When you have an infection, a doctor prescribes antibiotics to make the bacteria that causes it disappear. Sounds like a good idea, but the disappearance of microorganisms that have inhabited humans for millennia could be driving rising numbers of serious illness and debilitating conditions.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

Windborne microbes shifting in the snows of the great ice sheet of Greenland may be able to neutralize some of the industrial contaminants oozing out of the melting ice.
Changing your Facebook profile picture to a video is a great way to stand out from the crowd. A regular video file isn't the only option, though — if you're an iPhone user, you can also upload a Live Photo as your new profile picture to add more pizzazz to your Facebook page.

Being a city dweller does not mean you cannot save the planet — or your food scraps. Climate change and resource management are big issues. Composting in any size space is not only possible, but it gives you a chance to reduce greenhouse gasses and reuse food scraps. Right now, about 40% of all food in the US goes to the landfill. In addition to planning meals and using your food in creative ways to reduce the amount that goes to waste, you can compost.

What's in a sneeze? Quite a lot—dirt, mucus, and infectious germs—it seems. And sneezing the right way can reduce the germs you share with neighbors.

Joe McKenna died when he was 30 years old. A young married man with his future ahead of him, he was cleaning up the station where he worked as a fireman. Struck by a piece of equipment fallen from a shelf, Joe complained of a sore shoulder. Over the next week, Joe worsened and ended up in the hospital. Chilled, feverish, and delirious, his organs shut down from an infection we'd now call septic shock.

Samsung and Apple are back in court, but this time it's not just money at stake. The Supreme Court's decision could have a far reaching effect on patent law and innovation in design.

Whenever I went to the grocery store on a mission for blueberries, I'd inevitably find myself staring at these weird little tomato-looking berries... and wondering what the hell they really were. Tomatoes? Berries? A weird science experiment? Then, I'd set a pint of blueberries in my cart and carry on, forgetting about them for the time being.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - at my blog, here - https://techkernel.org/2015/12/11/embed-metasploit-payload-in-apk-easily/

I have been on Null Byte for a long time, a very long time and. I havent always had an account here, ive like many of you also have, been looking and decided to make a profile to contribute.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

If your iPhone can't last a full day without being recharged multiple times, something's wrong—but it might just be working harder than it needs to.

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

Unless you're someone who's terrified of social situations, chances are you love to talk. But no matter how much you want to share you life story or take over the conversation, you shouldn't. Your socially awkward coworkers that keep their mouth shut might actually have a leg up on you at work, and here's why.

Last week, I showed you why your refrigerator is one of the best tools in the kitchen when it comes to saving money and preserving food at its tastiest. But did you know your freezer is another underutilized ally in the cooking game?

With the new year right around the corner, it's time to talk about the end of the 19th century, a time which plays an enormous role in Steampunk. If you've done any reading of British books written from about 1890 to 1899, you may have come across the phrase 'fin de siecle' and wondered what it meant. You also may have come across this term in reading about the late Victorian era. No worries, I'll tell you all about it! Image by Giovanni Dicandia

Welcome to Minecraft World! Check out our tutorials, post to the Inspiration board, and come play on our free server! HELLO, FELLOW MINECRAFTERS. Pmaguire here, bringing you my favorite idea for a competition so far! I hope that you will come to love it as much as I do! Well, starting off, as the title states, this week's Redstone Competition will be PvP Arenas! Except, not just ones where you physically fight. You have to have traps, things that make it hard to fight, and various ideas using...

Unless you're a high-schooler building a nuclear fusion reactor, the hardest part of a science investigatory project often is coming up with a good idea. You want it to be cool yet feasible, novel but still useful.

While Apple is full steam ahead on iOS 18, which is expected to drop sometime next month, it hasn't forgotten about iOS 17, which still dominates most users' iPhones. On Aug. 19, Apple issued a rerelease of its iOS 17.6.1 software for iPhone.

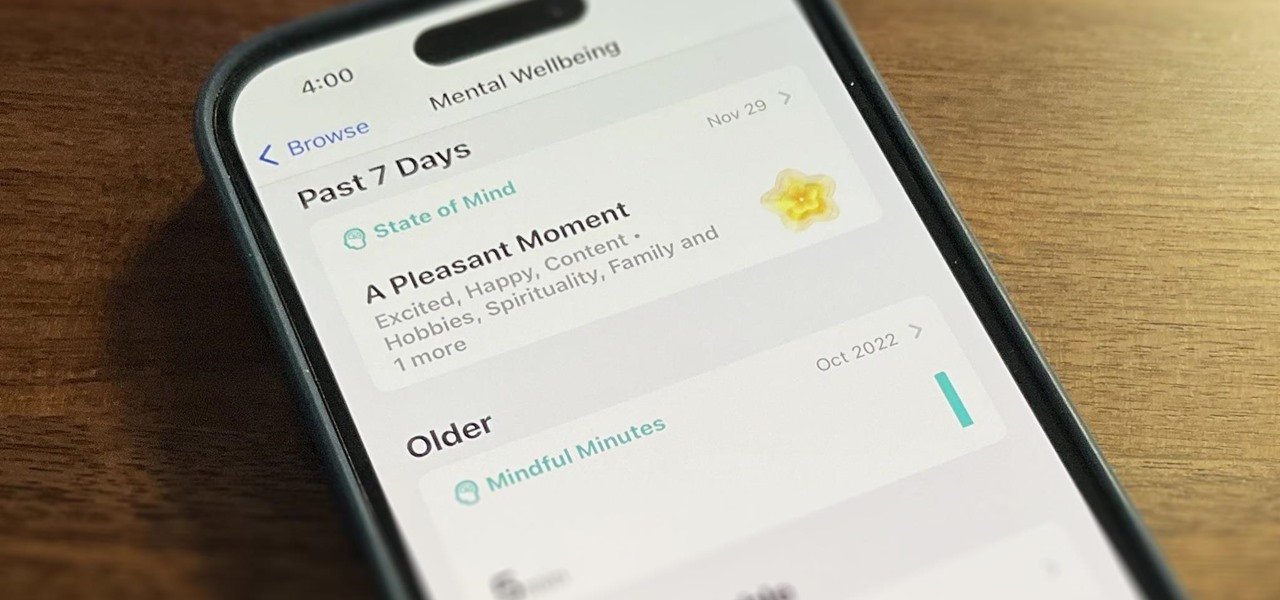
With iOS 17 on your iPhone, you have access to new health- and fitness-related features that can help you improve your mental well-being, reach your fitness goals, take your medication on time, avoid eye strain, and more.

Your Apple Music subscription is tied to the Apple ID that subscribed, so you can stream content from any iOS, iPadOS, macOS, tvOS, or watchOS device that your Apple ID is signed in to. However, things get slightly more complicated when you want to listen to Apple Music on another device you use with a different Apple ID, such as a work iPhone. Complicated, but not impossible.

The 2020 iPhone SE had been through the rumor mill for a long time, but Apple finally unveiled the second-generation iPhone SE on Wednesday, April 15. While it doesn't sport the 4-inch design of the original SE, it combines a small form-factor with modern specs. The big question, of course, is when and how you can get your hands on one.

Whether you're trying to become an influencer or just want to share better photos and videos, the best camera to start with is your smartphone. It is likely the only camera you always have on you and it's probably capable of excellent pictures and video capture. But with a little help, it could definitely be better.

People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the outstanding feat of "magic" presented, we nevertheless hold fast to our survival-based grip on the truth: we just saw simply "can't be real."

This week, the beginning of an epic legal battle was set to begin between augmented reality players Magic Leap and Nreal, the small China-based startup accused by the former of stealing trade secrets.

When filtered through the prism of the top stories of the year, the business of augmented reality 2019 was defined as much by epic failures of AR startups as it was by the promising developments that propelled the industry forward into 2020.

Thanks to numerous smartwatch deals this holiday season, many people are receiving their first one. But what exactly can they do? In regards to fitness, quite a lot. With a growing list of sensors and software updates, these small devices can be the very thing you need to ultimately reach your fitness goals.

This week's Magic Leap Lumin OS update contained a number of goodies, including iris authentication, and a way to stream to Twitch from the device.

So you've been playing Call of Duty Mobile for some time but can't seem to get MVP at the end of the battle. Well, since the game is a competition of players and bots, you're in an uphill battle. But you don't have to languish at the bottom. With the help of these tips, you might just nab your first MVP.

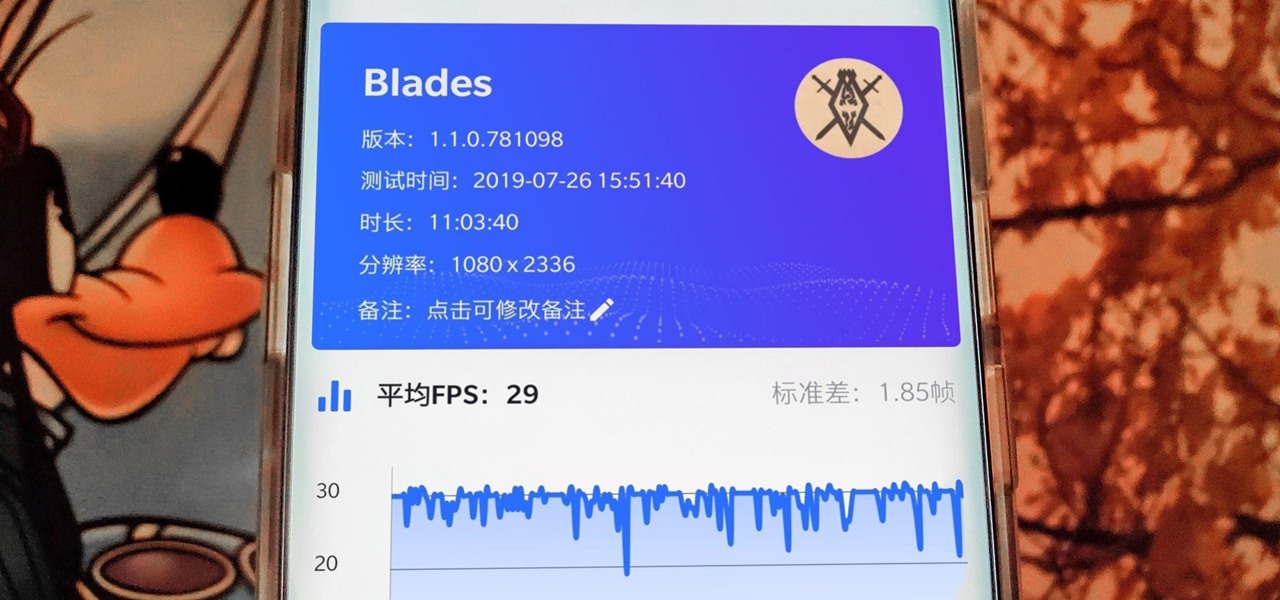
When you're gaming on your Android phone, does it sometimes feel "slow" and you can't figure out why? That means a drop in performance, which is when the frame rate dips, causing some noticeable stutters and lag. There's not really a way to know what's wrong unless you made the game yourself. But on the bright side, you can check any game's FPS with a simple tool.

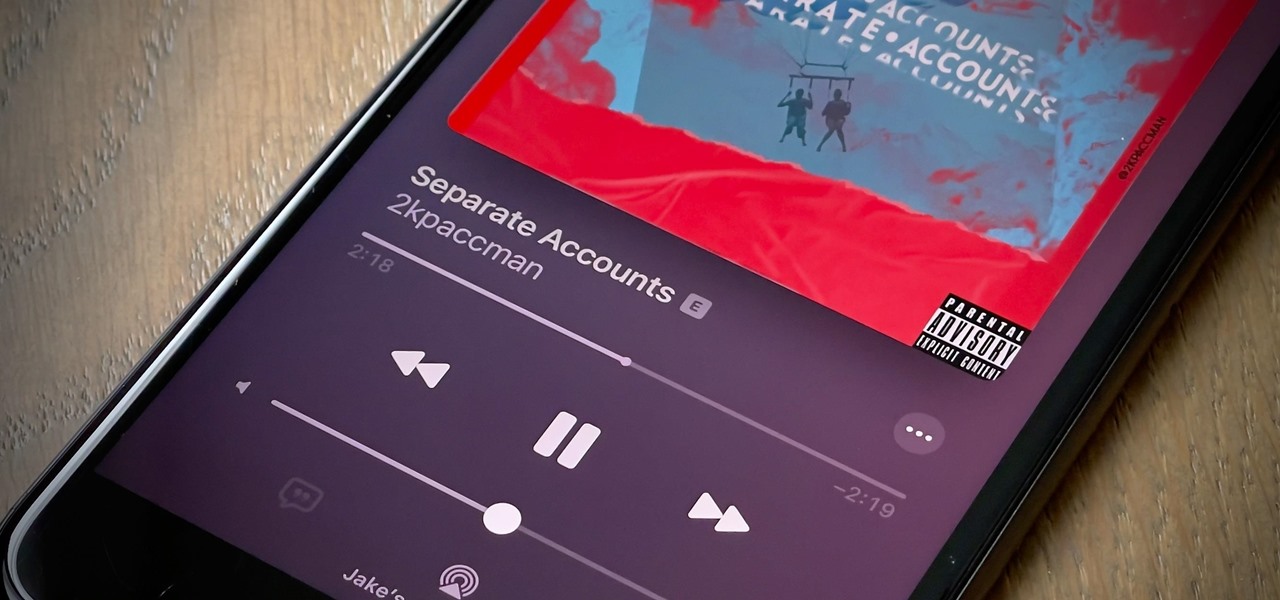
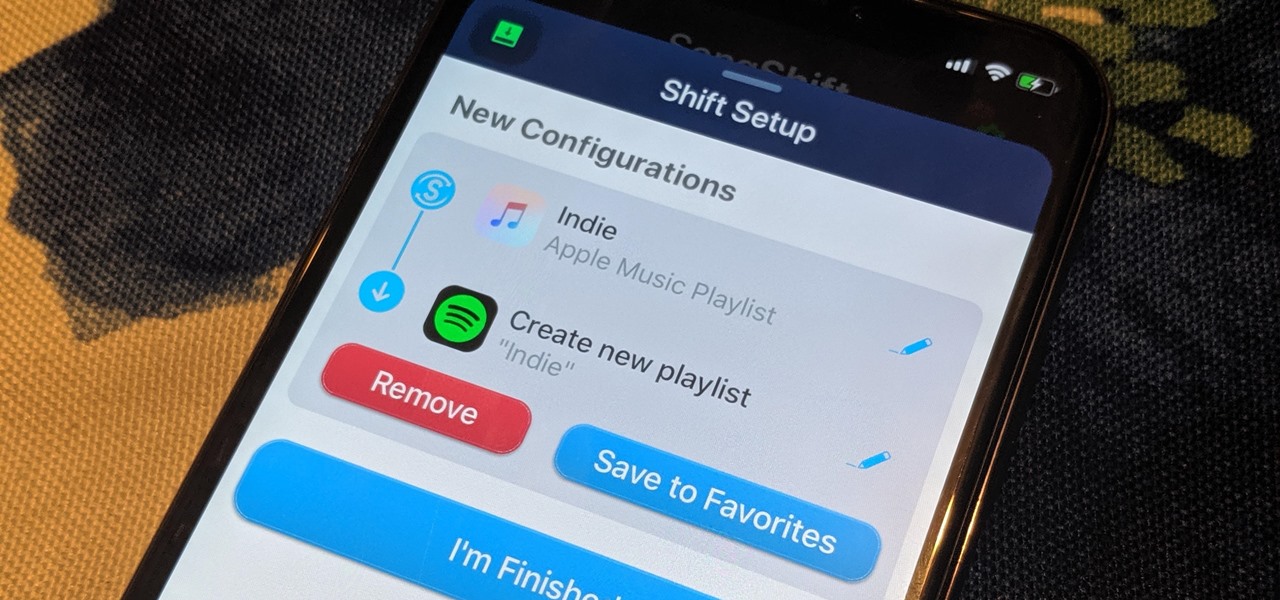
Switching from one popular music streaming service to another shouldn't have to be a hassle, but it is if you want to transfer all your favorite music over. No popular service offers a built-in feature to export or import playlists, so if you want to move your favorite Apple Music playlists over to Spotify, you'll have to use a third-party service.

Comparing the present-day states of the consumer and enterprise sectors of augmented reality is like evaluating the merits of sports car versus work trucks. Like consumer AR, sports cars are sexy and exciting, but perhaps a bit impractical at times. On the other hand, enterprise AR is utilitarian, but it gets the job done and, in the long run, pays for itself.

When I first found out about Nreal, back in the spring of 2018, the most interesting thing about the company's story was the founder's background. Chi Xu, the CEO and founder of Nreal, previously worked at Magic Leap as a software engineer.

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

What does mainstream augmented reality look like? I'm not talking about the stuff you see in concept videos and science fiction films. No. What does it really look like?

While Microsoft dominated the augmented reality news at this year's Mobile World Congress, a small AR startup we've covered in the past arrived in Barcelona, Spain, to unveil the next phase of its mission.

When your iPhone goes missing, it's serious business. Depending on your usage, your whole life might be connected to your iPhone, not the least of which includes debit cards, credit cards, and Apple Pay Cash stored in Apple Pay. While it's nearly impossible for someone to use your money with Apple Pay, it's still a good idea to disable it until you find your iPhone, just in case.