Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

There's a whole world of wallpapers out there. Apple always includes a selection of stock wallpapers, some unique to every iPhone model you have. Of course, sometimes, stock wallpapers don't cut it. Sometimes, you want to add your own style to your home screen and lock screen. In these cases, using an app to find the best wallpapers out there can be just what you need.

Microsoft has invested years and countless man-hours in an effort to get their cloud storage service on par with competitors like Dropbox and Google Drive, who have long resided at the top of this market. Their hard work has definitely paid off, as OneDrive (formerly SkyDrive) has finally reached a point in its development where it can stand toe to toe with any comparable service in almost any measurable regard.

So you finally decided to make the switch from iOS to Android, huh? Well first off: welcome to the world of tomorrow. And secondly: good call, mate.

When it comes to smartphones, the biggest complaint voiced by most users is battery life. Sure, it's unrealistic to expect your Android device to run for weeks without a recharge, but many folks struggle to even make it through the day without having to top off their battery.

Hello there, 'Flashers'! Welcome to my 8th Post. This tutorial will explain how to flash Kali NetHunter on OnePlus (Tested) and Nexus Devices (Not Tested-Should work) as a secondary ROM, so that none of your personnel data/ROM gets affected.

The Nexus Player is one of the most robust set-top streaming devices on the market. This is mainly due to the fact that the base software it runs is a direct fork of Android, which is a very powerful operating system itself.

With over a billion monthly active users, it seems that Facebook is nowhere close to being dethroned as the most popular social media service in the world (sorry, Ello). While their stats may be impressive, it doesn't mean that Facebook is as good as it can be.

Many modern Android devices use a display technology called AMOLED. These screens differ from traditional LCD displays in that each pixel emits its own light, so a backlight is not required. Even better, when rendering a black element on the screen, AMOLED displays simply don't light up the associated pixels, meaning virtually no power is used. Since black pixels use little to no power on an AMOLED screen, more black pixels means lower battery consumption.

When it comes to getting your computer and smartphone to work well together, there's no service more robust and capable than AirDroid. For years, it's been the go-to tool for users looking to transfer files between their devices or access contact lists and call logs from their computer.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

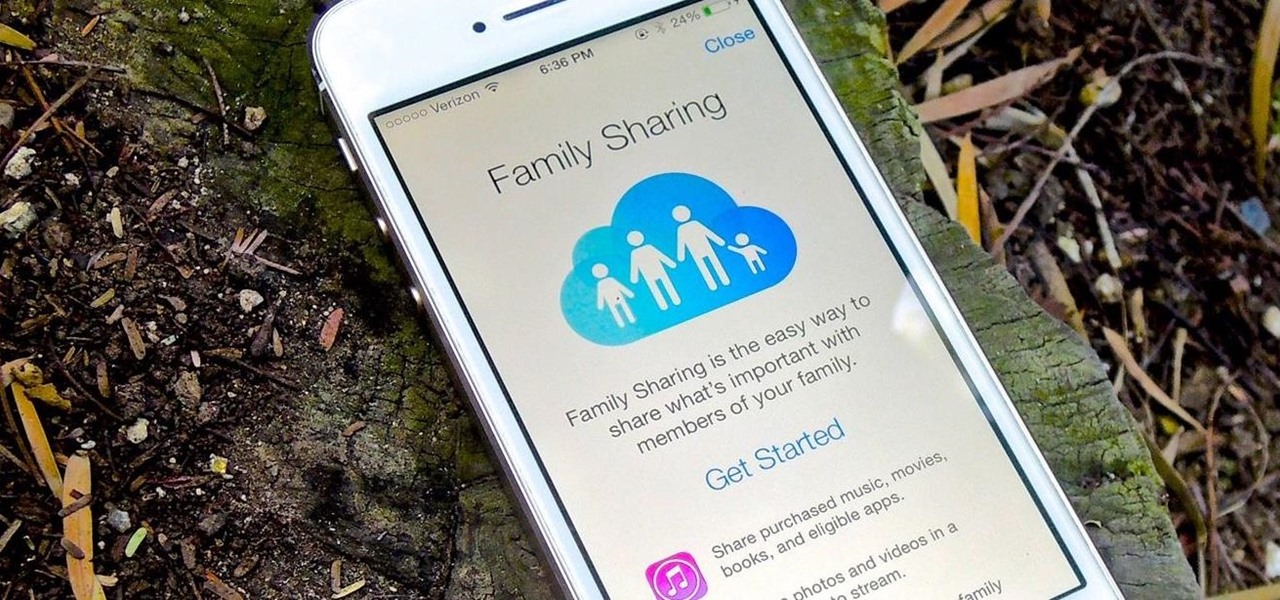
There are a ton of great new features in iOS 8, and one of the most interesting (and perplexing) ones is called "Family Sharing."

The Xposed Framework offers many great customization options for your Galaxy S5. S Health, with its ability to read your heart rate through a built-in monitor, is one of the main selling points of the GS5. Trouble is, the two don't seem to play nice together.

When the Nexus 5 debuted, one of its coolest features was the fact that you could say "OK Google" any time you were on the home screen to launch a Google Voice Search. This feature was ultimately made available for other devices by way of the Google Now Launcher.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Here's a routine that I'm sure all of us smartphone users go through at least several times a day. You notice your Samsung Galaxy S4's notification LED blinking, grab your phone to see what it is, and enter your PIN. Only instead of anything important, you find that it's just some online store enticing you with sales promotions, or some other email that you could have easily done without.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Whenever the word "popup" pops up, I immediately cringe because all I can think about are those obnoxious ads that ruin my everyday browsing experience. But, not all popups are evil.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Not having internet sucks! We do a ton online these days, from working, shopping, studying, and collaborating, to watching fail videos and endlessly clicking through memes.

Google Reader is soon to be no more. Yesterday, the company announced that the service will be shutting down as of July 1, 2013, as part of Google's second "Spring Cleaning."

In order to access blocked videos and websites, you will need to set up a proxy service in the U.S., if you are trying to use Hulu. Go to a list site.

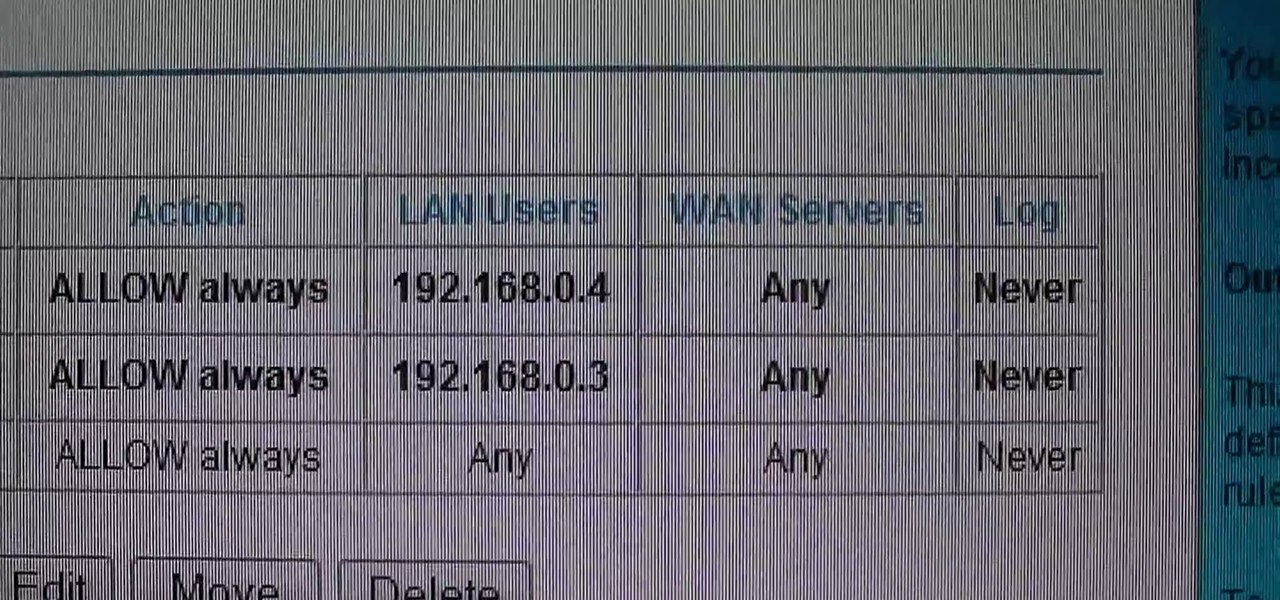
This video shows how to change the NAT type on a PS3. Go to connection settings>network settings>internet connection settings>OK>custom>wired connection>auto detect>manual. Choose an IP address that is different from your router, any other consoles, etc. Click right>automatic>do not use>enable. Press x to save settings, and test your connection. In this example, NAT type is 2. Now go to your PC and open IE. In the address bar, input router IP address, username and password. Go to Firewall Rul...

If you don't have room for a full-scale compost heap, you can always employ the services of some worms. In this handy vermiculture how-to, you'll learn how to build your very own wormery.

With all the documents ready, we need to fill our wallet with money for the travel. This video discusses various ways of filling the pocket. That is how to prepare the money for international travel. Over the years credit cards have been widely used by many travelers, which is safer than carrying cash. In this case we need to contact the credit card provider well in advance and notify them about the travel. Also we need to learn about the various fees applicable to international purchases. Th...

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

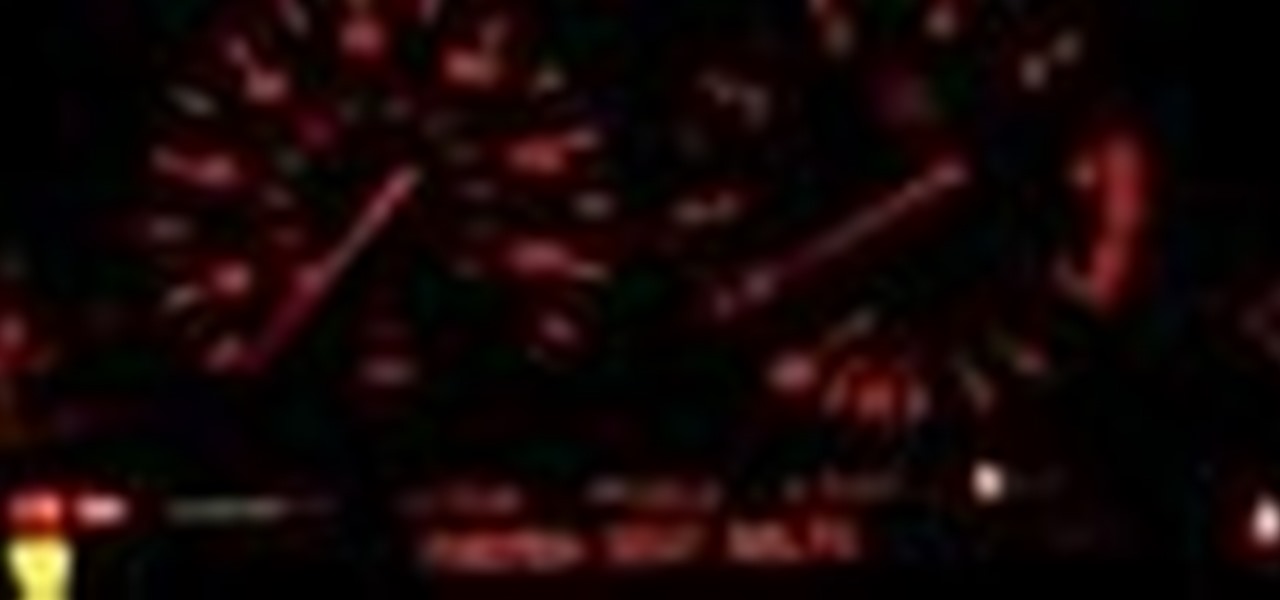
This automotive video tutorial will show you how to test an instrument cluster on a BMW E38 car. IT will show you how to activate an instrument cluster test on a 1995-2001 BMW 7 Series (E38).

This is an intensive one-day overview video tutorial of the fundamental concepts of the Ruby on Rails Web programming framework, presented by the UC Berkeley RAD Lab. The overview consists of six sections of approximately one hour each. Click through the video chapters to go through the Ruby on Rails programming course.

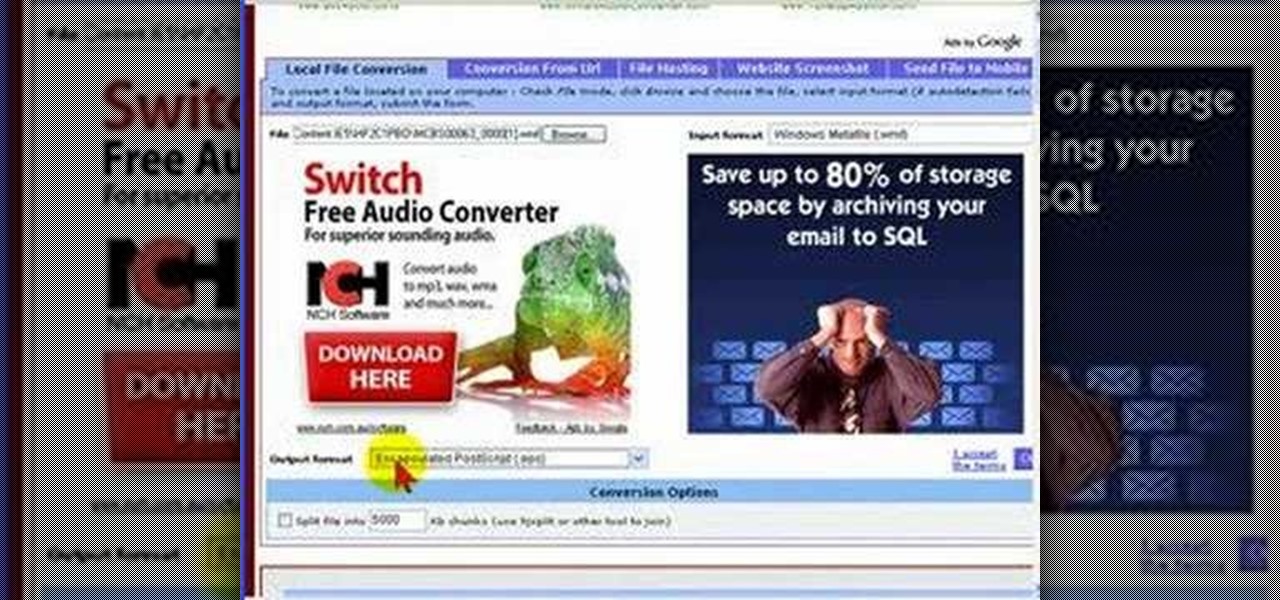
In this video tutorial we look at how to quickly and easily convert a file using the great free service at www.Media-Convert.com

First of all you have to search for a reputed dealer. Then ask him all necessary questions like what sort of lenses shall fit in your camera, what shall be the size of the lens to fit in your camera. If you are going to purchase it online then you have to ask whether the surface of the lens is scratched and marked in any way. Make sure that three is no mould or scratches on the lenses. You can also hold the lens towards the sun or a light source. Do not hold it directly against the sun. Now y...

Everyone who drives should know how to use a car jack in case of a flat tire or blowout. Check your owner's manual to find out where your car jack and spare tire are located. In most cases, they are somewhere in the rear of the car. The video shows us how to use a telescoping jack, though the more common type of jack requires a scissor motion to raise the car and lifts from the side rail. The telescoping jack lifts from the axel and to raise the jack you need to insert the rod into the hole n...

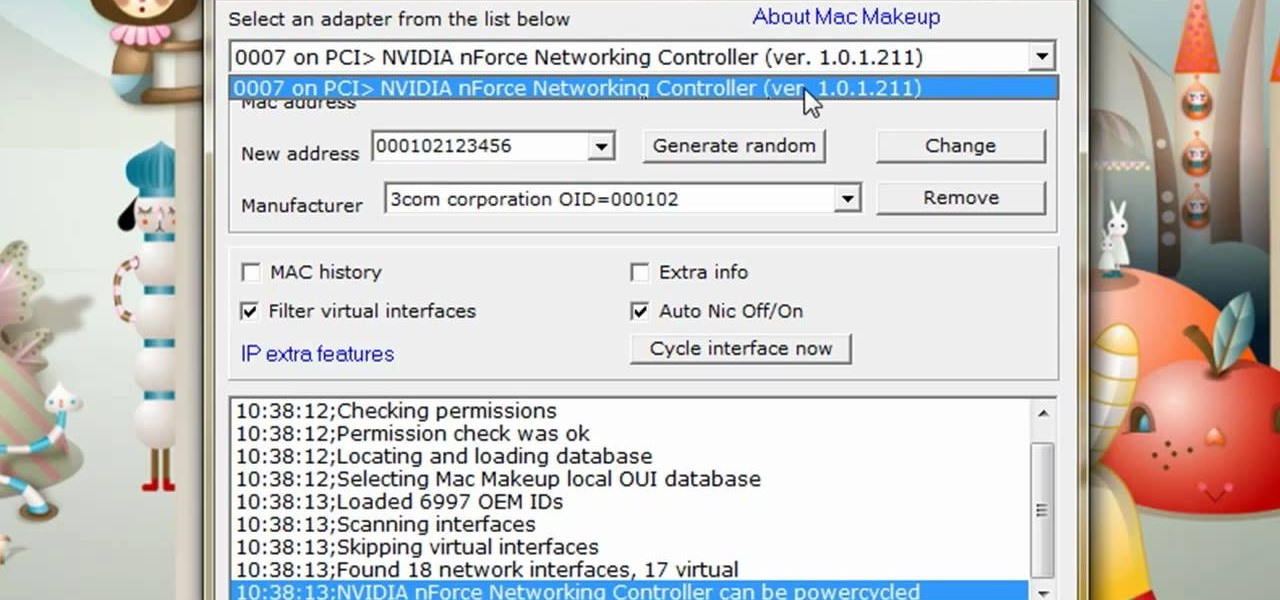
The video is about how to change the IP address. MAC address is the unique identifier a site of the most network adapters. MAC address is used to determine what IP address the computer will have and one way to change the IP address is by changing the MAC address. The method is only applicable for the windows systems and for the MAC systems you need to look at the link provided. In Windows in the start menu, type cmd in the run/search box, which will launch the command window. Type ipconfig/al...

People like Ralphige and The Jerky Boys have elevated prank phone calls to an art. Here’s how you can get in on the fun.

We've all seen the breathtaking, colorful photos of the Eagle, Egg and Cat's Eye Nebulae. You may not recognize them by name, but you've seen them, whether in astronomy textbooks, magazines, websites, album covers, or tee shirts. They are some of the most striking photographs ever taken from the Hubble Space Telescope (HST).