Noted poet T.S. Elliot once wrote that "April is the cruelest month." But Magic Leap might argue that March is the most miserable, as the Ides of March brought more legal woes to augmented reality startup. Elsewhere, its closely-held branding secrets have been spilled by way of the US Patent and Trademark Office (USPTO).
To revise a line from the Blues Brothers, when it comes to ARKit apps, we've got both kinds — home utilities and games. As such, two more candidates for each category have made their way to the app store.

The drama continues! In the latest installment of the feud that has rocked the driverless vehicle industry, Waymo is now accusing Uber of withholding a secret LiDAR device.

Apple is notoriously private when it comes to perspective products, but the latest leak from their De Anza office in Cupertino suggests that a new augmented reality device could be coming to a store near you.

Apple seems to want the public to perceive it as an environmentally-conscious entity, as evidenced by the company's recently published Environmental Responsibility Report. But as it turns out, they may be hindering recyclers from salvaging old iPhones and Macs by ordering the devices to be shredded instead.

In this how-to video series, learn from contractor and power tools expert Ed Reyes how to use and maintain a plunge router.

In this how-to video series, learn how to use a cordless nailer from certified building contractor Matthew Christian. Matthew will demonstrate how to load nails in a cordless nailer, how to unjam a cordless nailer, how to change air cartridges and air filters in a cordless nailer, how to properly handle a cordless nailer, how to change the battery in a cordless nailer, how to charge cordless nailer batteries, how to oil cordless nailers, how to flush a cordless nailer.

In this series of DIY video clips, expert contractor Dominic Capone demonstrates the simple process of how to install a shelving unit to drywall using anchors. These basic tips can be easily adapted to construct a closet, pantry or entertainment center. With the proper anchors, tools and instruction from these free video clips, you’ll be able to hang just about anything on drywall.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

Developers in the augmented reality industry got a lot of love this week.

Any app on your iPhone could potentially listen in on your conversations and use that information to target you with tailored ads. Although most companies, including Facebook and Apple, have come out and vehemently denied these claims of spying on consumers, who's to say they're telling the truth? The only way to be sure you're safe is to take matters into your own hands.

Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this saga has Apple outright disabling the Lightning port.

While IKEA is collaborating with Apple for its ARKit furniture app, Marxent is ready to help the rest of the interior decorating and home improvement crowd with their apps.

The Deepwater Horizon oil spill that began on April 20, 2010, was the largest maritime oil spill in history. Killing 11 people and discharging 4.1 million barrels of oil and natural gas into the Gulf of Mexico, the event was an unparalleled personal, environmental, and business disaster. It was also the first major oil spill to take place in the deep ocean.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

The modern remote workforce faces many challenges, but perhaps none is greater than organizing calls and syncing tasks. Many platforms are convoluted and difficult to manage. Team members get bogged down by administrative tasks instead of staying productive.

The reveal of Magic Leap One: Creator Edition brought with it some insight into the path the device took from prototype to "final" design.

Bed bugs are parasites not yet known to spread disease — but they cause plenty of irritation. As scientists and landlords search for new ways to deal with the pests, a new study examines how we can deter bed bugs without so many chemicals.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private detectives, and many other organizations.

One of the best things about Christopher Nolan's Batman trilogy is how realistic he makes the caped crusader feel. Unlike the Joel Schumacher or even the Tim Burton versions, Nolan's world seems grounded in some level of scientific fact. But just how close is science to actually being able to replicate some of the Dark Knight's gadgetry?

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

It's already been a banner year for mergers and acquisitions in the augmented reality industry, with WaveOptics and Ubiquity6 among the notable companies acquired. Two of the more active M&A players, Snap and Epic Games, continued their respective buying sprees this week with major deals supporting their AR strategies.

This year, as part of the Next Reality 30, in partnership with Snap, we're spotlighting an up-and-coming innovator in augmented reality. Specifically, we were searching for an independent developer or creator who embodies the bleeding edge spirit of AR and its ability to leverage machine learning. This year's honoree is Aidan Wolf.

Congress is asking top U.S. defense contractors to disclose their corporate plans if the military is forced to cut $500 billion from its budget early next year, putting the companies in the middle of a political fight between Republicans and the White House. U.S. defense firms drawn into Congress budget politics - CNN.com.
Employees of the US military contracting group are seen in new leaked video shooting their machine guns at random citizens while driving through the streets of Baghdad.

Just found two interesting articles, take a look: » Busted: Biotech Leader ‘Syngenta’ Charged Over Covering Up Animal Deaths from GM Corn Alex Jones' Infowars: There's a war on for your mind!.

Back in the '80s, NASA and the Associated Landscape Contractors of America did a study where they discovered which houseplants were the most effective in purifying the air in space facilities. Though you may not be living in a rocket ship, you can definitely benefit from having one or more of these plants in your home.

Xe Systems, the Private-Defense-Contractor-Formerly-Known-As-Blackwater, has been busy attempting to re-brand themselves. They have a new name, several new sub-names, and have at least titularly shifted their focus to training rather than mercenary work. Controversial founder Erik Prince is no longer with the company, which is now owned by a large investment consortium.

In this video from This Old House, you'll learn how to repair vinyl siding with General Contractor Tom Silva

In this video, This Old House General Contractor Tom Silva demonstrates how to repair a basement wall leak around a drainpipe.

In this video, This Old House landscape contractor Roger Cook explains how to prune and train rose bushes.

How about a laser? One that is strong enough to nudge debris out of earth orbit. That's what NASA contractor James Mason wants to do, and his lab simulations suggest that the idea is possible. Mason wants to use a 5kW ground-based laser and a ground-based 1.5 meter telescope to spot potentially hazardous space waste and shove it off, by about 200 meters per day of lasering. It's kind-of like air traffic control for near earth orbit.

This weekend in a jungle estuary, the DEA and local Ecuadorian police seized a prototype narco sub that may be the most sophisticated one yet. Complete with air conditioning and periscope, this 100 foot creation would have carried a more cocaine tonnage than any previously captured narco sub. To give you a perspective on the resourcefulness of these outlaws, consider this. A U.S. Navy Virginia Class attack submarine will run around $2.8 billion. But a drug lord in Cartagena would make you one...

Video game ranking site VGChartz reports that Mike Leyde, a 56-year old steel contractor from Riverside, California, has broken Bejeweled 2's scoreboard with a score of 2,147,783,647.

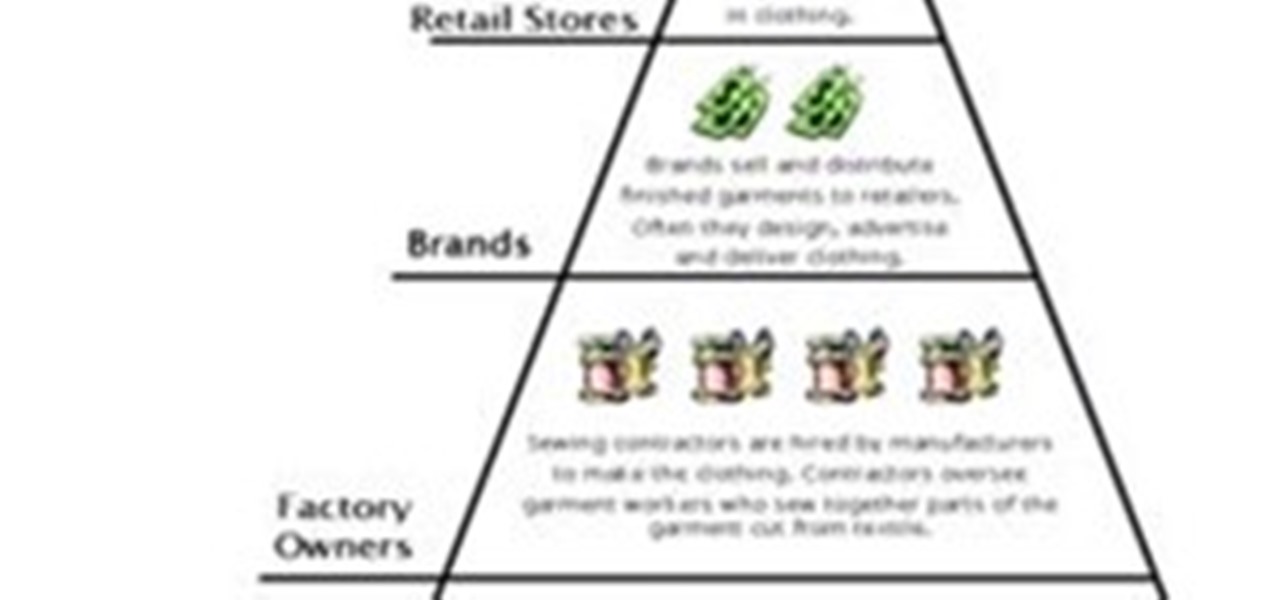
The United States is a hierarchical country where the weak ones are at the bottom and the powerful ones are at the top. Garment workers are at the bottom of the list although they are the most important. Without them there would be no fashion industry. They sew and cut the garments that people buy, the raiment that models wear on the runways. After the garments are sewn, factory owners send the garments to contractors to get make the clothing. Contractors make sure the garment workers sew the...

Continued from Organize Yo'sef Part One!