
How To: Teach a dog to shake hands
From housebreaking to traveling, crate training a puppy or dog can have long-term rewards for both owners and pets. Watch this how to video to learn how to teach a dog to shake hands.


From housebreaking to traveling, crate training a puppy or dog can have long-term rewards for both owners and pets. Watch this how to video to learn how to teach a dog to shake hands.

Oftentimes a friend will send you a PDF, MP3 or some other type of document such as a spreadsheet. When you open the file, an application opens. But sometimes it's not the application you wanted to associate with that file. In this video tutorial, you'll learn how to define which programs open what sorts of files. For more, and to learn how to set filetype application defaults in Mac OS X, watch this video tutorial.
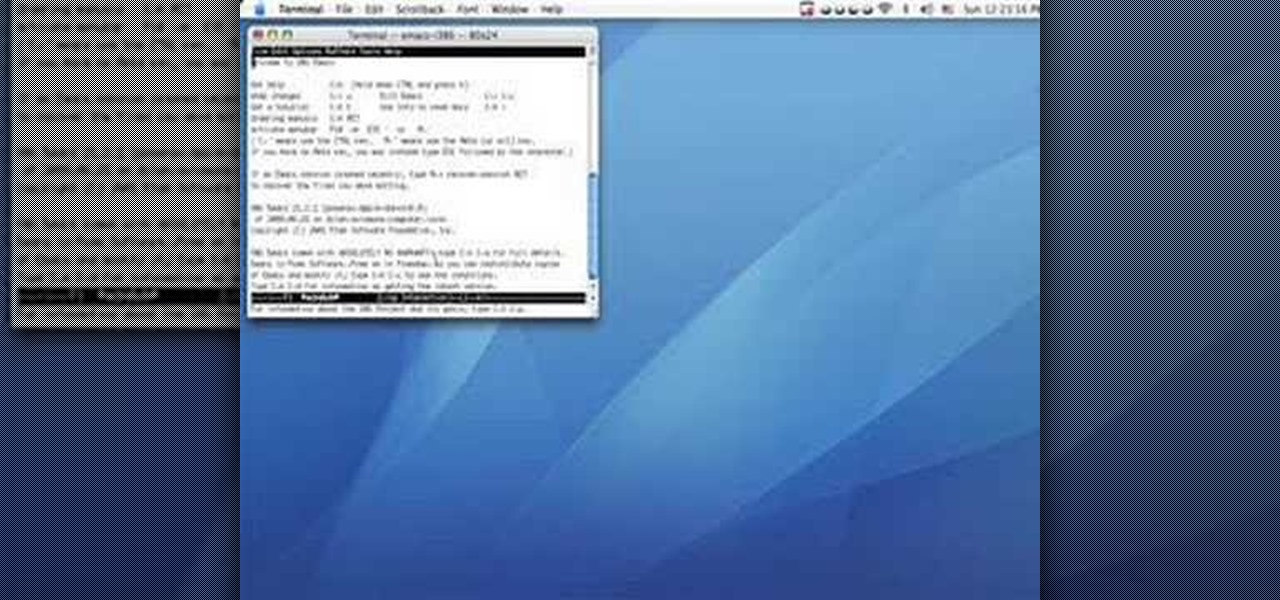
In this tutorial, you'll learn how to use the emacs text editor, accessible through the terminal on any computer running Mac OS X, to play a simple version of Tetris. The steps are simple and as follows:

Watch as a seasoned expert walks you through the steps of sliding screen door repair, from gathering your tools and buying the correct replacement parts to adjusting the newly-repaired door, in this free online video series about home maintenance.

Learn how to sew curtains, how to choose the correct fabric and how to install them when you've completed a curtain sewing project with expert sewing instructions in this free crafting video series.

There are so many things that can go wrong in a golf swing that it is hard to know what you did wrong so as to correct it. Watch and learn as this golf expert shows you some vital tips on how to improve your swing knowledge so you can get better on your own in this free video clip series.

Watch this automotive video tutorial to see how to scan your automobile for diagnostic trouble codes.
Whether you're a social type with a loooonnng list of friends or a PR gal with a bunch of people you've got to contact all at once to notify them of an event, it can often get time-consuming to type out the name of every single person you have to send the same email to.

This instructable aims to show you how to cut any type of disk to a desired shape. It is particularly useful in cutting down cheap 12cm DVD-+R 's into more expensive (can be up to 10 times more) 8cm DVD-+R disks. The technique shown here works with all disk types. The video below shows us cutting a music CD into a heart shape, and also illustrates the basics of cutting 12cm disks into 8cm ones. The actual cutting of a disk (and the guide) can be seen here:

Tim Carter demonstrates how to get professional painting results by caulking all cracks between woodwork and walls before painting.

Chef Don from HouseCallChef demonstrates how to grill mushrooms, asparagus, zucchini and yellow squash. You can also grill other vegetables such as parsnip, rutabaga, potatoes, tomatoes or peppers, and even some fruits like pineapple, watermelon, apples and oranges. You can use any type of grill that you want.
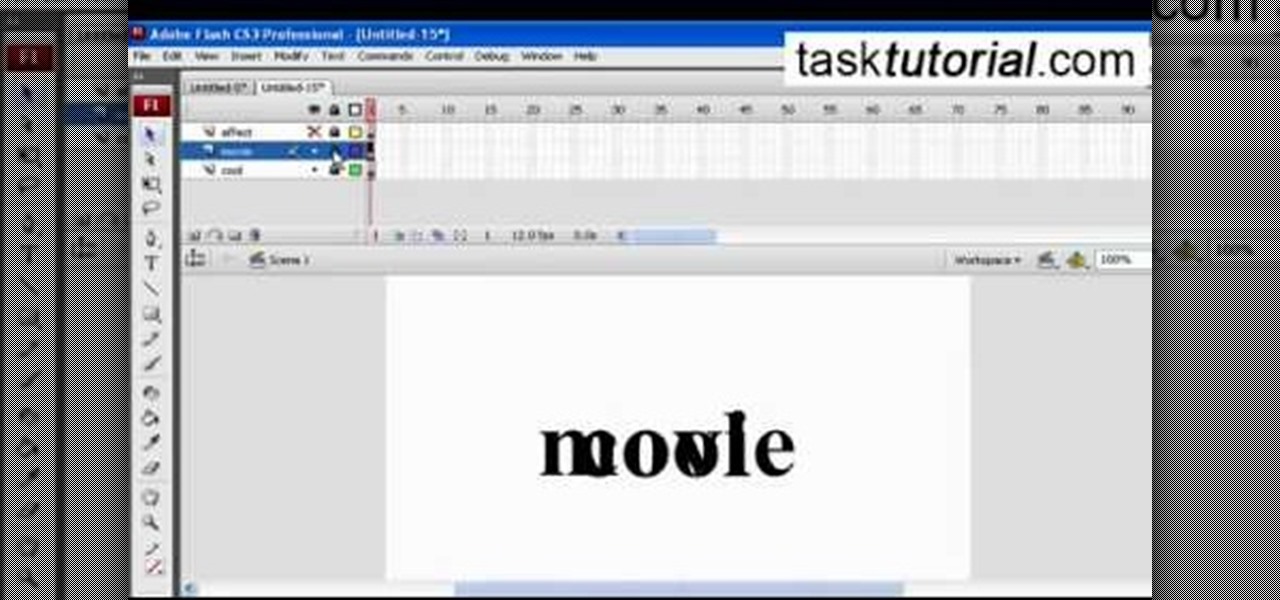
A great free video training from tasktutorial on how to create a cool movie text effect in Flash. Start by creating the text; type in "cool", rename the layer and lock it. Now type "movie" and rename the layer. Type in "effect" and rename this layer as well. Now focus on the first layer. Convert it to movie clip. Now convert the other two layers to movie clips as well. Stack the three layers on top of each other. Next add a key frame starting from frame 10. Select the "cool" layer. Re-size it...

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to transform a photo into a flashy poster in Photoshop.
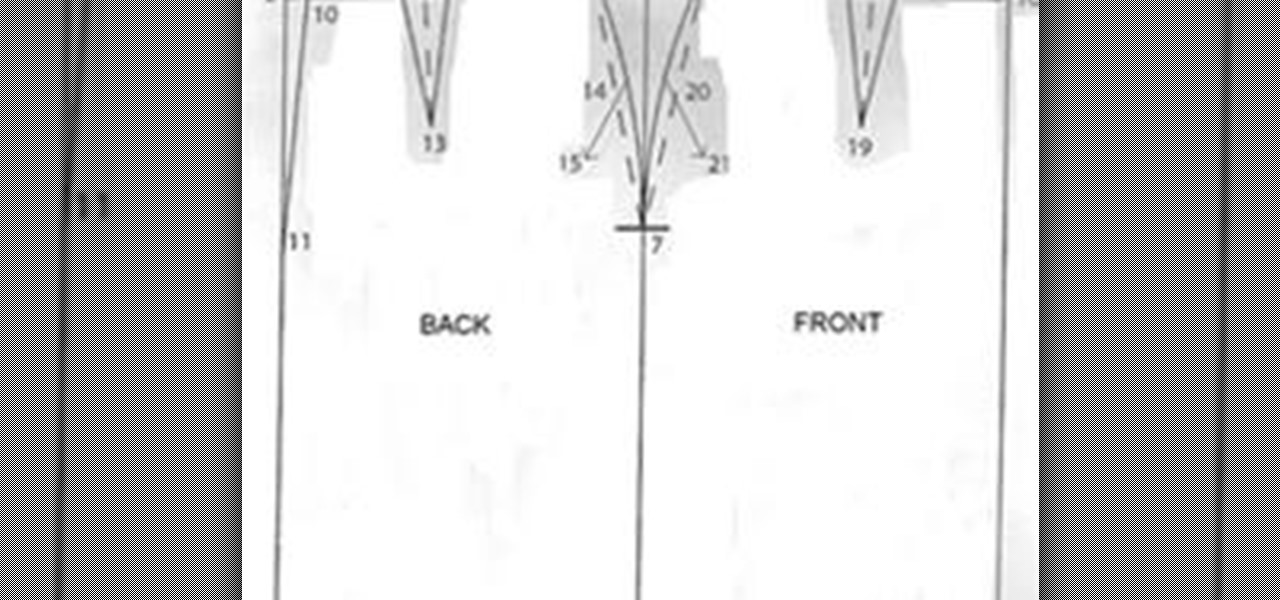
Written instructions on how to draft a basic skirt pattern with accompanying video. Take your correct measurements before you begin.
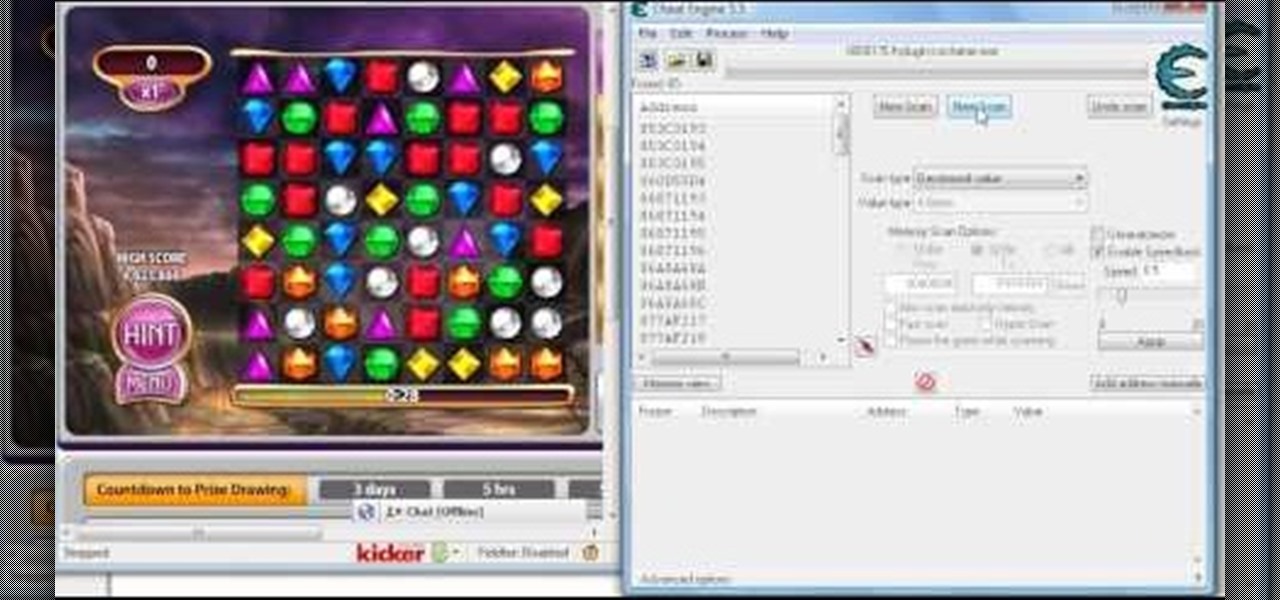
Don't let Bejeweled Blitz get the best of you. Show it who's boss and get the highest score possible. Of course, you'll need Cheat Engine to overpower the game, so make sure you have Cheat Engine 5.5 or higher and check out this video for the hacking Bejeweled Blitz (10/09/10).
This video will show you how to use the ‘find’ and ‘replace’ text buttons in Microsoft Word 2007. Microsoft Word 7 is slightly different from the Microsoft you might be used to but with these instruction you’ll have no problem finding the buttons.

This video will go over how to insert a check box in Microsoft Word for printing or for electronic distribution. With just a few clicks you can get a check box. You can even add different symbols or styles for your check box.
Stan shows an easy way to see and clean the files that are hogging hard drive space in the computer using a free software called "windirtstat". Now enter the following address in the web browser "windirtstat.info" and scroll down the page until you get the downloading and installing section. Click on the link "windirtstat1.1.2Setup(Ansi&Unicode)" which will be right after the "for all flavors of windows" this will direct you to "SOURCEFORGE.NET" download creations. This will ask you to save t...

In this series of videos you'll learn how to draw with charcoal from a professional artist. Expert William Cotterell shows you what types of art supplies you'll need to get started, including various types of charcoal, compressed and pencil varieties, types of erasers that work best with charcoal, and the best types of paper for making charcoal drawings. He also shares tips for choosing a subject, understanding light, blending techniques, adding highlights, and using Fixatif to protect your w...

In this video series, learn how to play the piano from expert piano player and professional musician Tony Newton. Tony will teach you basic piano lessons such as proper posture and correct hand positions for the piano. Developing nimble fingers is paramount for great piano playing. Our expert piano player will show you how to practice correct finger techniques to enhance your manual dexterity and facilitate muscle memory. However, this series is not solely for beginners. You can learn more ad...

Apple released iOS 13.5 for iPhone on Wednesday, May 20. The update came just two days after the company seeded beta testers iOS 13.5's GM (golden master), the build everyone would get if all went well. While only available to beta testers, the GM is the same software as iOS 13.5's stable release.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

For anyone interested in using cheap, Wi-Fi-connected microcontrollers like the ESP8266, the Arduino programming language can be a barrier to entry. Based on C++, Arduino requires knowledge of more computer science than languages like Python. Fortunately for beginners, setting up MicroPython on an ESP8266 allows anyone to write Python on affordable microcontrollers in a matter of minutes.

Remember when typing without physical keys seemed ridiculous? Now, touch typing is the smartphone norm. That said, mistakes are inevitable on small screens. So before you start hammering on that delete key or shaking your iPhone like a madman, know that there's a better way to undo text you didn't mean to type — no shaking involved.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.
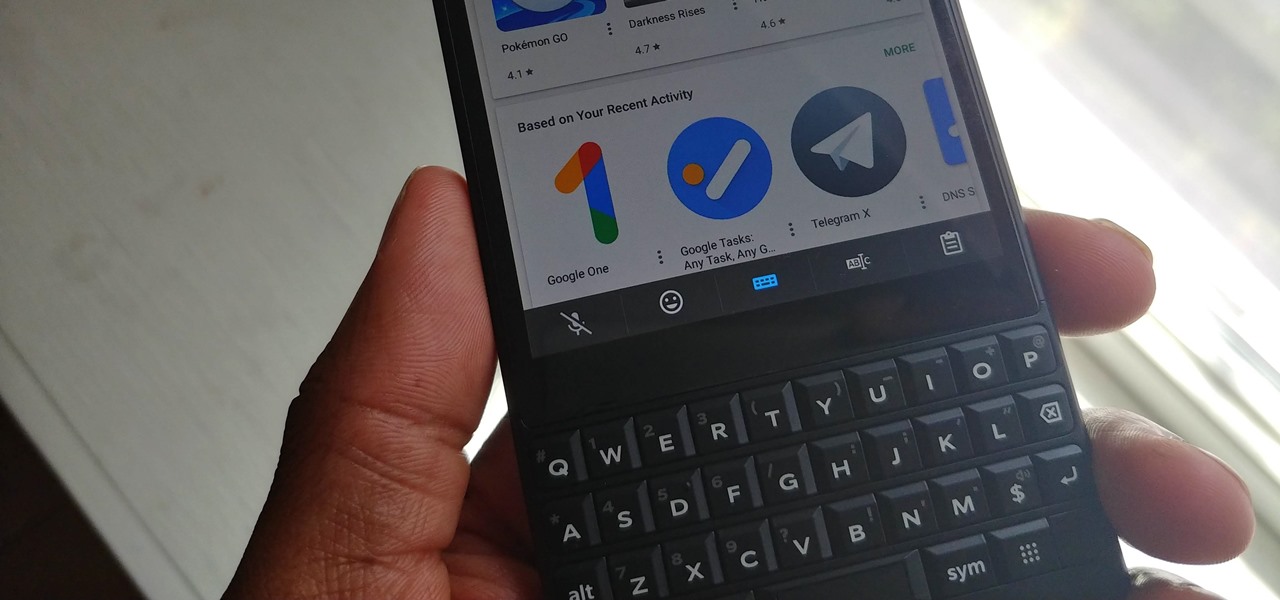
One of the best parts of the BlackBerry KEYone and KEY2 is the iconic physical keyboard. There is one major downside, though: By default, the virtual keyboard appears on these devices even when typing on the physical keyboard. Luckily, there's a way to change that.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

After learning that you'll need to spend at least $74 on a special charger and a USB Type-C Lightning cable to enable fast charging on the new iPhone X and iPhone 8 models, you may be wondering why you can't just use the standard Lightning cable. While we can't answer why Apple didn't include the USB-C cable in the box with their new phones, we can explain why you need USB-C to enable fast charging.

We are in a pretty major technology boom at the moment. One that will likely make the industrial revolution look tiny. And one of these technologies that are building up to lead the way is something called augmented reality.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

"Necessity, not novelty," is a phrase I use often when it comes to HoloLens development. It would be fair to call it my mantra, or mission statement, as I prototype and explore software creation on this new frontier of mixed reality.

Students from Carnegie Mellon University's Entertainment Technology Center have been working on an augmented reality system to help teach music in a project called Music Everywhere.

Hello there Nullbyte users! This will be my first article here.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

In this article, we will build a parallel password cracker using the techniques explained in the previous part. As SHA-512 is the digest function that Kali (and most modern Linux distributions) use to store our passwords, we will make a SHA-512 password cracker.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.

In Minecraft 1.9 New Command Blocks can be used to make elevators. You types different commands to achieve controlling the elevator for movement you like. This tutorial tells in Minecraft 1.9 how to use command blocks to make elevator. Lets just have a look at it!

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them