Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

With the new year just around the corner, it's a time we all reminisce about the year that was. In the midst of families fighting over white elephant presents and the financial stress that comes with holiday gifting, you may also be dealing with the stress of hosting parties and get-togethers as well as the decorating that goes with it.

When it comes to wallpapers, I'm no monogamist. I have a lot of wallpapers that I'm committed to, but they don't always get their fair share of time with me—and that's where the problem lies. I'm too lazy to go out of my way to make sure they all feel loved. I'd rather them to come to me when it's their turn, and thanks to Wallpaper Changer, they can do just that.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Earlier this month, AT&T quietly introduced a new "Mobility Administrative Fee" which levies a $0.61 monthly charge to all postpaid contracts. While it's a seemingly small amount on an individual basis adding up to $7.32 per year, with its huge customer base, AT&T stands to make around half a billion from the tight-lipped move. AT&T has stated that the fee will "help cover certain expenses, such as interconnection and cell site rents and maintenance" that's consistent with other phone carrier...
The world is surrounded by negative vibes, everyone of us needs to be positive in a way to have a balance in life. I will share with you, what are the steps to be an optimistic person.

I'm not admitting to anything, but let's be honest, most of us download content on the Web from time to time. With copyright holders laying down the law more and more often, it can't hurt to do so with caution. And even if you aren't downloading copyrighted material, you still don't want companies snooping in on your online activities. So just how do you protect yourself when torrenting? Avoid "Open Communities"

Jake von Slatt of The Steampunk Workshop kept breaking the rear glass panel on his iPhone. So, he ended up making his own gorgeous replacement out of brass to replace the standard Apple logo ones who kept getting. The only problem was that it made his signal strength super weak, so he figured out how to transfer the etching onto a glass back. Here's the basic rundown of how he accomplished this feat...

Thanks to everyone who submitted ideas in last month's Mad Science contest. The question called for your best idea for using Sugru, a temporarily malleable silicone modeling clay that self cures for a soft-touch permanent bond. It's a marvelous product for at-home quick fixes and for even making some cool DIY bumpers and grips for your electronics. William scoured through all of the comments and chose the two winners he felt best deserved a pack of Sugru.

It's not always an easy task to paint used furniture, especially when you're dealing with Formica, which is a hard durable plastic laminate used on countertops, cupboards and some furniture pieces. This video will show you the steps required to start painting a Formica surface. Also, you'll learn how to properly prepare metal hardware to be painted.

You will need 2 packs of kanekalon hair extensions, gel, for a firmer hold. You will also need clips to get the hair out of the way and a comb to make straight lines. A lighter is also used, to seal the ends. You first want to separate the air into sections. Put a little bit of gel at the root of the strands. You get the strand of extensions between your thumb and index finger, with the strand in the middle. Then you braid the extensions with the natural hair and twist so the two of them bond...

It is almost indisputable that smartglasses and head-worn displays are the future of augmented reality. However, at this precise moment, they are still a very niche market.

After tapping Nvidia for its first AR headset, Magic Leap is calling in reinforcement for its future enterprise-focused efforts.

Two brands with affinities for augmented reality, Marvel and the NBA, joined forces to inject some AR superpowers into Monday night's matchup of the Golden State Warriors and New Orleans Pelicans.

While holographic Whitney Houston is hitting the road, a new mobile app is bringing volumetric captures of up and coming performers directly to the iPhones and iPads of fans.

We've been so worried about volumetric scans possibly robbing celebrities and performers of their agency and right to control their image that, somewhere along the way, we forgot that scans may not always be necessary to produce passable holographic performances.

When it comes to building luxury cars, Bentley certainly knows what it's doing. However, when it comes to building an AR app, Bentley is looking less Continental GT and more Geo Metro.

Continuing our NR30 series this week, we focused on the leaders of the software development industry that make augmented reality experiences possible. In other news, two of the current leaders in making AR headsets, Microsoft and Magic Leap, are pursuing multiple verticals with their products, as both now appear to be interested in making AR headsets for the military.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

In the Android community, Samsung's slow updates have long been the accepted norm. With the Note 8's recent Android Oreo update, Samsung completed annual version updates to their 2017 flagship lineup. Now is a great time to look back on how Samsung has fared with updates over the past few years. Hint: It's not pretty.

It looks like there is a fatal flaw in the current macOS High Sierra 10.13.1, even straight from the login menu when you first start up the computer. This severe vulnerability lets hackers — or anyone with malicious intentions — do anything they want as root users as long as they have physical access to the computer.

Now that it's been officially released for Android, Monument Valley 2 shot to the top of our best paid puzzle games list, and rightly so. This was no easy feat, as the games we covered ran the gamut of puzzles and all had stellar reviews. But there's just something about Monument Valley 2 that made it stand out from the rest.

DownToDash, an app from an NYC-based startup, connects students to other students who want to hang out the same way they do. The social networking app has gained increasing popularity since its launch in October 2016 and looks ready to become even more available. The app was founded by Sama Jashnani and Anuja Shah, both recent students themselves.

What would it be like to have clothing that killed microbes? Or paper that repelled pathogens? A research team from Rutgers University has developed a prototype out of metalized paper to zap the bad guys without being super expensive. Sound good? Read on.

Augmented and mixed reality developer Arvizio is working on a suite of software solutions for enterprises that will extend HoloLens capabilities as a full-fledged collaboration and conferencing tool. The company will demonstrate its Mixed Reality Studio suite to attendees at the Augmented World Expo, which begins later this month in Santa Clara, California.

Antibiotic use in infants has been associated with a host of childhood conditions later in life. Yet when an infection is suspected in a newborn, usually a sample of their blood is drawn to check for the presence of bacteria and 5 to 8 percent of them receive antibiotics while the diagnosis is pending.

And so it begins... CES 2017 is upon us! This is a very exciting time for those who are looking out for the newest innovations and releases from the world of technology. I said this was going to be a fun week, and here we start it with a bang from smartglasses developer Osterhout Design Group (ODG).

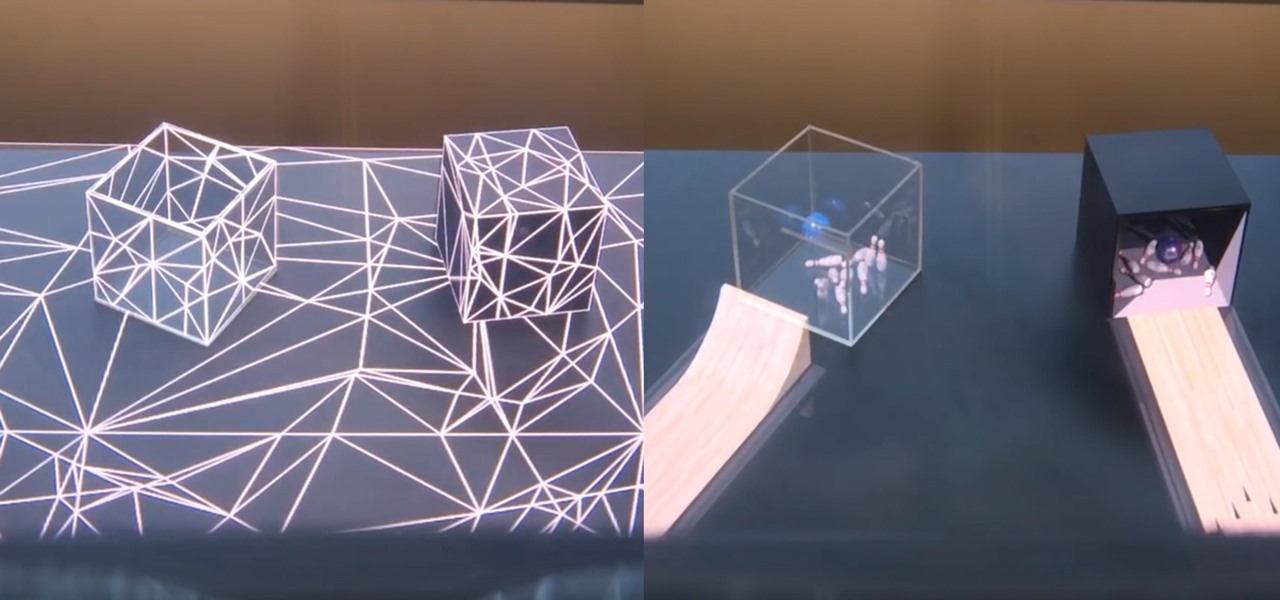
Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.

If you've been following NextReality, you've surely seen me around, or at least have seen my articles. My name is Jason Odom, aka Subere23, and it's about time for a formal introduction.

Throwaway phones aren't just for seedy criminals and spies—they can be useful for many everyday situations.

Today's pollution, hectic lifestyle, inadequate sleep and no time for pampering can leave your skin lackluster resulting in drying skin and making dry skin drier ultimately causing the early appearance of wrinkles and aging. A good fruit facial helps relax your skin from deep inside and the proper messaging gives it a rosy glow by increasing blood circulation imparting your face with a luminous glow. These are even better because they are natural and chemical free unlike the artificial facial...

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

I love eating fish at restaurants—the flesh is flaky and tender; the scent, fresh and sweet. Cooking fish at home is a completely different story, though. Even when I do cook successful fish dishes, it often leaves this (for lack of a better description) fishy smell that permeates everything it touches. Monday's salmon becomes Wednesday's odor. It's enough to deter me from cooking fish, period.

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.