It's about time people acknowledged that judging drug users would do nothing productive to help them. In the US this week, two new programs are launching that should help addicts be a little safer: Walgreens Healthcare Clinic will begin offering to test for HIV and hepatitis C next week, and Las Vegas is set to introduce clean syringe vending machines to stop infections from dirty needles.

In March, we wrote about the growing threat of yellow fever in Brazil. At the time, the disease had killed just over a 100 people. Unfortunately, the disease has only spread since then with many more people infected and more killed.

Have you ever had the stomach flu, aka the 24-hour flu? Well, chances are high that you never had influenza, but an intestinal infection called gastroenteritis.

Ecosystem changes caused by agricultural choices in Brazil are creating a dangerous microbe mix in exploding populations of vampire bats and feral pigs.

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

There's no shortage of ways to filter water, but it doesn't get much simpler than this. Researchers at MIT have found that you can turn dirty water into drinking water with nothing more than a stick.

Welcome back my precious hackerians. Today i would like to promote an OS which i have been using for the past couple months. I'm not talking about Backtrack 5 or Kali Linux. Something even more promising:

What's the most installed Android app in the world? Facebook? Gmail? Maps? While those all have well over 100 million installs, the one that takes the cake—and always will—is Google Play.

Link shorteners like TinyURL and Bitly are great for Twitter (or anytime you're limited on space), but they're also great for hackers. It's easy to hide a malicious link in an innocent-looking shortened URL, which increases the chances that people will click on it.

If you use Ubisoft's uPlay browser extension, you should probably get rid of it right now. An Information Security Engineer at Google discovered that the plugin has a hole in it that allows programs to be installed through uPlay, essentially letting anyone who feels so inclined to take over your computer. How the Exploit Works

In this video tutorial, viewers learn how to completely format a hard drive. Begin by downloading the Knoppix Live Boot CD. Then burn the newly download ISO onto a CD as a bootable disc. Use your BIOS to tell your computer to boot from the CD-ROM instead of the hard drive. With the Knoppix CD still in your CD drive, restart your computer to load up Knoppix. Once loaded, use Knoppix to run the “dd” command and reformat your hard drive. This video will benefit those viewers who want to learn ho...

It's not hard to let the new SARS-CoV-2 strain of coronavirus put pressure on our minds. Fear of catching COVID-19 is never far from the topic of conversation. But it doesn't have to be that way. If you're struggling with anxiety, stress, depression, or any negative emotions due to the virus's effect on our lives right now, you might find some solace in meditation.

MIT artificial intelligence researcher Lex Fridman recently asked SpaceX and Tesla founder Elon Musk possibly the best question he's ever been asked: What would he ask a hypothetical AGI system (an AI system with human-level intelligence and understanding) if he only had one question?

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

Young girls, especially those who live in areas where HIV is epidemic, like sub-Saharan Africa, are particularly vulnerable to becoming infected with HIV. A vaginal ring containing the antiviral agent dapivirine has been shown to decrease the chance of developing HIV-1 in adult women over 21 and now in the first step for use in adolescents, the ring has been shown to be safe and well-tolerated in that younger age group.

As a part of the already crowded field of diseases transmitted by ticks, you may not know the disease babesiosis, a dangerous infection caused by a parasite that infiltrates blood cells.

Like humans, cats can suffer infections caused by ticks, and too often, the disease is fatal. Learn about tickborne diseases that affect cats and what you can do to protect Fluffy from an untimely demise.

When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was quarantined by the State of New Jersey in Newark. She later filed a lawsuit in U.S. District Court for violation of her civil rights, false imprisonment, and invasion of privacy.

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.
As a hacker or an aspiring one, You need to be careful and anonymous if your doing anything illegal. But you slipped up. Now someone is tracking you! Well luckily you read this post ahead of time and have a backup plan!

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.

It's officially the holiday season, which means everyone will soon be traveling home to spend time with loved ones. And anyone who has any knowledge whatsoever of computers knows what else that means—family members left and right asking you to fix their various technical woes.

We're living in uncertain times. The sudden outbreak of the novel coronavirus and subsequent self-isolation of roughly half the world's population has led to a massive reorganization of the economy, countless layoffs, compromised security networks, and a variety of other significant disruptions that will forever alter the landscape of our daily lives.

As the COVID-19 virus continues to spread, counties, cities, and states are closing down businesses, events, and schools that aren't absolutely necessary. Some companies around the US are recommending or requiring employees to work from home during the coronavirus pandemic. If you're stuck at home, there are apps and services to help you make it through a lockdown.

The coronavirus continues to disrupt the tech industry, including the augmented reality segment, with Apple and the iPhone the latest to feel the impact.

Antibiotics are one of our main weapons against infections. The problem is that many bacteria are becoming resistant to most of the antibiotics we use to treat them, and those 'superbugs' have created an urgent threat to our global health. A research group found a new way to hit a well known bacterial target and have developed a drug to hit it.

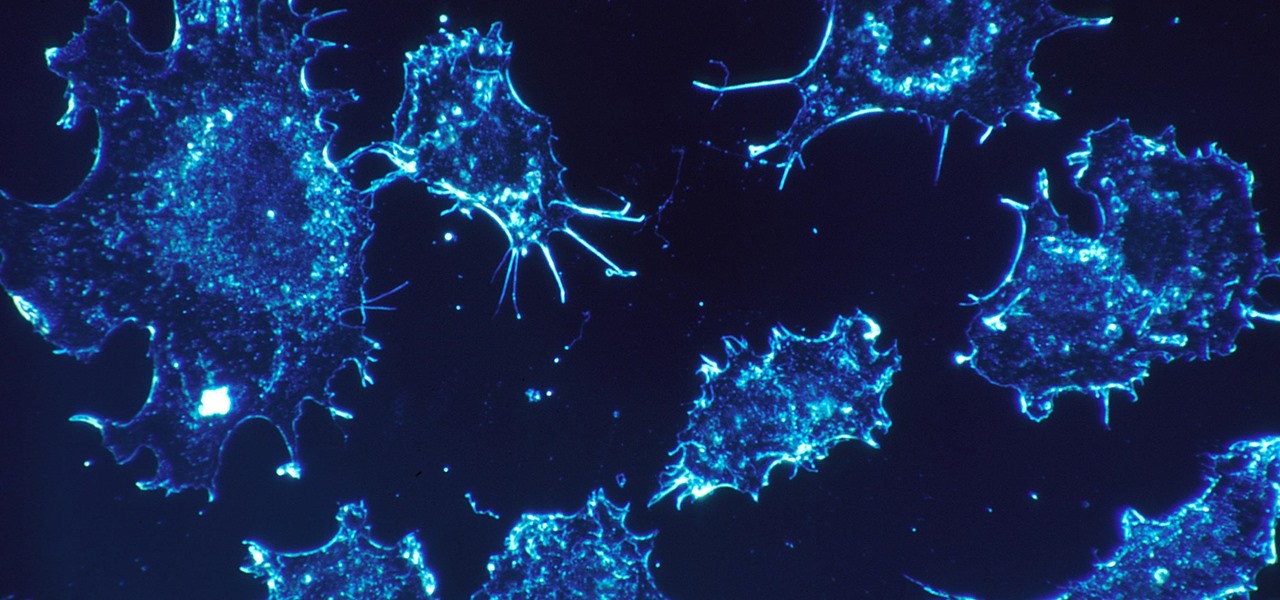
As our cells age, they eventually mature and die. As they die, they alert nearby cells to grow and multiply to replace them. Using a special imaging process that combines video and microscopy, scientists have observed the cellular communication between dying and neighboring cells for the first time, and think they may be able to use their new-found information against cancer cells, whose damaged genomes let them escape the normal dying process.

What would it be like to have clothing that killed microbes? Or paper that repelled pathogens? A research team from Rutgers University has developed a prototype out of metalized paper to zap the bad guys without being super expensive. Sound good? Read on.

Usually, the mucus lining of the female genital tract presents a barrier that helps prevent infections. But, somehow, the bacteria that causes gonorrhea gets around and through that barrier to invade the female genital tract.

Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications' clothing," infects Android users.

As it turns out, your Android apps are pairing together to share your data without asking for your permission first. Researchers from Virginia Tech developed a tool called DIALDroid to monitor exchanges of data between Android apps over the last three years, and what they've found is quite alarming.

Rumor has it that a gang of hackers—or possibly, one lonesome individual—holds the power to remotely wipe millions of iPhones and iCloud accounts, unless Apple coughs up some ransom money by April 7.

Sleep lets our body processes rest and restores us for the next day, so a bad night's sleep can ruin the following twenty-four hours and even make us feel sick. Now, new research published in the journal Sleep cements the idea that loss of sleep actually leaves us vulnerable to sickness.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.

Let's say you got a little careless while installing apps from unknown sources, and now your Android device has been infected by malware. Or perhaps your friend has come to you for help after they had haphazardly installed random apps until their phone was filled with popups and garbage like that.

Coffee is a topic that everyone has a strong opinion about, especially when it comes to brewing the perfect cup. Even if you buy the best beans and grind them yourself, chances are you're skipping one necessary step to make sure your coffee tastes the best it can: cleaning your coffeemaker the right way.

Hi! Let me get started on this subject as it is a very "touchy" subject. We all want to "hack" these days, and that's logical. Te be real honest here, i was inspired once by the words someone from the Null byte community said. In the (near) future, wars will be ended by computers and not a nuclear missile. That's something i really do believe in. But let us take a defensive measure instead of the offensive one. Sure, Full frontal bryte forcing is an option, but when it'll come that far we'll ...