On the internet, everything is possible, even if it's not grounded in reality (check no further than anything The Onion publishes). Witty headlines combined with clever photo edits make even the most absurd topic seem like a serious news story. Some of these stories are so convincing that they even fool news organizations, such as the New York Times and even the official newspaper of the Chinese Communist Party. While some of us can tell when something sounds a bit off, others (like our paren...

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"
As a hacker or an aspiring one, You need to be careful and anonymous if your doing anything illegal. But you slipped up. Now someone is tracking you! Well luckily you read this post ahead of time and have a backup plan!

Are you a follower or a leader? No matter how you respond, we all know that leader is a more desirable position to hold. Great leaders typically share a few qualities—confidence, intelligence, and strength, to name a few—but one of the most intriguing is their appearance. With the right facial structure, and some well-rehearsed expressions, you can trick others into thinking you're leader material.
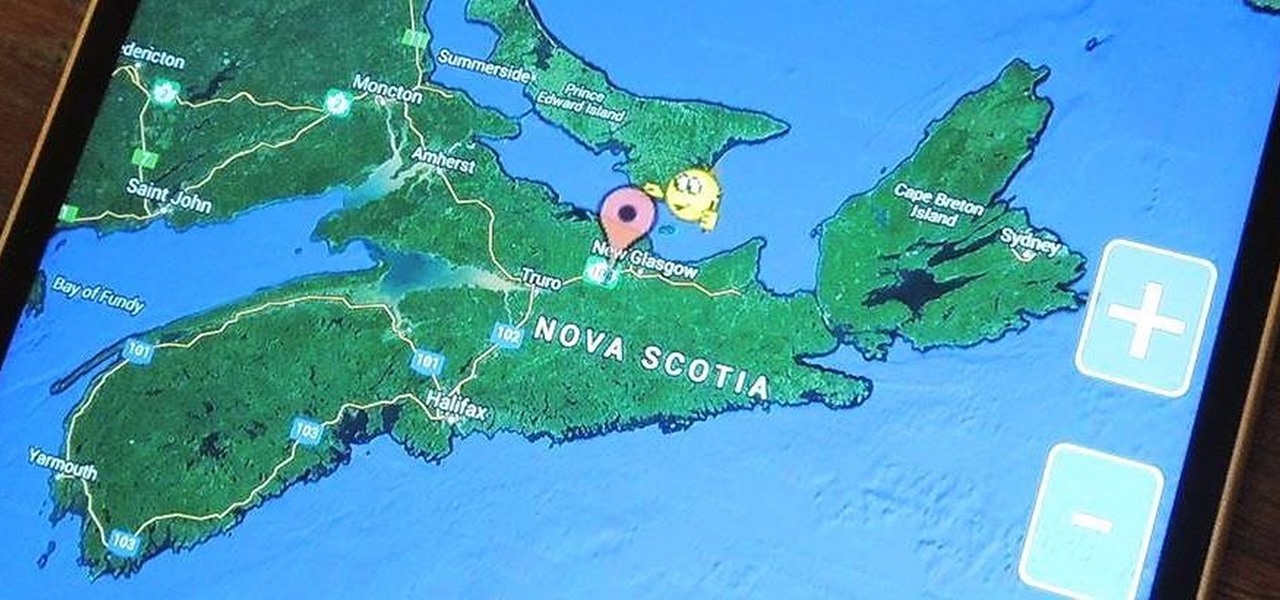
You wouldn't send your GPS coordinates to a completely random stranger just because he or she asked you for it, right? So why are you constantly sharing your location (and other data) to apps on a daily basis?

Admit it: when nothing's at stake other than your boss's disapproval, you don't exactly feel the urge to get working. Finding the motivation to take on a task, whether at work or home, can be a constant struggle. Though working through your laziness might seem like the best course of action, a meaner method can make more of an impact on your productivity.

The biggest hurdle faced when text messaging (besides more convincing lies) is accurately communicating our emotion and tone. Anything we say can be interpreted in various subjective ways by the recipient, and that's why we have emoji—to illustrate what we actually want to say.

There's more to earning someone's trust than simply shaking their hand, especially if you're not particularly trustworthy. Your body language doesn't reveal your thoughts, it reveals your intentions, and sometimes intentions are better left unrevealed. Psychopaths, take note...

The international hit Xperia Z2 may be headed to Verizon if a posted, and quickly erased, image is any indication. Take this information with a grain of salt—I certainly am—but this could be Sony's entrance into the non-GSM realm. The image above was posted to Sony's Xperia Google+ page, and very quickly removed. Compared to the Z2 that's currently on the international market (below), we can see that not only has the Sony logo shifted to the bottom, but a Verizon logo rests squarely along the...

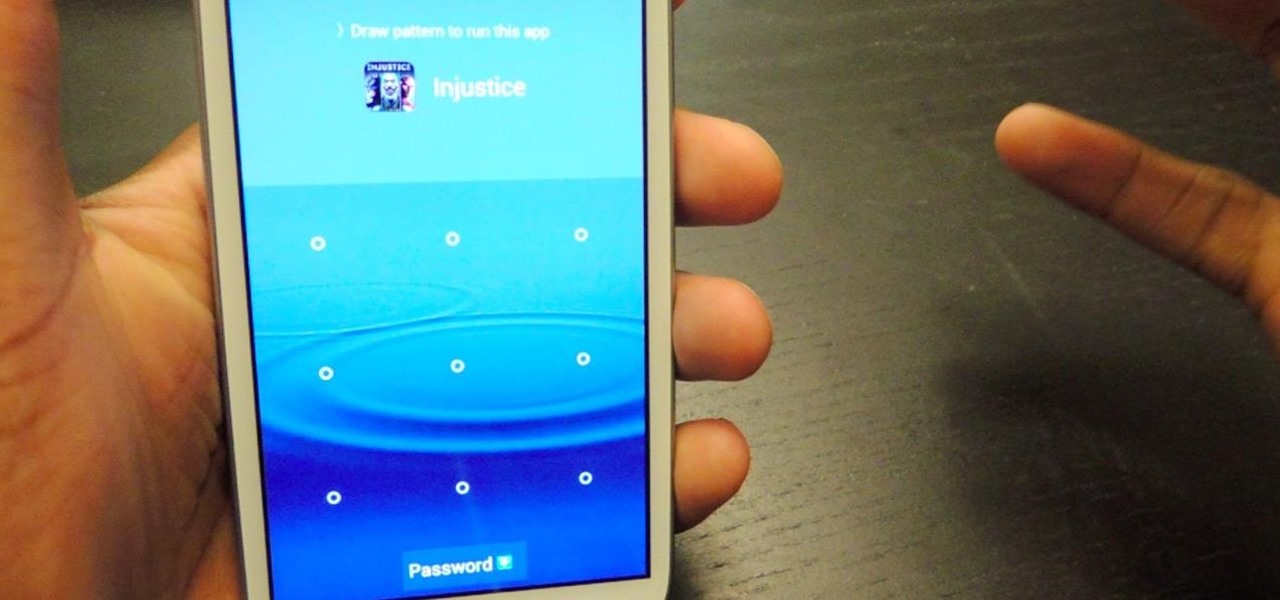
Keeping unwanted clowns off on my Samsung Galaxy S3 is priority number one. I've shown you how to snag a picture of people opening your apps and how to lock your screen for whenever you hand off your phone, allowing them to access only the page you left open.

Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

They say imitation is the sincerest form of flattery. You have a Google Nexus 7 tablet, but you really wanted an iPad. What do you do? Skin it to make it look like an iPad, of course! Today, I’ll show you how to transform your Nexus 7 into an iPad and trick your friends into thinking it runs iOS! Let’s begin.

The reasons for donating surpass much more than the direct and obvious benefits (ahem...taxes). Charitable donations are a direct reflection of your values and perspectives, not only improving your self worth, but can bring about unintended advantages.

With the new year right around the corner, it's time to talk about the end of the 19th century, a time which plays an enormous role in Steampunk. If you've done any reading of British books written from about 1890 to 1899, you may have come across the phrase 'fin de siecle' and wondered what it meant. You also may have come across this term in reading about the late Victorian era. No worries, I'll tell you all about it! Image by Giovanni Dicandia

What happens when a entrepeneur/theme park creator and special effects artist/magician team up? You get a team crazy enough to create the first true virtual reality theme park (sorry, Six Flags). They only have a single experience so far, but it's already taken a giant leap beyond the wonders we've seen in today's consumer virtual reality headsets.

While there's an art to surviving the all-nighter, there's also an art to staying awake throughout the day when you're operating on little to no sleep. In 1964, the record for sleep deprivation was set by 17-year-old Randy Gardner, who stayed awake for an incredible 264 hours and 12 minutes. Now while we're not out to challenge Randy for his title, we can certainly look to him for inspiration in beating back our own fatigue.

The results of Microsoft's $480 million contract with the US Army are on display and users continue to test the suped-up version of the HoloLens 2.

The wearables space experienced its "big bang" moment back in 2015 when Apple released its first wearable device, the Apple Watch. Although the device was initially dismissed by some as an unnecessary charm bracelet packed with frivolous tech, in very short order, the public learned just how useful the Apple Watch can be.

Magic Leap's legal battle against Nreal has taken an intriguing turn this week, as Magic Leap set a date to discuss the matter with Nreal. But a new partnership struck by Nreal adds another wrinkle to the duel between the two AR wearable makers.

While Apple's smartglasses development reportedly moves forward behind-the-scenes, the company continues to build on its AR software foundation in its mobile ecosystem with further iterations to its ARKit platform and the introduction of new AR development tools.

The hype around augmented reality has risen to a fever pitch over the past two years, and if this week's selection of business news stories are any indication, the din is about to get down right deafening.

Despite its status as a hot commodity amongst emerging technologies, the augmented reality industry is not immune to the ebbs and flows that occur in every industry.

The emerging narrative as CES begins is that consumer-grade smartglasses require a heavy compromise in functionality in order to arrive at a form factor and price point that appeal to mainstream customers.

Mixed reviews of Magic Leap One aside, it would be hard to deny that Magic Leap has had a big year. And the AR unicorn isn't coasting to the finish line, with a number of new apps dropping and prescription frames finally arriving to bring relief to those who wear eyeglasses.

Sony Pictures has tapped the powers of augmented reality as provided by startup 8th Wall & the Amazon Sumerian development platform to help it promote the latest motion picture manifestation of Spider-Man.

From day one, my favorite thing about the Magic Leap One has been its portability. It's so well designed that it just screams to be taken out for a walk through the city. Alas, Magic Leap says the device is (currently) designed to be used indoors, preferably in settings containing few windows or black surfaces.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

With the macOS stager created and the attacker's system hosting the Empire listener, the malicious AppleScript can be designed and disguised to appear as a legitimate PDF using a few Unicode and icon manipulation tricks.

The default Camera app got a few more tricks up its sleeves when iOS 11 was released, and the best addition by far was the inclusion of a built-in QR code reader since that meant no more third-party apps just for QR code scanning. However, Apple's built-in QR code scanner did have a vulnerability at one point that would let hackers direct you to a compromised website without you even noticing it.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

The Guardians of the Galaxy have to be the most fun superhero team to have at a Halloween party. They dance, they break the rules, and they definitely have the grooviest music. So the Guardians are a great bunch to pick from for your Halloween costume — or even for a themed group costume. Just imagine the badass vibe when you all walk into a venue together with Star-Lord blasting "Cherry Bomb" from a portable speaker. Here's a roundup of some of the best Guardians of the Galaxy costume guides...

We are in a pretty major technology boom at the moment. One that will likely make the industrial revolution look tiny. And one of these technologies that are building up to lead the way is something called augmented reality.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

The story of Helicobacter pylori is a real testament to the tenacity of medical researchers to prove their hypothesis. It took decades before the scientific world would accept that the bacteria H. pylori caused ulcers.

To some people, Thanksgiving is merely quality time with family and friends that they can't get throughout the rest of the year. To others, it's that one time when it's okay to be a greedy hog and get hammered all weekend long.

When most people say, "Damn, look at that rock," regarding an engagement ring, they're usually not referencing an actual rock—let alone a space rock.

If you're grossed out by anything creepy, crawly, and with more than 4 legs... then stop being so close-minded and eat some bugs already, dammit.

Mochi seems to be everywhere these days: as a topping at your local frozen yogurt shop, in ice cream balls (the green tea ones are heaven), and as colorful treats all over Instagram. It seems like mocha mania is in full force!

When given the choice between canned and dried beans, many of us are guilty of reaching for cans. They're much more convenient than investing 5-6 hours of your time to make dried beans edible.

A cup of ginger tea with lemon first thing in the morning, a pick-me-up cup of green tea (or matcha) to fight off the afternoon slump and a soothing cup of chamomile tea to help me unwind before bed—I would be lying if I said I weren't a major tea enthusiast.