
How To: Winterize your riding lawnmower
This video provides a handy tutorial on how to make your riding mower stand up to the harsh effects of winter.


This video provides a handy tutorial on how to make your riding mower stand up to the harsh effects of winter.

When shooting video on your phone, you have two cameras at your disposal, the rear camera and the selfie camera, and you can switch freely between the two. As for microphones, you may have more than one but, unlike with the cameras, it's not easy to switch between them. Filmic Pro solves this problem by isolating the mics so you can choose the best option for the audio track.

Putting your Galaxy S9 in Immersive Mode lets you truly enjoy the gorgeous display that Samsung is so famous for. You can't have it set on at all times, however, so you'll still have to deal with the status and navigation bars that cut the phone's aspect ratio down to that of a standard phone. But if you're willing to dig a little deeper, there are ways to go full Immersive Mode on your S9 for good.
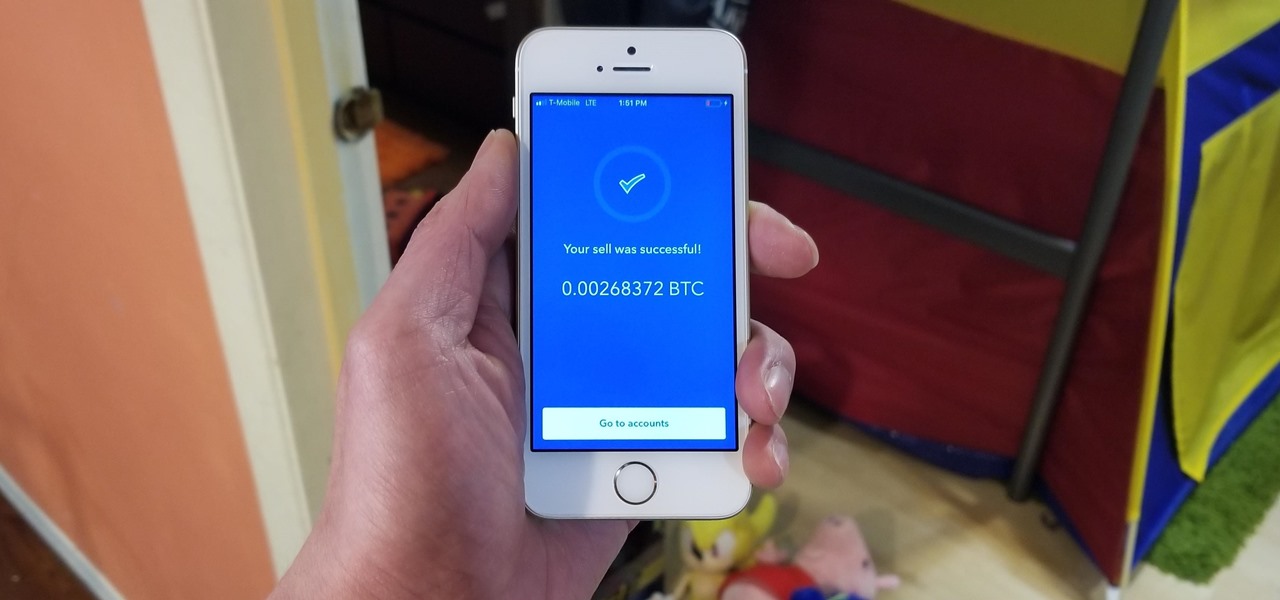
Coinbase has become the most popular mobile wallet app due in large part to its user-friendliness. The app takes the hassle out of buying and selling Bitcoin (BTC), Bitcoin Cash (BCH), Ethereum (ETH), and Litecoin (LTC), letting Android and iPhone users alike trade their favorite cryptocurrency in a few easy steps.

Apple likes to make their products simple. However, sometimes that simplicity leads to a confusing user-experience. Take the Apple TV, for example. How do you turn it off? Just press the power button, right? Sorry, there is no power button. Okay, so it's like an iPhone and has a nondescript button designated as a power button, right? Nope.

The Samsung Galaxy S8's almost bezel-less display is truly a sight to behold, especially when set to Immersive Mode. While transparent when on the home screen, the navigation and status bars on the S8 will often turn opaque depending on what app you're using at the moment. This, in turn, can detract from the overall experience when viewing anything from the S8's display, as the bars along the top and bottom of the screen bump the phone's aspect ratio down to lower levels.

Google switched things up this year by releasing a developer version of Android N far ahead of I/O, but that's not the only convention they've done away with this year. For the first time, Google will accept name suggestions from the public.

When it comes to proper tomato storage, conventional kitchen wisdom (and Alton Brown) state that tomatoes are best stored at room temperature—not in the refrigerator. Supposedly, refrigerated tomatoes develop a mealy texture and lose their flavor if they are exposed to cooler temperatures over time.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

If you've switched ROMs before or flashed quick mods on your Android device, you've probably used TWRP or another custom recovery to install them. But another great purpose for flashing through a recovery is to install your own custom .zip file filled with everything a fresh ROM needs—namely, all your apps.

This Video will Show you how to Prepare Yarn before you do your Yarn Wraps, Braids, Faux Locs....etc
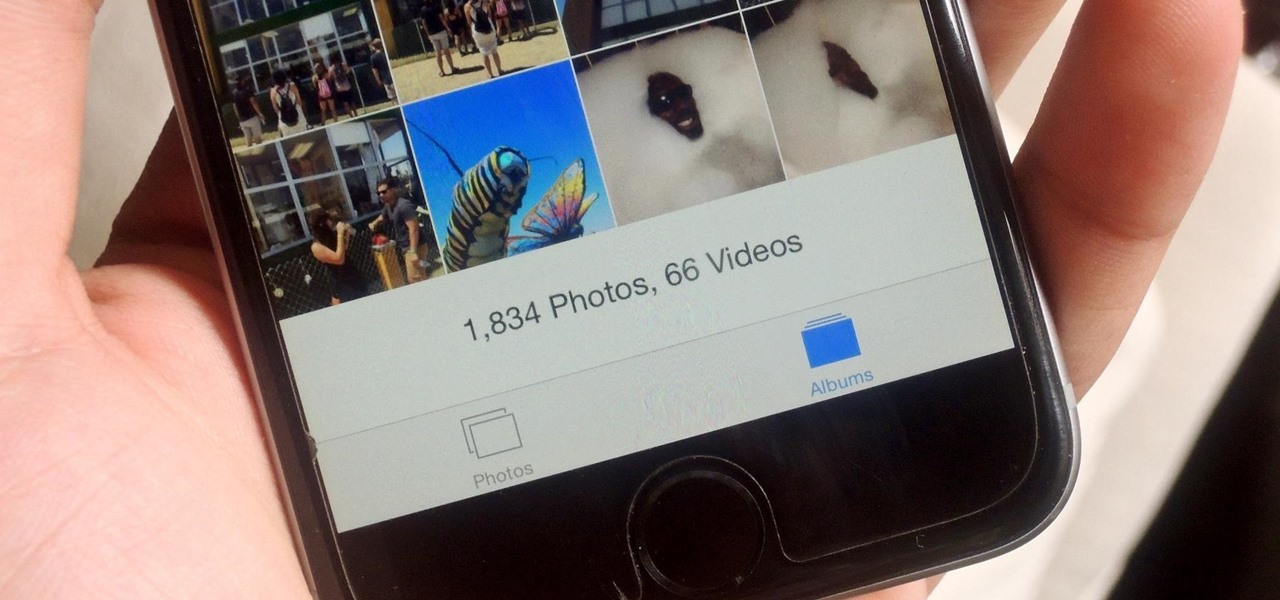
If you have a ton of photos and videos on your iPhone, backing up to iCloud is probably a no-go since it only provides 5 GB of free storage. Yes, you can buy more storage, but who wants to do that? And what happens if you run out of storage, stop backing up, and your phone gets lost, stolen, or damaged.

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

When you first receive bObi, the battery is not plugged in. Luckily all you need is a Phillips head screwdriver to install it before bObi starts working for you.

Icebox cakes are some of the most satisfying, easy desserts to put together. This version made out of ice cream sandwiches takes the cake, literally, because the layers are almost pre-made for you. Simple and pretty when cut and served, it will be love at your first creamy bite. Depending on whether you want a layer of chocolate crunchies in your ice cream sandwich cake or not, this could be either a two-ingredient ice cream cake or a four-ingredient one. If you don't need the crunchy layer, ...
These days, most of the hardware components in smartphones evolve at a breakneck pace. Batteries gain capacity while decreasing in size, displays continue to get sharper as graphics rendering steadily improves, and processors clock higher speeds at every generation.

Lately, it seems, that we live in a two-dimensional world. With smart phones and tablets constantly at our fingertips, it always seems as if we are looking into a screen.

Video: . How to Dye Weave Extensions Easy!!

Video: . What You Need

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Video: . Steel wool fire Photography

If you want to convince your friends that money is not an issue, then you can just burn it for real like Walter White. But if you don't really want to destroy your hard-earned cash, this burn trick is perfect for you. It just takes some basic chemistry and a few materials, such as salt, water, alcohol, tongs, and a source of fire. And of course—money.

You love your hooded sweatshirt but starting to feel like a weak person is strangling you all day long? With a quick snip with the scissors you can have a perfectly fitting sweatshirt and never have to worry about unnecessary discomfort again.
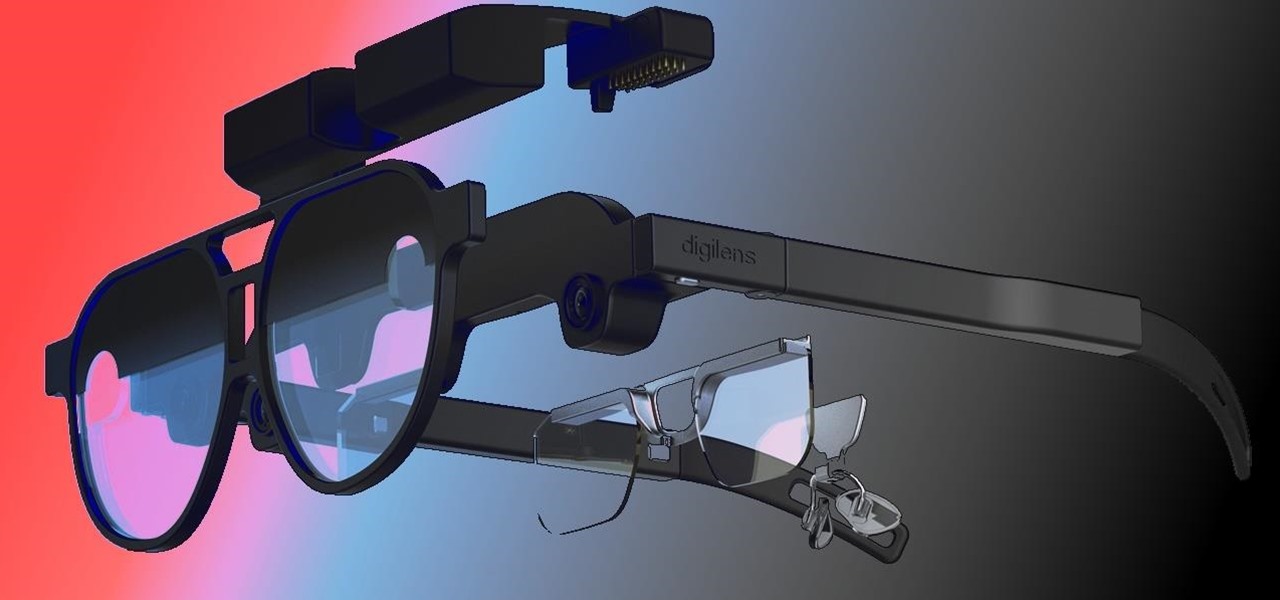
When it comes to the future of AR smartglasses, DigiLens has one word for you. Just one word. Are you listening? Plastics.

Since Motorola engineer Bill Smith invented Six Sigma in 1986, corporations around the world have employed it to eliminate costs and process cycle time while increasing profits and customer satisfaction. These techniques and tools for process improvement were invaluable to famed CEO Jack Welch, who used them to redefine General Electric's business strategy in 1995.

Invented by Motorola engineer Bill Smith in 1986, Six Sigma's methodology defines a series of steps with specific value targets. These targets can be used, for example, to eliminate costs and process cycle time while increasing profits and customer satisfaction.

Google has started to release a Go line of Android apps. These apps offer a minimalistic version of their major app counterpart. So far, we have Go versions of Maps, Photos, Gmail, and more. Who are these apps for and why would you want to use them? Here's a quick overview of Google Photos and Gallery Go.

If you're concerned about someone accessing your OneDrive files, you may want to upgrade your protection by enabling fingerprint or Face ID unlocking. Your sensitive information deserves to be protected, and now you can do so easily. Worry no longer — if you need to let someone else use your phone, with a password-protected OneDrive, sneaky file grabbers will be out of luck.

Sticky notes and the refrigerator go perfectly together, like chocolate and peanut butter. They're particularly popular among families with young kids, so they've been a key part of our personal lives for many years now. But what if you could turn those sticky notes into a digital format? Now you can.
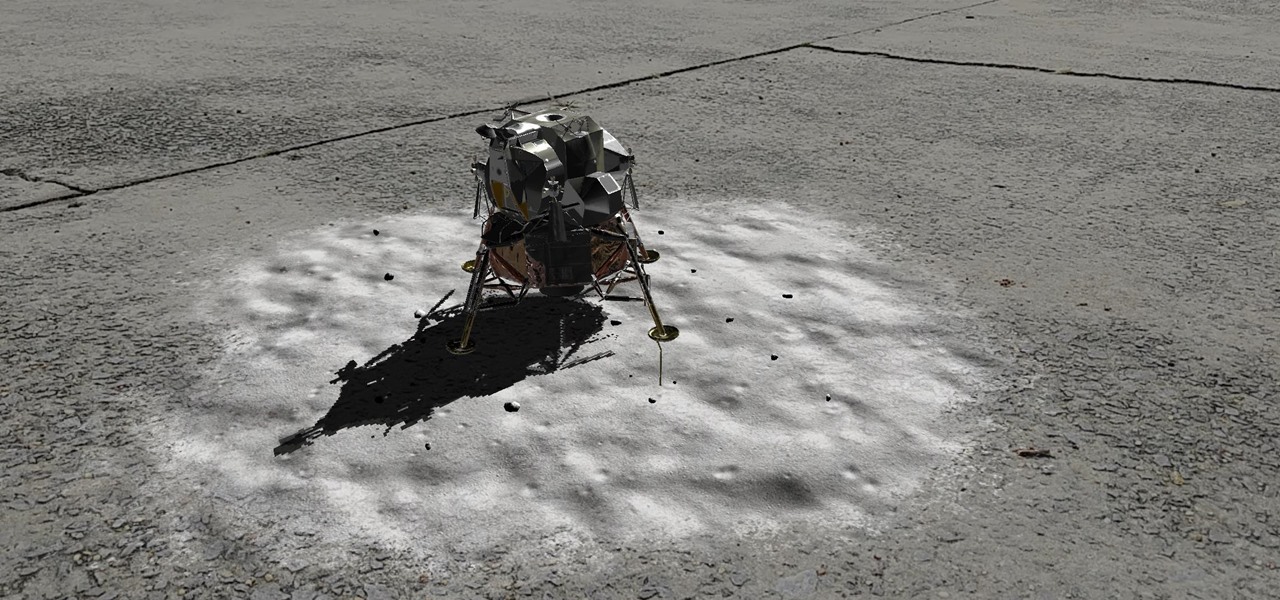
Unless you've been hiding under a (moon) rock for the past month, you already know that Saturday, July 20 is the 50th anniversary of NASA's Apollo 11 lunar landing.

While a viable version of consumer-grade smartglasses has yet to find mainstream success, two more contenders emerged this week, as Vuzix confirmed that a leak of a fashion-forward design is legitmate and Vivo introduced tethered smartglasses designed to pair with its new 5G smartphone.

As Microsoft continues to bask in the glow of its HoloLens 2 unveiling and begins ramping up the hype to launch, Nreal and Vuzix are carving out their own niches in the AR hardware landscape.
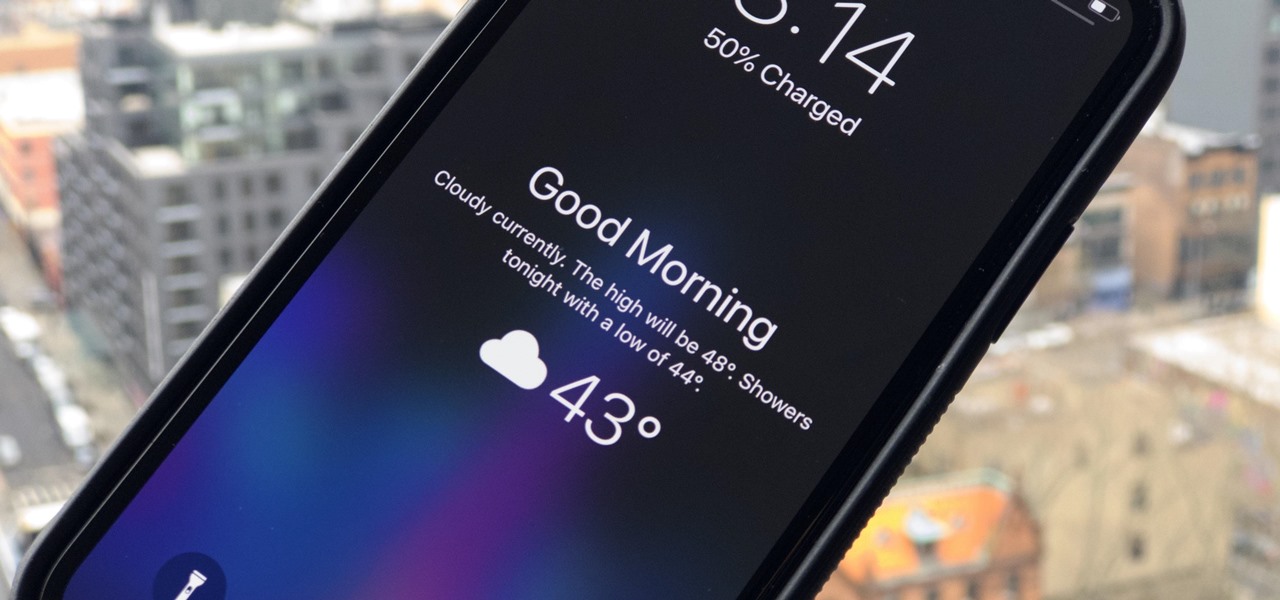
I'm not a morning person, so getting a "Good Morning" message on my iPhone when I wake up makes me want to toss it across the room. If you feel the same way about this morning greeting, there's an easy way to stop it from showing up on your lock screen. This also applies if your "Good Morning" is actually "Good Afternoon" or "Good Evening," depending on your sleep schedule.
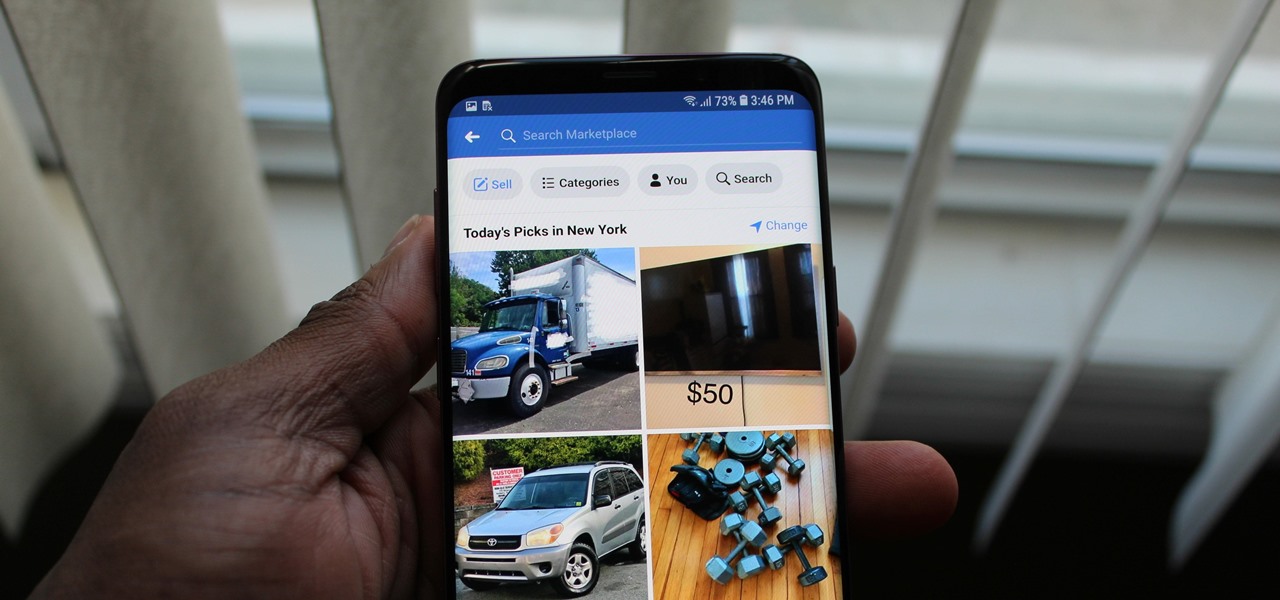
While many of Facebook's tools are well received as they enhance the experience, one which is often complained about is the Marketplace. The Craigslist-like feature which offers a way to facilitate transactions between users can be a little overbearing with its alerts. However, you can change that.

This week, inside sources divulged details of how Apple nearly acquired Leap Motion, twice. Otherwise, companies offering or working on augmented reality technology had more successes than failures to talk about.

A week after the L.E.A.P. Conference, our cup of Magic Leap news continues to floweth over, with the company's content chief giving us some insight into the company's strategy, and Twilio sharing what its virtual chat app looks like.
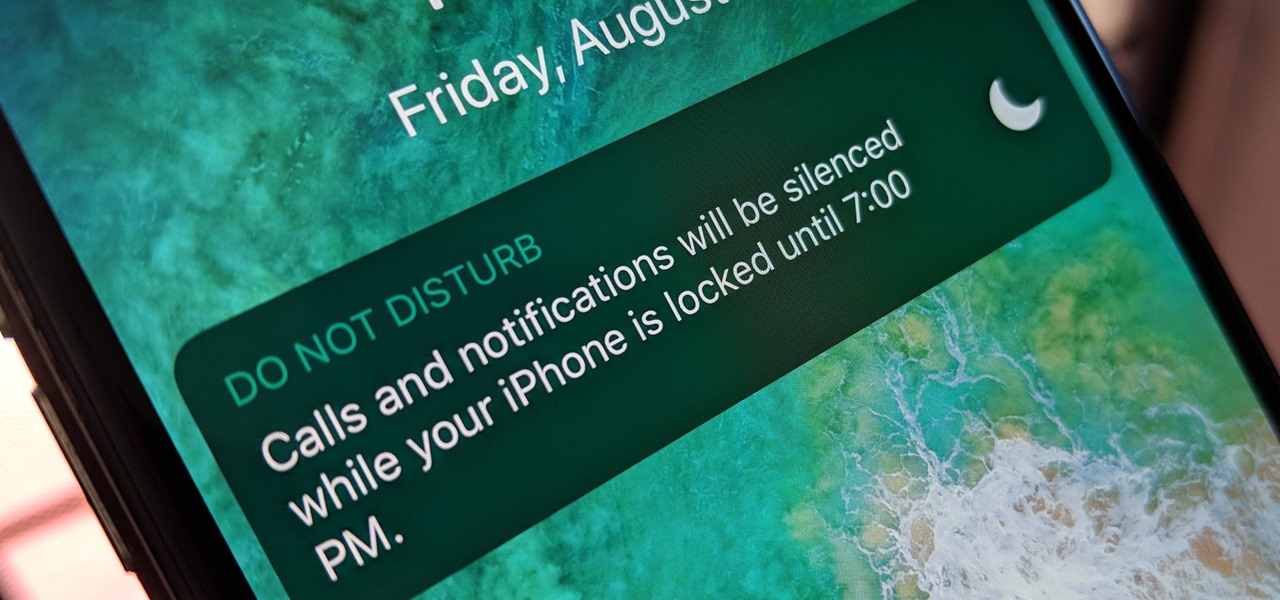
Included with iOS 12 is an easier-to-use Do Not Disturb mode. Not only is there a new Bedtime Mode that makes waking up less annoying, but also new ways to quickly launch the DND temporarily. One example is having the ability to set Do Not Disturb based on a time of day — specifically, morning or evening.
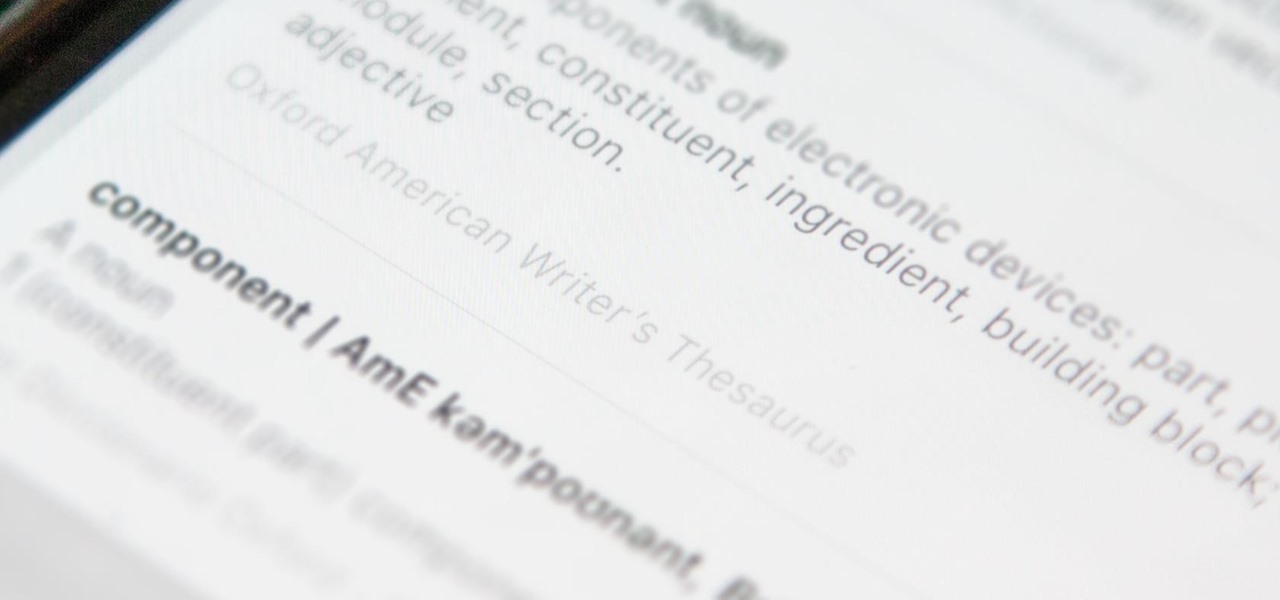
One gem that Apple added with iOS 12 is the perfect companion for the dictionary that's already available with the "Look Up" tool. I say gem because it's taken a backseat to all of the other new iOS 12 features, but it shouldn't, because a thesaurus is like the phloem to a dictionary's xylem, making it hard to believe that Apple didn't include this synonym finder from the start.

Mozilla's Firefox has always been a highly praised internet browser. Since it's open-source, users know what they're getting without any secrecy. It's got plenty of features that are unmatched by any of its competitors on mobile. However, speed and performance have always been a pain point for Firefox, but Mozilla went back to the drawing board to solve this problem with the release of Firefox Quantum.
Most of the free apps you'll find on the Play Store have ads. These ads are personalized — in other words, they're for products and services Google believes you might be interested in. The way Google knows about your interests is by collecting data from your smartphone, including your location and app usage. While personalized ads have their advantages, the collection of data is unsettling.