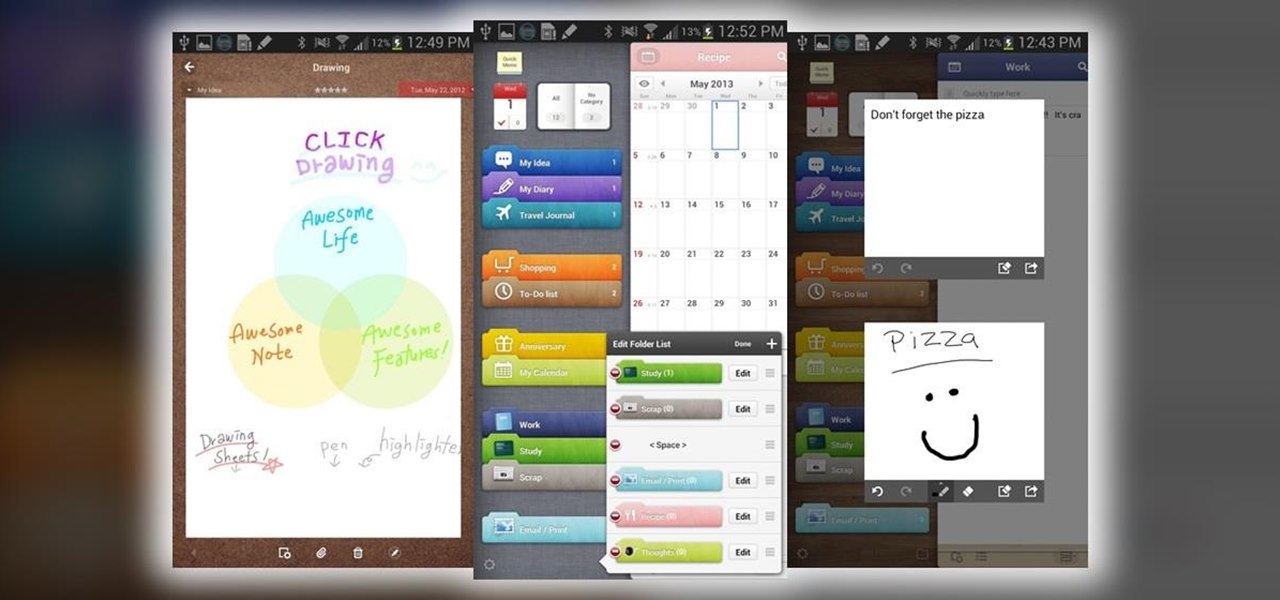
Update, November 12, 2014: Android 5.0 Lollipop is officially out now. If you haven't gotten the OTA yet, check out our new guide on installing the official Lollipop builds on any Nexus for download links and instructions, for Mac or Windows.

Admit it, you wish Siri was on your Mac, and so do I. She stole my heart on iOS, and now every time I open up my MacBook, I feel something missing. Wouldn't it be great if we could, I dunno, hack Siri onto our Macs? Yeah, it would!
The desktop layout in Mac OS X Yosemite is undeniably beautiful—it's sleek, simple, and easy to admire. Thing is, I do too much on my Mac to install a developer preview as my main OS (even though I can make a bootable install drive and dual-boot it), but I do want the aesthetics of the new build.

Welcome back, my greenhorn hackers!

If you've seen ParaNorman or Fantastic Mr. Fox, then you have some kind of idea of what stop-motion animation is. Basically, these artists make objects, or small figures, appear to be moving on their own by manipulating and repositioning them in the smallest increments, then capturing each frame after doing so. When all the frames are compiled together, the final product is something spectacular like The Nightmare Before Christmas, which took roughly 109,440 frames in all.

The original Kit Kat was a mutton pie served at a political club in London during the 18th century, which is quite different than the chocolatey version we're familiar with today. Kit Kat bars have been around since 1911, are produced in 13 countries, and have been sold in over 200 flavors in Japan.

If I were a math major, I'd probably be rolling in dough somewhere in Silicon Valley right now, but since multiplying numbers and figuring out tangents gives me panic attacks, I went the English route... pays much better.

If you thought humans were reading your résumé, think again. Robots do, and their one solitary objective is to systematically crush the hopes and dreams of those who don't make the cut. Instead of paying a few humans to read thousands of résumés over a couple weeks, many companies use computer programs that can do the job in less than an hour. In fact, at least 90 percent of Fortune 500 companies use what they call an applicant-tracking system, aka rejection machines.

According to WitsView, 8-inch displays will rule the tablet scene this year at 11.9% market share, compared to yesteryear's 2.6% market share. By year's end, it'll be almost 18%.

Since the introduction of the Nexus 4 to the Google Play Store last November, the phone's been in constant demand thanks to the low price and sleek design. Even today, the phone is still listed as sold out. LG's Nexus 4 is also the only smartphone in circulation that can run a naked version of the Android operating system; one that does not come loaded with a manufacturer UI running over top of it.

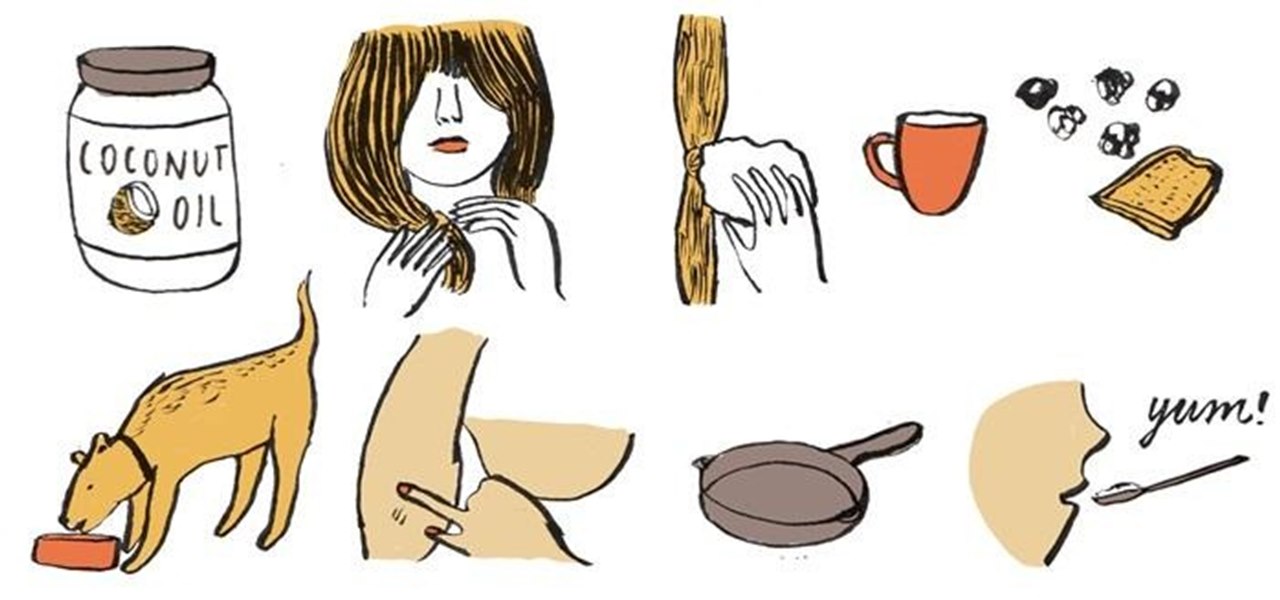
What can't coconut oil do? This edible oil, extracted from the copra or meat of a coconut, has done what most other food, beauty, and health trends have not: demonstrated real lasting power. Indeed, the "superfood" continues to make headlines, with its many uses the subject of debate, study, and fervent support. From the obvious (cooking) to the less so (home improvement), there are likely many coconut oil uses you're not yet aware of.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

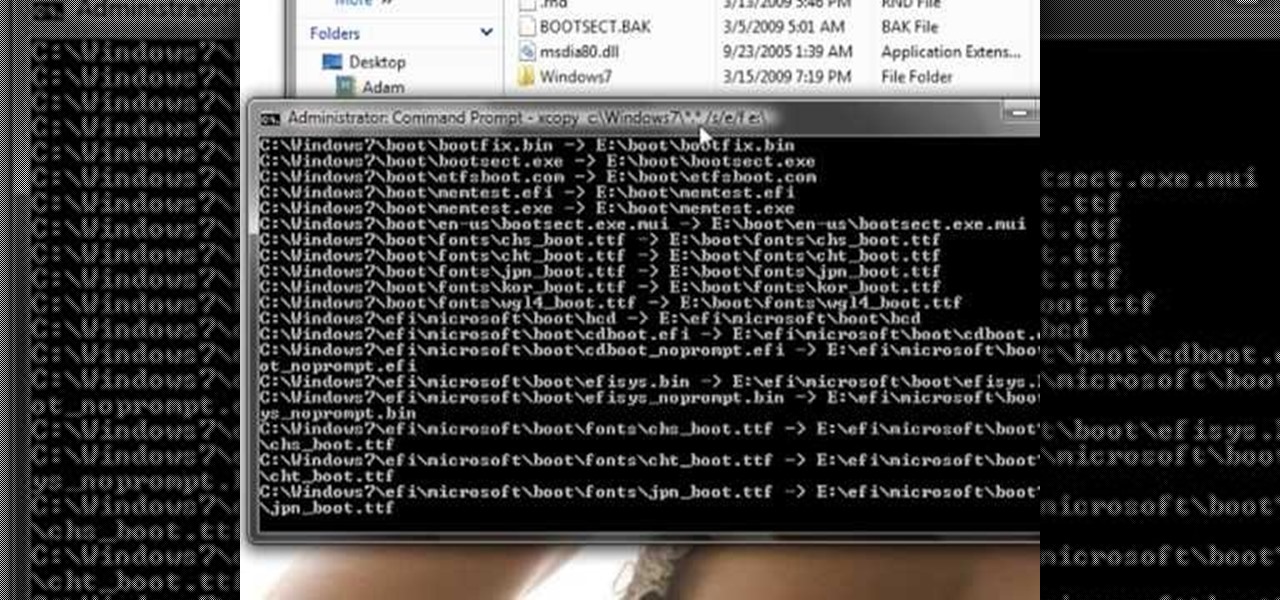
There are loads of reasons for somebody to want to recover a Windows password, and there are lots of different ways of doing it. My favorite of all of these ways is to use a piece of software called Ophcrack because:

In this video tutorial, viewers learn how to easily preview content by improving Quick Look on a Mac OS X computer. Quick Look allows users to preview files without having to open it. This video reveals a plug-in that enhances the abilities of Quick Look. Download the plug-in and extract the files into the Library/Quick Look folder. Then right-click on Finder and select Relaunch. Now users will be able to see all the contents of a folder just by pressing the space bar. This video will benefit...

Kongregate is a site that allows users to upload games. Users must go to the site to download the hack. On the site, select Kongregate. Then select the first topic and click on KBH 2.0.14. Once downloaded, you can extract the files onto your desktop. Open up the file and follow the video on how to use it. It also comes with the auto rater. This video will benefit those viewers who play games on the Kongrgate website and would like to earn badges.

Taco Bell's in the news for umpteenth time, and today the controversy is over their infamous beef taco meat. Gizmodo leaked a picture of Taco Bell's "Taco Meat Filling" and surprise, surprise— it's missing a lot of the "meat" that it claims in its advertisements. Taco Meat Filling Ingredients

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

One of Android's most glaring weaknesses is its lack of an iMessage equivalent. That is, of course, until now. There's one app that will allow Android users to experience iMessage on their non-Apple phone, complete with end-to-end encryption, message effects, and group messaging.

Fight me all you want, but it ain't a party without alcohol—whether it's a Halloween party, Christmas party, dinner party, or even a damn wedding. (If you think that people will stick around after dinner for a dry wedding, then you're sorely mistaken.)

When you clean the carpet in your home or apartment, it seems like that dirt just comes right back the next day. It's never really clean. Well, that could be changed with a deeper clean. Deep-cleaning your carpet can offer benefits including getting rid of dust mites and allergens. Not to mention dirt.

Dying leather is a great option to revamp or change the look of an existing leather piece. Choose a dye that provides the qualities you are looking for, be it flexibility or depth of color. The possibilities are endless.

This guide works 100% for Vista & Windows 7, unlike most of the guides out there. The method is very simple and hassle free. Needless to say, your motherboard should support USB Boot feature to make use of the bootable USB drive.

This video will walk you through the process of updating a psp to the 5.50gen-a. This is information you may want if you are an avid psp user and would like to hide your Mac address. This video is a little hard to see but he will talk you through the main points.

If you’ve got a minor cut or nasty sunburn you may reach for the aloe vera for the soothing and healing qualities. You don’t have to buy aloe, it is easy to extract the aloe from the inside of the leaf of a living aloe vera plant.

Add a perfect theme dessert to your next Hawaiian luau with this decadent coconut cream pie. After a long week at work there’s nothing better than a little back yard barbecue fun with friends topped off with the perfect treat.

Jennifer Cail begins by showing you the pots and pans you will need, then demonstrates how to season and baste your main course. She also includes tips for extracting fat from the goose and making the roux that will perfectly compliment your holiday meal.

Google released the first build of Android 12 almost exactly one year after dropping Android 11, which is remarkable in the midst of a global pandemic. But you can tell the Android engineers have been hard at work while quarantining, because the latest OS version is absolutely packed with new features.

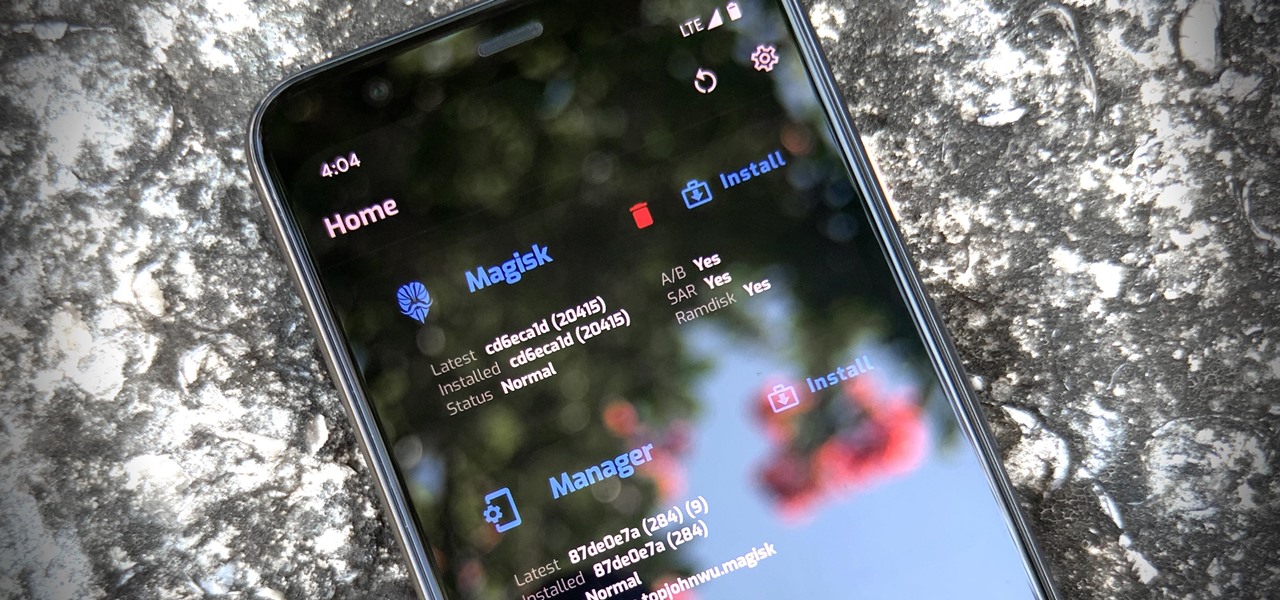
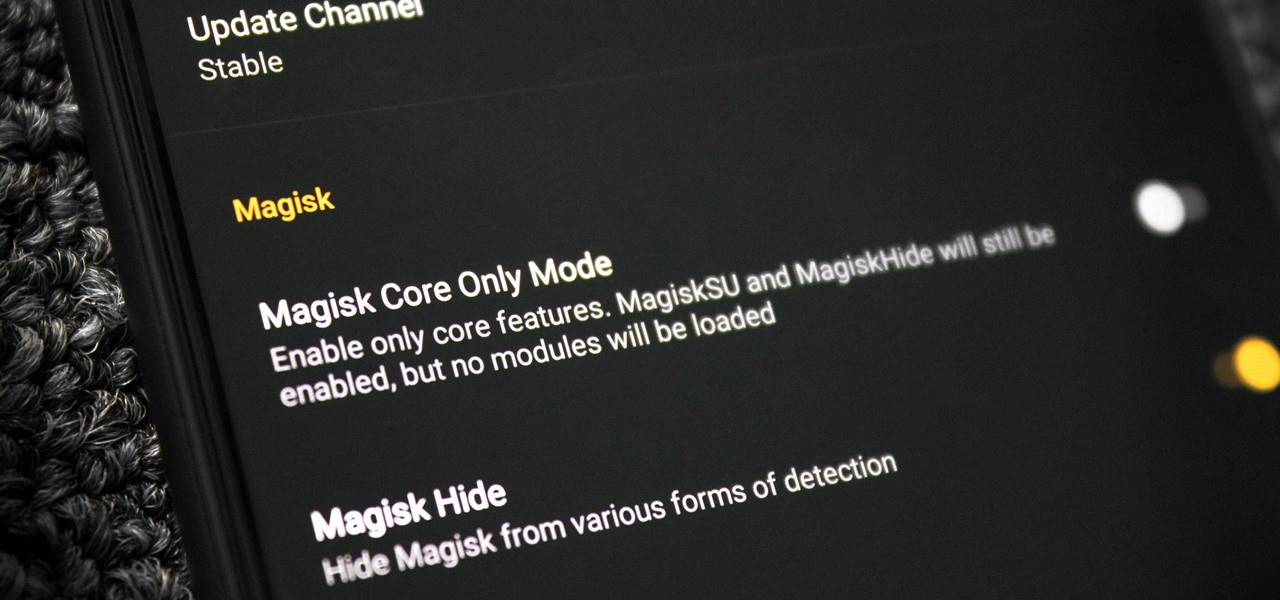
Thanks to Magisk, you don't have to lose root when updating to Android 11. The popular systemless rooting tool already achieved superuser access on Google's latest OS, even before the official release. It's currently in its experimental stages so the process is trickier than usual, but it does work.

Bootloops are a risk inherent to rooted devices — with great power comes great destroyability, after all. While custom recovery sometimes provides a quick fix when you flash the wrong Magisk module, with TWRP becoming more challenging to implement thanks to Android 10, the solution is a bit more complicated nowadays.

While conducting an OSINT investigation, it's important to be able to pull in information based on any clue you uncover. In particular, license plate information can turn up everywhere, from photos to live data to on your own street. You could use that data to find the VIN, see if a Tinder date has hit anyone, find out who's blocking your driveway, and so on. Skiptracer can help get the ball rolling.

From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

If you haven't used a Samsung device in a few years, the Galaxy S20 series will be your first taste of One UI 2, the skin running on top of Android 10. Although One UI is on the heavier side, it has loads of exciting features that go beyond what's offered in stock Android.

You may have noticed your Note 10 came with quite a bit of bloatware. Even the unlocked version of the phone comes with Facebook preinstalled, and if you bought it from a carrier, it's much worse. Luckily, there's a way to remove any apps you don't want, and you don't need root or a paid app to do it.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

Many apps claim to record phone calls on Android, but very few actually deliver. There's just too many different devices floating around out there for one app to be able to support them all — or so it would seem.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.