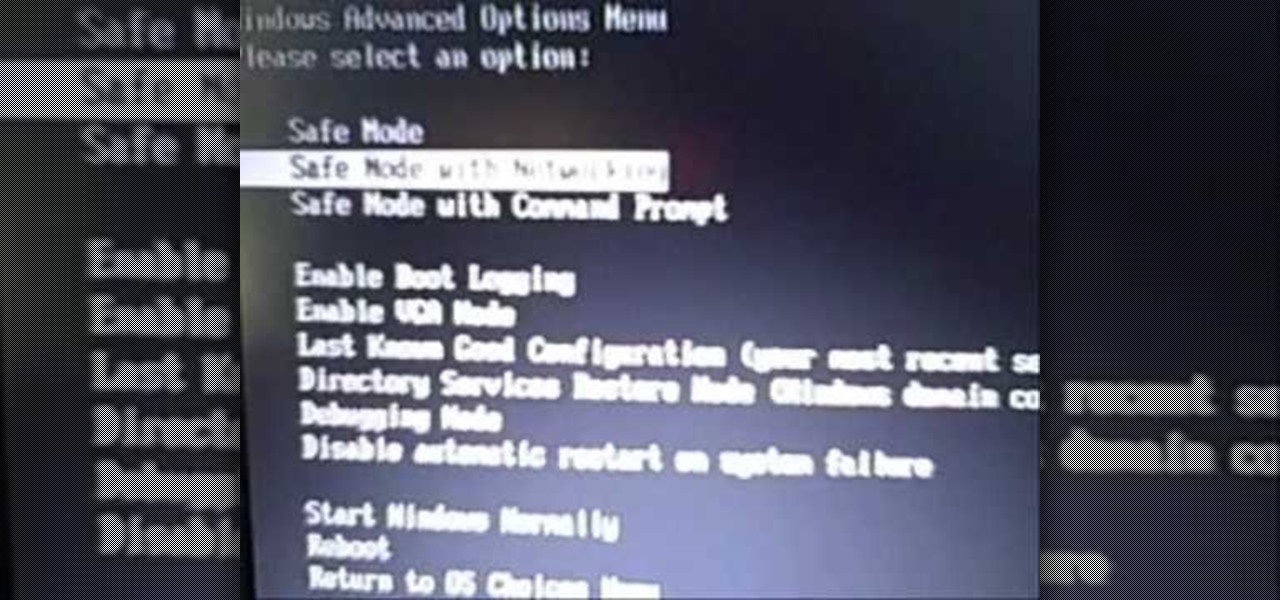
There are times when you must start up your Windows XP computer system in Safe Mode, for example if you need to remove certain viruses, key loggers, adware, etc. that cannot be removed while in standard mode. If you want to learn how to boot in safe mode in Windows XP, you should watch this. 1. Turn on your computer. Make sure your monitor is on and you do not step away from your computer, as booting into safe mode happens within the first minute of when you turn on your computer. You should ...

In this Know Your PC video the instructors show how to perform a recovery on your computer by demonstrating it on the HP TouchSmart PC. This recovery process will work on any HP desktops, HP Pavilions, Compaq Presarios. Your PC might get corrupted if you recently made any changes to it or installed software that contained viruses and many other reasons. In such cases the best thing to do is perform a system recovery. Recovery will help you take your computer right back to the way it was out o...

Next time you don't want to make your bed, dry the dishes or clean the house there's no need to feel guilty. You may be doing yourself a favor. There are legitimate scientific reasons why some chores aren't always the best health choice.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a mini multi-touch table and photo stitch.

In late June, the biggest measles outbreak to strike Minnesota since 1990 seemed to be winding down. Today, public health officials announced a new confirmed measles case in the area.

Electrical impulses course through our heart and keep it beating. That's why a jolt from an automated external defibrillator can boost it back into action if the beating stops. But new research says there may be more to keeping a heart beating than just electrical impulses.

Officials in Colorado are concerned as 61 cases of the mumps were reported so far this year, a significant increase in the prevalence of the contagious disease in the state.

There's now more reasons to make sick workers stay home—a new game theory study suggests adequate hand washing and other illness-aversion tactics aren't as useful as we thought to keep you from getting infected when a virus or bacteria is circulating.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

A wave of shock and anger swept across the country after Edward Snowden released private documents recounting the U.S. government's secretive mass surveillance programs. Although some of the fear was unwarranted (they don't read your emails or listen to your calls), many scrambled to find privacy of new heights for protection from the all-watchful eye. While the government may not be tracking you down, there are a myriad of other candidates that fill that Big Brother role—and I'm not talking ...

Sometimes it's necessary to format your memory card in your mobile phone or digital camera, just like you need to format a hard drive, because of virus problems or slower speeds. This video will show you the steps to formatting (or reformatting) the SD memory card for a cell phone, using a memory card reader. You'll also get details about a write protect error that could happen.

Apple announced upcoming changes today to prevent third-party tracking of users and prevent autoplay, on Safari. Safari will prevent the recording (by anyone other than Apple) of users' browsing behavior, and by doing so prevent advertisers from targeting ads based on individuals' history.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.

Hello Friends … My name is Suresh Senarathna and this is my first “How-To” post,

Video: . Extraterrestrial life is life that does not originate from Earth. It is also called alien life, or, if it is a sentient and/or relatively complex individual, an "extraterrestrial" or "alien" (or, to avoid confusion with the legal sense of "alien," a "space alien"). These as yet hypothetical forms of life range from simple bacteria-like organisms to beings far more complex than humans. The possibility that viruses might exist extraterrestrially has also been proposed.

Lock screen exploits are becoming increasingly common in the mobile world. Four weeks ago there was the iPhone 5 passcode bug (which just got fixed yesterday...kinda). Then there were a couple lock screen bugs on the Samsung Galaxy S3 two weeks ago.

Now is the time to instill good hygiene habits that will serve your child for life. You Will Need

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

How to scare and prank your friends with a fake virus.

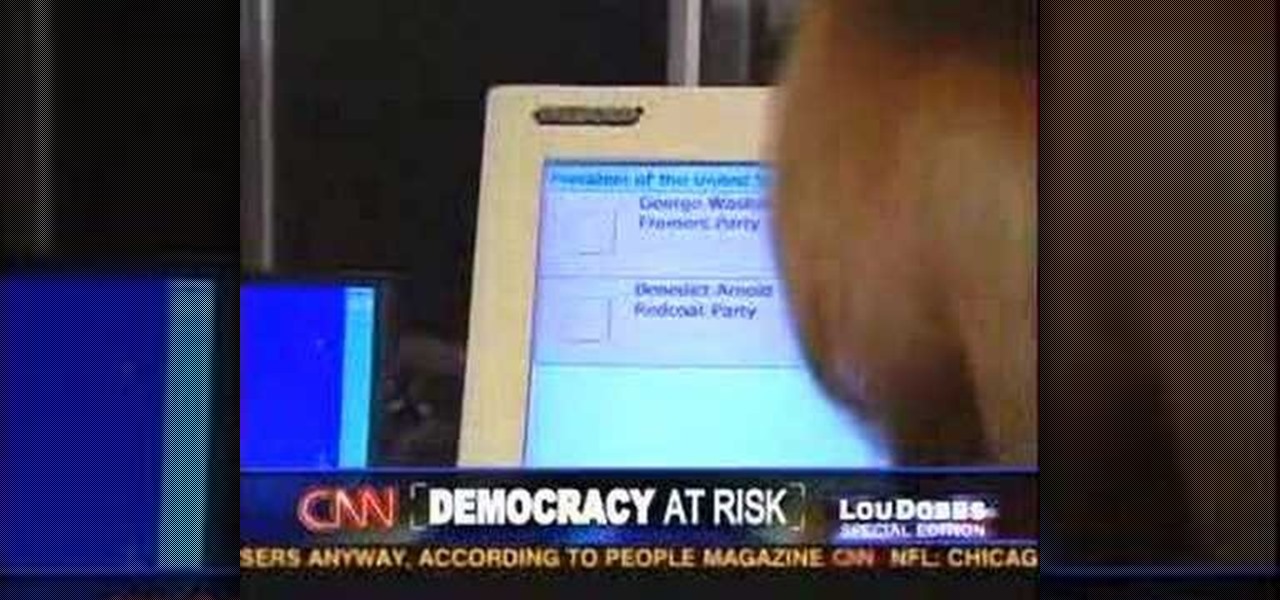
It only takes a minute to steal a U.S. Election!

Learn to hide icons and use paint to prank friends. This prank makes friends think their computer froze or the have a virus.

Every state has begun reopening in some capacity. While there are important steps for everyone to get back to work and begin socializing, precautions will be in place for some time, especially with an expected second wave coming this fall. The virus is not over.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Whether you were exposed to the COVID-19 virus or just taking precautionary measures, self-quarantining is a tremendous disruption for anyone. Still, we all have to eat, pandemic or not. But unless you like eating canned food for two weeks, you're going to want to explore other options. That's why food delivery apps are going to be so necessary during such a hectic and uncertain time.

There have been hundreds of reports of Google Calendar users receiving notifications for events they didn't create. These "events" are actually spam ads and potential phishing threats. If this has happened to you, you're not alone — but luckily, there's a way to put an end to it.

Our national month-long celebration of all things creepy and crawly comes to a climax on Wednesday with Halloween and will end with Día de Muertos on Friday, so now is the ideal time for the The New York Times to publish a mildly chilling augmented reality story for children.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

For a company more associated with debugging computer programs, Google's parent company, Alphabet, is making a name for itself by taking on the real thing — mosquitoes.

Sex makes the world go 'round, and when it does, so does gonorrhea. Finally some good news on the growing menace of drug-resistant gonorrhea — a large, long-term study shows a vaccine may work in reducing the incidence of an increasingly dangerous infection.

Maine reported their first measles case in 20 years yesterday, June 27, in a press release from the Maine CDC. Many other people may have been exposed and could show signs of infection soon, with the potential for outbreak brewing. The last measles case in Maine was in 1997.

In Indianapolis, two-year-old Kenley Ratliff has passed away from what is suspected to be Rocky Mountain spotted fever (RMSF), a tick-borne illness. The young girl fell ill with a fever, and just a week later, passed away. Now her family and doctors are looking into the cause of her death and warning others to check themselves for ticks this summer.

The Massachusetts Department of Public Health (DPH) issued a health alert for a Boston mumps outbreak, on Monday, June 5th, to healthcare providers and local boards of health. There have been 12 reported cases of mumps during the recent outbreak. The affected residents' symptoms occurred between March 24th and May 31st, and 10 of the 12 had symptoms after May 9th. There have been 35 confirmed cases of mumps in 2017 in Massachusetts, and "nearly 300" suspected cases in the continuing outbreak.

Dangerous to humans and dogs, Rocky Mountain Fever, along with several other tickborne infections, is on the rise.

The possibility of severe tickborne illness is increasing as an aggressive tick from the American southeast moves up the Atlantic Coast.

As researchers from Yale searched our environment for compounds to aid in the battle against drug-resistant bacteria, they got an unlikely assist from ticks.

Lyme is a growing threat as we move into warmer weather in the US. Researchers have said this year could be one of the worst for this tick-borne disease, as a skyrocketing mouse population and warmer temperatures increase the risk.