carving a whole raw chicken. You can save your pockets an average of 20 – 30%! First take out any insides; this is usually the neck, heart and liver when included. Lay the chicken on its back and start with the wings. Break the skin with a boning knife and pull the wing away from the body until the socket pulls out. Finish the incision where the socket meets and repeat on the other side. Then you’ll...

In this how to video, you will learn how to make a croissant. You will need 130 grams of sugar, 100 grams of butter, 250 grams of butter, 200 grams of flour, 500 grams of milk, 20 grams of salt, 3 eggs, 1 kilogram of plain flour, 50 grams of yeast, and 1 vanilla pod. First, melt 100 grams of butter for about 15 seconds in the microwave. Add the melted butter into the mixer. Add the 3 eggs, sugar, vanilla, and salt. Mix everything together. Next, add the yeast and then continue to mix. Add mil...

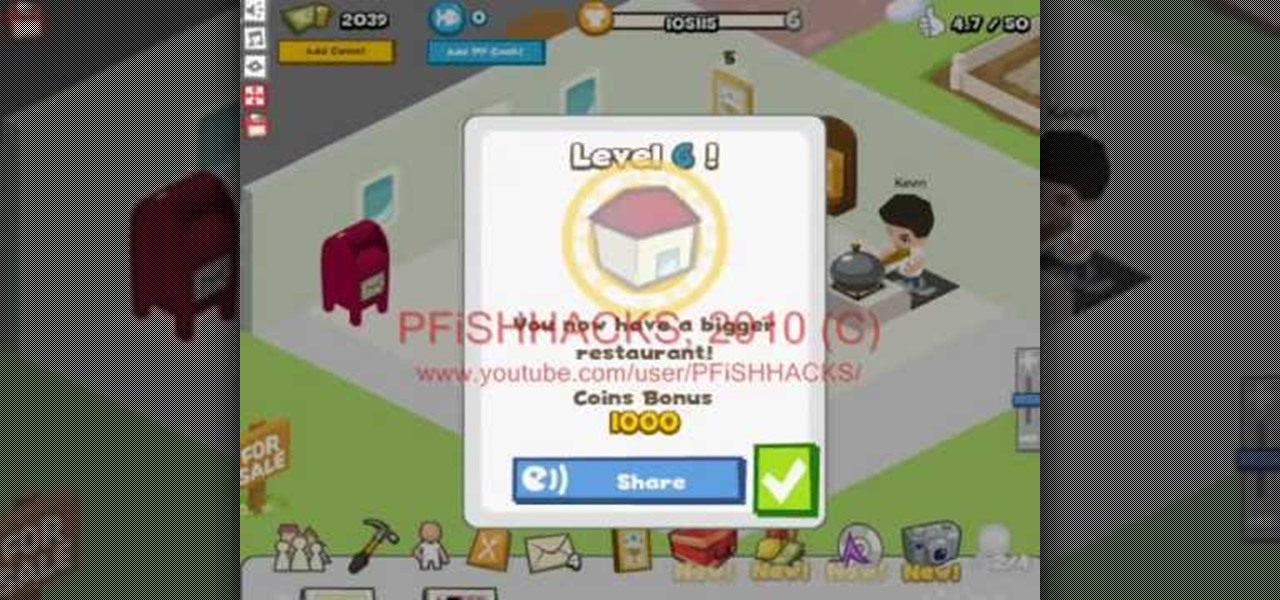
Want to be the John (or Jane) D. Rockefeller of Restaurant City? Watch this video tutorial to learn how to hack Restaurant City with Cheat Engine 5.5 (02/04/10).

How to make warm, fresh homemade bread

For a fun novelty project, try making a zoetrope at home. * A plastic coffee can lid

Imagine a game almost anyone can play that combines the best of skee-ball, bowling, and shuffleboard. Welcome to the ancient sport of bocce.

Watch this video tutorial from the Polish Guy to see how to polish aluminum alloy car rims with Simichrome and a buff ball. In this demonstration we use Simichrome Polish and a Flitz Buff Ball to clean and polish a Subaru wheel rim. The tutorial includes detailed work instructions and best practices.

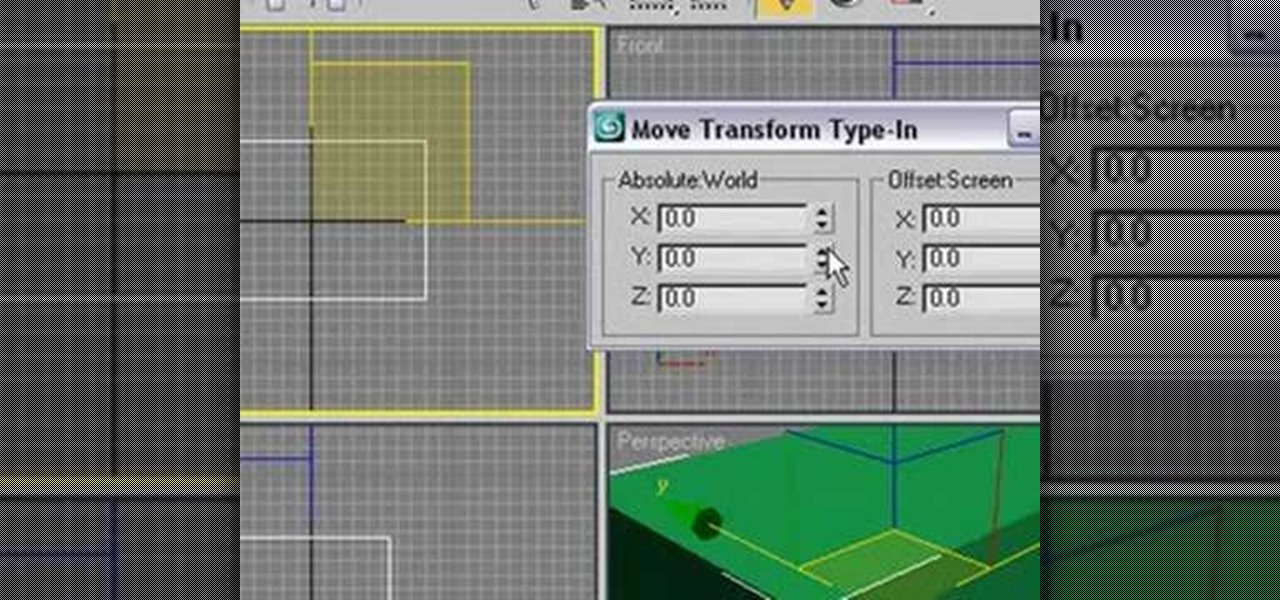
This software tutorial series teaches you how to box model in 3DS Max. Specifically, you will learn the basics of box modeling in 3D Studio Max, then box model a jet and animate it for PaperVision3D.

Ever wonder how to do the long tail cast on for knitting? Well, wonder no more with this knitting demonstration video! Begin by measuring out a length of yarn for the tail. (Search video "Estimate the length of tail when knitting" on WonderHowTo)

Have an old bike combination lock that you can't remember the code for? If it's a simply four-digit cable lock, you can easily figure out the combination with a quick peck-and-go method. Best of all, this technique doesn't require any tools or special know-how, and let's you reuse the cable lock again versus just damaging it with bolt cutters. All you need is a bit of patience and you'll have your figure out your combo in no time.

In this tutorial, Jenny Jones invites you into her bedroom to show you how to give yourself an easy, 6 step at-home facial. Keep your skin young and bright with these fantastic tips from America's favorite talk show host.