After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

A tethered version of the Vuzix M300 smart glasses, developed to pair with wearable computers from Toshiba Corporation, is expected to be available by the first quarter 2018, if not sooner.

The de Blasio Administration of New York City has announced that the NYU Tandon School of Engineering will be hosting the country's first publicly funded VR/AR facility.

Former Google employee Tristan Harris claims there's an easy way to combat phone addiction without installing any new software. By enabling grayscale on your phone, checking your apps and notifications will be less appealing and thus stop you from obsessively checking your phone.

The world of investment and finance can be labyrinthine in its very nature — and even more complicated in regards to augmented and mixed reality. While these new emergent technologies are teeming with explosive levels of unrealized potential, there's still a big layer of uncertainty in terms of return — but these investors aren't afraid to take the leap.

Forget 3D movies. Warner Bros.' newest patent shows off designs for a mixed reality movie-going experience that will leave other theater-going experiences in the dust ... all in the comfort of your own home.

General Motors Co. (GM) is set to expand their fleet of driverless cars in San Francisco, Detroit, and Scottsdale, according to documents filed by the company.

We love a refreshing glass of wine in the summertime, but who doesn't, right? More often than not, we favor a rosé or a light red, depending upon the meal, but when the sun is setting and the evenings are warm, chilled wine is the way to go.

Apple is planning to completely overhaul its Apple Music streaming service this summer, and is expected to unveil the changes at its Worldwide Developers Conference in June, according to reports from Bloomberg and 9to5Mac.

Welcome back, my novice hackers! You have probably heard of the Panama Papers hack by now. This was a hack of the servers at Mossack Fonseca, a major law firm in Panama. This law firm specializes in assisting the rich and powerful to hide their wealth from taxes and scrutiny by creating tax havens overseas.

As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

A few months ago, my friend Sarah appeared at a party bearing homemade liqueurs—amaretto, hazelnut (e.g. Frangelico), and vanilla liqueurs, to be exact. Her cool factor, which was already quite high, jumped up a few more notches—as did the overall energy of the party. (And that's why we call her 'Game Time.')

So, you want to become anonymous? well let me give you everything I know (or at least most of it) to you.

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

Ah, the joys of bottomless brunch. Paying a flat rate for endless mimosas while having a long gossip over eggs Benedict is exactly how many of us love to spend our Saturdays. However, in practice, this isn't the sophisticated affair we all like to imagine. After refill number four we sway in our chair, doze off into our porridge, and end up tipping 50% because math is too hard. In short, not a very successful brunch.

Welcome back, my rookie hackers! As most of you know, Mr. Robot is probably the best hacker TV show ever! This is a great show about a cyber security engineer who is being enticed to hack the very corporation he's being paid to protect. This show is so good, I began a series to demonstrate how to do the hacks he uses in the show.

This easy "recipe" requires just two ingredients: popcorn and caramel bits. Caramel bits are made for melting, and they take all the work out of making caramel-based anything. If you've ever made caramel before, the result is delicious, but it's often hot and sticky work—in most cases.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

Tuesday has long been considered the best day to save money on a plane ticket. Airlines typically announce new deals on Monday, so by Tuesday, all other airlines have matched their competitor's lowest fares. It's a tip that I learned at a young age from my father and was solidified by countless others who swore by it. Well, it turns out that we were all wrong.

Just like Leslie Knope, I love waffles. Unlike that imaginary character, I don't require that my waffles come from JJ's Diner. I have a deep affinity for frozen waffles as well as the homemade ones. They're so convenient! A few moments in the toaster, and you have a great foundation for a sweet or savory topping, or just a big fat slab of butter and a little syrup. Turns out there's a great big world of frozen waffle innovation out there that I had never dreamed existed. And remember, frozen ...

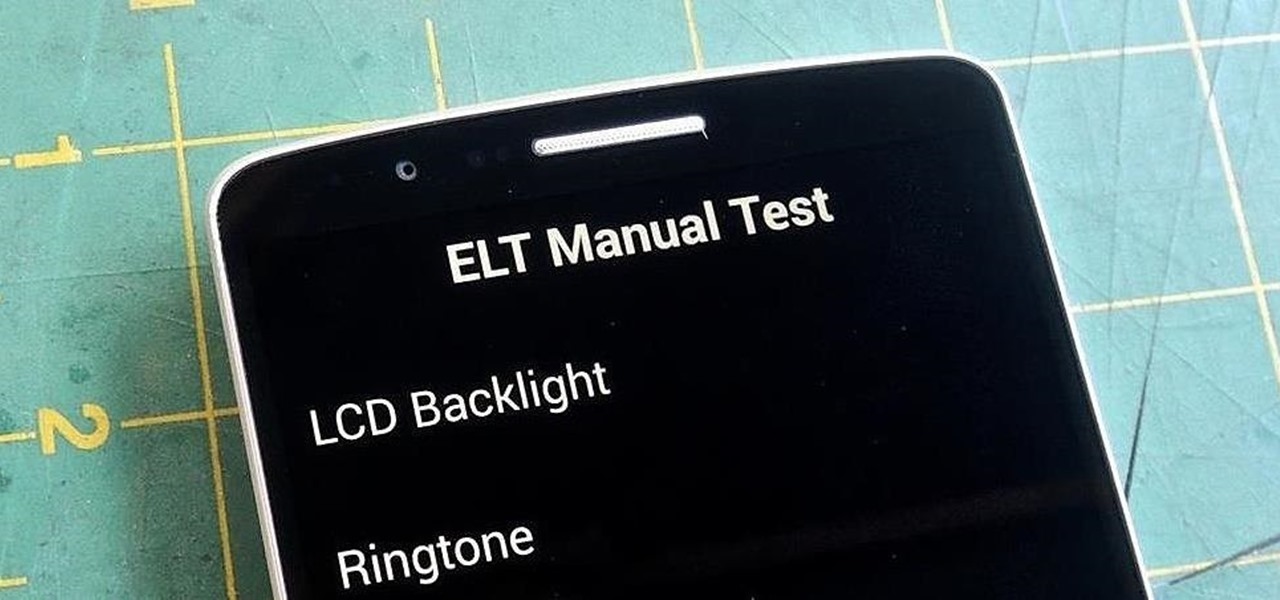
If you notice any issues with your LG G3, pinpointing the culprit can be an arduous task. It could be a hardware issue, a resource-heavy app, or a bloatware-infested operating system.

If you're a Febreze fanatic, you're well aware that the "odor eliminator" can be pretty pricey, and that's reason enough to stop buying it.

Usain Bolt ran 100 meters in 9.58 seconds, an insane record-breaking time that might not ever get beat. As fast as that is, wouldn't it feel like a travesty if your Samsung Galaxy S3 took that long to open up Wikipedia?

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

BitTorrent—corporations hate it with a passion, but the people love it. The notorious file-sharing protocol was responsible for 36.8% of all upstream Internet traffic last year, as well as 10.3% of all traffic.

I'm not admitting to anything, but let's be honest, most of us download content on the Web from time to time. With copyright holders laying down the law more and more often, it can't hurt to do so with caution. And even if you aren't downloading copyrighted material, you still don't want companies snooping in on your online activities. So just how do you protect yourself when torrenting? Avoid "Open Communities"

Love chess, but hate having to stop in the middle of a game when you don't have time to finish? This DIY vertical chess set made by Redditor pigthunder will ensure you never have to abandon a game again. It hangs on the wall, so you can pick up where you left off anytime. Here's how to make your own.

'Loose Change' is cool secondary quest in Dragon Age 2 that varies depending on whether you chose to be a smuggler or a mercenary when you enter Kirkwall. This video will walk you thorough the mercenary version of the quest, allowing you to, in fact, tie up your loose ends.

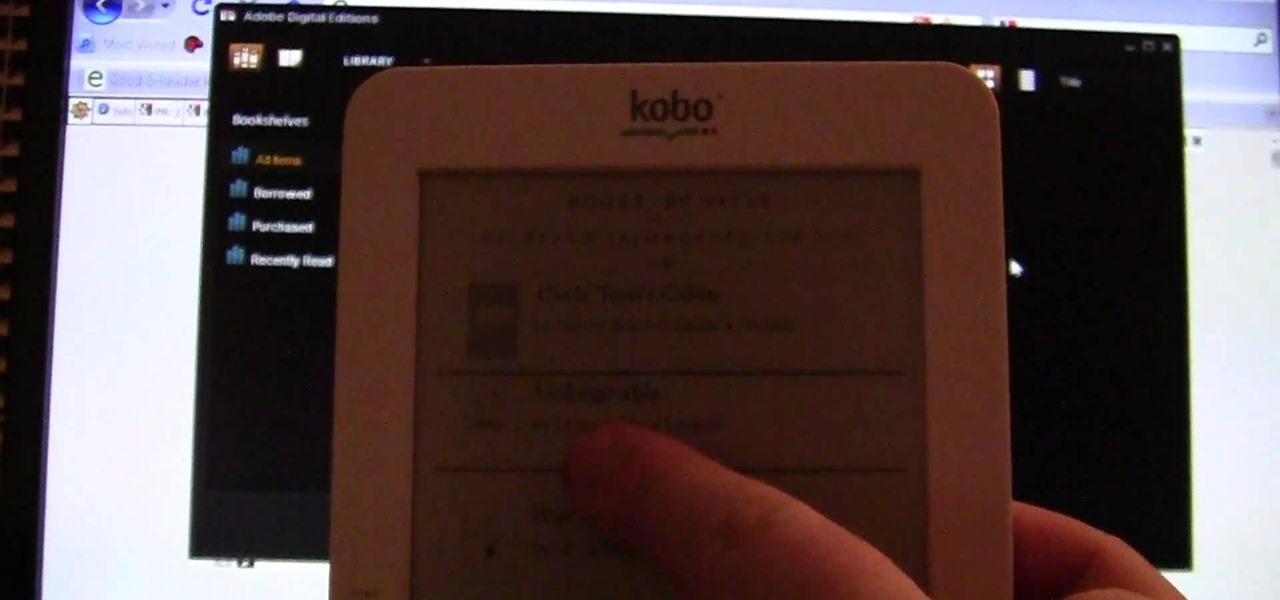
Through Thursday, January 19th, Borders is offering the Kobo Wireless eReader for $99 with coupon—that's $40 off its typical retail price of $139! Though the Kobo Wireless eReader comes preloaded with 100 out-of-copyright classics, new users will nevertheless be interested in filling their new eReaders with their own books.

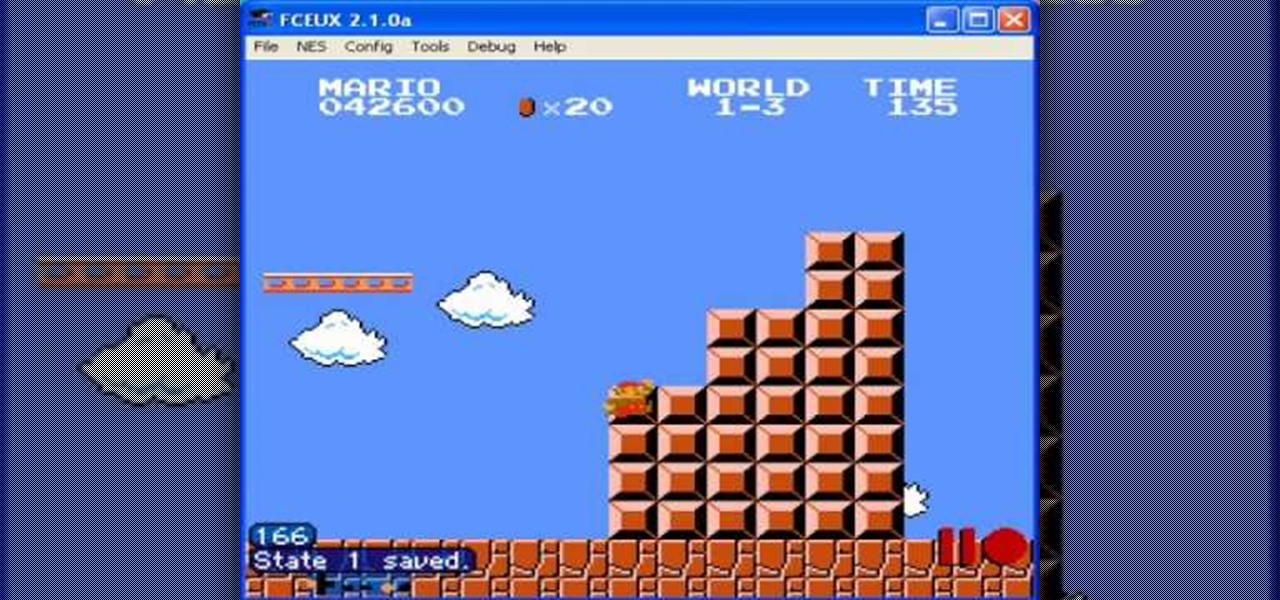
The flagpoles at the end of each level in Super Mario Bros are rewarding when you're playing the game, but if you're setting up a TAS they suddenly become infuriating wastes of time. This video will show you how to TAS skip the flagpoles, which should improve your time substantially.

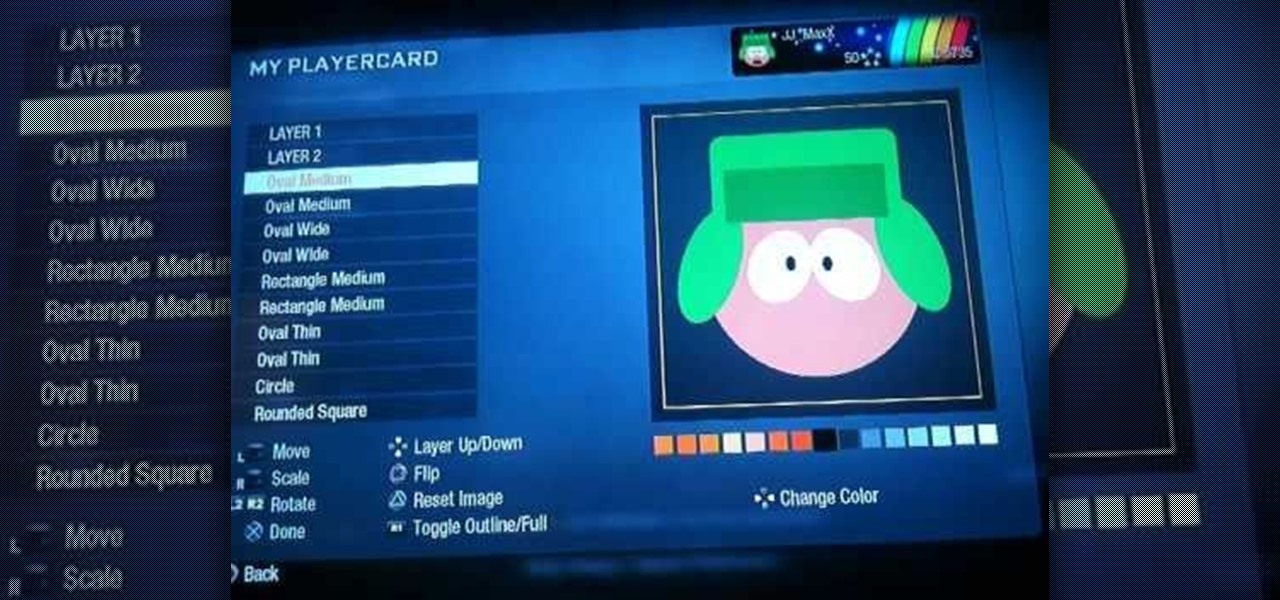
Forget the callsigns and titles from previous Call of Duty video games, Black Ops gives you something new to play with— playercards. Playercards allow you to create virtually any emblem you can possible think of because they're fully customizable, and emblem images can be colored, moved, rotated, flipped, resized and stacked on top of each other, with up to 12 emblem images layered at once. And if you're making Kyle Broflovski from South Park your playercard emblem, you'll need all 12 layers!

The hidden blade that Altair uses to murder his victims in Assassin's Creed is a great costume piece, and if you don't mind working with metal then you should be able to use the instructions in this video to make a really cool one.

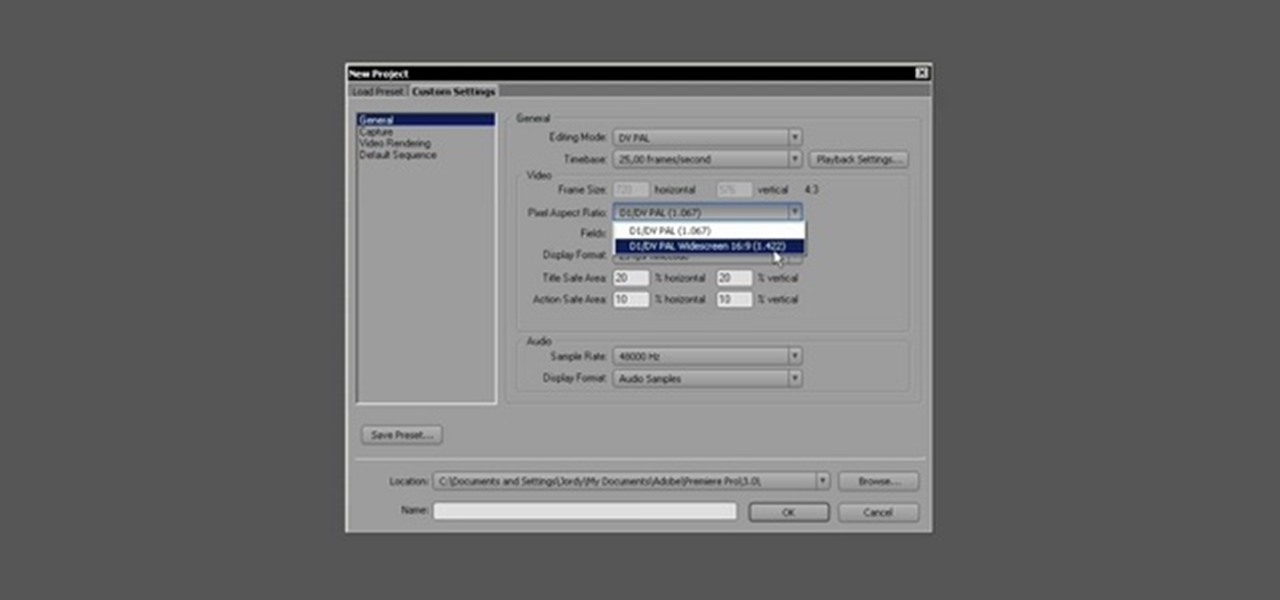
For a new user, Adobe Premier Pro can be overwhelming. There's just so much you can do! So, a little guidance, or shall we say "basic training," is what you'll need to get started editing your own home video or professional film. This five-part series is your basic training, taught by Jordy Vandeput, showing you the basic, need-to-know stuff in Premiere Pro CS3.

The personal computer is a strange and powerful entity, capable of bringing great joy. Just as often, you probably want to chuck the damn thing at the wall because it doesn't work right. If you want to pull a prank on a friend that will really upset them, messing with their computer is one of the best ways to do it. This hilarious video will show you how to do three great PC pranks quickly and easily, including changing the contrast on the monitor and pretending to edit websites using Javascr...

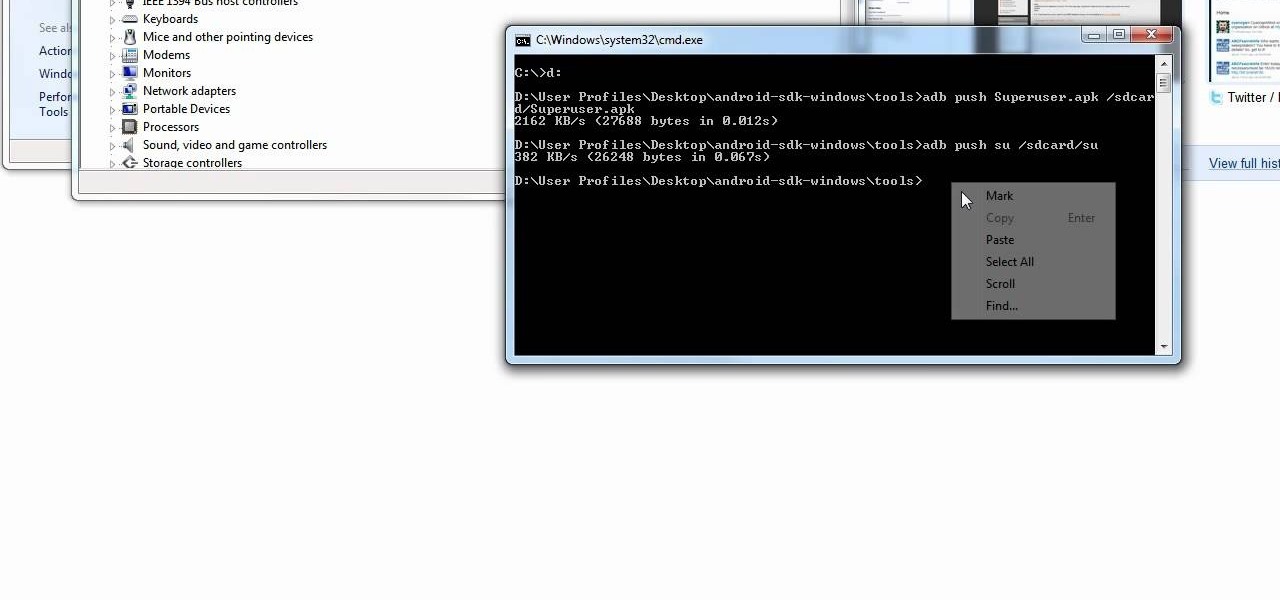
Yes, the Droid X from Motorola can be rooted, and yes, you can do it at home. Just make sure you follow the directions precisely. If you succeed, you'll have a completely rooted smartphone. eFuse doesn't matter. If you want to expand your options on Verizon Wireless's Droid X, then you just have to take a chance… use this video in conjunction with the links and description below.

In this tutorial, we learn how to create a website with external CSS and HTML. Start off by managing your site like usual, then create a new HTML document and new CSS document. Now, name both of these to what you would like, then link them both together by linking the CSS in your HTML document. Now, make a container div, which is what will center your main document. Change your different settings so your div will be exactly how you want it to be. Next, make a banner for your page and set the ...

If you picked up a new Xbox 360 Slim, the first thing you're going to want to do is transfer all your old saved game data from your old Xbox 360 to the new internal hard drive in the Slim 360.

Not every nurse can get an IV every time, that's why it's important to stay in practice for the proper technique used for inserting a peripheral IV. This is a common medical procedure that all fields related to medicine should know. Even the soldiers in the military are taught how to insert an IV — every soldiers, not just the medics.

One of the hardest things a man can go through in life is a trip to the hospital, especially when he knows he's going to need a catheter. It's every man's worst fear. But for a nurse, it's necessary knowledge. Learning the male urinary catheterization procedure hands-on is difficult due to the urgency involved in patient care, so this video aims to prepare nurses so they can learn and stay fluent with the proper urinary catheterization technique of a male patient.

In many situations, learning proper medical procedures is difficult due to the urgency involved in patient care, so this video aims to prepare nurses so they can learn and stay fluent with the proper urinary catheterization of a female patient.