There’s nothing more special than a beautiful pearl necklace. But how do you know if they are real? Knowing some qualities that pearls have should help you determine when there is an obvious fake in your presence. It might ultimately be necessary to leave it to a professional to authenticate those pretty little presents from the sea.

Being a male, I may be the only one among my gender stating this, but I'm sick of girls using Halloween as an excuse to dress scantily. Why can't more girls skip the playboy bunny costume and get this gnarly? Below, ten badass Halloween looks executed by girls only...

There's an epidemic on the Internet, and the disease—Facebook. It's an addiction comparable to a hot cup of coffee in the morning or a soothing cigarette throughout the day—in worse case scenarios, a hit from the crack pipe. If you're on Facebook, you know what I'm talking about. You're addicted to finding out what's going on with your friends and addicted to telling those friends everything you're doing. You can't stop, even when you're at work.

Deep fakes, the art of leveraging artificial intelligence to insert the likeness and/or voice of people into videos they don't otherwise appear in, typically focus on celebrity parodies or political subterfuge.

Over half of all Americans have listened to at least one podcast, and that number is growing every year. With over one million podcasts and 30 million episodes in existence, there's no end to discovering new voices expounding on a range of topics.

If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed.

It's been proven that hackers can manipulate your screen with fake taps through specific exploits, so they can potentially hit the "Grant" button when you get a superuser request. This is the last thing you'd want to happen since the malicious app from that point forward has full system privileges. Luckily, using a fingerprint to lock your superuser requests can prevent this.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

As the stigma of online dating fades and swiping potential suitors on your phone becomes the new norm, one very real issue that you may have to deal with is catfishing: the act of being deceived by a fictional online persona. Although dating apps do their best to weed out fake accounts, a few of them slip through the cracks and take advantage of innocent people just looking for a connection.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

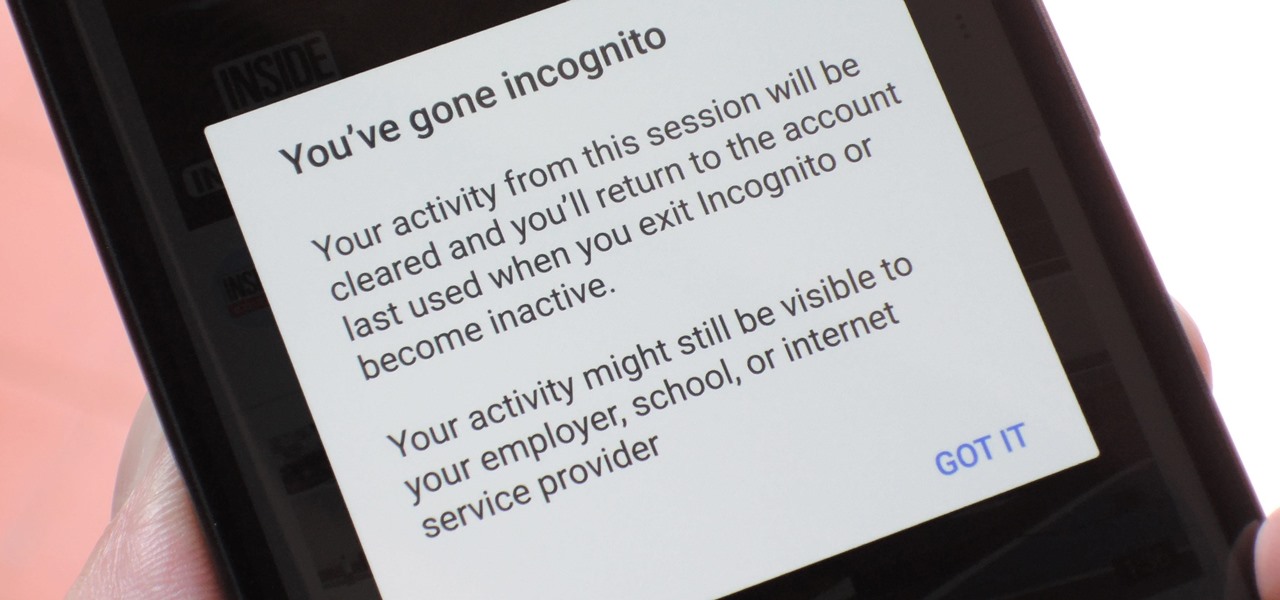
Incognito Mode is a privacy feature that was popularized by Google Chrome, and it recently made its way to GBoard. Now it's coming to the YouTube app to help make your video watching experience truly private.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

On Wednesday, Snap, Inc. unveiled a revamp of its Snapchat app that draws a hard line between content from your friends and content from professional media organizations.

Wonder Woman is going to be everywhere this Halloween, and you know it. One way for your rendition of Diana to stand out among an (Aegean) sea of Wonder copycats is to shy away from the classic high-glamour makeup style that Gal Gadot wears in the recent movie. You can still put on your tiara and carry your golden lasso all the same — you just need to go with a unique comic-book style makeup. With the help of licensed esthetician and self taught makeup artist Lex, instead of looking like you ...

If you live in New York City and are itching to sell your Yeezys, you're at risk of falling victim to thieves. A devious duo is searching Facebook to find people selling the popular sneakers and then robbing them at gunpoint when they meet up in person.

The laws and regulations in place in the US for driverless vehicles are a mess, but Republican congressional members say they can fix it.

Can't wait till Apple's ARKit is released? Me neither. Luckily, a fun new app launched today that is close to what the ARKit promises to deliver in a few months.

Combine the word "fake" with the word "Instagram" and you get what's called a "Finsta." If you are concerned about posting pictures on social media that you wouldn't want your family or boss to see, then a finsta account might be the thing that you need.

UPDATE 5/12: According to Bloomberg, it looks like the merger is on. Anonymous sources claim discussions have already begun about consolidation. Looks like there might be a new 5G powerhouse after all.

Everyone feels a little safer with Android's security updates, which are welcome and often necessary protective measures. But what happens when the update that's supposed to safeguard your phone actually ends up wreaking havoc with its security system?

We've been hearing rumors for months now that suggest Apple will be getting rid of the 3.5 mm headphone jack in the iPhone 7, which will presumably be replaced by an adapter that connects your earbuds directly to the Lightning port. But finally, thanks to Vietnamese site Tinhte, we now have some hard evidence to back up this claim.

It's a given that if you're driving, you or someone you know has Waze as a go-to on their smartphone. The Google-owned crowdsourced navigation app is one of the best for avoiding traffic, roadblocks, and even cops.

For generations, parents have been struggling to come up with innovative ways to get their kids to eat their vegetables. They'll cut them into fun shapes, bake them in cheese, batter, and deep-fry them.

In this video I'm going to teach you 5 pranks you can get away with at school or at home On April 1st.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

The Xposed Framework was just recently made available for Android Marshmallow, but everything isn't quite back to status quo just yet. Sure, some Xposed modules function properly, but others are a bit buggy, and several don't even work at all. This is mostly a result of changes to the Android system that Lollipop modules relied upon, and such modules will need to be updated for Marshmallow compatibility.

Hello again, ***UPDATE: Adding links to the other Two articles****

The Cheshire Cat isn't like other famous cartoon cats: he's brilliantly purple and hot pink, ever smiling and entirely unnatural. However, he makes for a perfect Halloween costume, with his bright, neon appearance and mysterious nature.

With the explosive popularity of both Thor himself and The Avengers, Thor is an obvious good choice for a Halloween costume. But you don't have to opt for one of the pricey, pre-made costume choices found in every Halloween store in every city. Instead, craft your own in just a few steps, saving yourself money in the process.

There are a number of ways to give your productivity a kicktstart, from taking a break from your distracting smartphone to just taking a break, plain and simple. Yet finding the motivation to start working doesn't require any effort at all—just a little bit of green.

Show your significant other just how much you love them by surprising him or her with one of life's most precious, romantic gifts—bacon! Best thing is, this passionate treat works for any day of the year (Valentine's Day, a first date, anniversary, etc.), since love and bacon go hand in hand.

With Mobile World Congress right around the corner, we're all left to patiently await the unveiling of two Android flagship smartphones—HTC's One M9 and Samsung's Galaxy S6.

Casting Angelina Jolie as Maleficent was a no-brainer on Disney's part. No one else could project beauty, elegance, and fear simultaneously just like the animated villain in Sleeping Beauty did. But what sets the character apart from other evil witches, or any other Disney character for that matter, is the sinister, yet gorgeous-looking horns and headdress. And with news that a Maleficent sequel is currently in the works, this will surely be a great Halloween costume this year.

With over 2 million uploaded videos and over 28 million people who had talked about it online by the end of August, the ALS Ice Bucket Challenge was the most viral social media event of 2014. Its popularity provided the ALS Association with $115 million in donations to date, with everyone from students to veterans to celebrities contributing.

It takes a lot of time, effort, and cash to create a unique Halloween costume that will likely never see the light of day after the 31st. Not to worry: you can do it on the cheap and feel savvy and creative while everybody compliments your ingenuity.

As I begin my move across the country, I find myself dodging all kinds of Craigslist scams, particularly in the apartments and housing classifieds. Fortunately, I've discovered a little trick that will tip me off to a scam before I lose $1,000 in a fake security deposit.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

Snapchat was created for the sole purpose of removing evidence from your mobile that a photo or video ever existed. That way, snoopers can't find any of these questionable selfies in your photo gallery. Of course, there are plenty of ways around this safeguard, but it's still more private than the standard social networking app.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

Voodoo you want the best costume this year? You're probably laughing so hard right now that you need to hold yourself together with pins and needles, right?