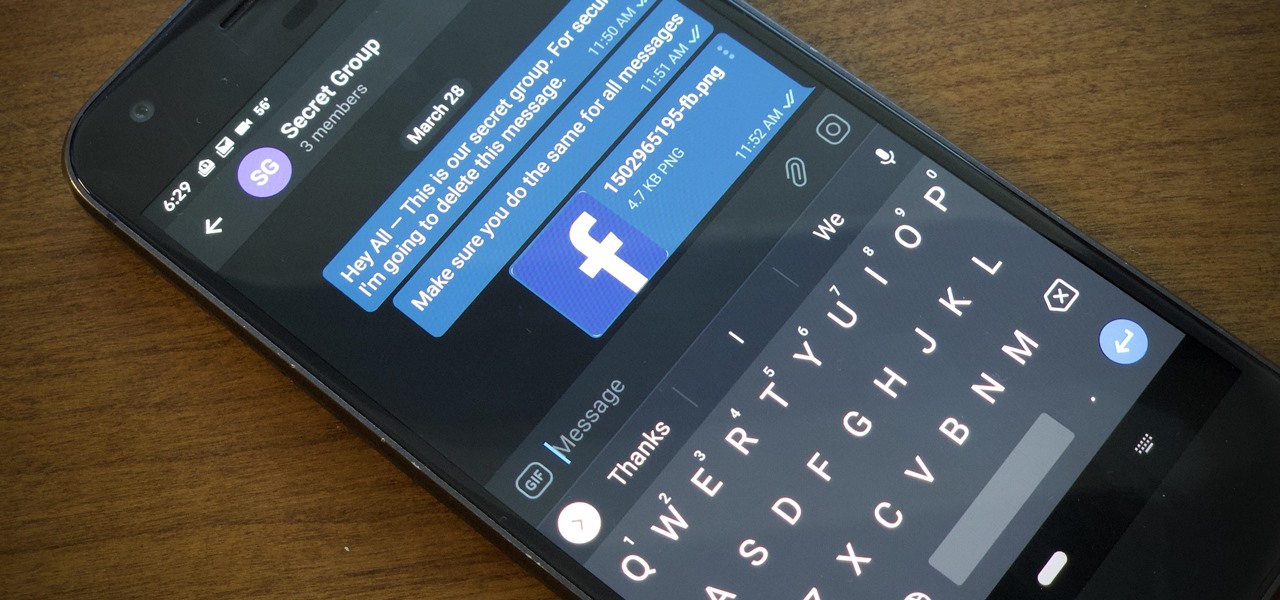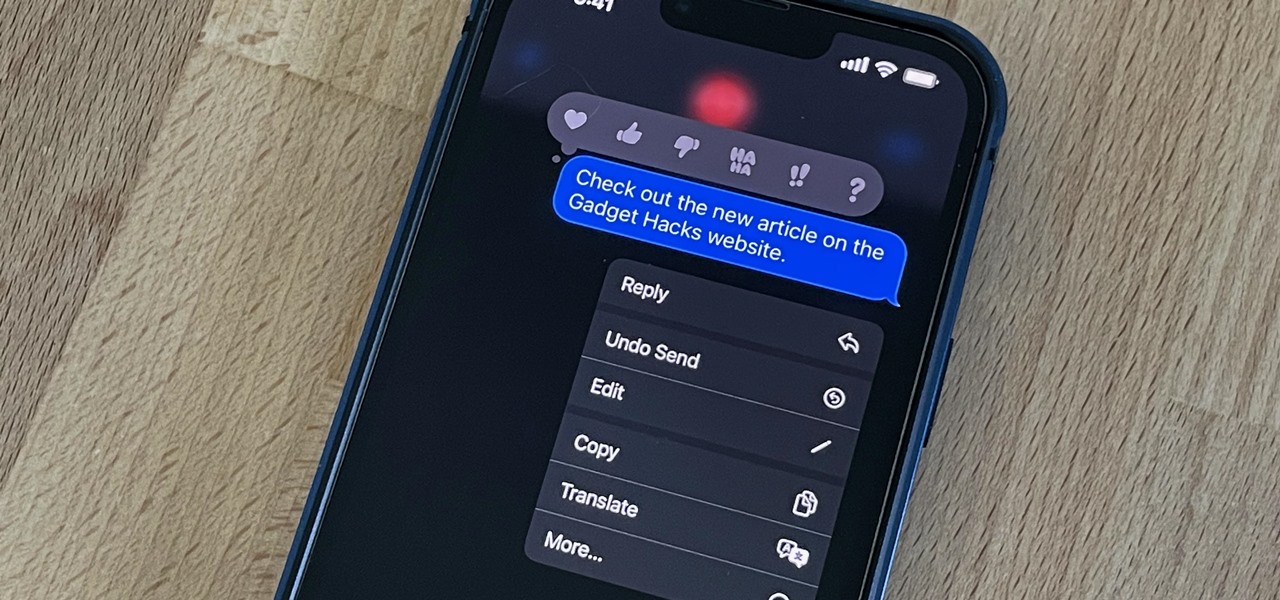
While you can quickly see the edit history of a modified iMessage in the Messages app, there's no way to view an iMessage that somebody in the conversation deleted unless you happened to see it before it disappeared. But that's only true if you didn't implement these security measures on your iPhone.
Ah, the dreaded "green bubble" group chat. All it takes is one non-iPhone contact to turn an entire thread from iMessage paradise to SMS slog. Normally, it isn't that bad since the group chat still functions. However, sometimes, you end up getting messages individually instead of in a single group thread. Before you go blaming your Android friends, know that the issue is probably on your end.

To be honest, the Mail app for iPhone had always been somewhat forgettable. It lacked many of the features that made third-party clients like Spark and Edison better, but with iOS 13, the gap between Mail and its competitors is much smaller. Apple updated the layout and added many new features to its native emailing app, and that may be just enough to get you to switch back.
You're in constant communication with your friends and family. The only issue? Nobody uses the same app. Messenger, Instagram, WhatsApp — you have contacts spanning all three, and the resulting balancing-act to keep in touch can be overwhelming. That's why Facebook — who owns all three apps — is coming out with a way to call and message friends across all three platforms from one place.

You can almost detect the collective breath-holding of the augmented reality industry as it waits for Apple's inevitable entry. A new Apple wearable built with augmented reality technology is likely the device that will finally make the smartphone take a backseat.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

One of Android's most glaring weaknesses is its lack of an iMessage equivalent. That is, of course, until now. There's one app that will allow Android users to experience iMessage on their non-Apple phone, complete with end-to-end encryption, message effects, and group messaging.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Telemarketers can be as terrifying as a villain from a horror film. Your phone rings with an unknown 800 number, and you immediately fill with a sense of dread. There's no way to get them to stop calling; you imagine the number appearing on your phone at all hours of the day and night, haunting you.

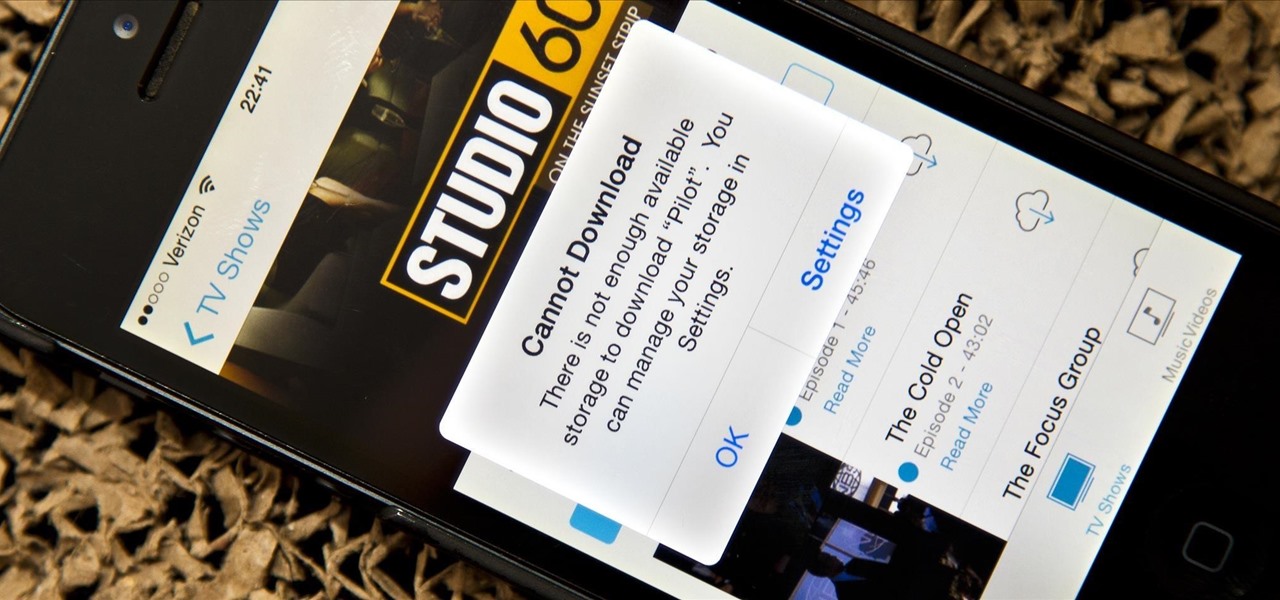
Running out of storage space on your iPhone is annoying, but trying to free some up is downright aggravating. Until they figure out a way to throw a terabyte of flash memory in there, you're going to have to do some spring cleaning every now and then, especially if you're trying to update to iOS 8.

There's a lot of cool features rumored to be included in next year's HTC One 2 (M8), the follow up to the flagship HTC One smartphone, including a fingerprint scanner, Android 4.4 KitKat, and Sense 6.0, but it's just too far away to get really excited about yet.

In this tutorial, we learn how to use Quick Connect Wireless with Epson Projectors. First, make sure you have one cable connected to the projector and one cable connected to the computer with a USB streamline. This makes it much easier and more efficient to plug in your projector. As soon as you plug this in, you will see a message appear on your notebook, then the screen will star to appear on the projector as it does on the notebook. It will take a few seconds, depending on the monitor and ...

There may be a time when you want to run a program for 24 hours straight. If that app happens to quit unexpectedly, you have some options to get it going again without having to manually reopen it. Check out this video on how to restart a crashed program automatically on Windows. You need WatchDOG.

Sputnik was the very first man-made object to be sent into space. Though it was a truly epic accomplishment, all this Soviet sky surfer actually did was transmit a constant beeping noise back to the surface.

By the time you watch all of the videos in this extensive language series, you’ll feel like you could jump right into a conversation in the heart of Reykjavík. Eva Natalja Robertsdattir begins with basic phrases such as “yes,” “no,” “good morning” then moves on to more advanced expressions such as “I’m afraid that I have to go now.”

Whether it's everybody or just a specific contact you can't hear during audio and video calls when wearing headphones, your iPhone has hidden, little-known tools to help you catch every word they say in the conversation. Even if you can normally hear everyone during calls, customizing these headphone preferences can make conversations crystal clear.

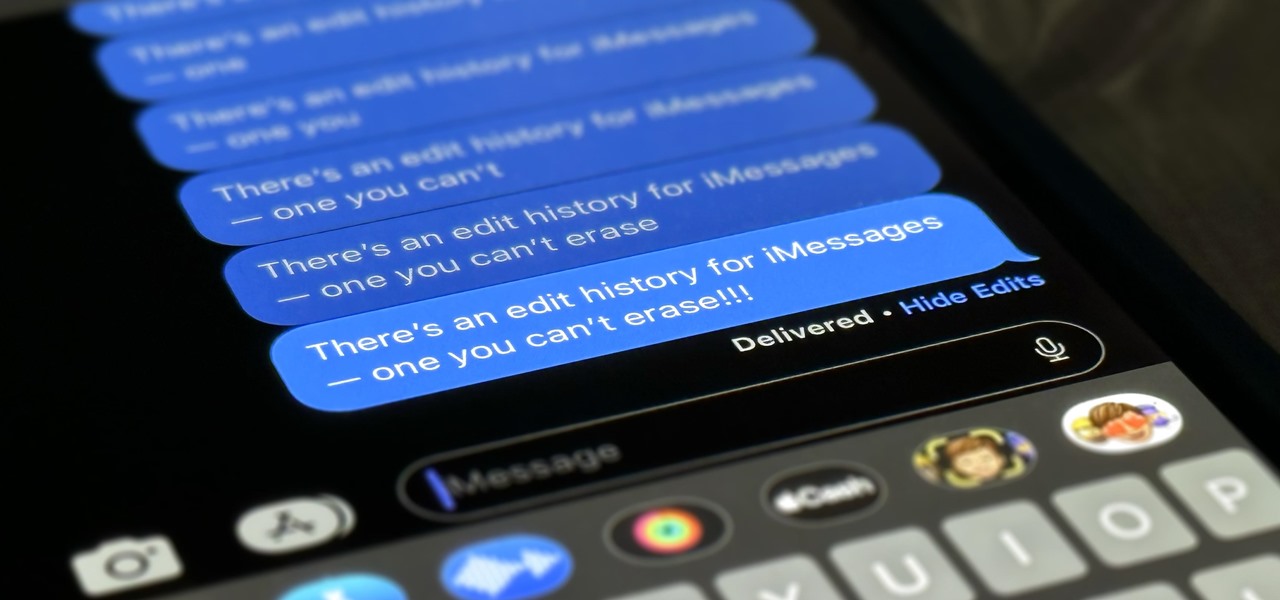
Apple lets you edit iMessages in the Messages app on iOS 16 and later, but everyone in the chat can see all the edits between the final and original text. Thankfully, there's an easy workaround to stop that from happening when you only want them to see the last message and nothing else.

If you've recently built a Wi-Fi spy camera out of an ESP32-CAM, you can use it for a variety of things. A baby monitor at night, a security camera for catching package thieves, a hidden video streamer to catch someone going somewhere they shouldn't be — you could use it for pretty much anything. Best of all, this inexpensive camera module can perform facial detection and facial recognition!

The NFT space is moving so fast that if you're not already engaged, you've probably already missed several history-making events.

Apple released iOS 13.4 to public beta testers on March 18. The update comes the same day we learned that iOS 13.4 would be made available March 24. The sixth beta is iOS 13.4's GM (golden master), even though Apple refers to it as "beta 6."

Apple released iOS 13.4 to registered developers on March 18. The update comes just hours after news broke that iOS 13.4 would hit all compatible devices on March 24. The update is the GM (golden master), which makes it the same build as the official release we expect to see on March 24, although Apple does refer to it as "beta 6" on the dev site.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

You're a busy, on-the-go professional, so you deserve an email client that keeps up with you. "Mail" on iPhone wasn't always the best option, but thanks to iOS 13, it feels like a completely different app. That said, there are plenty of alternatives that offer a different experience. Better yet, these apps are free. You won't need to spend a dime to try them out for yourself.

Apple has packed a lot of new features into the iOS 13 update, and practically no core app has gone untouched. The Messages app, in particular, got plenty of love, including new ways to dress and use your Memojis.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

Whether gabbing via cloud chat or Secret Chat, there's no denying that private messaging is one of Telegram's strengths. Communications can often occur at night, where Telegram's default bright white theme can be a bit uncomfortable to use, but Telegram supports dark mode on Android and iOS — with a few different themes to match any late-night chatting style.

I'm here at the annual AWE event in Santa Clara, California, and the venue is just as packed, if not more so, than last year.

When you can't think of a way to respond in Messenger with words, emojis and stickers will do the trick. Since Facebook is all about the "likes," which use a thumbs-up icon, there's a shortcut to the symbol just to the right of the chat field. It's always there to send a quick like in response to something. But it doesn't have to be the standard Facebook thumbs-up sign — it can be any emoji you want.

With Magic Leap One approaching six months since launch, Magic Leap is fully focused on building a content ecosystem and developer community.

In 2017, Google introduced a new feature called Fast Pair. This made discovering and pairing Bluetooth devices completely stress-free, as it eliminated the need to fumble through settings. Google has now made it even easier, so Fast Pair is a must-have feature for your next headphones.

Depending on your region, you may not be offered the same call recording option other OnePlus users have. But, as with most things Android, where there's a developer with a will, there's a way regardless. And the method we are about to describe is one of the easiest, most stable, and undetectable ways to do it. Perhaps we should discuss why OnePlus has been holding out you when it comes to this feature, though.

Stickers are a staple in most messaging apps. Facebook Messenger and Apple Messages, among others, are all compatible with still or animated stickers to personalize your chats. Now, WhatsApp is stepping into the sticker arena with a new update, bringing the popular feature to one of the most used chat apps in the world.

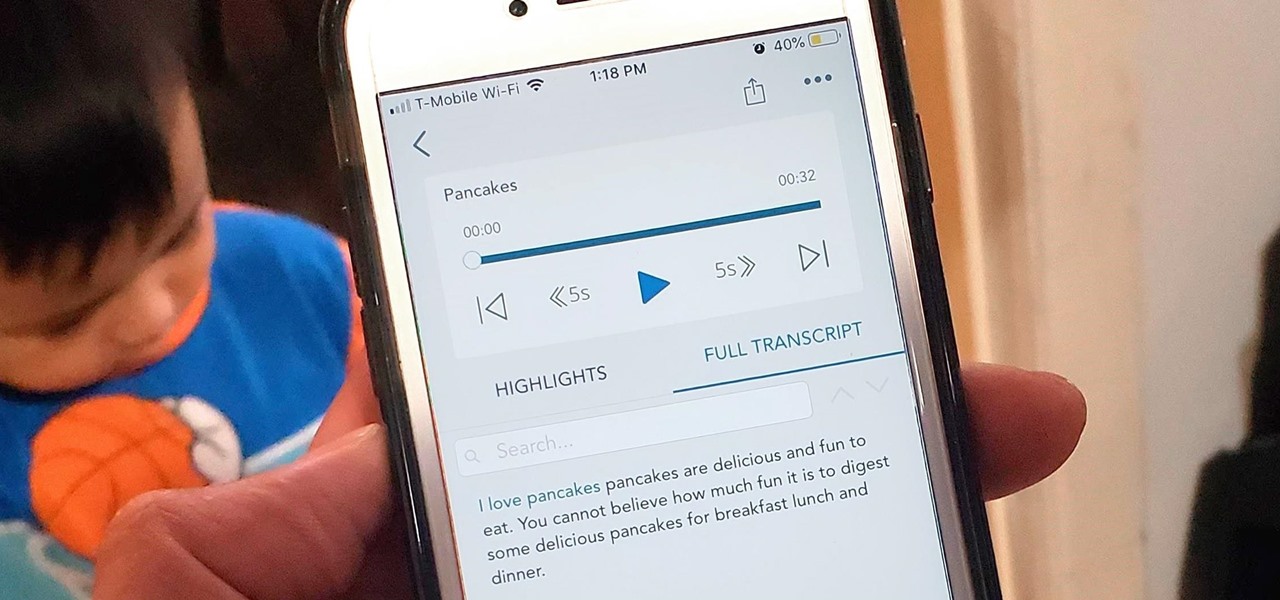
Despite its fifth-place finish in our ranking of the best transcriber apps on iOS, Voicera is still worth highlighting due to numerous factors that set it apart from the crowd. Besides being completely free to use on both iPhone and Android, the app's AI-based transcription service performed extremely well in our testing.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

In iOS 12, Apple included new, Snapchat-like effects and stickers for photos and videos in Messages. While these new options are fun, they're missing something that takes away from the appeal, especially since Snapchat, Instagram, Facebook, and similar apps already let you do it.

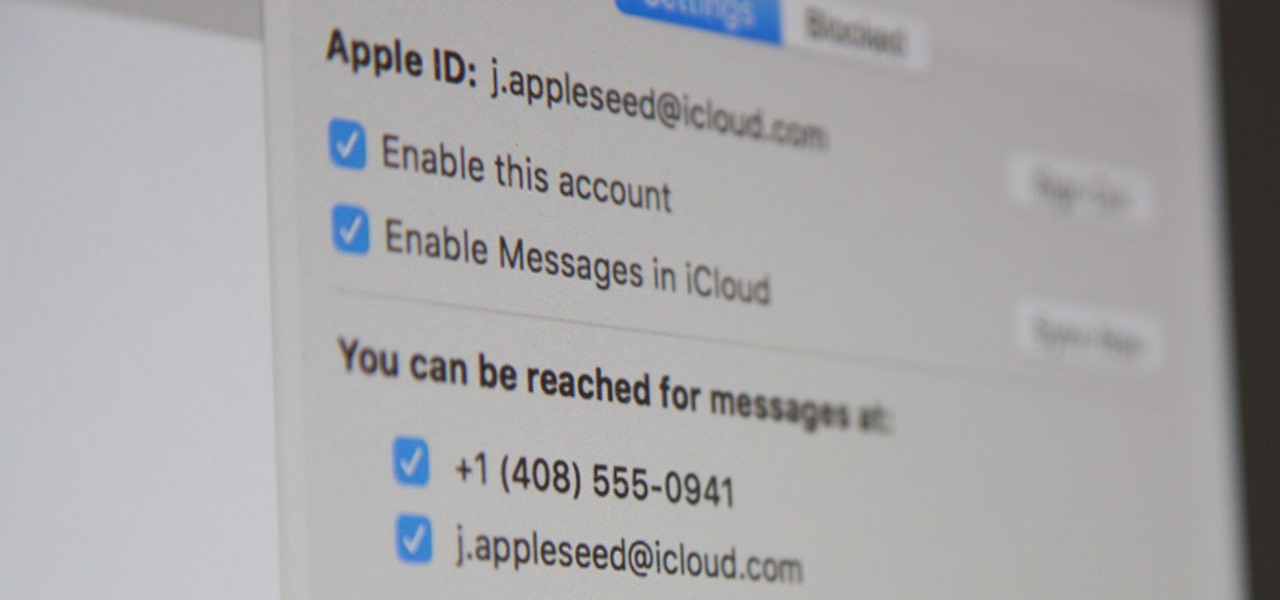
Apple pushed out iOS 11.4 on May 29 to iPads and iPhones, which included the long-awaited Messages in iCloud feature. The company did not release macOS High Sierra 10.13.5 at the same time, limiting the usefulness of being able to sync messages in the cloud since 10.13.4 is not compatible with Messages in iCloud. But three days later, Apple finally released macOS 10.13.5.

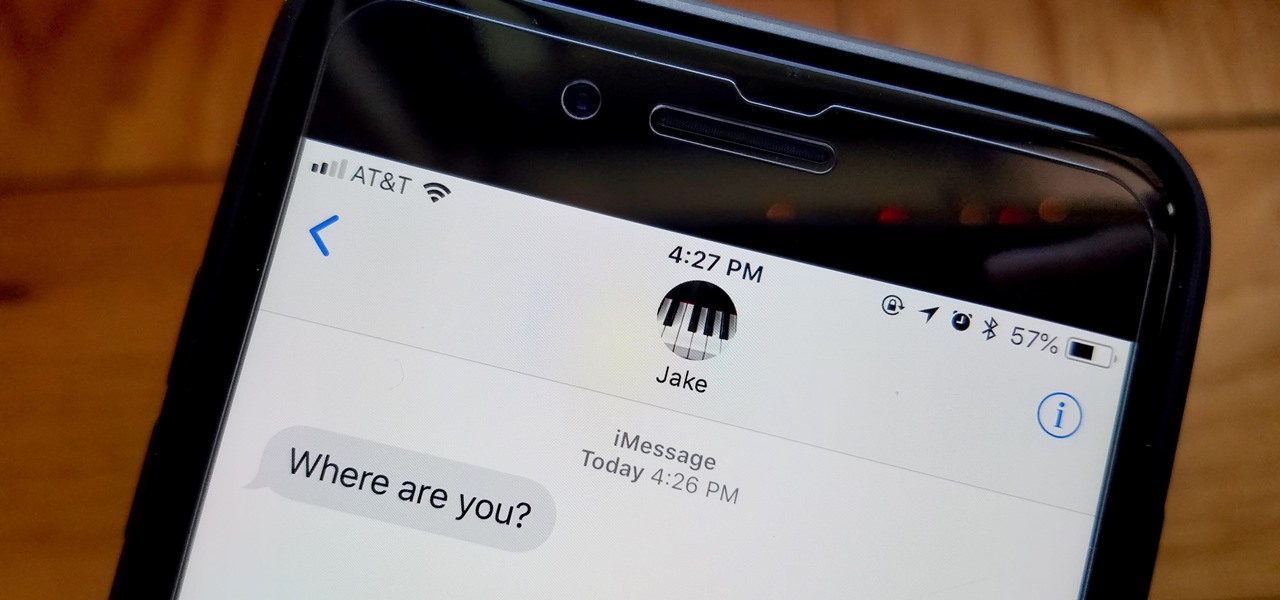
You're at the bar, but your friend can't find you. You could call them, but that wouldn't feel very 2018. Instead, let your iPhone do the talking. Right in the Messages app, you can easily send your friend your current location — all without interrupting the friends you're hanging out with.

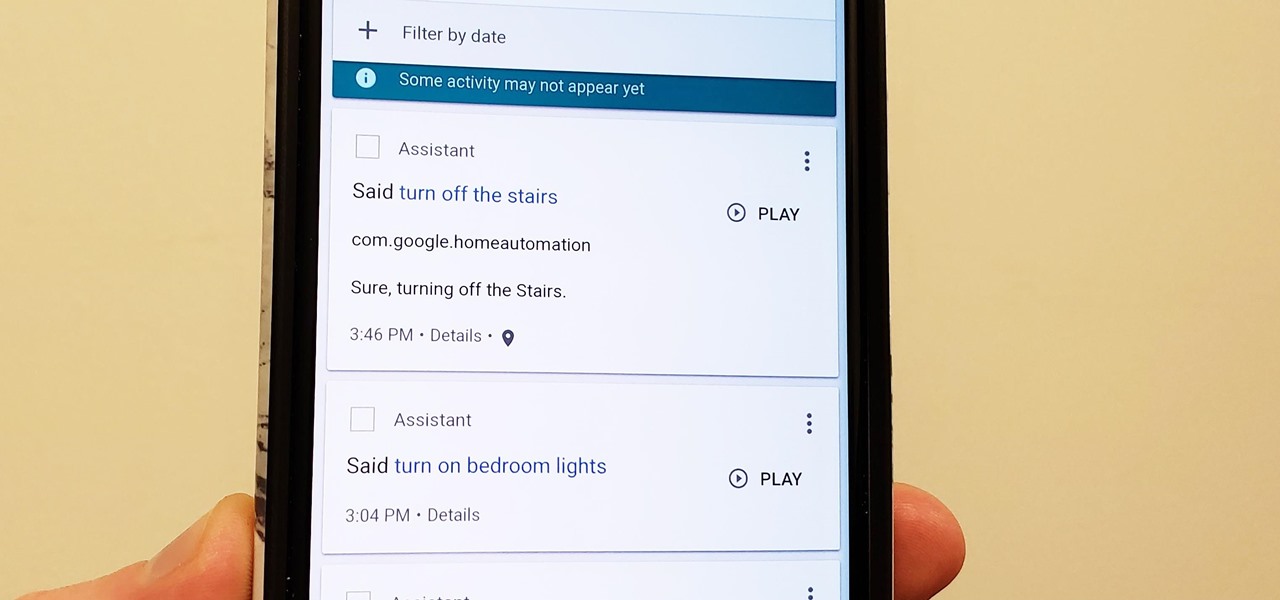
Privacy is a hot topic. In the wake of Facebook's data scandal, many want to safeguard their personal info. On the other hand, we all gain a certain amount of convenience by using services administered by huge companies like Google, Facebook, and Twitter. Google Assistant collects plenty of data, but you can easily check what is stored and delete items at will.