JavaScript is the language of the internet. It is what allows us to create dynamic, interesting webpages that are fast, web-based applications and so much more. The primary use of JavaScript is to write functions that are embedded in or included from HTML pages and that interact with the Document Object Model (DOM) of the page. This is the magic that allows all of what we see to happen, and for our browser to be manipulated.

Permanently deleting files is something that a lot of people aren't aware of. Actually, most people think that once a file is deleted, it is gone forever. This is not the case. Hard drives write to the disk via magnetic charges, positive and negative correlate to 1s and 0s for binary. This is then interpreted into information for the computer to use and access.

Behavioral ad targeting companies are diving deeper into the realms of your subconscious with a new approach to serving adverts to you online—and they're using your television.
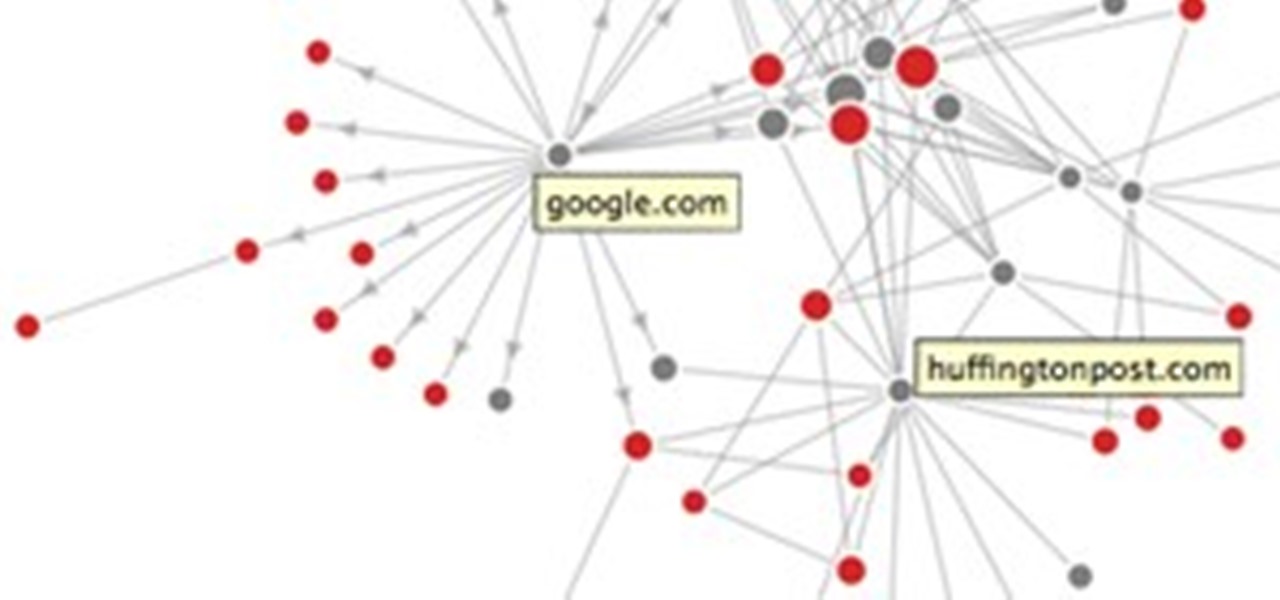
The whole world is connected to the Internet, which means bank for advertising companies who track your every move online. Most of the content you see on the web is free, and that's because of advertisements. If there were no ads, none of us would be addicted to the Internet because none of us would be able to afford it.

I am the sort of man whom game companies fall all over themselves to seduce. I'm sweaty, pale, awkward, and spend too much money on video games. There are many of us, especially among XBox 360 owners. We are the most stereotypically "gamer" group of console owners. The XBox 360 doesn't have motion control like the Wii or a blu-ray player like the Playstation 3. It just plays games really well. That's why hardcore gamers like me prefer it amongst all the consoles, and probably why Silver Dolla...

If you take to reading food labels you will start to notice some ingredients come up again and again. Sugar, MSG, high fructose corn syrup, spices that really don't mean "spices", things you can't pronounce. If you can't have it, chances are it's in that package you're holding.

Lifehacker posts an article on the art of cracking weak passwords, courtesy of Internet standards expert, CEO of web company iFusion Labs, and blogger John Pozadzides. Pozadzides certainly knows a thing or two about password logic. (Note: this information is not intended to hack into accounts, but rather to protect you from using weak passwords).

Cross-Site Request Forgery (CSRF, pronounce "sea-surf") is a common web exploit. However, for unknown reasons it's not used very often. It plays on a given website's trust in a web browser by executing another website's form action, for example, sending money to another person. It's usually placed in abnormal places like HTML image tags.

Welcome to the second Null Byte in a series educating you on Social Engineering awareness and techniques. Today, I'm going to show you how a saavy Social Engineer would trick a friend into unknowingly surrendering their Facebook password. My intent is to warn and demonstrate how easy it is to succumb to phishing via Social Engineering, and therefore expose yourself.

Private browsing is all the rage with browsers these days. Once you go into private browsing mode, you can traverse the internet without leaving a trail. Your history? Deleted. Your cookies? Destroyed. Your bookmarks and non-private history? Preserved for when you come back to the surface.

Thanks Anonymous User For This Article, Not Bad Ok SoftzZz...!.!.!.: Step 1 Antivirus

WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

It's Monday, which means once again, it's time to highlight some of the recent community submissions posted to the Math Craft corkboard. In this post, we'll also make a flexagon, which is a type of transformable object.

So your mom may have told you not to spoil your appetite with that chocolate chip cookie you were eating before dinner, but did you ever think about what that energy drink your sipping on looks like in terms of its sugar content? The article "20 Worst Drinks in America" takes a look at what is hiding in that sinfully sweet soda. You may not ever dream of eating 6 Krispy Creme glazed donuts in one sitting but thats how much sugar you are putting in your body when you have a 16 oz Rockstar Ener...

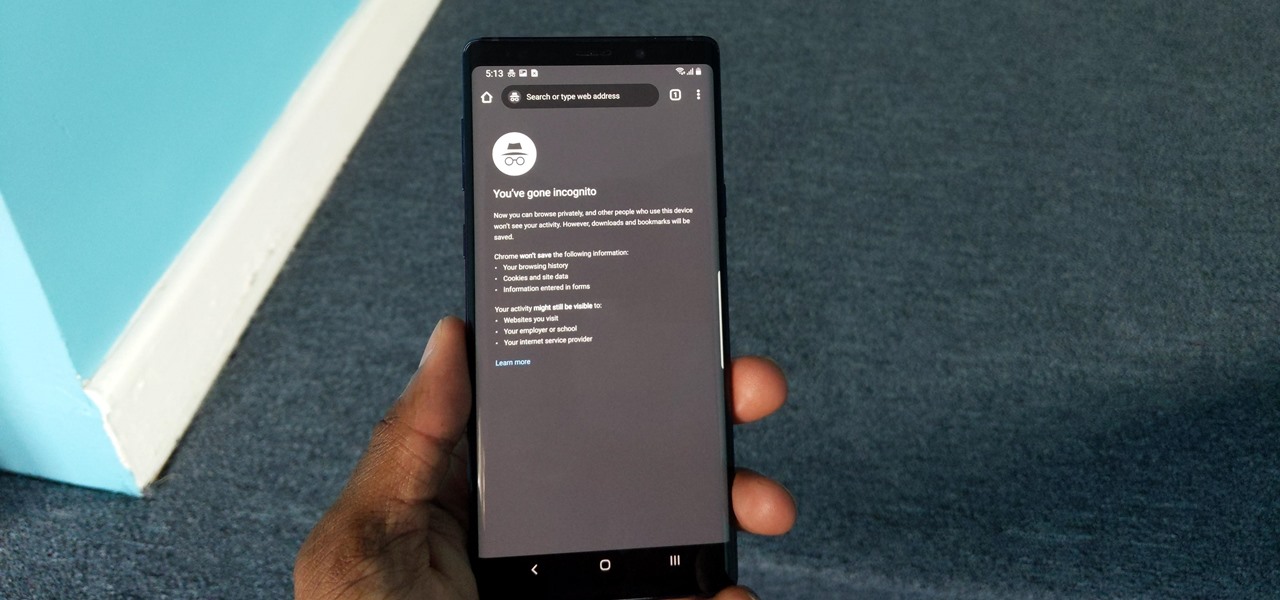
Chrome's Incognito Mode gives you a layer of privacy when browsing. While it's enabled, your browsing history, cookies, site data, and information entered in forms is not saved, making it perfect for, cough, more private web usage. With an Android smartphone, you can jump right into this mode.

Even if you don't ever plan on baking cupcakes or muffins for the rest of your life, you should still invest in a set of silicone muffin cups for your home and cooking needs. They're not just for baking!

Have you been caught eating the cookies that were left for Santa? That's easy to explain, but what do you do when the doubt begins to rise in your child, rendering them dubious about the authenticity of everyone's favorite childhood lie?

Which cooking oil is best for baking cookies? Sautéing vegetables? Deep-frying chicken? With the plethora of different cooking oils out there, it can get pretty confusing choosing the best one for your next cooking adventure.

So it is Christmas Eve and you are just getting started on your Christmas gift shopping. Thankfully, even for the last-minute Christmas gift shopper, you have a good variety of options to choose from within driving distance or on the internet without worrying about shipping costs or waiting in ridiculously long lines at the mall.

Dopamine is a neurotransmitter that motivates us to engage in rewarding activities such as eating and sex. Animals without dopamine stop eating and starve to death.

An experiment was run by Walter Mischel with four-year-olds back in the 1960s. Each child was brought into a room in which there was an Oreo cookie. The child was told that s/he could have the Oreo right then and there—or if s/he waited 15 minutes, could have two Oreos instead.

People sometimes ask me about the IT industry here in the states. These folks are usually either trying to get into a certain field, or looking to switch or move into another one. Right now, you may currently be a Computer Science major that will be graduating shortly and are interested in the current state of IT security.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Spam is everywhere and Facebook is no exception. In fact, spammers are constantly stepping up their game by tricking unsuspecting Facebook users to participate in quizzes, games, apps, or "new features" that are actually dangerous computer viruses, spyware, or other trojan horses in disguise. Their attempts even trick people into unknowingly becoming spammers themselves.

Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called caching. For example, when a site is down, you can view its cached page on Google.

In a nutshell...go donate blood at a one of those buses that just drives around and parks at shopping malls etc...act confused about the ENTIRE process. I mean, like you have NO idea whats about to happen. All's you know is that you're gonna get some free cookies at the end....when they hook you up and your blood begins flowing into the bag for a while, pull out a real blood bag and tube, except its full of some type of fake edible blood. Put the tube connected to your fake blood bag in your ...

The Motivation So, I want the Jackass guys to antique my mom. Plain and simple, she bakes terrible cakes. They're horrible. And the only solution I have dreamed up is to destroy her flour supply.

Chef David Ogonowski demonstrates how to make triple chocolate treat. A chocolate tart with rich truffle filling, espresso parfait, and cocoa cookies. Make triple chocolate treat.

Follow this fun technique for creating Pac-Man cupcakes with two different colors of frosting. You can do this on cookies and cakes, too. Kids can line the muffin tins, mix the ingredients, spoon the batter into the muffin cups and of course, supervise the icing. Make Pac-Man shaped cupcakes.

First Prank: Title: Bull-ish Thugs

invite someone to a new nice home show them round but first give them chocolate (laxetive) or some sort of greeting of cookies or insist them to use the batroom or check it out if they dont accept, They go and do their buisness or if they were just washing their hands checking the sink while then the host leaves and locks the door and they cant get out and say hold on i might have to fix the door. but he floor in the bathroom is not connected to the house and the walls fall down exposing the,...

make some browines or cookies whatever you want and some ex lax pick someone up and offer them a cookie and drive aroud tell the have to go

First things first, this has to be a hidden prank on the cast of the show, so dont let em see this,