Have you ever wondered where you'd come out if you drilled to the other side of the world? Now, if you have an Android device and Chrome web browser, you can find out.

Ah, subscriptions. Whether you love or hate them, they are now a fundamental part of our increasingly digital lives. If you have some essential subs on your iPad, iPhone, or Mac, like Apple Arcade, Apple Music, Apple News+, Bumble, Pandora, Tinder, or YouTube Premium, there are three key issues you need to know about that could unexpectedly stop your membership from renewing.
Unity often reminds us that the majority of AR apps and experiences are built with the Unity 3D engine, and now the Unity MARS service, which facilitates easy AR creation for seasoned coders and newcomers.

Battery management is a never-ending struggle. To be on the safe side, you likely won't want to leave your home with less than 100% battery, but continually checking your charging iPhone is a hassle. Instead of continuously monitoring your battery's power level, have your iPhone tell you when it's reached a full charge.

Google Maps Live View is already one of the more useful examples of augmented reality on smartphones that is available to the average consumer today.

We are now in the age of 5G. Carriers worldwide are upgrading their networks to the newest standard for mobile, which will dramatically improve your phone experience. How? By giving it download speeds and latency that surpass Wi-Fi. But before you upgrade, there are few things you should know first.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

When Facebook launched its first hardware products last year, the Portal and Portal+ smart displays, the company mostly touted its video-calling features as it faced off against Amazon and its Echo Show.

They're finally here. Apple revealed the brand new iPhone 11, 11 Pro, and 11 Pro Max on Sept. 10, and despite the questionable names, these are the best iPhone models money can buy. If you're looking to get your hands on one of these devices as soon as possible, there are few important dates you need to know.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

OnePlus always seems to offer affordable yet powerful tools for videographers of all kinds. The camera hardware itself is crucial, but what's hardware without good software to highlight its real potential? It doesn't matter which version of the smartphone you have, they're all powered by the very same OnePlus camera app.

In 2019, Sony is mixing up its design, attempting to stand out among the sea of familiarity. Instead of emulating Samsung with punch hole cameras, they decided to target a rare section of the market, content consumers. There's the Xperia 1 for those who want the best, and the Xperia 10 and 10 Plus for the budget crowd.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

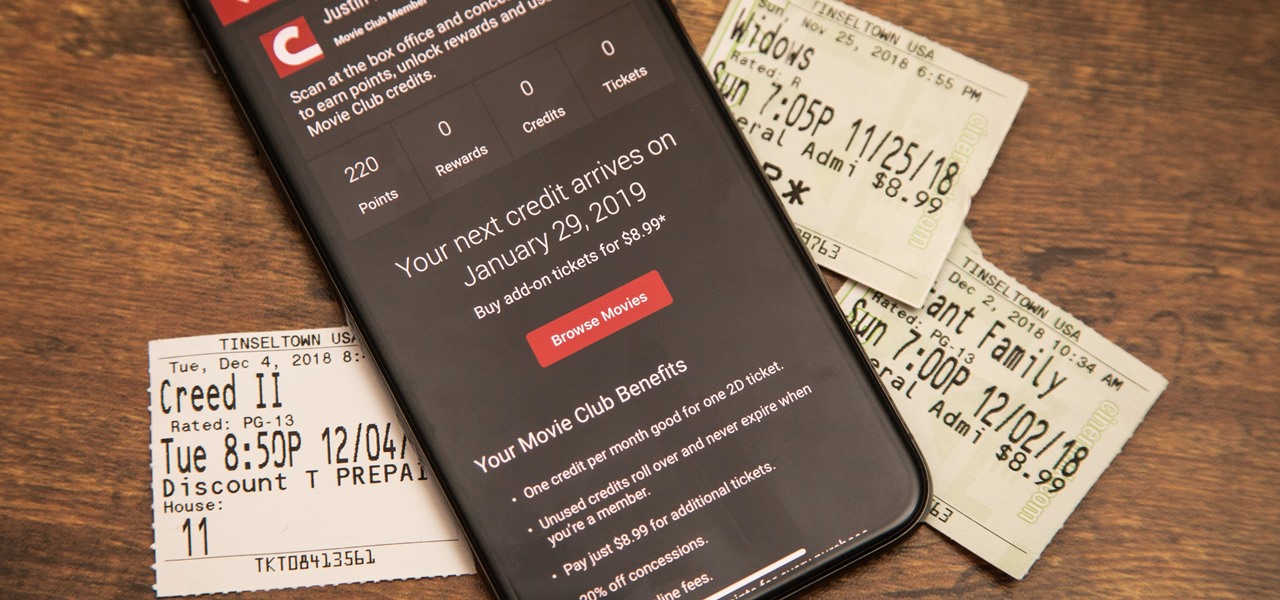
Cinemark may not be as big as AMC Theatres, but it also has a subscription if you want cheaper access to movie tickets. There aren't as many theaters, but if there's no AMC around you, there will likely be a Cinemark to save the day. But is the price of its Movie Club plan worth it?

In this jam-packed October, the Huawei Mate 20 Pro has flown under the radar in the US. Due to Huawei's lack of presence in the States, many are unfamiliar with the second largest OEM in the world. Huawei has continuously put out amazing mobile devices, and this year they released a phone that's nearly perfect on paper.

Over the years, Magic Leap's long-cultivated shroud of mystery led some onlookers to buy into the company's dream before even trying the device, while for others, the secrecy seems to have stoked the kind of resentment and overcorrecting critique usually reserved for the mighty Apple.

One of the biggest advancements in the new iPhone XS, XS Max, and XR is the dual SIM functionality that will let you use two cellular networks at once. Like Sinatra, however, Apple is known to do things its own way, so their dual SIM setup is a bit different than you might think.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Following the launch of the Magic Leap One earlier this month, the device and the company took a few hits from early reviewers. But it turns out those were just love taps compared to the absolute scorched earth acidic screed penned this weekend by someone well credentialed to dissect Magic Leap One: Oculus Rift creator Palmer Luckey.

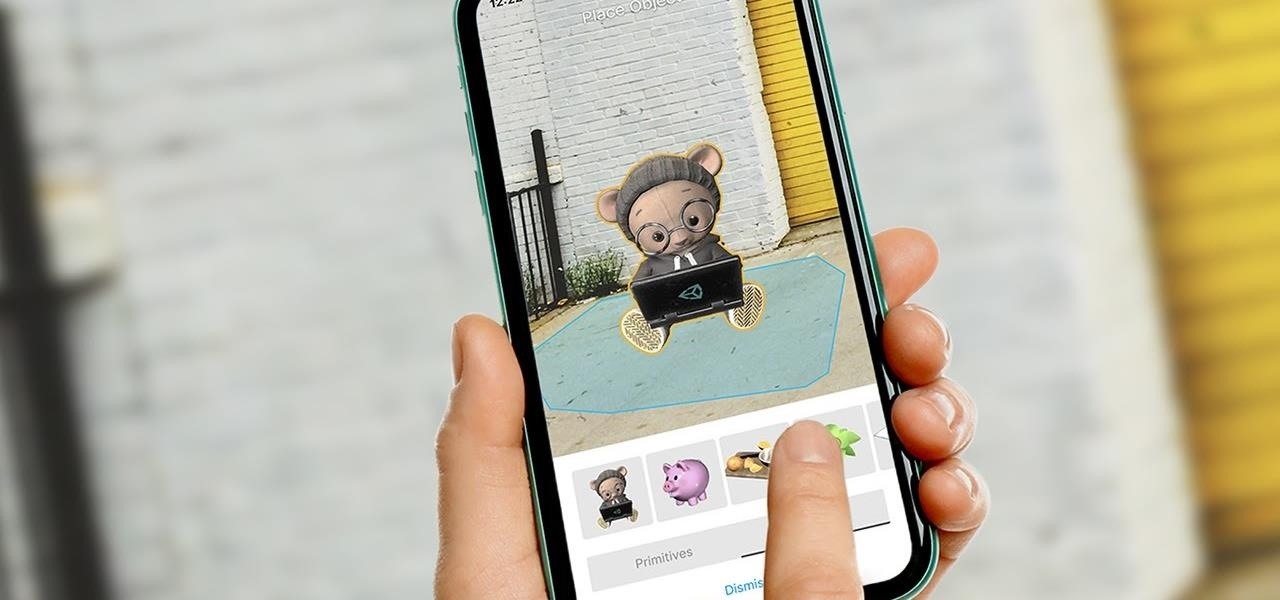
Since getting our hands on the Magic Leap One last week, we've been methodically delving into each feature and reporting our findings step-by-step. Earlier this week, we took a look at the Screens app (a video viewer) and the Helio app (an AR web browser). This time around, we'll be digging into the Create app, the experience that allows you to fill the real world with objects that transform the nature of your local reality.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

An incorrectly scaled object in your HoloLens app can make or break your project, so it's important to get scaling in Unity down, such as working with uniform and non-uniform factors, before moving onto to other aspects of your app.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

If you're in the market for a new smartphone, you'll likely scan spec sheets and read reviews of the top phones, compare display size and technology, RAM amount, and processors. But one factor that is often overlooked is cell reception — and for T-Mobile subscribers, there's only one device that has flagship specs and an exclusive antenna that will actually improve your signal.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

In the previous section of this series on dynamic user interfaces for HoloLens, we learned about delegates and events. At the same time we used those delegates and events to not only attach our menu system to the users gaze, but also to enable and disable the menu based on certain conditions. Now let's take that knowledge and build on it to make our menu system a bit more comfortable.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Thanks to ever more powerful smartphones — the iPhone X with its advanced A11 processor and the Galaxy Note 8 powered by Snapdragon's 835 come to mind — the mobile industry is fast closing in on consoles and PCs with regards to gaming. Game developers have been aware of this fact, and have ported many games once dedicated to computers onto our handheld devices.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

Adding additional photos to a movie project in iMovie for iPhone is relatively simple, but incorporating more videos to your timeline is a little bit more involved, only because there's more that you can do. Unlike with photos, you can trim the length of new videos, select the audio only, and add overlay effects.

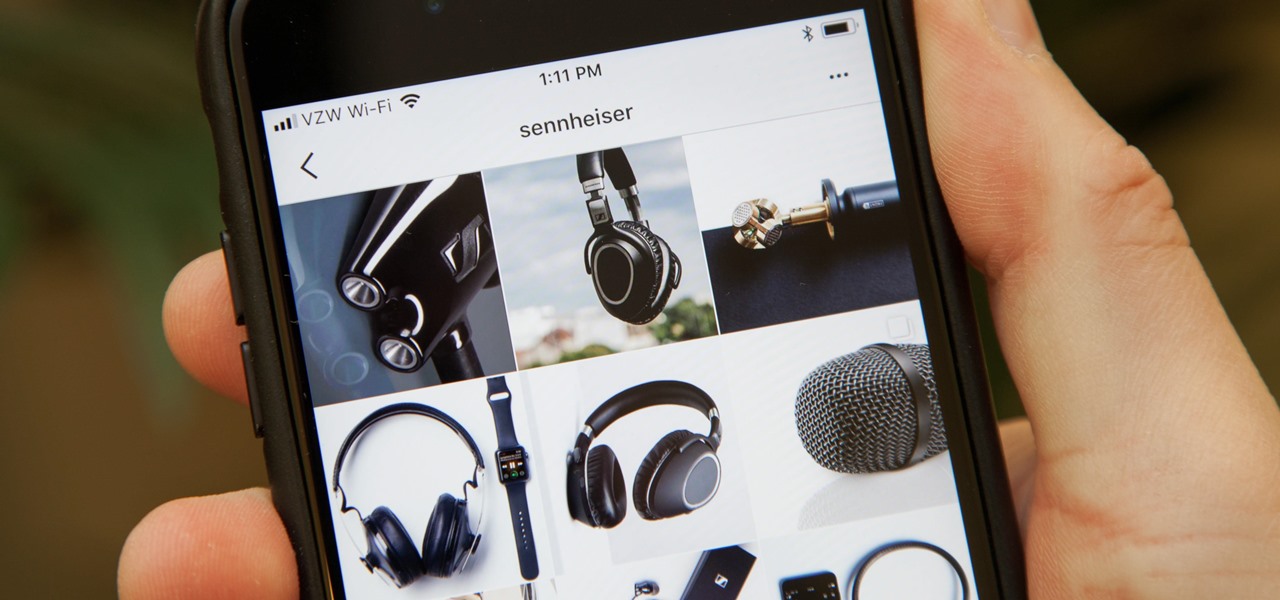
Andrew Mucci, a New Jersey-based vlogger who is also Social Media Coordinator at Sennheiser, likes to use Instagram not only as a platform for the brand but also as a place to experiment with content on his own account.