Among the many new changes ushered in by the iPhone 7, only one has the potential to completely change the way you interact with your smartphone—a new 3D Touch-enabled home button. Instead of the mechanical click we've grown accustomed to, your home button will now behave like the rest of the phone's touch screen interface.

Over the years, we've covered many different methods for enabling background playback for YouTube videos on Android, but none have ever been as easy as this: Simply watch the videos with Firefox for Android, and they'll continue playing when you leave the app.

Opioids, or narcotic painkillers, serve as our primary method for alleviating physical distress. They also happen to be a leading cause of death due to their addictive nature. AppliedVR hopes to introduce a safer alternative: virtual reality gaming. They utilize the existing Samsung Gear VR for the hardware, but provides specialized software that offers up a distracting experience that fosters greater pain ignorance.

It just got a whole lot easier to decide whether or not saving $50 on Amazon's new ad- and bloatware-subsidized smartphones is worth the headache of having to see an advertisement on the lock screen every time you wake the device.

Google kicked off I/O 2016 by debuting Assistant, a next-level version of Google Now. While you could search the web by voice before, now you'll be able to have a conversational interaction with Google. In short, it's a smart chat bot.

Facebook Messenger is getting ready to roll out a Snapchat-esque feature that will let users send messages that self-destruct after a certain amount of time, so you'll have an extra level of security when you need to send sensitive financial information or, more likely, risqué texts or images.

One thing you have to love about Google is their sense of humor. From their annual April Fool's Day pranks to the hidden Flappy Bird mini-game in Android to tons of hidden commands in Hangouts, you can just tell that those smart guys in Mountain View still like to have a little bit of fun with their work.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Anyone who paid attention to the Lavabit shutdown had a feeling it was connected to Edward Snowden, the high-profile NSA whistleblower. Ever since the government's case against Lavabit went public in late-2013, people have put two and two together.

This is a nice project that you can continue to work on and modify as you learn more Arduino projects. The Instructable linked below goes through the complete build for the Bluetooth-enabled robot seen in the first half of the video.

Now that Android Auto and Apple CarPlay have finally arrived, the days of clunky in-dash infotainment systems are coming to an end. Instead of using software created by an automotive company to get directions, stream music, or take calls, we can now get the best user experience Silicon Valley has to offer—all while sitting comfortably in the driver's seat.

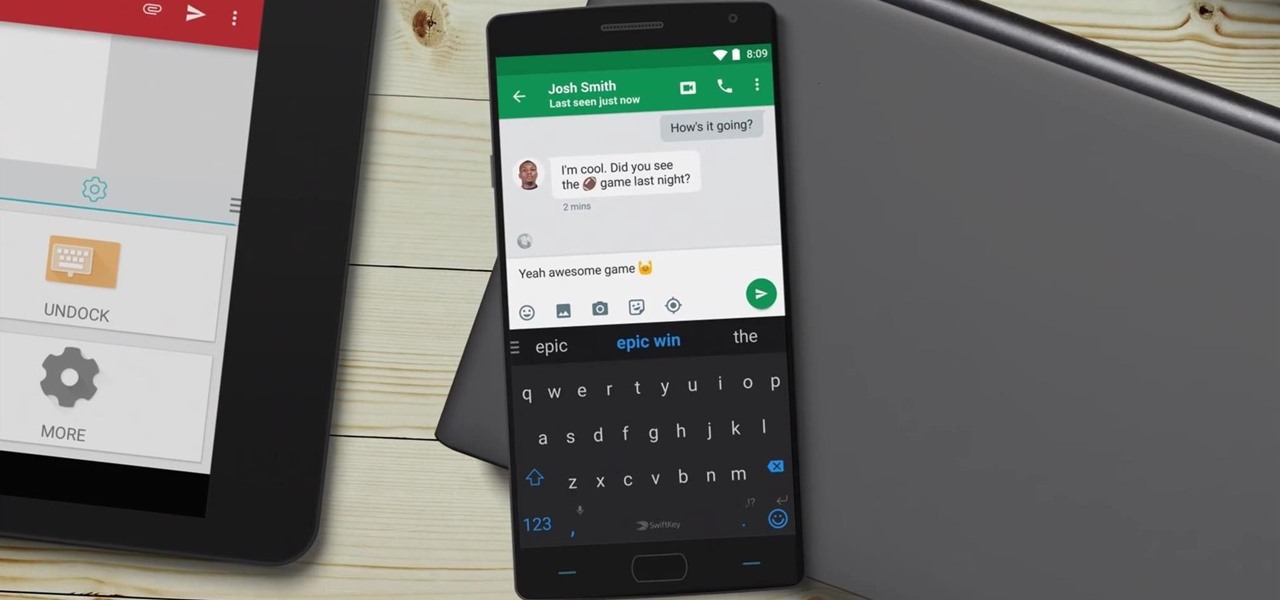
Microsoft announced Wednesday morning that it has entered into an agreement to acquire SwiftKey, makers of the SwiftKey predictive keyboard and its SDK that runs on over 300 million Android and iOS smartphones, for about $250 million.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

Here on nullbyte we always hear mention of hacking being used to shut down power grids or attacking SCADA and other such cyber warlord activities, but ive never seen a TDos post come up.

Taxi drivers and cab companies across the globe are in an uproar over Uber, and for good reason, too—you just can't compete with the low fares and ease of use that Uber brings to the table. The only downside is that the groundbreaking ride share service usually requires a smartphone—but that shouldn't be an issue anymore with one simple tip that I'll outline below.

Hello everyone. I'm Calypsus and i've been around for a while learning from various tutorials, expanding my knowledge and this is one of the best platforms for newbies to sharpen the skills. Today i decided to register myself and contribute to this wonderful community. Since this is my first post, any kind of feedback is appreciated.

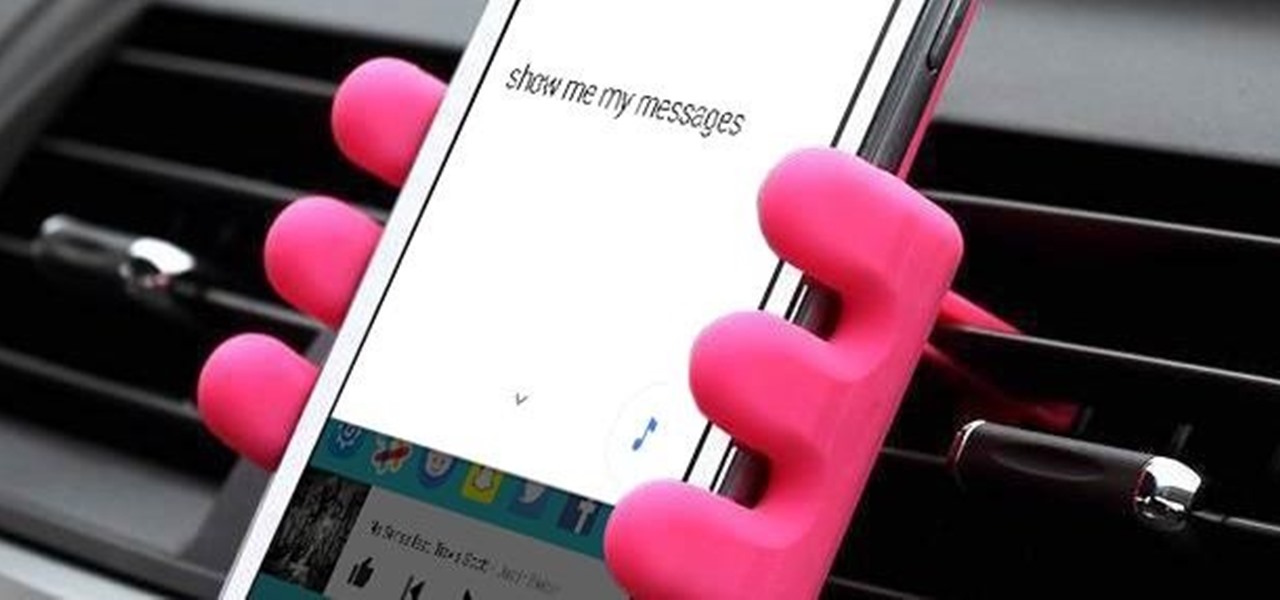
For some time now, iPhone owners have been able to use Siri to listen to and reply to text messages, but that functionality has been lacking on Android. That is, until Google silently rolled out a similar feature for Google Now (thanks to Android Police for the tip).

We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of companies are few and far between in corporate America.

This tutorial is for those who've purchased an account with Private Internet Access to hide your VPN and would like to set it up in Kali. Please note, you can chose to run your PIA service from your Windows computer without configuring it in linux as long as you'll be using a NAT connection. Using a NAT connection will allow your Windows machine and Kali Virtual Machine to use the same IP address, hence if your IP is hidden on one, it will be hidden on the other.

When eyesight deteriorates, either due to illness or advanced age, many people turn to audiobooks as an alternative to reading. With today's technology there is an abundance of services and devices one can use.

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

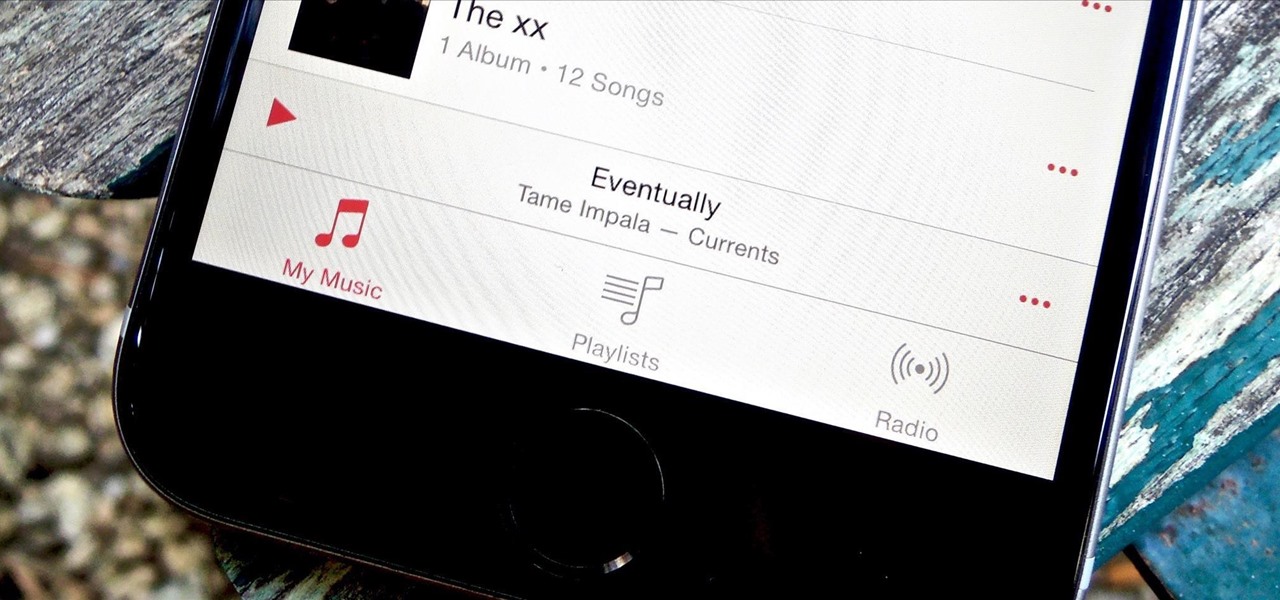
In an attempt to get more people to subscribe to Apple Music, the Music app was completely revamped in the iOS 8.4 update for iPad and iPhone to include new tabs for New, For You, and Connect.

Snapchat has built upon the photo-sharing service it once was to become a money-sending, commercial-shelling, video-messaging giant. They improved their user experience by adding Stories, Geofilters, and even the rarely-used Snapcash feature, but why isn't there something as simple as color filters? Yes, they have filters for black and white, saturated, and sepia, but that's it as far as color goes.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

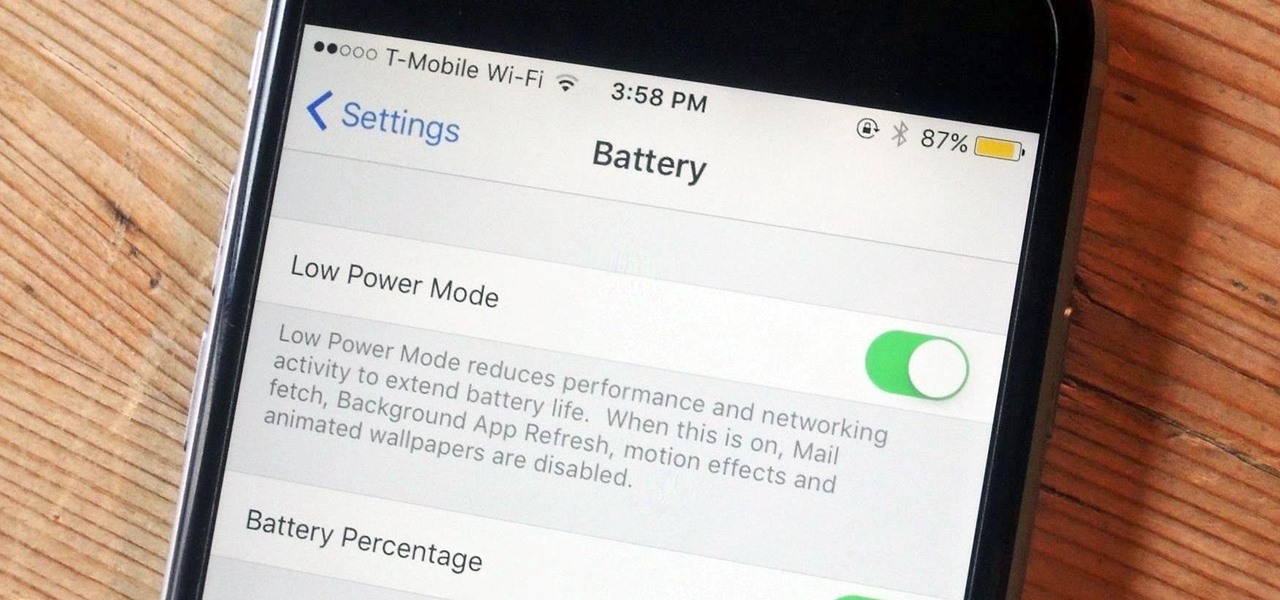
One thing Apple users universally complain about is battery life, whether it's on an iPad, iPhone, or Apple Watch. Apple did include a Battery Usage feature in iOS 8 to help us monitor which apps suck up the most energy, but it's too big a pain to deal with. Now, in iOS 9, there gave us something that actually matters—Low Power Mode.

When you think about it, YouTube may actually have one of the largest music collections on the planet. This is why, at $10 per month, Google's new YouTube Music Key subscription is a solid value for many users, especially with its inclusion of Google Play Music.

Mobile service providers have an uncomfortably strong grip on the Android platform as a whole. For instance, all four U.S. versions of the Galaxy S6 and S6 Edge play their carrier's obnoxious jingle every time they boot up. You don't get any say in the matter—if you buy your phone from one of the big 4, you're a walking audible billboard.

Snapchat developers insist that the app stay true to what its always been: a service for snapping and sharing self-destructing images. This belief is further hit home with their strict 31-character text limit, which some people refuse to abide by. Namely, Snapchatter Shayne Skellett.

Android has a permission that allows apps to draw on top of other apps, but as fun as that may sound, it has mostly been used to create floating multitasking utilities. While these can certainly be useful, it would still be nice if this permission were taken literally and we could actually draw on top of apps.

Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...

It's that time of year again. Each spring, Google likes to have a bit of fun with April Fool's Day. Pranks have ranged from a fake email printing service called Gmail Paper to a search engine for smells. It's all fun and games, but this year, they've taken that mantra rather seriously with a Pac-Man game baked right into Google Maps.

Before you purchased your smartphone or tablet, the device had already embarked on quite a long journey. From product development to manufacturing, your Samsung Galaxy device had already developed a rich history prior to your ownership.

Apple's iOS 8 ushered in a new way of typing with the addition of third-party keyboard compatibility. We've seen everything from keyboards with swipe gestures, customizable themes, different sizes, and even embedded GIFs. Now we've got one for all of you music lovers called AudioShot, which allows for easy sharing of music directly from the keyboard.

I know where I bought my phone, and I definitely know who I'm paying money to every month for cellular service, so there's absolutely no need to see my carrier's name draped all over my device. Fortunately, with Android Lollipop, the carrier label is only present on the lock screen. Nevertheless, that label can keep your phone from feeling just right, so let's go ahead and show you how to get rid of it.

Yes, they're called volume keys, but they can do much more than adjust your volume. With minimal effort, you can do some amazing things with these physical buttons, like secretly record videos, toggle on your flashlight, scroll through pages, control your music, and much more. And while using them to wake your screen is useful, let's take it a step further and show you how to use them to completely unlock your device, even if the screen is off.

These days, using the power button to lock your Android seems a little old-fashioned. Thanks to third-party apps and mods, you could seamlessly lock your device using a double-tap, a swipe, and even gravity, or you could just throw it in your pocket, all of which help prevent additional wear and tear on your power button. Now, we've got another method for you—just shake.

If you've had your Gmail account for awhile, it's probably a cluttered mess thanks to unread messages, out-of-control newsletters, and never-ending email threads. This is one of the main reasons for the creation of Google's streamlined Inbox service, but the adoption rate for it hasn't indicated a huge shift over for most of us yet (partly because it's invite-only still).

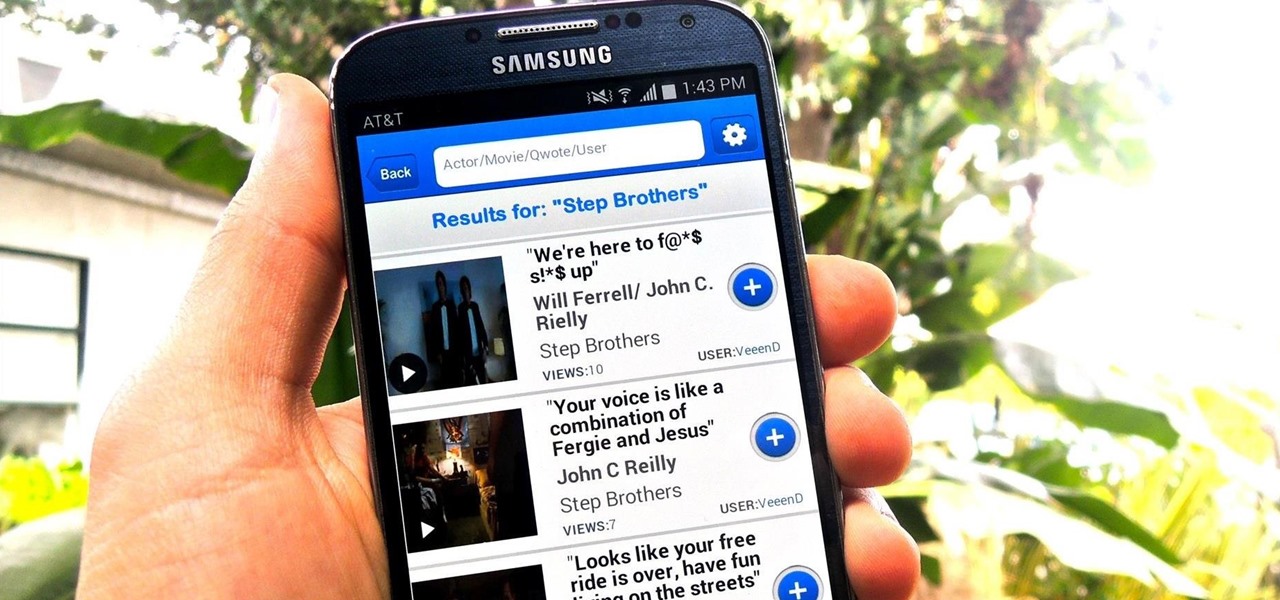
The Oscars are just around the corner, so it's the perfect time to remind people of your favorite movie moments, even if they're not exactly Oscar-worthy. But don't just settle on sending GIFs that don't include any of the fun audio, or resort to scouring YouTube for that one specific movie clip. Instead, take a look at Qwotes, a new mobile app from developer StudyUp.

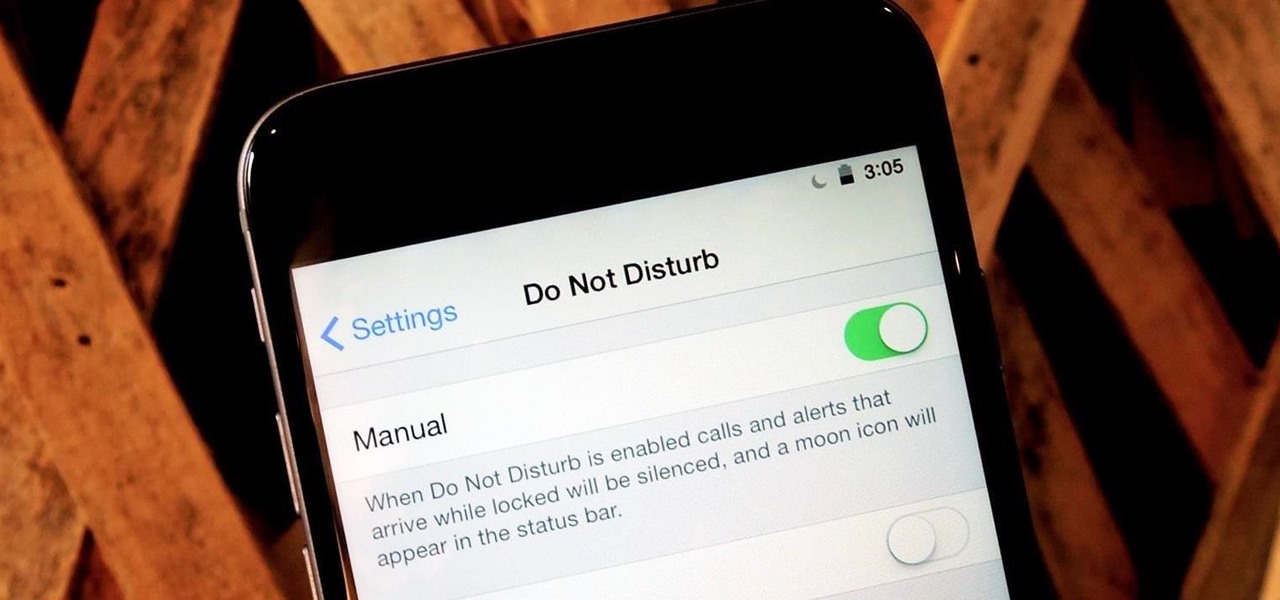
At certain times of the day, like when I finally get home after sitting through aggravating traffic, the last thing I need is the sound of my phone irritating me any further. So, I toggle on the "Do Not Disturb" feature (introduced in iOS 6) on my iPhone and get to enjoy a little peace of mind.