Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

The gig economy is thriving, and if you aren't already making money with your phone, you could be missing out on easy residual income. Some people just want extra cash, and some even manage to completely ditch the 9–5, enabling them to work at their own pace and set their own hours.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

The calendar app is one of the unsung heroes found within your iPhone. It's the ultimate personal assistant that you've come to rely on to keep track of your schedule and ensure you never miss a class or meeting, all while reminding you of upcoming birthdays and deadlines to help maintain good relationships with loved ones and colleagues.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

Defcon is the largest hacker conference with something for everyone, whether it be the talks, parties, villages, or any of the hundreds of events. In this guide, we'll take a holistic view at everything that goes into attending the con for the first time, from securing your electronics and making the most of your time to the logistics of getting there and finding the right place to stay.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

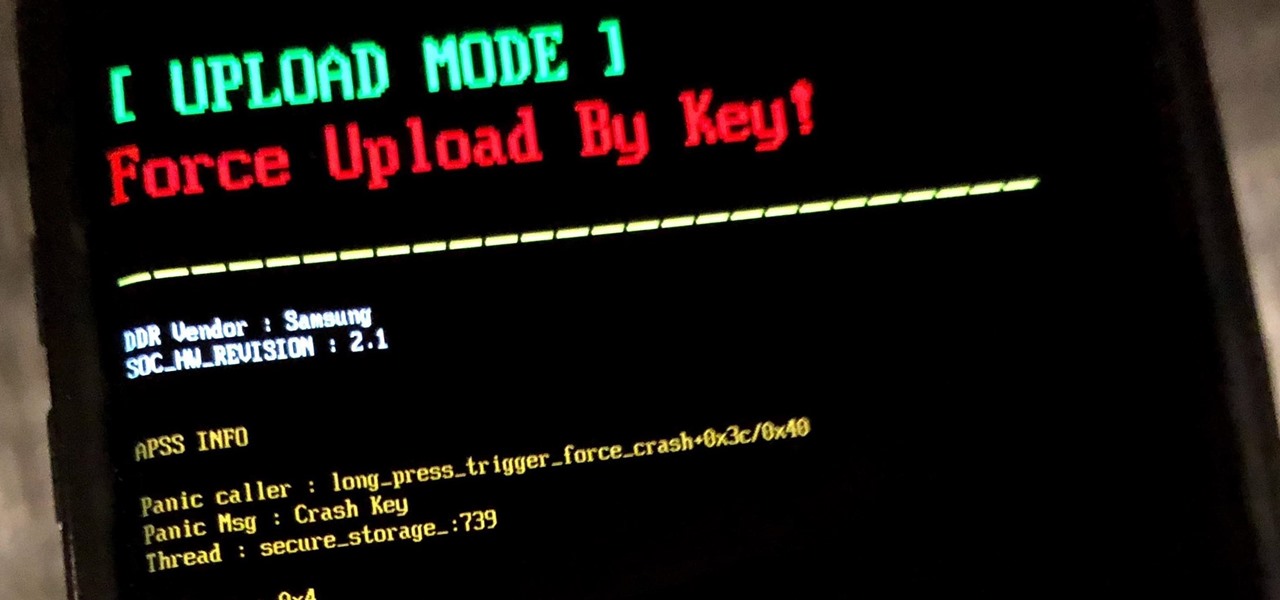
If you own a Samsung phone and enjoy rooting or modding your device, flashing official firmware can be very useful. Odin is Samsung's own internal program for loading such updates for testing purposes, and it's quite easy to use for your own custom modification needs.

One of the most popular usages of modern-day smartphones is listening to music. It doesn't matter if you download or stream your tunes, you are part of a massive group of users who do exactly the same. While statistics are a bit foggy on how many smartphones users download music, we do know that over 68% of American smartphone owners stream music on a daily basis.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

My first encounter with a phablet was late last year with the AT&T version of the Samsung Galaxy Note 2, having never touched or even seen its highly-acclaimed and pioneering predecessor. Initially, I was a bit overwhelmed by the enormous screen and taken aback by the dated stylus, which brought up ugly memories of my dad using his ten pound PalmPilot.

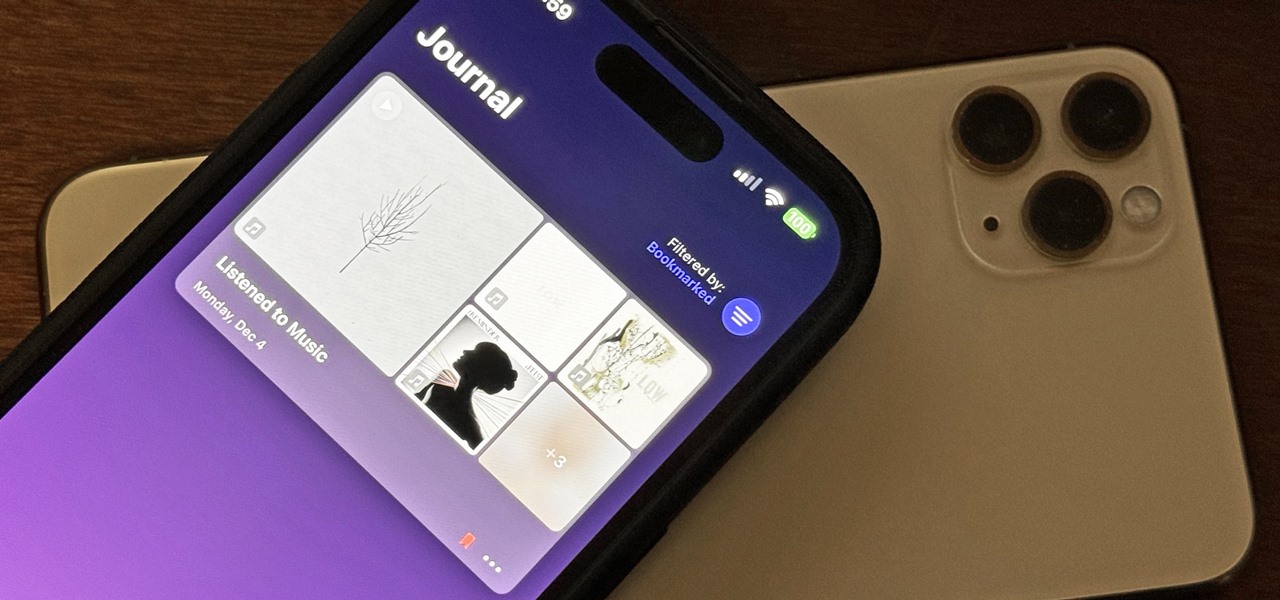
Perhaps the biggest new feature within Apple's iOS 17.2 update for iPhone is Journal, a new journaling app designed to help you take a moment to reflect each day using reflection prompts, recommendations via on-device intelligence, and suggestions for recent activities and events.

While new features in Safari, Camera, Photos, Notes, Weather, Messages, and other Apple apps may steal the show on iOS 17, there are some impressive new features you need to know about when it comes to FaceTime audio and video calls.

Apple previewed new cognitive, speech, and vision accessibility tools for the iPhone back in May, and they've finally been realized with the iOS 17 release. But there are more accessibility features than that hiding in Apple's latest software update — and they're not just for users with disabilities.

The volume buttons on the side of your iPhone can do more than just adjust the volume levels for media, ringers, alerts, Siri, and other sounds and voices. You can use them to perform different actions in certain apps and even create custom actions using the Shortcuts app. It's not exactly button mapping, but it's as close as you'll get without jailbreaking iOS.

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

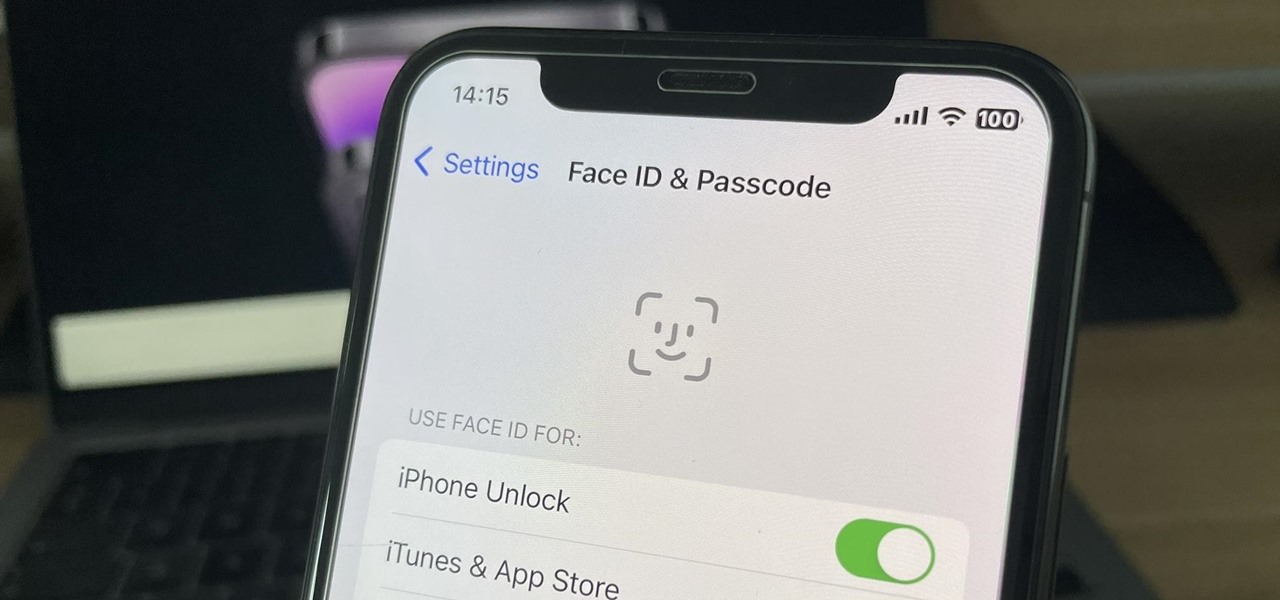
The iPhone 13 and iPhone 14 series models have a new feature on iOS 16 that lets you use Face ID when your iPhone is in landscape orientation. This is most helpful when trying to make purchases in apps and games where you use your iPhone rotated on its side. If you're having issues using Face ID in landscape mode, there may be some easy solutions to getting it working.

You're probably sharing a ton of information on your iPhone with other people, apps, and services without really realizing it. Now there's a new tool to show you just how much, and it can be an eye-opener as well as a fast way to manage sharing permissions and review your account security.

The latest software update for iPhone has a few new features you should know about, including an enhanced security feature to protect your Apple ID account from phishing and other attacks. Keep reading to see everything new that's included with iOS 16.3 for iPhone.

Night Shift, Dark Mode, Reduce White Point, and Zoom's Low Light Filter all help reduce the harmful effects on your body's clock that bright iPhone and iPad screens have at night. But there's another option on iOS and iPadOS that turns your entire display red, and it's useful for so much more than just late-night browsing in bed.

When you enable Low Power Mode on your iPhone, it's not always clear what measures it's taking to reduce battery drain and conserve power. Changes to energy-hungry features you use daily may be immediately noticeable, but some things you frequently use may be disabled or reduced without any apparent indicators.

Downloading content from TikTok is relatively easy, even if the video is protected, but the same can't be said of Reels, Instagram's version of short-form videos. Instagram doesn't make it easy to download content unless it's your own, and that's especially true with Reels. However, there is a way to bypass Instagram's restrictions on your iPhone and save videos locally without ever leaving the app.

For its latest take on augmented reality-infused playsets, Lego is giving the young, and the simply young at heart, its twist on the viral lipsync format made popular by TikTok with Lego Vidiyo.

The new iPhone 12, 12 mini, 12 Pro, and 12 Pro Max may seem like minor updates to the iPhone 11 lineup, but there are quite a few features that make them worth the upgrade. Apple has done a good job of highlighting all of those features, but some didn't get all of the love they deserved.

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.

Apple announced four different iPhone models during its Oct. 13 web-only event, but only two of them can be purchased this month: the iPhone 12 and iPhone 12 Pro. Preorders have already started for the two smartphones, and you could have one in your hands as early as Oct. 23, if you're lucky. To help keep your shiny new iPhone protected from scratches and cracks, try one of these cases.

Even though the Music app took a backseat during Apple's initial iOS 14 announcements, there's a lot going on in the updated app. Some of the new features and changes apply only to Apple Music subscribers, while others apply to your own music library, so there's something for everyone.

Are you tired of endless rows and columns of apps on your home screen? Before iOS 14, your only option was to hide apps in folders, uninstall them, or use some sort of elaborate workaround. You could hide a few stock apps easily enough, but that's it. Now, in the latest version of iOS, you can hide apps for real, and even hide entire home screen pages, and still access the apps in one convenient drawer.

Android 11 is here. Prior to Google dropping the naming scheme, this would have been a dessert with an R name (maybe Rice Krispies Treat or Red Velvet Cake) — but nope, just plain ol' Android 11. And after months of betas and a global pandemic, it finally debuted a little over a year after Android 10.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

3D printers allow hackers and makers alike to create something from nothing. They're an incredible technology that lets you build protective cases and covers for gear such as a wardriving phone and Raspberry Pi-Hole. 3D printers can even help you out in a bind when something breaks, and it's impossible to get the part, since you can just print one out yourself.

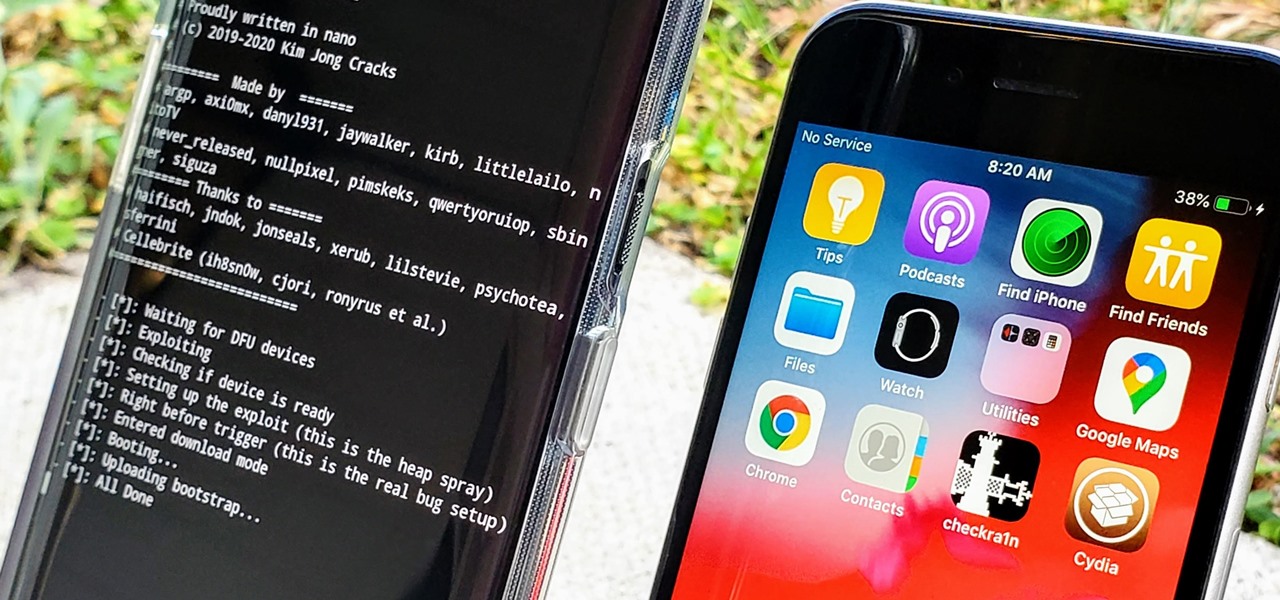
In the iPhone modding scene, the Checkm8 bootrom exploit, by developer axi0mX, led to a powerful jailbreaking tool known as Checkra1n. With it, you can jailbreak a variety of iPhone models without worrying about it getting patched later on. But in the past, it required you to have a macOS computer — but not anymore.

Network enumeration is one of the essential phases of an attack, but it can take a lot of time and effort depending on the size. We've all been spoiled by Nmap and similar tools, and while there is a learning curve involved, they are extremely useful. But there's also GoScan, a tool that builds upon Nmap, offering an automated way to enumerate networks and services quickly.

In a time where we're more connected than ever, privacy and security have never been more important. Maybe you're not concerned, but I'm sure there's someone in your life who is, and shopping for them can be daunting. However, with these gifts, you can provide them the tools they need to enhance their protection.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

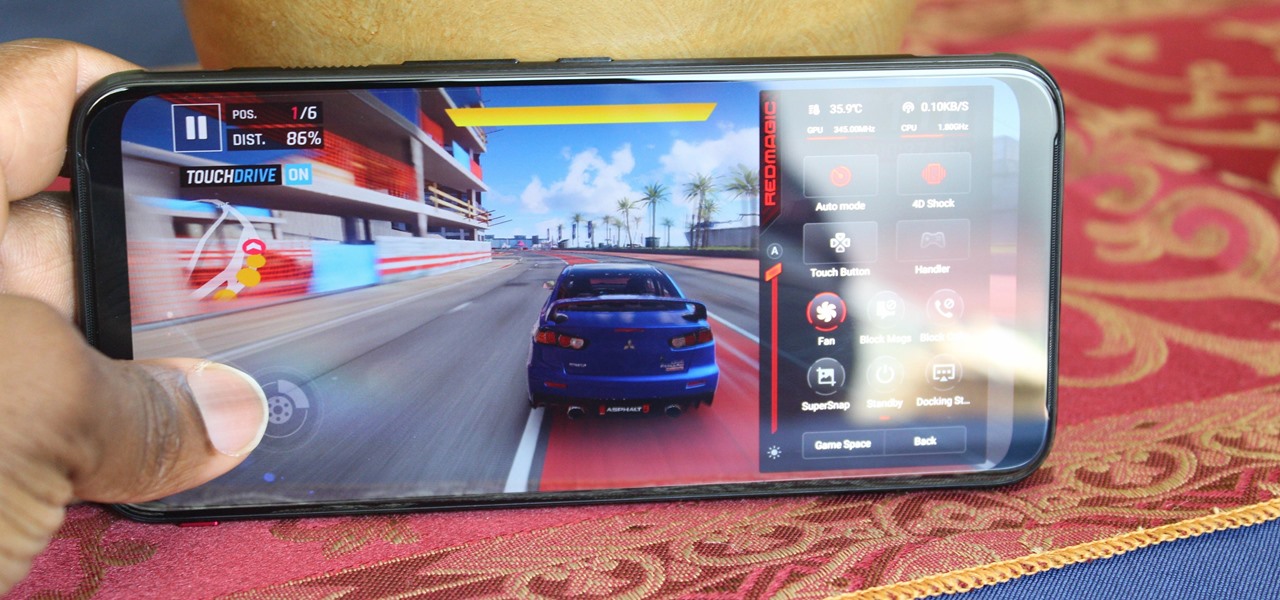
Mobile gaming has exploded in recent years, with experts predicting 2.4 billion global mobile players by the end of 2019. It already accounts for 47% of the worldwide gaming market, besting console and PC. No wonder we've seen the rise of gaming smartphones, a class of phones that specialize in mobile gaming.

Your phone's keyboard is one of the most commonly used apps. Whether you're typing out status updates, sending private messages, or just bombarding everyone in sight with as many emoji as you possibly can, you probably couldn't get by without a good keyboard app.

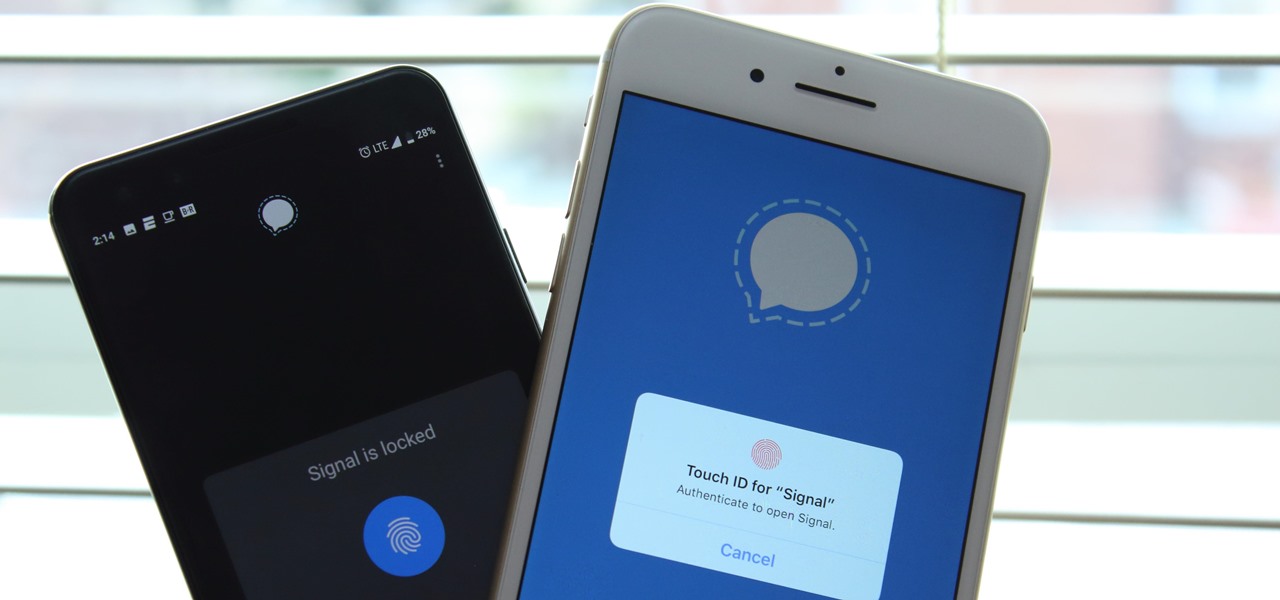
Signal is one of the best end-to-end encrypted messengers on the market. It offers robust security, keeps minimal information about its users, and is free to use. Switching to it as your main messenger can be a bit daunting, so to help, we created a guide to walk you through the process.