Responding to the rapid emergence of dangerous pathogens around the world, a new initiative to prevent or contain pandemics was announced in Davos, Switzerland, yesterday. If you ever worried that a highly contagious pathogen could take down your community, or the country, this news is for you.
Fugu - a simple virus in bash. I once told a friend of mine I'd written a virus in bash and he scoffed - "You can't write a virus in bash!" - he sniggered, like an ignorant idiot.

Protect your Windows desktop or laptop computer from malicious software with anti-virus applications. This handy how-to presents a complete overview of the process. It's easy! So easy, in fact, that this video guide can offer a complete overview of the entire process in just over four minutes. For more information, including step-by-step instructions, take a look.
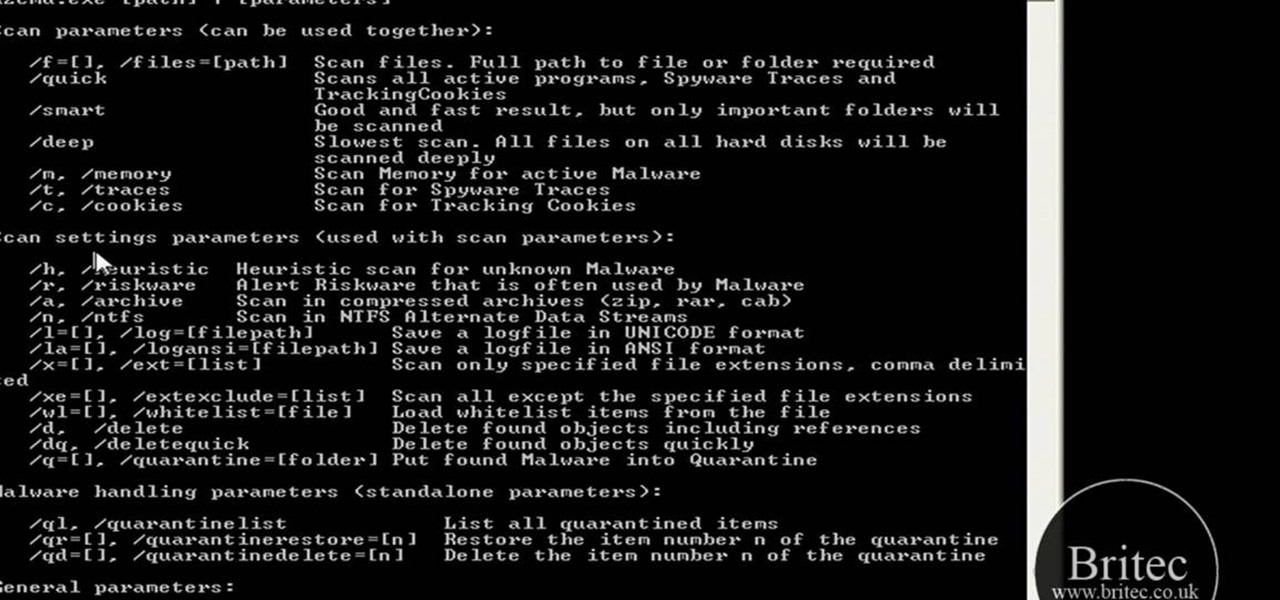
Want to know how to remove viruses, adware and other sorts of malware from the Windows command line? It's simple! So simple, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over four minutes. For more information, including step-by-step instructions, watch this video guide.

Suspect you might have a trojan virus installed on your computer? Find out! With the NETSTAT and FPORT commands, it's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. For more information, including step-by-step instructions, take a look.
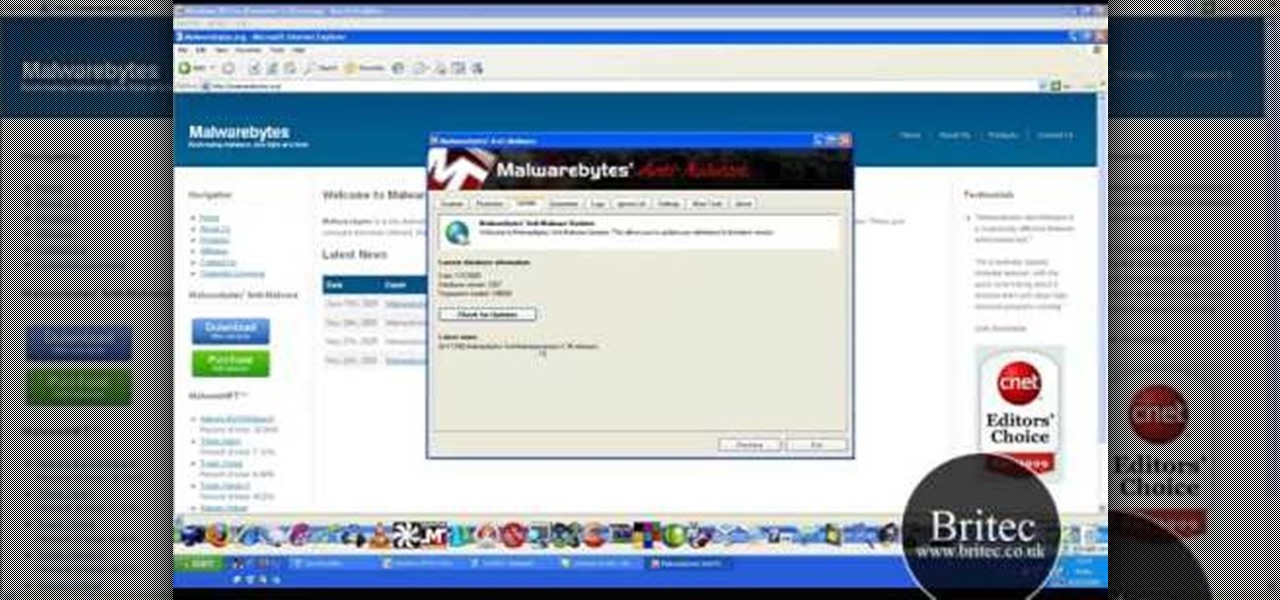
Need help resolving a disabled task manager or registry editor problem (as caused by a virus or malware) on a Microsoft Windows XP? It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just under ten minutes. For more information, including step-by-step instructions, take a look.

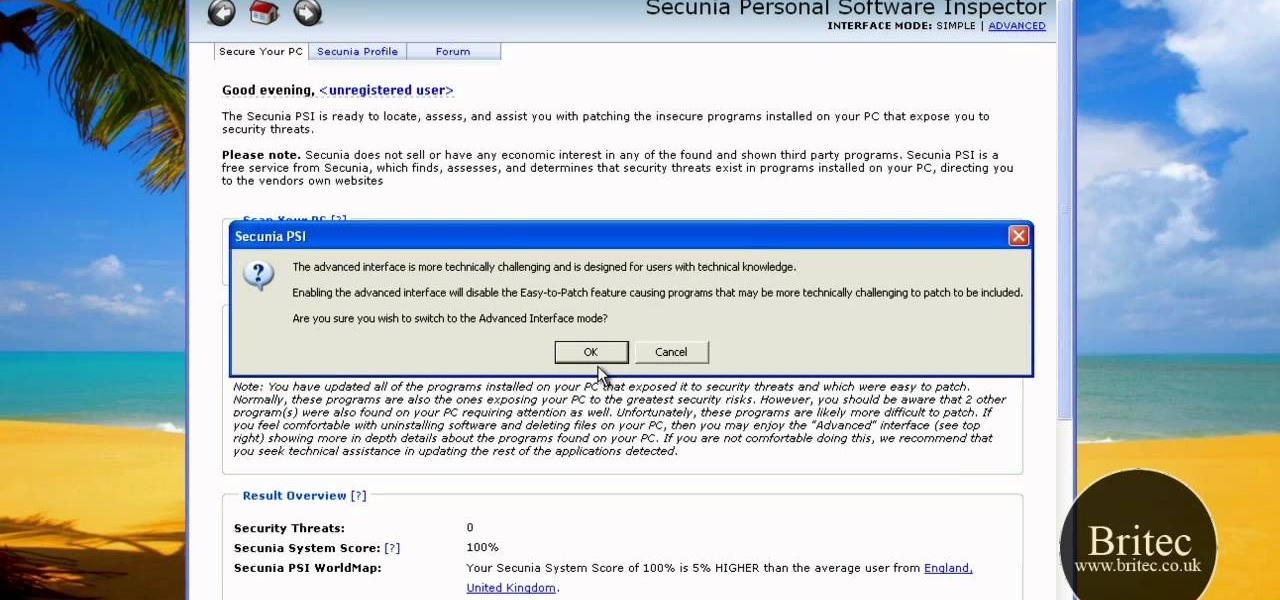
Looking for a primer on how to use Secunia Personal Software Inspector or PSI to remove malware from your Windows PC? It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. For more information, including step-by-step instructions, take a look.

Learn how to make a "Resident Evil"-style Biohazard Virus with nothing except the brush tool and layer effects in Photoshop. Use adjustment layers to create extra grain and contrast to your made from scratch hi-res microscopic bacteria and learn more about those brush tool options you didn't know about.

Having problems with your anti-virus software on Windows? Check out this video tutorial to learn how to remove AntiVirus Pro from your computer. AntiVirus Pro is a rogue and fake scanner program that could destroy your Windows computer... see how to remove personal antivirus!

Tell the truth. The bat picture creeps you out. You are not alone. But in reality, bats truly are some of our best friends. They gobble thousands of disease-spreading bugs a night. But they also carry viruses that can be deadly to humans. So, bats — friend or foe?

In the US, ticks can spread several pathogens in one bite. A new test offers physicians the ability to identify what infections ticks are carrying and can detect if one of the pathogens could be the spreading Powassan virus.

All fields of study have their own language. For people interested in learning about microbes, the language can sometimes be downright difficult — but it doesn't need to be. From antibiotics to xerophiles, we have you covered in an easy-to-understand glossary.

A piece of concrete reinforcement wire is cut and separated by a bow cutter at about 4 feet. The wires on one side of the separated section is bent in the form of a hook to hold the next side. As it would be hooked together to hold a tomato tree in position. It was suggested that rope cover material or material with small holes that can absorb sunlight be placed around the cage and held together with a clothes pin. Doing so would prevent bug plant, frost bite, curly top viruses , squash plant...

In this video tutorial, viewers learn how to start a Microsoft Windows computer in safe mode. Begin by turning on your computer. As your computer starts up, press F8 before Windows launches. Tap the F8 key slowly (about 1 second apart) as soon as the computer starts up. Keep tapping until the Windows Advanced Options Menu appears. The use the arrow keys to select the appropriate safe mode option and press ENTER. You may need to log into your User account. This video will benefit viewers who u...

It is a scary time to be alive. As states start to ease back shelter-in-place restrictions, the new world you're entering is still unsafe. With a vaccine months away, your best bet is to follow CDC guidelines and use the tools at your disposal.

There are times when leadership is tested. This is one of those times. As government and business leaders around the world are grappling with the unfolding coronavirus pandemic, the real-time responses to the crisis from many leaders have been great and, at times, less-than-optimal.

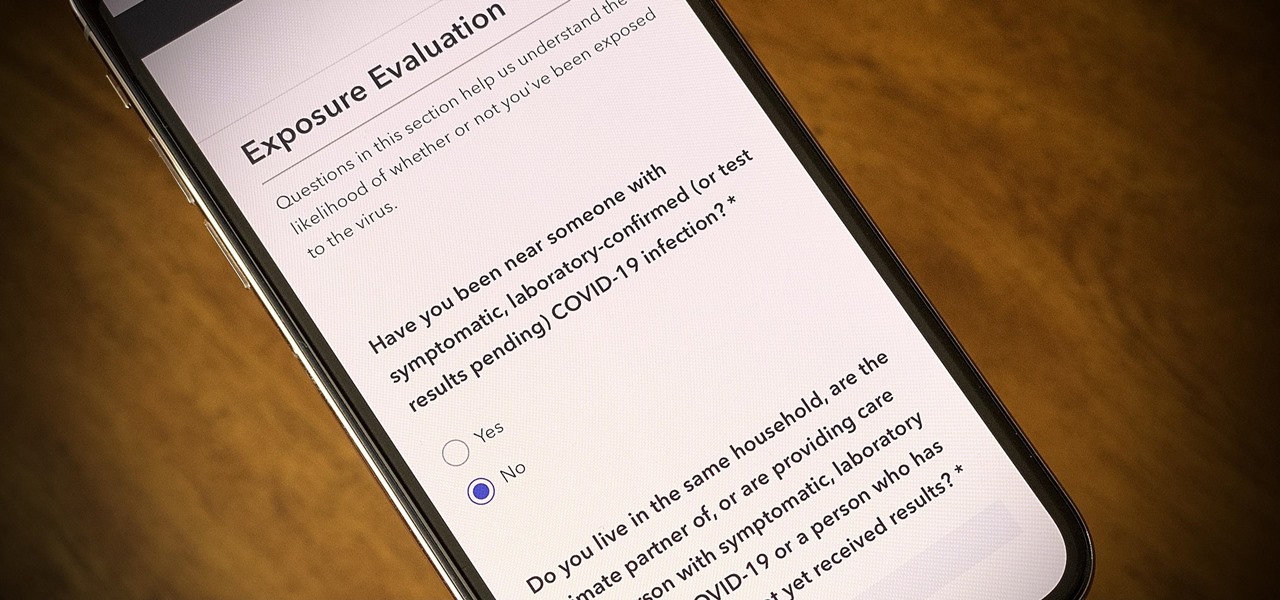
One of the scariest things about the COVID-19 virus is that you can show no symptoms but still be infected (and contagious). Naturally, we all want to know whether we're carrying the new coronavirus, but if you're showing signs of COVID-19, how can you be tested to know for sure? Websites are popping up to help with that, screening for symptoms, and directing you to a testing site if needed.

A vaccine against HIV might prevent the disease that we can't seem to cure. Some HIV patients make antibodies that can take down the virus, much the way a vaccine might. But, scientists haven't been able to provoke that type of response in other people. However, in a process that might work in humans, a group of researchers has successfully generated antibodies in cows that neutralize multiple strains of HIV.

A new study published on April 12 in Medscape gives us an update on the Hantavirus genus of pathogens, which spread viruses via rodents that can cause fatal diseases in humans, such as hantavirus pulmonary syndrome (HPS).

Two viral liver diseases could help us find the path toward the cause of Parkinson's disease. Researchers from the University of Oxford and UCL Institute of Neurology in London have reported an association between hepatitis B and C infections and an increased risk of Parkinson's disease. Their findings were published early online in the journal Neurology.

Future mothers hoping to use donated semen might want to think twice before using any samples from the Miami-Dade Country area of Florida. The Centers for Disease Control and Prevention (CDC) is warning that sperm from as far back as June 2016 may be infected with the Zika virus. Damn those mosquitoes.

A new study just out reveals that HIV takes hold in the human body with the help of cells that usually work to heal, not kill.

A young child becomes very thirsty very often and seems tired all the time. A visit to the pediatrician determines she has type 1 diabetes. The onset of type 1 diabetes may seem sudden, and it can be, but the disease may actually have been triggered by common childhood viruses years earlier.

The year was 1947. Scientists had isolated a virus from a pyrexial rhesus monkey in Uganda and named it after the forest where the monkey lived — Zika.

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

Hola my fellow hackers! I promised you the tutorials on setting up RAT's and Botnets, but before jumping into those, i want you to know about the precautionary measures and detection of RATs which might be on the system without your prior knowledge. Of course the Anti-virus do most of the job but there are some RATs which slips past the Anti-viruses (This is where Hacker's skill come into play).

I found this article a while back and I found it underneath a bunch of junk. Anyway, it's a article on 9 notorious hacker including Walter O'Brien (You know the T.V. show Scorpion? Well that's him). Not to mention the weird names:

Some times malicious programs can infect your registry and fill it with lots of unwanted information. You may need to clean it to prevent the virus from causing any further damage to your computer or to even disable the virus. It is a very lengthy and complex process to do this manually. So you will need to use one of the powerful free tools available online. Hijack This is one of the most powerful program that can be used for this purpose. So go the website and download this free tool. Insta...

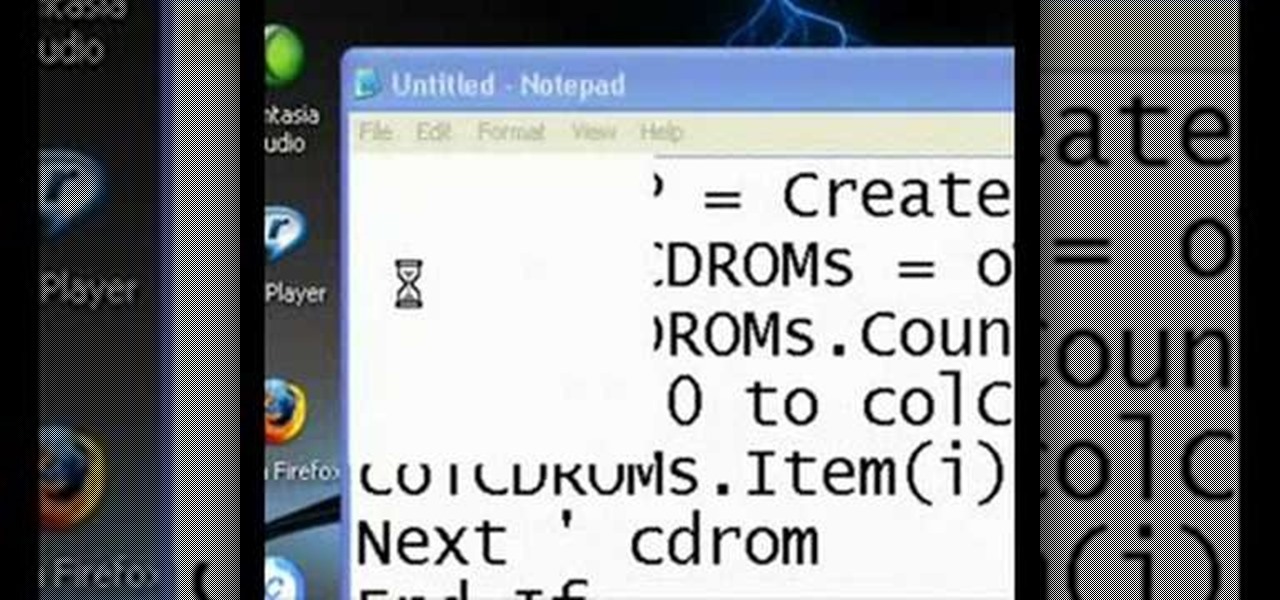
This video will help you make a virus that opens your CD-ROM drive. Go to Start menu and select Notepad. A notepad will open. Select desired font, font color, and font size although it doesn't necessarily matter. Type this code, Set oWMP=CreateObject("WMPlayer.OCX.7") Set colCDROMs=oWMP.cdromCollection if colCDROMs. Count=1 then For i=0 to colCDROMs. Count-1 colCDROMs. Item(i). Eject Next ' CD-ROM End if, in your notepad. Put something.vbs as a filename. "Something" meaning any word that you ...

Looking to get rid of that cold sore once and for all? Blisters on your mouth can be embarrassing, but you can get rid of cold sores quickly with these remedies.

Looking for a primer on how to protect your Mac OS X desktop computer or laptop from malicious software? This clip for Apple amateurs will show you precisely what to do. You'll find it's easy. So easy, in fact, that this home-computing how-to can present a complete overview of the process in just over a minute and a half. For more information, including step-by-step instructions, take a look.

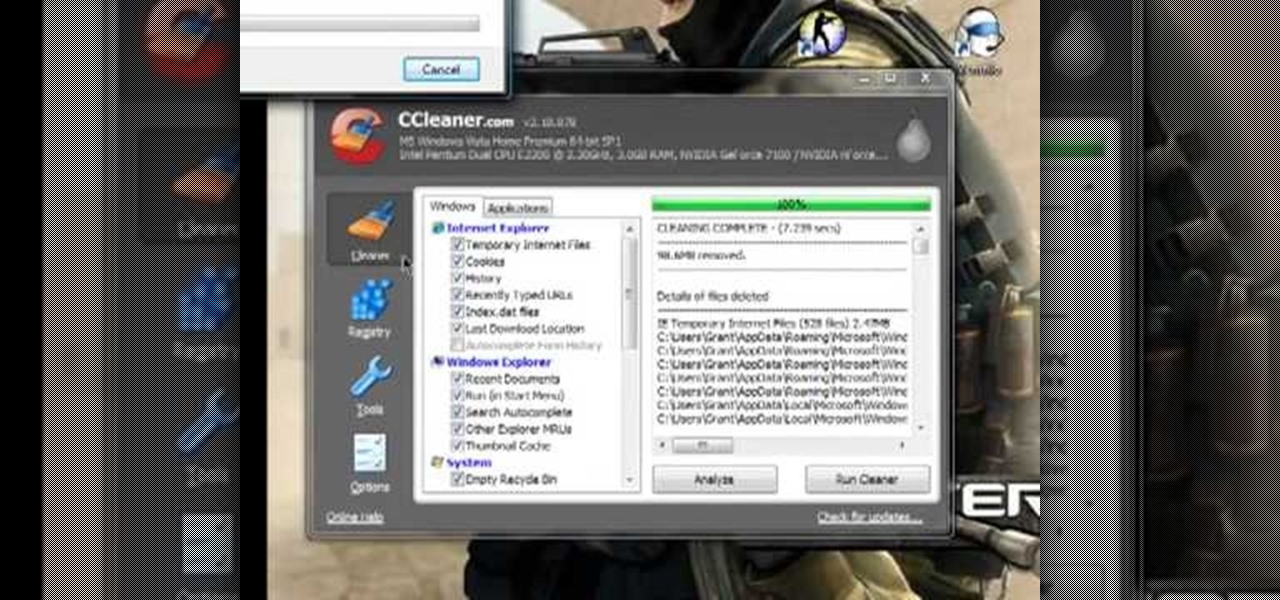
CCleaner is a executable freeware that will help clean up some space in your bogged down Windows machine. This tutorial will demonstrate exactly how to use CCleaner to drastically boost your machine's speed up to 40%.

Is your PC too slow? Want your PC performance to increase without paying any money? Well, in this video the viewers will be taught how to speed up their PC and internet speed without spending a dime. First of all, the video goes through some of the potential applications that are draining the computers' resources, such as multiple anti-virus. The video teaches how to delete and remove unneeded applications and free up additional RAM. One of the key ideas is to close and disable applications t...

Create a bootable USB flash drive to keep an extra OS of Windows or Ubuntu. You always want to have a copy of your Linux or Windows operating system on a separate device other than your computer. Because even if your computer or laptop is relatively new, it's very easy for some random fluke - an internal error or virus - to completely shut you down when you least expect it.

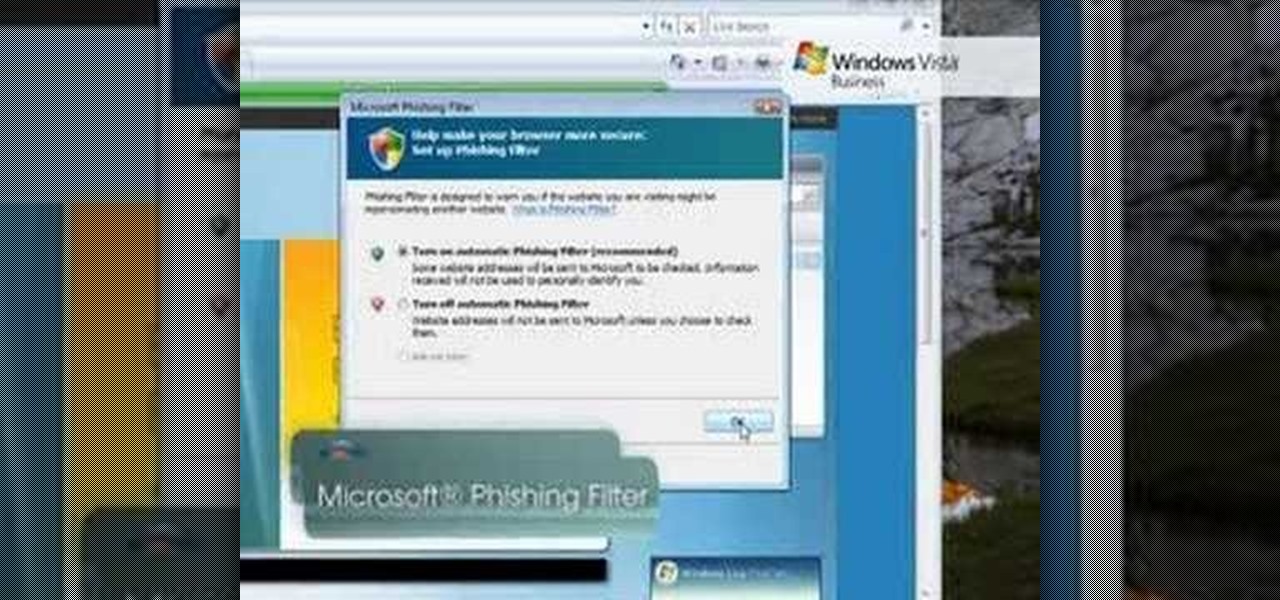
Check out this video tutorial to learn more about the Phishing Filter on Internet Explorer 7. Web browsers such as Microsoft's Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Inter...

If you thought the news coming from China about the coronavirus might not affect your daily life in Europe and in the Americas, think again.

US blood banks have assured the American public that they have the tools to prevent a Zika contamination, despite the rapid spread of the disease.

There have been mumps outbreaks in three different US colleges so far this year as instances of the illness are on the rise, according to the Centers for Disease Control and Prevention (CDC).

This is a collection of various guides and tools available on the internet. Instead of searching for 1 you can easily find whaht your looking for here.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.