Welcome back everyone. This article isn't going to contain anything related to scripting, but rather some updates about the series. We'll be quickly discussing what we've covered so far and what is to come.

This is a nice project that you can continue to work on and modify as you learn more Arduino projects. The Instructable linked below goes through the complete build for the Bluetooth-enabled robot seen in the first half of the video.

For well over a year, Spotify's most requested feature was to add Chromecast support. While they left the request unanswered, it seemed that Spotify just didn't want anything to do with the $35 streaming stick.
Hey everyone. Only found the site a few days ago but really loving it. Been
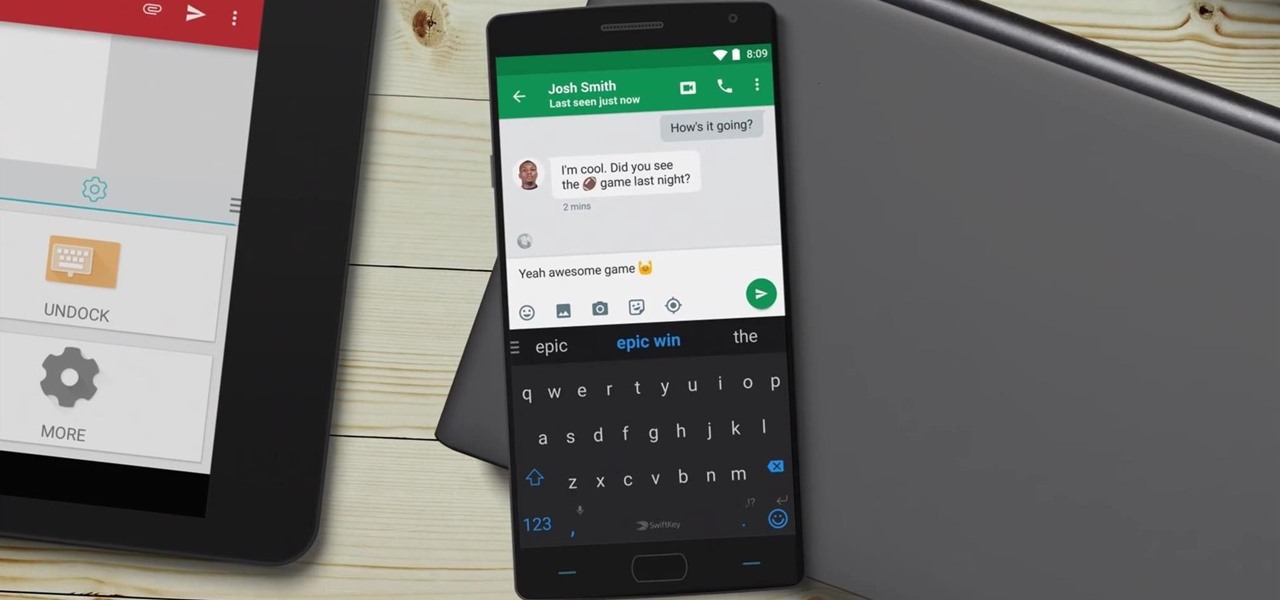
Microsoft announced Wednesday morning that it has entered into an agreement to acquire SwiftKey, makers of the SwiftKey predictive keyboard and its SDK that runs on over 300 million Android and iOS smartphones, for about $250 million.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private detectives, and many other organizations.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

Well, here we are. We've come a long way, we really have. Watching this community grow has been amazing. Well, before I start babbling on about the community, let me get to the point...

Not that long ago, Google introduced a beta program for their Google Search app on Android. Much like any beta program, testers will get access to new features before they officially debut, but you might have to put up with the occasional bug as new functionality is introduced. If you'd like to sign up, it's quite simple, but I'll go over the process in detail below.

Hello, everyone! Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice to have something related on our WonderHowTo world. So here it is!

If you don't have the time or patience to build a complete Ant-Man suit from scratch, there's another way to make a Ant-Man costume for Halloween. If you're more skilled with brushes and makeup rather than drills and cardboard, this is the Halloween DIY for you—especially if you're a fan of the Marvel universe.

A fire snake, also referred to as a black snake or sugar snake, is a classic science experiment you can do right in your own kitchen using a baking soda and sugar mixture and a fuel to ignite the reaction.

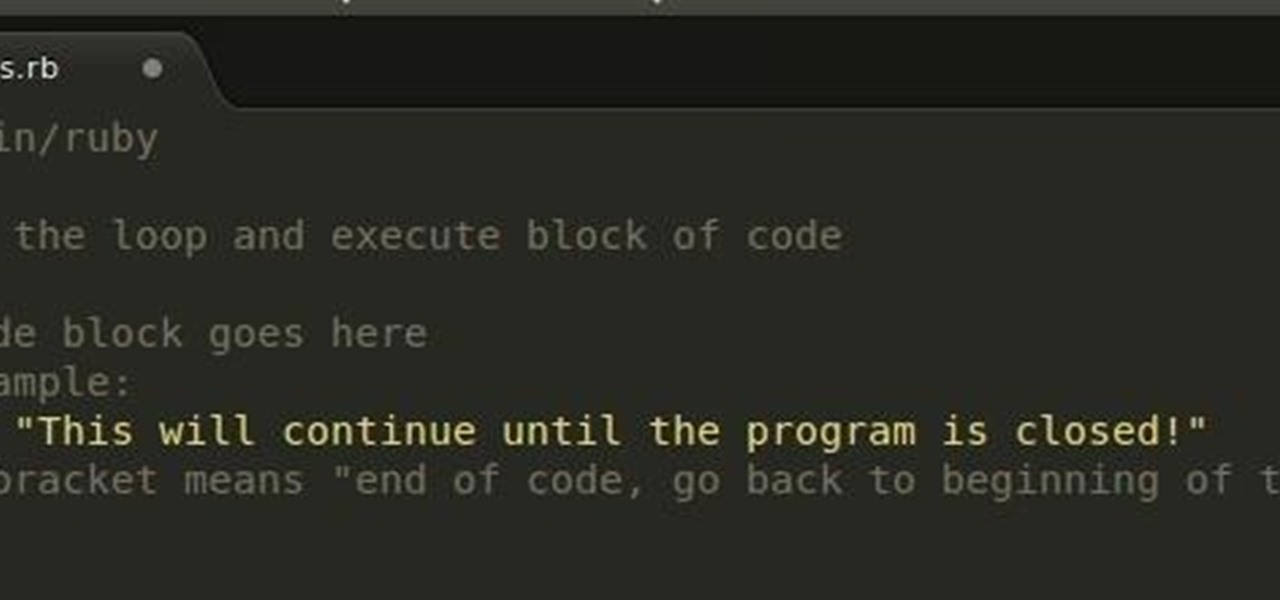
In the last Ruby article, we talked about how to store information in three different kinds of storages: variable, array, and a hash. After we get the data, we have many ways of using them, but, for right now,

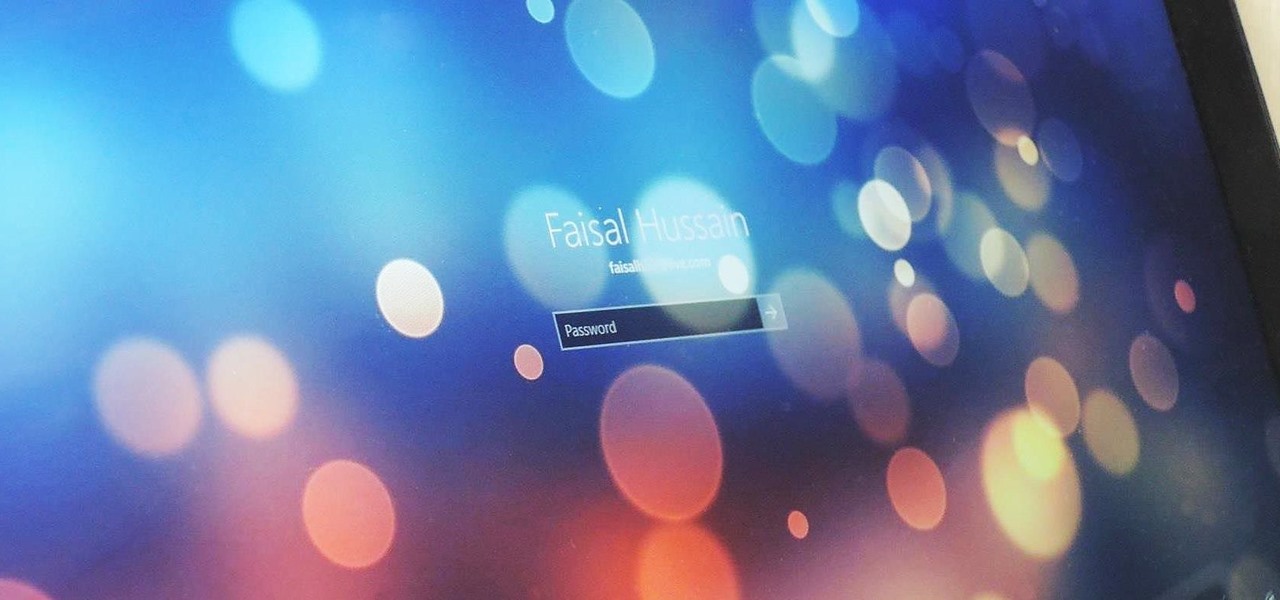
Windows 10 makes it a cinch to change the lock screen background: simply go to Setting -> Personalization -> Lock screen, then change the background to whatever you'd like. But, trying to change the login screen background—the screen where you enter your password—was a long, complicated, and possibly dangerous process. Luckily, developer Krutonium has published a tool that automates the entire process, and it's very easy to use.

It's no secret that Google stores your search history in order to provide you with targeted ads when surfing the web. What's even more interesting (or freaky) is that your Google Now voice searches are also being stored, and you can actually listen to them right now.

Now that Apple's latest Worldwide Developer's Conference (WWDC) is over, you can sign up for the public beta version of iOS 9 for your iPad or iPhone. For the first time in their history, Apple made a beta version of their mobile OS available to the general public just a few months ago, in the form of iOS 8.3, and they'll continue that trend for the newest build.

Living in Southern California means I don't really have a need to check the weather all that often. But every now and then, I'm caught off guard by a particularly chilly or hot day—no one wants to be the only person walking around with a T-shirt and sandals on a rainy, 50-degree day.

When you think about it, YouTube may actually have one of the largest music collections on the planet. This is why, at $10 per month, Google's new YouTube Music Key subscription is a solid value for many users, especially with its inclusion of Google Play Music.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

Aside from the fact that it was the only game available on my cell phone at the time, I was really good at Snake. I still occasionally play it on my smartphone, but I've never been able to duplicate the same level of achievement as I once did.

Most smartphone games are clichéd and mundane, but every now and then a mobile game will appear with a new concept or idea that sets it apart from all the rest. While other developers continue to regurgitate the same old "winning" formulas, developer Sebastian Goszyla is changing how we play.

Not too long ago I showcased ReCam, a free app that lets you schedule recordings and use your Android device as a security or spy camera of sorts. While useful, this app required you to schedule when to record in advance, resulting in you possibly missing the footage you intended to record (assuming your scheduling wasn't as on-point as you wished).

Problems with eyesight affect people of all ages and walks of life. And while it is possible to increase font sizes on Android, even the "Huge" setting is neither big nor clear enough for a lot of folks.

For $35, there's hardly a better value in the online media player market than the Chromecast. Taking that sentiment a step further, if you factor in the promotions Google likes to offer with it, Chromecast practically pays for itself.

With over 500 million downloads on Android alone, I find it safe to assume that most of us use the Chrome Browser on our mobile devices; it's great for reading articles with Reader mode enabled, syncs open tabs and bookmarks across all your devices (as long as you're signed in to your Google account), and is regularly updated with new features and optimizations.

How to do the sliced banana magic trick! Fool your friends and be the life of the party with this awesome magic trick! This video will show you how to cut a banana before you even peel it! All that you will need for this cool trick is a needle and a banana.

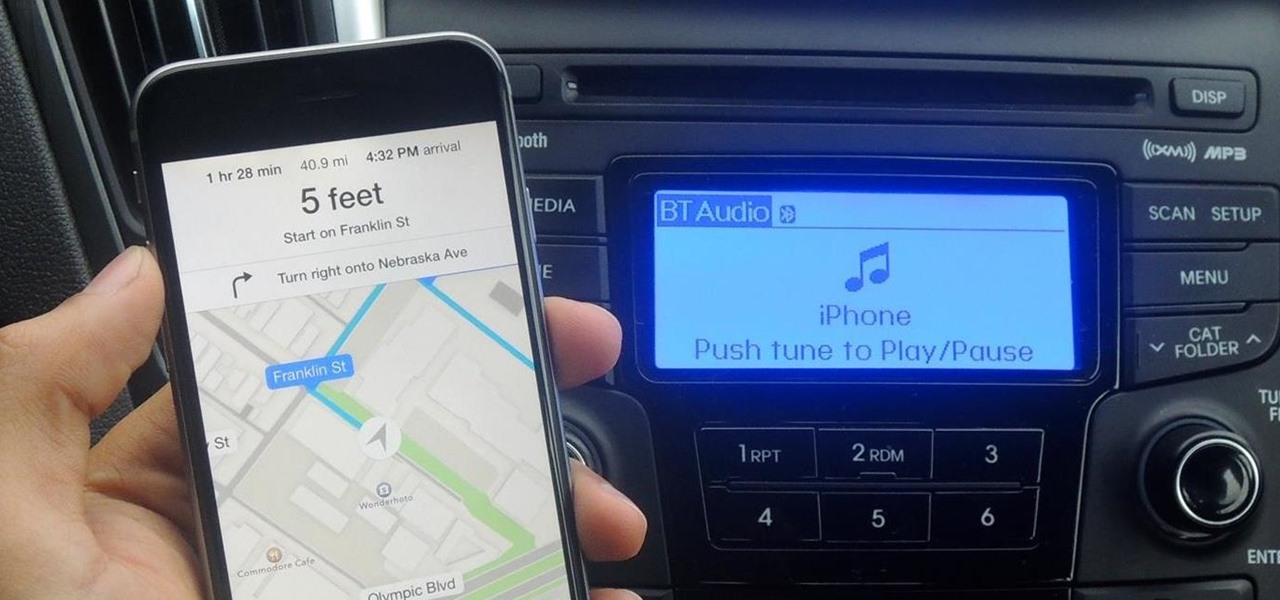
Maps is great for getting turn-by-turn directions in unfamiliar territory, but how many times does your favorite song have to be rudely interrupted by that navigation voice telling you to turn left or right? Yes, you need those spoken directions to get to where you're going, but you also need to hear every part of your song, right?

Technology allows us to communicate with others like never before, providing us with the ability to stay connected with past and current coworkers, classmates from high school, and even relatives in far-away countries.

I'm all about customizing my iPhone and making it as different as possible from everyone else's. While it's easy to change the wallpaper, swap keyboards, and hide apps on your home screen, there's not much else you can do aesthetically without jailbreaking, especially when it comes to the status bar and app icons.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

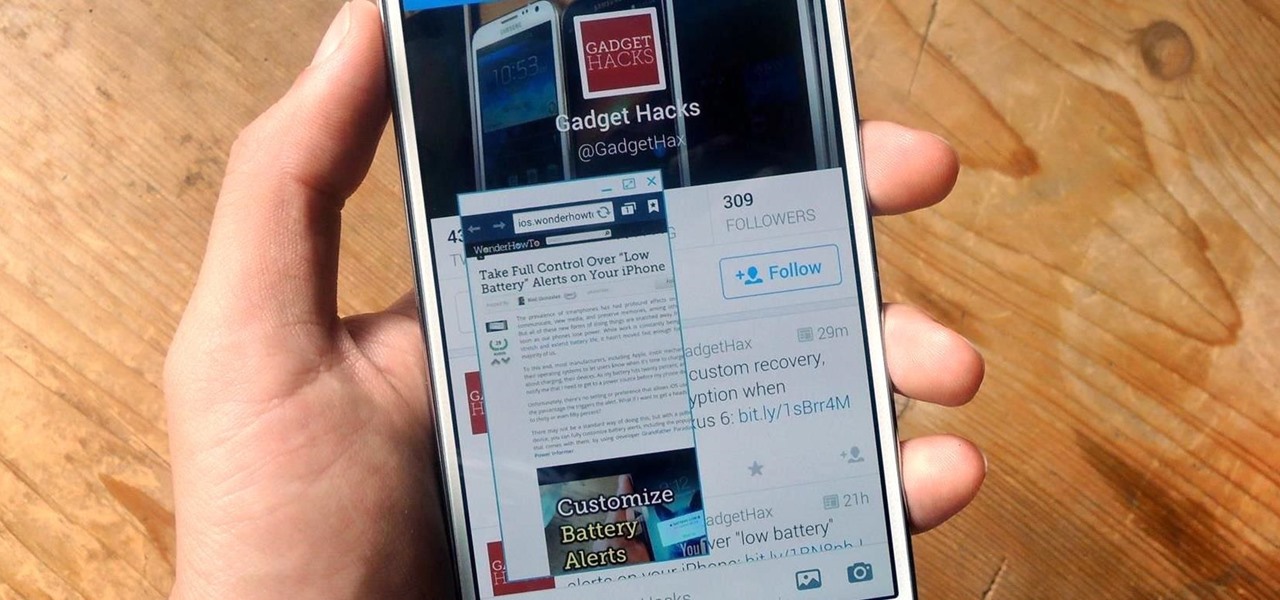
Android has plenty of features that provide multitasking support, which are especially useful on smartphones with larger screens. One such feature that I loved on the Samsung Galaxy Note 2 was the popup browser, which brought up a floating window whenever I opened a link inside of third-party apps like Facebook and Twitter.

Don't hit that button yet! I know that everyone is eager to update to iOS 8 as soon as humanly possible, but when it comes to enabling iCloud Drive, you need to wait.

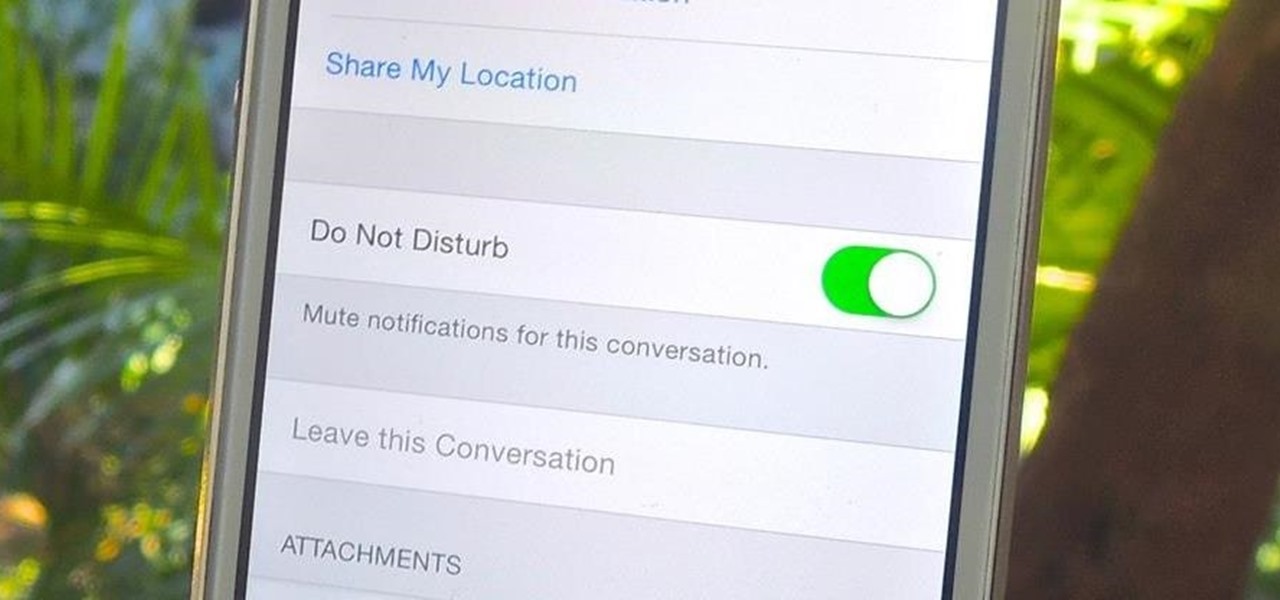
As hilarious and fun as group messages can be on your iPad or iPhone, they can also be equally annoying. You may not necessarily want to leave a group message thread, but you don't want to be bothered by notification after notification as participants in the conversation continue to send out rapid-fire texts. Thankfully, one of iOS 8's new features now makes it extremely easy to mute notifications from specified conversation threads, single or group.

Despite being one of the largest and most feature driven companies on the planet, Google can sometimes come up short. I have my Chromecast running 24/7, and while I use my phone to cast most of my content, I sometimes find a video while browsing Reddit or LiveLeak on my laptop and I'd rather just cast it from there.

These days, phones are more like portable entertainment systems. It's a hybrid mobile device for gaming, texting, watching movies, and listening to music more than it is an actual "phone" that you talk on.

The camera on the Amazon Fire Phone is simple and easy-to-use, with a 13-megapixel rear shooter with optical image stabilization, but there are a couple of features that makes this camera stand out from others.

Certain foods like garlic, onions, and shallots are food staples for a reason—they're unbelievably flavorful and cost very little. However, with their papery thin skins, they're also a pain to peel.

Google I/O 2014 is currently going on in San Francisco, but as the conference rolls on, the Android Gear smartwatches continue to be one of the hotter topics.