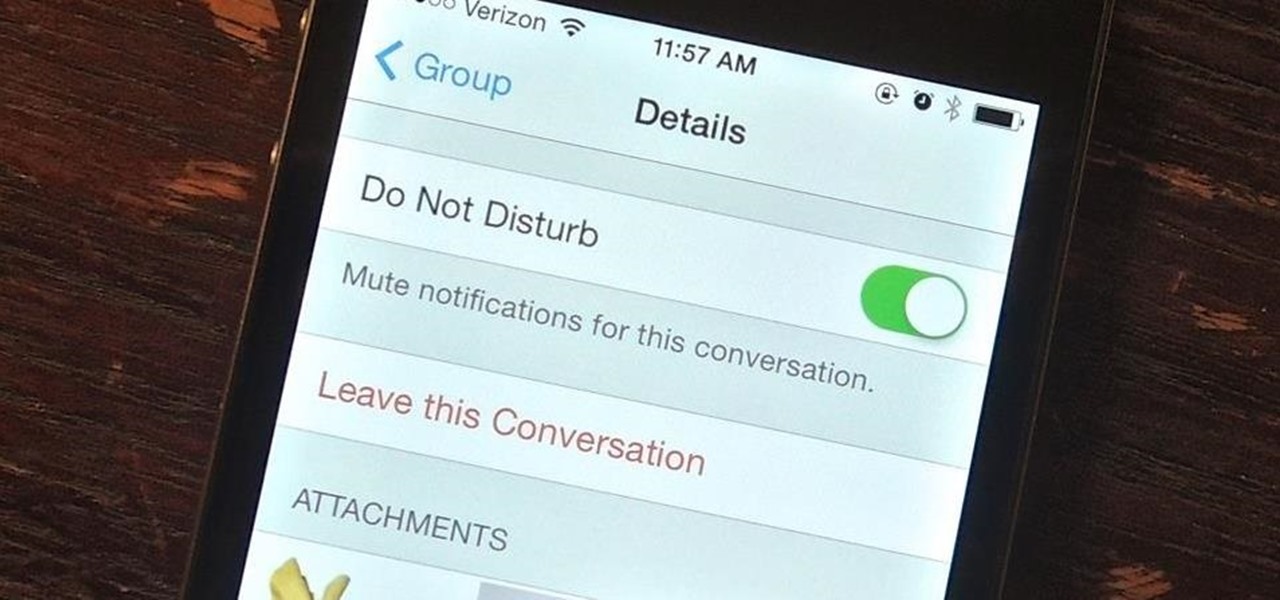
Group messages make for some hilarious conversations with your friends, and are also a great way to update multiple people without sending individual text messages. But as awesome as they can be, they can also be as equally annoying.

The new operating system for your Mac is here, and it looks fantastic—OS X Yosemite. At Apple's WWDC presentation, we were shown the new iOS-like aesthetics, as well as other awesome enhancements to the operating system. Improved Aesthetics

I love Android, and I think its apps are great—the polish that came with the Ice Cream Sandwich update truly put Android design on the map. That being said, one of the more frequent complaints from iOS fans continues to be that apps just "run smoother" and "look better" on iOS than they do Android.

With the Samsung Galaxy S5 all but assured to be showcased in a just a few weeks, we've got our hands on some fresh details of the upcoming flagship device.

Snapchat is like that very attractive girl at the bar that has one too many shots and ends up slobbering on the bouncer as she gets led out. Of course she can still recover since she is hot, but you only get so many chances before you just become a complete failure. And that's where Snapchat has been treading these past few weeks.

Impeccable is the word for this distinctive and exclusive Ladder Hair Style. Extremely elegant and graceful, girls with long hair will be going to love this. Follow these simple steps and just with a little effort arrive at special and distinguished look. Step 1: Comb Your Hair to Make Them Smooth and Tangle Free. Gather All Your Hair and Tie Them in a Pony. Step 2: Take a Small Chunk of Hair from One Side of Pony and Braid It Leaving a Small Strand of Hair Before Each Weave at Inner Side Onl...

As an avid music fan, Spotify and Pandora only partially satisfy my needs on a day-to-day basis. When there's a certain obscure or underground band that I want to listen to, I'm relegated to using YouTube as my main music player source.

Gmail is a free, advertising-supported email service provided by Google. Users may access Gmail as secure webmail, as well as via POP3 or IMAP4 protocols. Gmail initially started as an invitation-only beta release on April 1, 2004 and it became available to the general public on February 7, 2007, though still in beta status at that time. The service was upgraded from beta status on July 7, 2009, along with the rest of the Google Apps suite.

If you didn't already know, Apple is giving away their newest operating system, Mavericks, for most of your computers. While the folks over at Microsoft surely despise this tactic, those of use Mac users still running Snow Leopard surely do appreciate it.

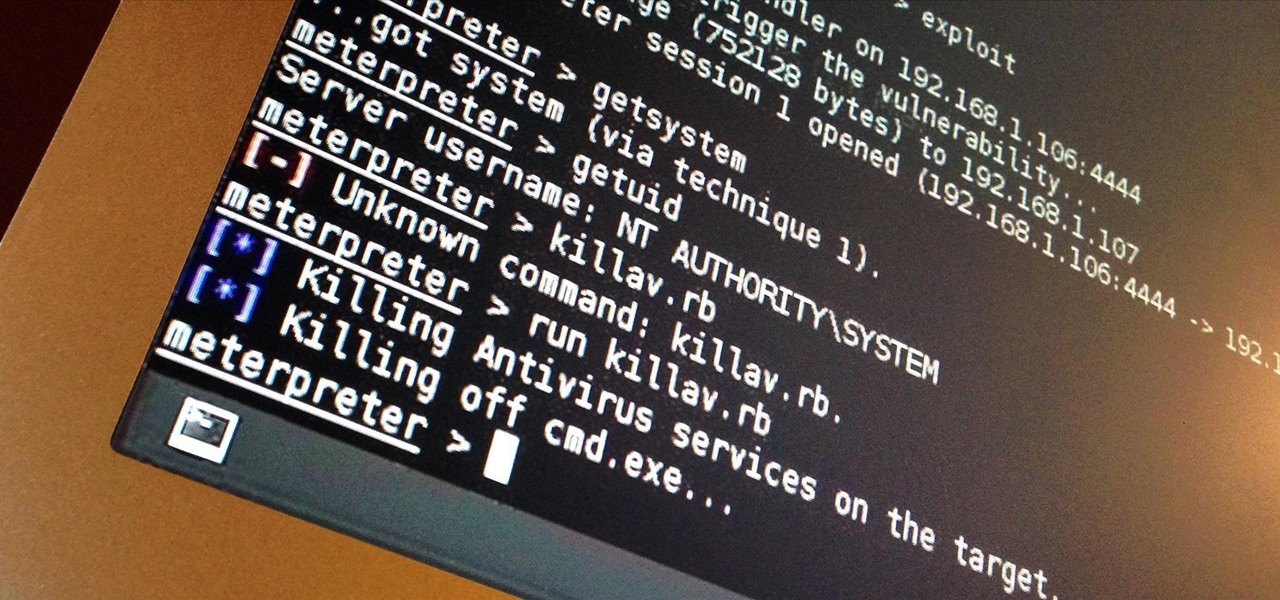
I've done numerous tutorials in Null Byte demonstrating the power of Metasploit's meterpreter. With the meterpreter on the target system, you have nearly total command of the victim.

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

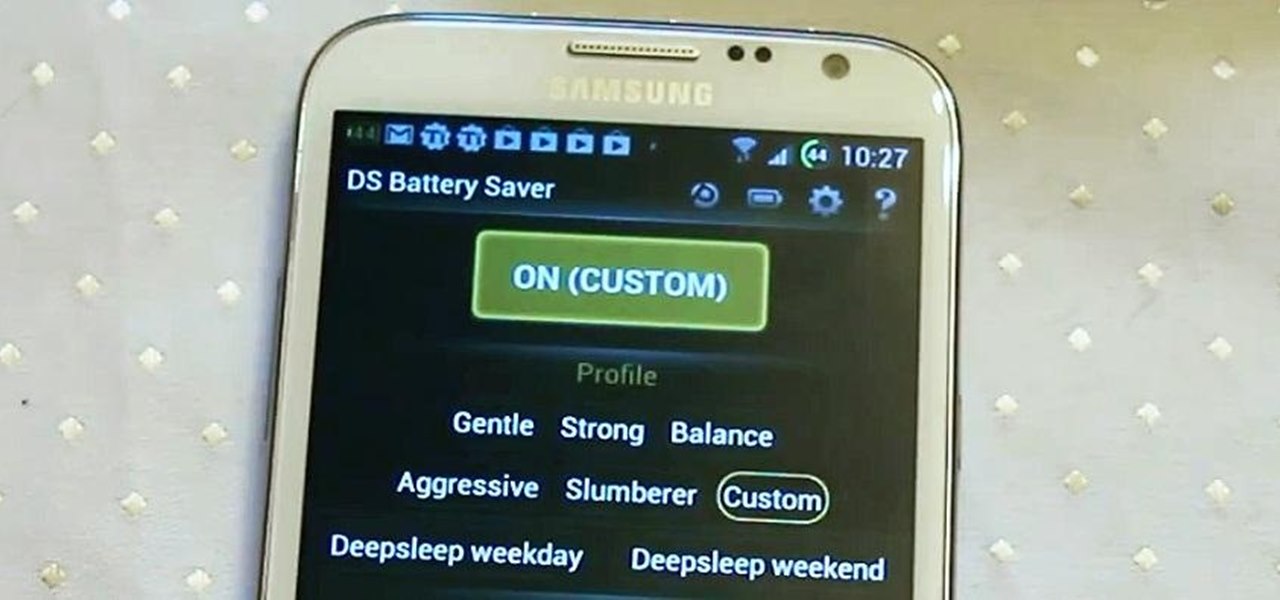
Newer smartphones are more power hungry than ever before, and the Samsung Galaxy Note 2 has a mighty appetite for amps that only Jenny Craig could possibly curb. On average, your Note 2 (or other Android device) lasts for what, a day, maybe two days before dying. Mine barely lasts 8 hours! This is thanks to all of the apps running in the background of your phone, even when you're not using them, eating through all of your CPU, leaving nothing but crumbs.

Although it's been several years since Angry Birds first came out, it's still going strong in the App Store, currently third place on the Top Free Apps chart. The new Angry Birds Star Wars is sixth place on the Top Paid Apps chart. What does this show us? Those pesky birds can't be shooed away.

Checking notifications from all of your social media accounts is half the fun of the Internet, but can become quite tedious—hopping from site to site can take up hours of your time, especially when you're running away from something (in my case, it was always homework/studying).

This is a simple pattern, designed to produce a well-fitting mitten. Both the right and left mittens worked the same up to the shaping for the top of the mitten. A slight adjustment for making one right and one left, then they are worked the same. The gusset for the thumb constructed with the increases made in the center of the gusset, rather than on each side. This makes it easy with a minimal amount of counting stitches as you go. I have been crocheting for 56 years. In doing research for w...

I love YouTube for listening to music I don't already have on my phone or in my iTunes library, but there is one very simple thing that you think they would've figured out by now—the ability to have your video continue to play outside of the app!

One of the coolest things for readers using the Samsung Galaxy Note 2 is the stock Smart Rotation feature. While most smartphones use the accelerometer to adjust the screen orientation, Smart Rotation actually uses the camera to detect your face-to-screen angle and adjusts accordingly. Now, if only there was a way that all Android users can continue reading an article or text without sporadic and unexpected 90-degree turns of their screen. Wait, there is!

How much time do you spend outside, as opposed to inside? Whether it's because you're working, studying or just have a bunch of errands to run, it may seem like the majority of your day is spent indoors. Ever wondered exactly how much time you spend indoors and outdoors? Now you can, thanks to this DIY Arduino-powered tracking device by Instructables user Gramsky.

The first album I ever bought with my own money was Nirvana's MTV Unplugged in New York. It featured mainly lesser-known songs and covers, but was on constant repeat on my Walkman. While the whole album was fantastic, there was one song that stood out the most to me—"The Man Who Sold The World." The song (originally written by David Bowie) kept me under a spell, which had me replaying the song over and over and over and over. As I got older, I found myself sharing this relationship with a han...

Early last month, Sony released PlayStation Mobile, bringing PlayStation games to the PS Vita and other certified phones and tablets. The list of certified phones isn't as extensive as it should have been, consisting of only Sony devices (a few tablets and Xperia) and a couple of HTC ones. For anyone with a supported device, you can head over to the PS Store for the download and installation instructions.

Apple's latest iPhone software update — iOS 17.5 — is finally ready for prime time. Released on May 13, it includes at least 32 new features and changes you need to know about, from a new game and offline news access to new wallpapers and anti-stalking capabilities.

Because our smartphones are ever present, frequently used apps become the topic of conversation in social situations. This often leads to sharing app links via messages, either by copying/pasting an app's URL or sending it through the sharing menu. However, there's another way to share an app, and it's most valuable when you need to share multiple apps and app updates without an internet connection.

As we move toward the end of the year, the wheels of the augmented reality space continue to shift in major ways.

This was a busy week in the tech space. After everyone got over the major announcements of Apple's latest, we examined the metaverse through the lens of Hollywood, and then took a closer look at Facebook's first smartglasses.

This week, Google showed off some wild new and innovative AR experiences that showcase the WebXR protocol for browser-based AR content, while 8th Wall applied its own web-based AR platform in service of Captain Morgan.

After weeks of reports about their first augmented reality device, Apple actually shipped a real AR product this week in the form of a TV tie-in AR app.

Just as the augmented reality industry grows, so too does the segment dedicated to creating experiences for the tools becoming available.

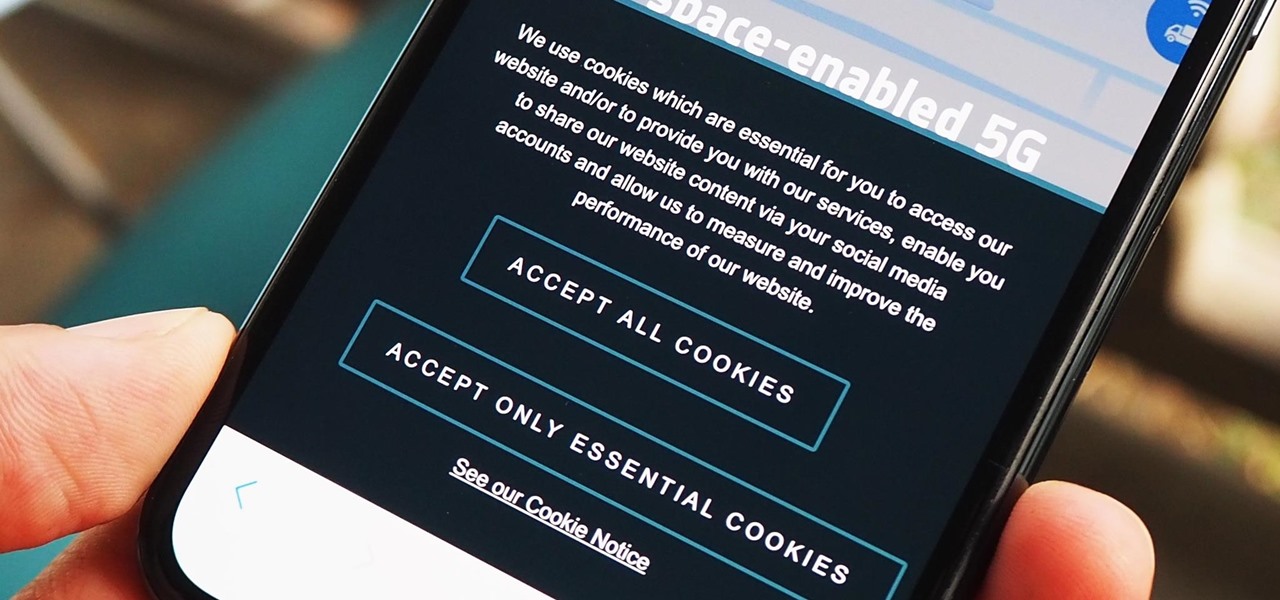
As a means to combat annoying and intrusive advertisements in Safari, Apple added native support for content blockers on the iPhone. Instead of being bombarded by notifications, banners, and pop-ups, content blockers prevent them from opening, which can also be said about those annoying cookie consent notices that many websites now have.

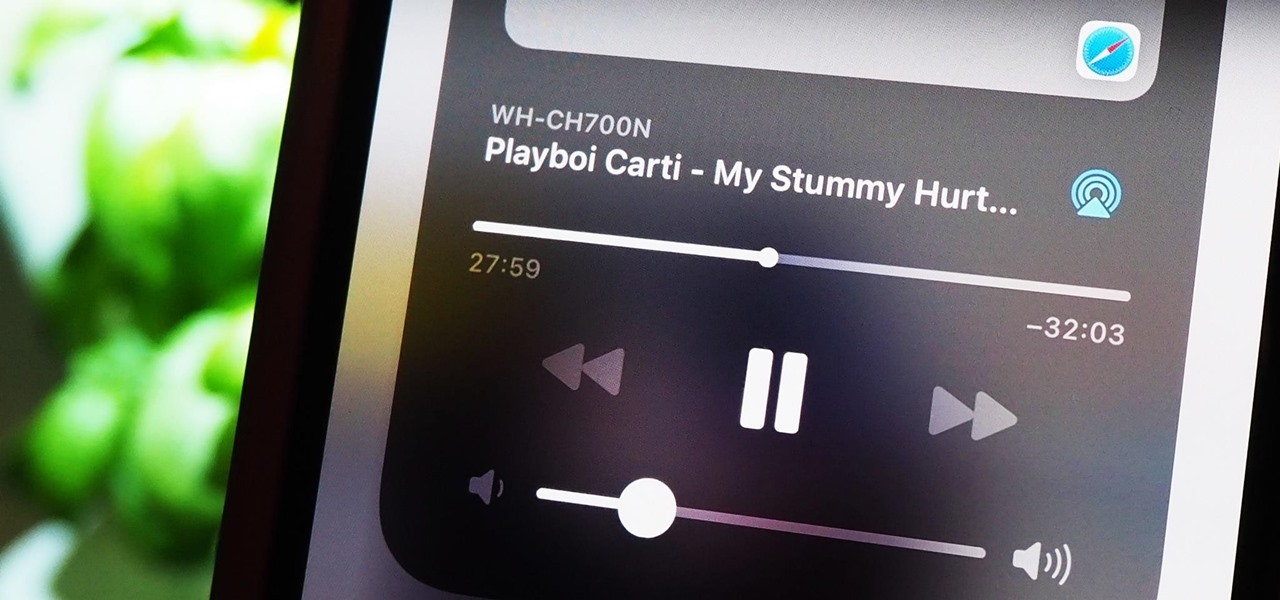
It's pretty clear with all of the annoying "Get YouTube Premium" pop-ups that litter the YouTube app that Google really wants you to pay for its Premium membership tier. That's why you'll see that "Get background play with YouTube Premium" ad after closing YouTube with a video playing — even in iOS 14 which supports Picture in Picture playback. But there are workarounds for background listening on iPhone.

For some, one of the coolest new features in iOS 14 is the Picture in Picture mode, which had previously only been available on the iPad. With it, you can continue watching a video from an app in an interactive floating overlay window on the home screen or within other apps. But for others, it can be annoying when it appears unexpectedly all of the time, and there's a way to stop it.

Late last year, Snapchat introduced Cameos, deep fake-ish stickers animated from your own selfies. Now, Cameos have evolved as a sticker option to use in photos and videos captured with the app's camera.

A modern iPhone is capable of running sophisticated, exquisitely-rendered games that rival titles on current-generation consoles. However, there is some value in classic video game titles, whether you grew up playing games on the Atari 2600, Nintendo Entertainment System, and Sega Genesis or not.

If you made a resolution for 2020 to get healthier, it's essential to concentrate on your mental health just as much as you do on physical fitness. Running and exercising is great, but a sound mind is integral to a healthy and balanced life, and you can improve your emotional and physiological well-being with your smartphone.

It's safe to say that we can call the annual ranking of AR investments a holiday tradition at Next Reality.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

If you're on the hunt for a profitable side-gig, or even a completely new way to to make money, you'll want to take a look at Upwork, a leading freelancing platform that connects skilled freelancers with clients from all over the world.

Believe it or not, there are a variety of ways to customize app icons in iOS. While iOS 12 made gave us an unofficial built-in way to do it, and iOS 13 improved it, and iOS 14 made it the best it could possibly be, there's still another option if you don't like using the Shortcuts app.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.