Amazon has completely changed the way we purchase household items, to the point where many of us haven't visited a big box, brick-and-mortar store like Walmart or Best Buy in years. And when you think about it, all of this success comes down to two main factors—convenience and price.

A sphere of clear gelatinous goo may not sound all that appetizing. But to food fad fans on social media, the raindrop cake—a soft and lightly flavored edible blob—has gone insanely viral.

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.
We knew it was coming eventually, but this is a bit out of left field—early builds of the next version of Android have been released almost two months ahead of schedule. Android N, as it's being called for now, is already available for the last two generations of Nexus devices, though it's just an early preview build for now.

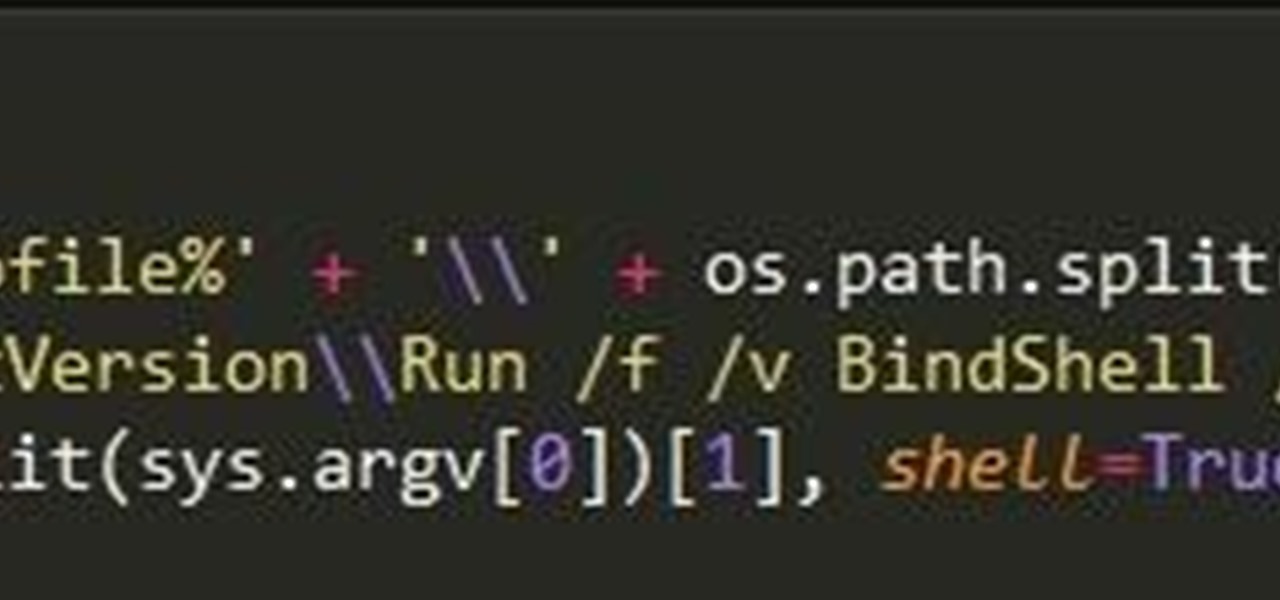
In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

The end of a weekend can be depressing knowing just how bad Monday morning will be when you get back to work, but that feeling is tenfold when coming back from a lengthy vacation with zero work responsibilities.

Hello fellow Null-Byters! This is my first post so please be respectful and constructed criticism is much appreciated. I am no professional, however I believe that it is important to understand technologies before you go poking at them and trying to break them, I therefore decided to make this series. In this "tutorial" we are going to setup a web server with php and mysql. I will be doing this with a raspberry pi because a pi is quite versatile.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - at my blog, here - https://techkernel.org/2015/12/11/embed-metasploit-payload-in-apk-easily/

Hello! This is my first post on this awesome website! I know that Windows exploits are less common than the more advanced hacks, but I found something I deem pretty cool and figured why not share it with you all. Alright, enough about me, lets begin.

I was bored when I found this piece of literature: ==Phrack Inc.==

Cheap Chinese knockoffs have been around for ages, but recently, skyrocketing demand has led to a massive influx of counterfeit smartphones. Sellers on Craigslist seem to have no trouble getting ahold of these fake devices, then passing them off as the real deal and turning a solid profit before vanishing into thin air. This type of scam tends to happen even more frequently after Apple launches a new iPhone or Samsung debuts a new Galaxy.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

Last year, the Washington Post's Ashley Halsey wrote an article on what really happens to your luggage at airports. In it, they unwittingly published a photo of the master keys the TSA uses for TSA-approved baggage locks. Now, thanks to that picture and a French lock-picking enthusiast, anyone with a 3D printer can make their own master keys to unlock any TSA-recognized locks.

Hi guys, I'm gonna keep this short because I got assignments and a lot of notes to study and also other how-tos and forums to reads. lol...Since I'm keeping this short...no story time just scenario. And I want to thank n3stor for giving me the idea to post this.

This is a collection of various guides and tools available on the internet. Instead of searching for 1 you can easily find whaht your looking for here.

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

Reddit is one of the internet's greatest sources of funny and interesting videos. Its user base is extremely active, and a system of upvotes and downvotes ensures that the best content always rises to the top.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

There are hundreds of delicious ways to enjoy caramel, from chocolate confections to sticky caramel apples and carnival bags of caramel corn. Caramel might be the special sauce that makes every dessert taste better, but it's also surprisingly simple to make.

Dulce de leche is a beautiful, caramel-like spread that you can slather onto bread or use to flavor cakes, cookies, or flan. You can also use it as a drizzle for ice cream, chocolate candies, and pastries. It tastes like heavenly toffee, translates roughly to "milk candy," and is popular all over Latin and South America. A version of the confection is also popular in the Philippines, in Russia, and is known in France as "confiture de lait." The traditional way to make dulce de leche is to slo...

Aside from the occasional "creative" collage, most of your friends on social media are content with pretty basic image and video posts. You can easily one-up them with celebrity cameos or awesome time-lapse videos, but to truly outshine them, try your hands at some creative double exposures.

Want to get even this Halloween? Want to scare somebody with nothing but a few lines of code? Here's how it can be done...

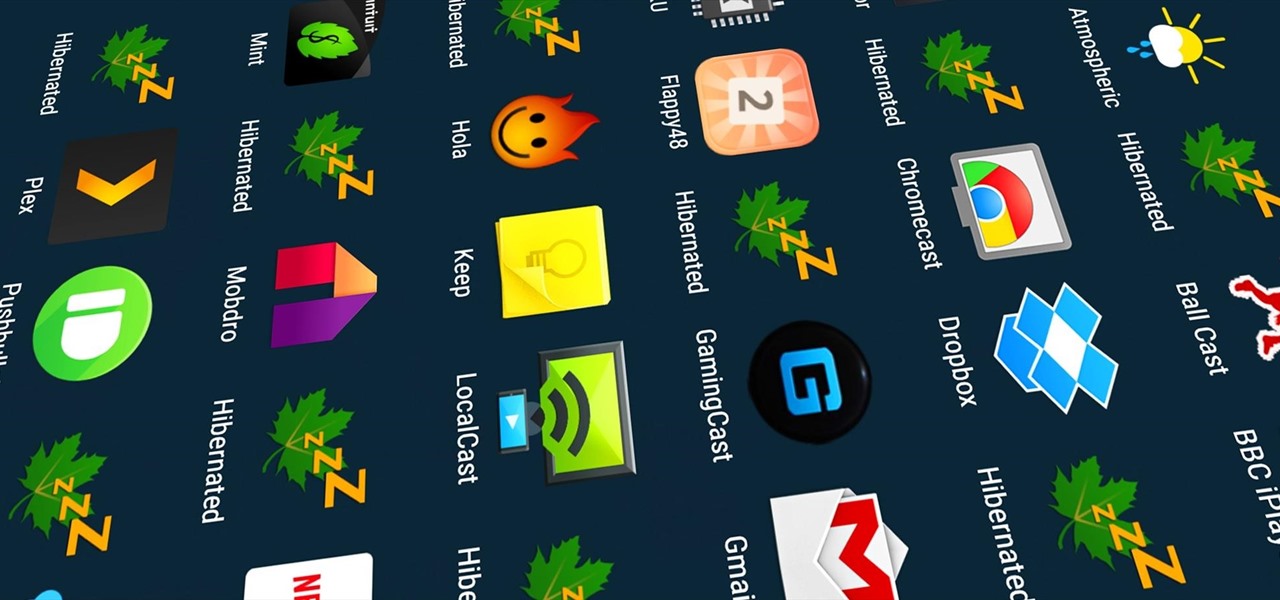
Greenify is a terrific app that allows you to put battery-hogging apps into "hibernation." Effectively closing the problematic apps and preventing them from running until you explicitly launch one of them, hibernation is a great way to save battery life while you're not using your phone.

What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break?

In recent months, HTC has decided to start breaking its proprietary apps out of its own ecosystem and into the Google Play Store. Along with the benefit of allowing its users to update their system apps more easily, this move also means that other folks can get a glimpse of what it's like to use an HTC device.

This is the best how-to's website that I've ever seen, and I wanted to join it. It taught me a lot, but, because I'm here to learn too, please correct me if I'm wrong.

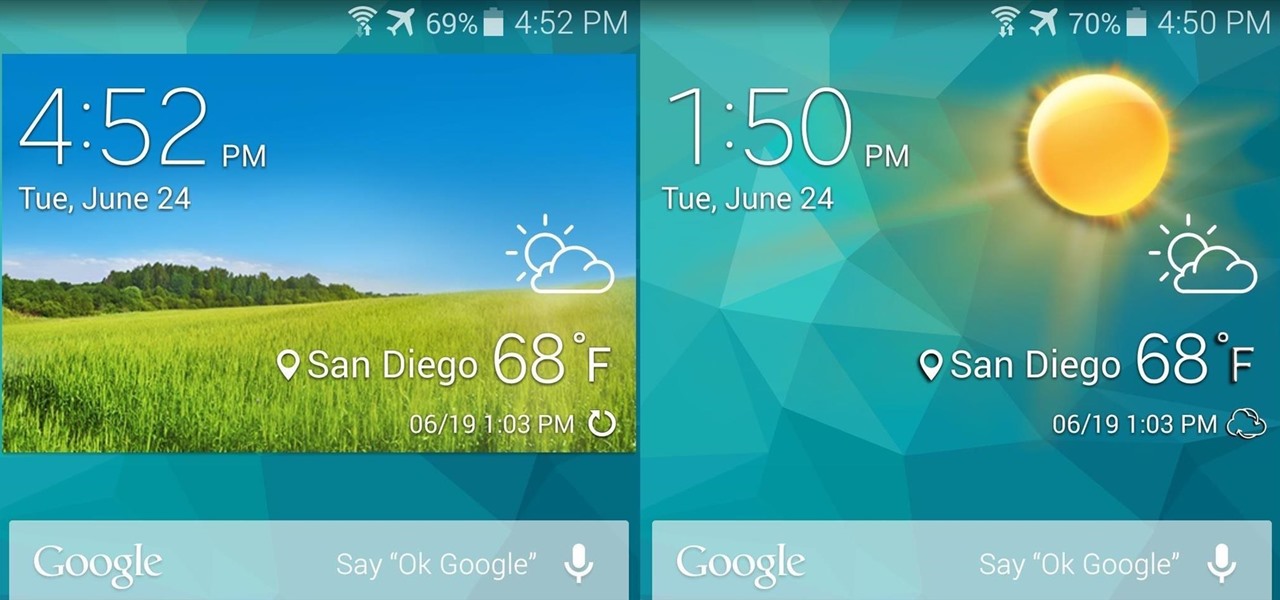
The weather widget on the main home screen of a fresh-out-of-the-box Galaxy S5 is meant to show off the screen. Super-high contrast and crisp definition on the individual blades of grass in the background let you know that the phone you're holding has one helluva display.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

You've got to be sick of it by now. Those meaningless and unsatisfying articles, lists, and videos you were duped into clicking on because their headline made them impossible to resist.

April Fools may be over, but any day is a good day to prank someone, and the best time to do it is when everyone's eyes are glued to the television.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

I recently wrote about Twitter's super now app called Vine, which lets people create 6 second video clips that can be embedded in a tweet. Those videos have their own proprietary extension, but if you want to turn those 6 second videos into an animated GIF, you can now do so thanks to developer Esten Hurtle, who created VineGifR, a seamless way to transform your (or someone else's) Vine movies into GIFs.

This post has been brought to you by the letter S. With the Christmas season fast approaching, it's time to ask one of the most important questions of our lifetime:

TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in the Windows Store for free or purchase.

The guitar is a double-edged sword. I've played all my life, and though I love the act of guitar playing, there are quite a few people I could live with never hearing play again—ever.

Hello! I want to share a few thoughts about affection with you. This post is for all who wonder what is or could be the best way to communicate with the person you like. There are many ways of expressing. When Two Worlds, Mars and Venus Collide.

Remember summer camp? Remember the smell of the log cabins? The feel of the treated wood? Well, you can create something for your home that's perfect for a nostalgic summer camp aesthetic. Meg Allen Cole (recently of Threadbanger) was inspired to make this mid-century modern wall hanging piece made from a small wooden log (or branch) when she was at a relaxing, wooded vacation spot in Maine. And she shows you how to make one, too!

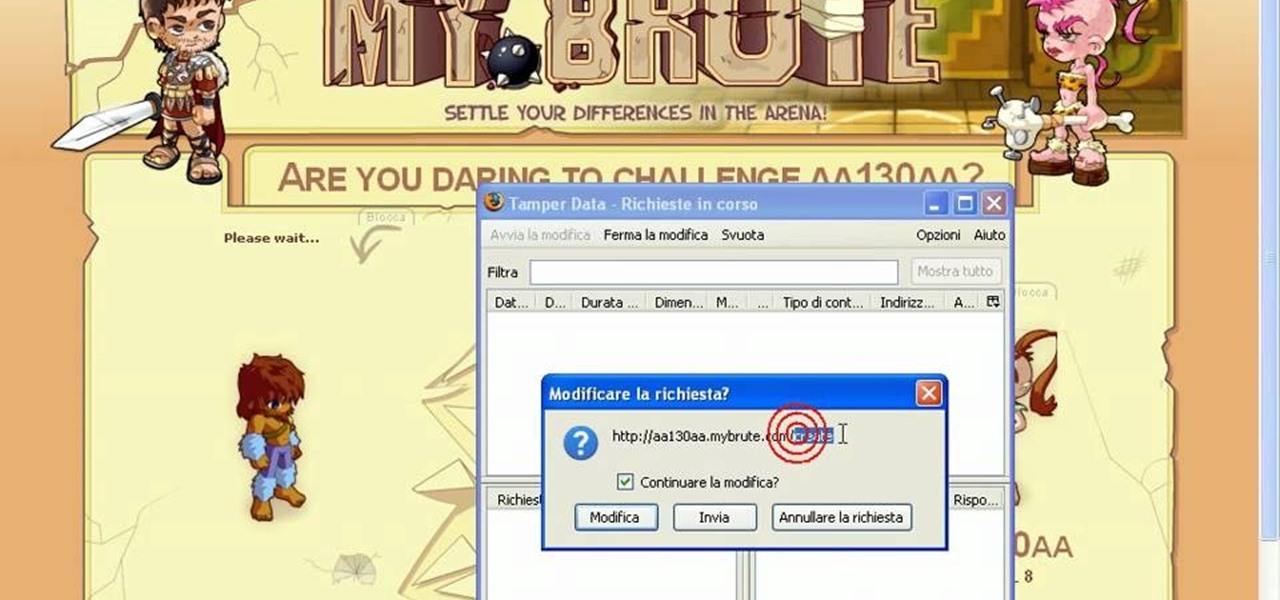
Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to cheat MyBrute for a bear (05/08/09). This is the easiest way to get a bear!

Mr. Shane Benedict describes the delicate balances necessary to hit that perfect boof every danged time.