Two slices of whole-wheat toast with lots of butter. Two eggs, poached to a firm yet custardy texture. The yolks should absolutely not be hard-cooked and the whites should be tender, not rubbery. That's my idea of the perfect breakfast.

Most people give their fruits and veggies a cursory rinse under the faucet before eating or cooking them, but is that few seconds under running water really enough to remove any remaining dirt, pesticides, or wax clinging to the surface?

Hard-boiled (also known as hard-cooked) eggs are notoriously easy to mess up. We've all ended up with tough, rubbery egg whites and overcooked yolks that have that unappetizing gray-green ring around the edge. An ideal hard-cooked egg has a firm yet tender white, while the yolk is creamy and well-done without being mealy.

This summer's going to be a hot one, so skip the water pistol this year and break out the big guns! In this project, I'll be showing you how to build a water balloon shotgun—a high-powered water balloon launcher that's capable of firing 17 water balloons at the same time!

A deck of cards may be a magician's best way to demonstrate his or her's sleight of hand, but for the prankster, it's the perfect way to deliver a shocking 300 volts of electricity! And that's exactly what I'm going to show you how to do today. Stuart Edge used it in his "Electric Shock Kissing Prank" to show the ladies how a man can really put the sparks in a kiss.

If you're too old to trick-or-treat (are you ever really?), throwing a Halloween party is the next best thing. You could always just serve beer and jungle juice like most other people will be doing, which will certainly get the job done, but where's the fun in that? Instead, impress (or gross out) your guests with one of these gruesome drinks.

Eat wonderful peaches all year long. Freezing fruit is easy and a great ways to preserve and retain nutrients. Freeze your peaches now and thaw them when you are ready to make a peach pie or smoothies. This is the perfect way to make the most out of your fruit.

After tapping Nvidia for its first AR headset, Magic Leap is calling in reinforcement for its future enterprise-focused efforts.

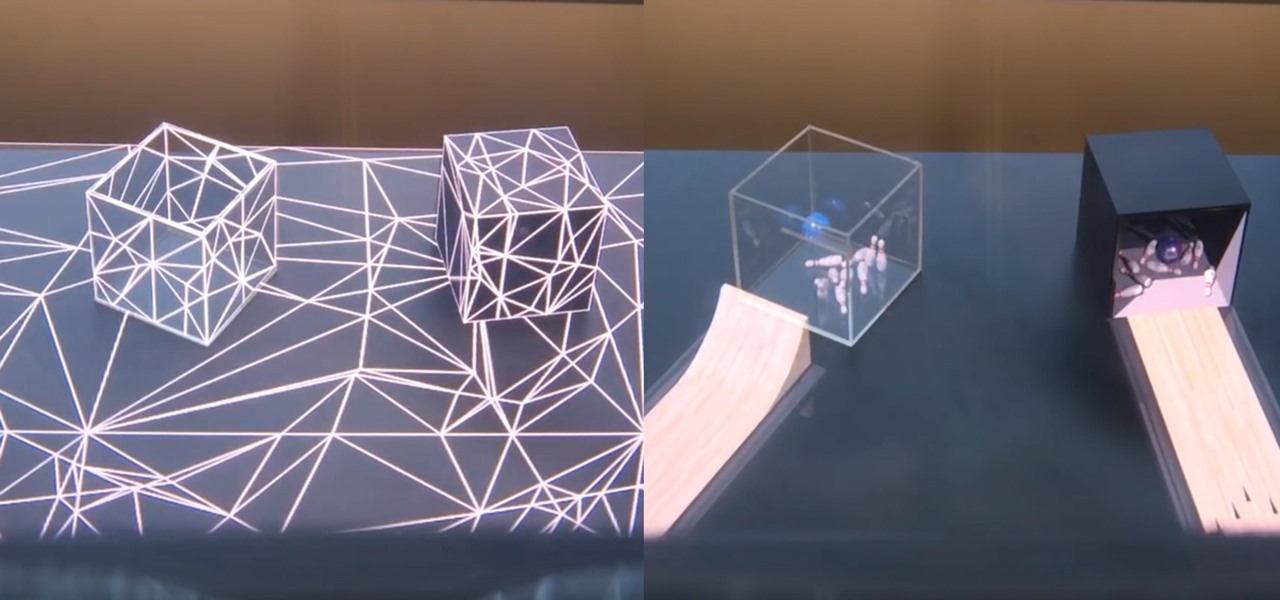
We've been so worried about volumetric scans possibly robbing celebrities and performers of their agency and right to control their image that, somewhere along the way, we forgot that scans may not always be necessary to produce passable holographic performances.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Continuing our NR30 series this week, we focused on the leaders of the software development industry that make augmented reality experiences possible. In other news, two of the current leaders in making AR headsets, Microsoft and Magic Leap, are pursuing multiple verticals with their products, as both now appear to be interested in making AR headsets for the military.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

In the Android community, Samsung's slow updates have long been the accepted norm. With the Note 8's recent Android Oreo update, Samsung completed annual version updates to their 2017 flagship lineup. Now is a great time to look back on how Samsung has fared with updates over the past few years. Hint: It's not pretty.

DownToDash, an app from an NYC-based startup, connects students to other students who want to hang out the same way they do. The social networking app has gained increasing popularity since its launch in October 2016 and looks ready to become even more available. The app was founded by Sama Jashnani and Anuja Shah, both recent students themselves.

Augmented and mixed reality developer Arvizio is working on a suite of software solutions for enterprises that will extend HoloLens capabilities as a full-fledged collaboration and conferencing tool. The company will demonstrate its Mixed Reality Studio suite to attendees at the Augmented World Expo, which begins later this month in Santa Clara, California.

And so it begins... CES 2017 is upon us! This is a very exciting time for those who are looking out for the newest innovations and releases from the world of technology. I said this was going to be a fun week, and here we start it with a bang from smartglasses developer Osterhout Design Group (ODG).

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.

If you've been following NextReality, you've surely seen me around, or at least have seen my articles. My name is Jason Odom, aka Subere23, and it's about time for a formal introduction.

Throwaway phones aren't just for seedy criminals and spies—they can be useful for many everyday situations.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

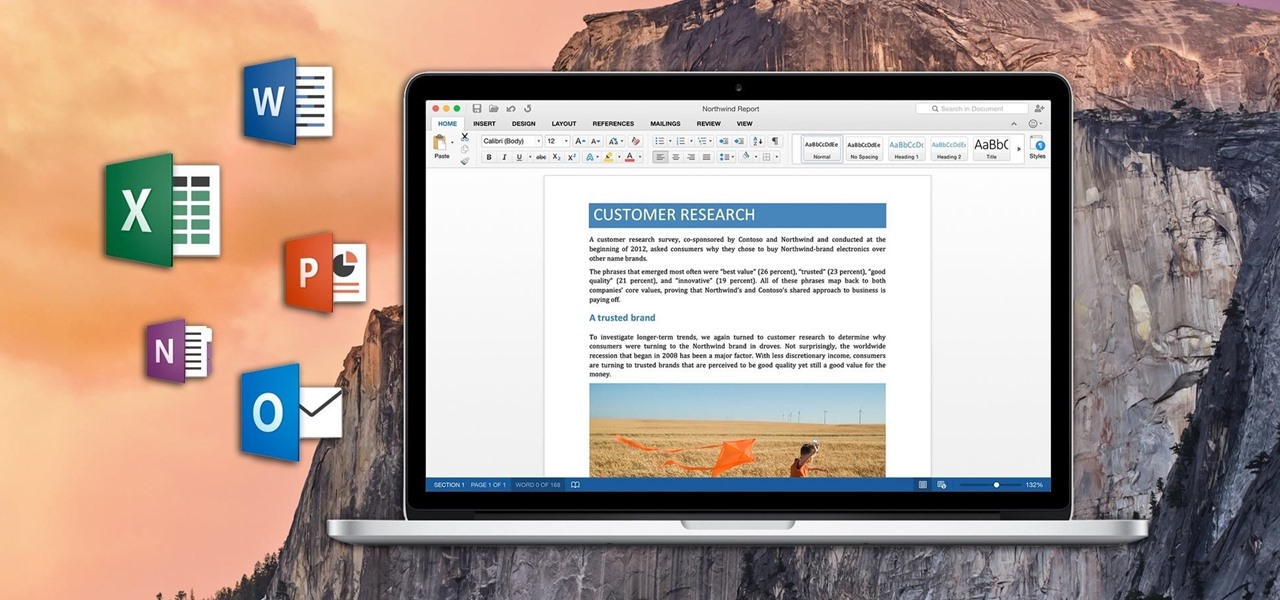
If you've ever attended school or held a job, you're probably well familiar with Microsoft Office, whether you used it or not. It's the most popular office suite available, and has been for some time. Apple does have its own suite of productivity apps (iWork), but Microsoft Office has always been the industry leader for word documents, spreadsheets, and presentations.

As the largest wireless service providers in the United States, AT&T and Verizon Wireless carry some serious clout. Sadly, they use some of this power to heavily modify the Android phones that they offer.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

OSAGYEFO DR. KWAME NKRUMAH (1909-72) Founder and Father of the Nation Osagyefo Dr. Kwame Nkrumah, the first Prime Minister and President of Ghana, stands out not only among the Big Six but also among the greatest statesmen of history. It was he who canalized the discontent of the people of the Gold Coast Colony into the highly organized movement of protest against British rule, and within a relatively short period won political independence for Ghana on March 6, 1957. With Ghana independent, ...

It’s easy to gain a little extra weight in college but there are ways to defy this weight gain trend. It won’t work without will power but you can limit your unhealthy food intake and sneak in some unconventional exercise routines.

The egg is an incredible compact, nutrition, protein and fat all in one prepackaged unit. This video will show you how to boil an egg using a strainer basket in your boiling water to heat steam your eggs as an alternative to regular boiling.

In this video, we learn how to decorate a horse birthday party cake. First, take two 8 inch round cakes and cut out the shapes to make it into a horse. You can find these templates at www.bettycrocker.com. Once you have these cut out, chill the cake again to make sure it's firm. Now, arrange the pieces of cake until it looks like a horse. Now you will apply a chocolate top coat of icing and let set. Once it's set, add another layer of icing to the entire cake. You can now take icing and make ...

You only 'thought' the HoloLens 2 was the most expensive augmented reality device on the market. As with many things tech, Japan is here to up the ante with what may indeed be the most expensive AR-dedicated wearable we've seen—the Canon MREAL S1.

You don't need to work as an executive at Google to understand and appreciate the importance of large-scale data analytics in today's world. Whether you're interested in joining the ranks of a major tech firm or want to improve your company's marketing campaigns through consumer analysis, knowing how to work with large sets of complex data is paramount.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

After facing reports of financial troubles over the past month, Magic Leap came out swinging this week with a big push for the enterprise segment of AR, including a repackaged Magic Leap 1, a suite of enterprise apps, and updates to Lumin OS and its supporting development ecosystem. Oh, and its AR headset managed to win a starring role in the marketing juggernaut for the forthcoming Star Wars movie.

The long wait is over — the best augmented reality device on the planet is finally available.

The idea of squeezing your phone might have sounded a bit out there when it was new, but it's now a hallmark feature on Pixel devices. As useful as it is for summoning the Google Assistant, however, it certainly would be nice to be able pick and choose what action is triggered by squeezing the phone. Well, now you can.

When I first found out about Nreal, back in the spring of 2018, the most interesting thing about the company's story was the founder's background. Chi Xu, the CEO and founder of Nreal, previously worked at Magic Leap as a software engineer.

What does mainstream augmented reality look like? I'm not talking about the stuff you see in concept videos and science fiction films. No. What does it really look like?

Last year's augmented reality investments roundup was impressive. And in 2018, the dollars flowing toward AR haven't decreased, as venture capitalists and strategic investors continue to aggressively fund AR startups at a rapid pace.

In case you hadn't heard, Google is now a legit cell service provider. Google Fi has its pluses and minuses, but the biggest upside is in the pricing. Depending on how much data you typically use, there's a good chance you could save a lot of money without sacrificing coverage by switching to Fi.