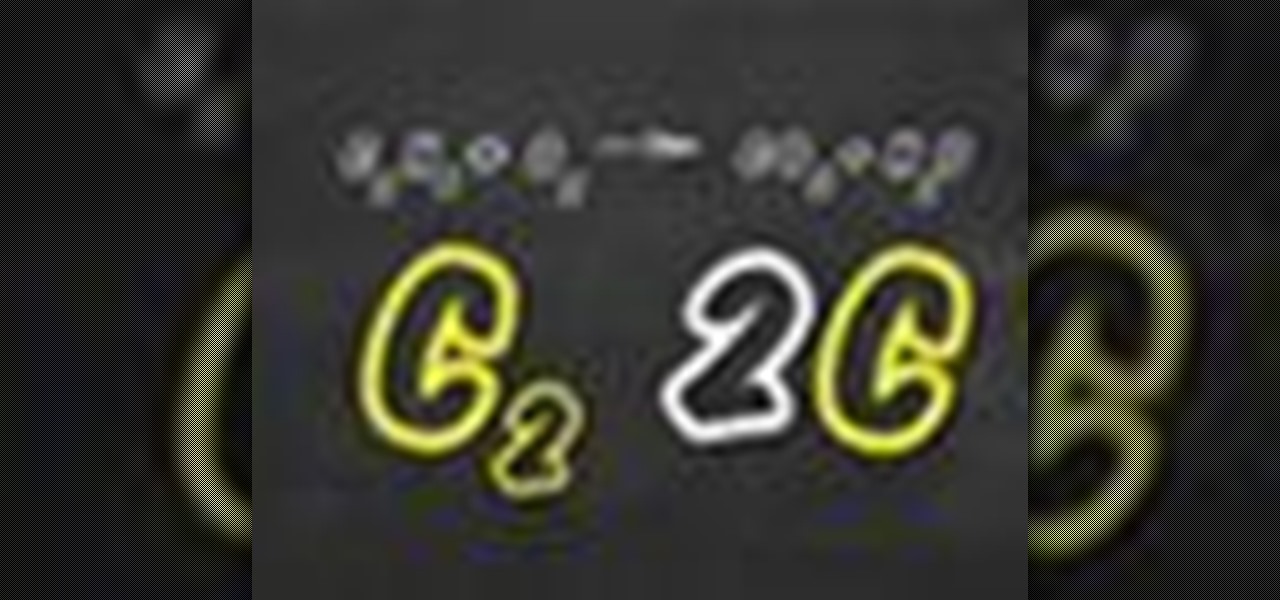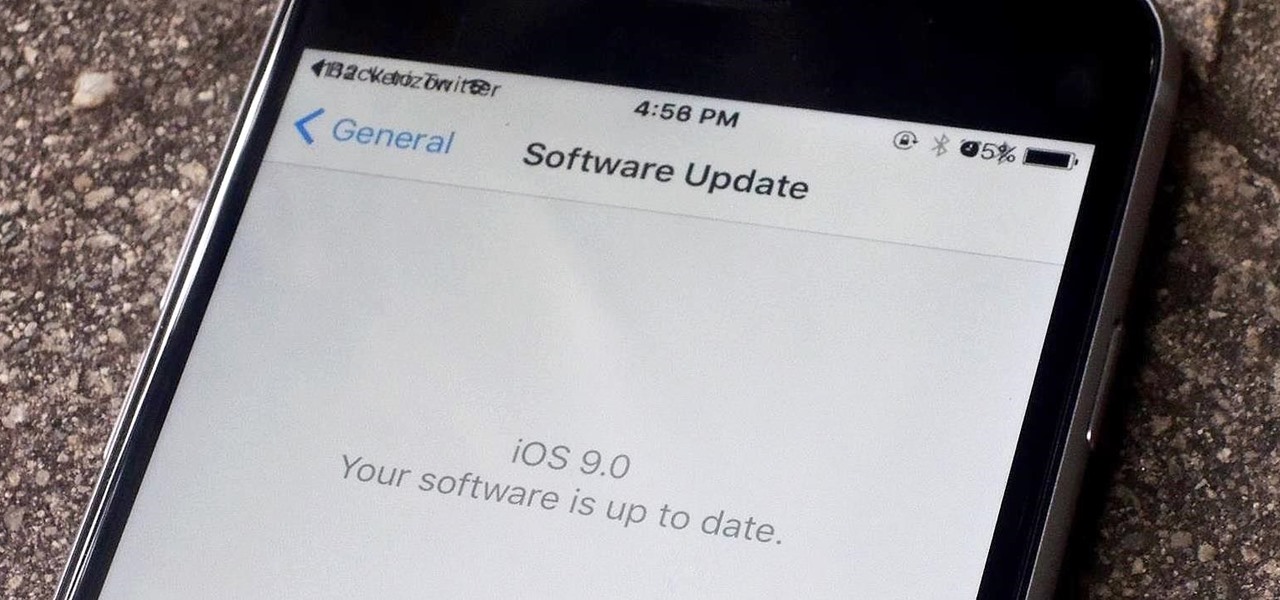
Apple's unveiling of the iPhone 6S, iPhone 6S Plus, Apple TV, and iPad Pro dominated the news today, but at the end of their special September 9th event, they quietly released the final version of iOS 9 to developers, called the Gold Master (GM) build.

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

From laptops to tablets, technology is taking over classrooms. Elementary schools offer kids tablets, and college students are bringing laptops into lecture halls, leaving their notebooks behind. Today, many students prefer putting their fingers to a keyboard rather than pen to paper, but are these helpful devices truly beneficial?

What Is IPython? IPython is a richly featured replacement for the standard python interpreter. It offers a wider range of functionality, that the standard

When you have a parent who cooks—and has you act as sous chef—the kitchen automatically becomes a less intimidating place. In other words, kids who know their way around the kitchen will most likely become adults who cook for themselves, which also means that they'll eat more unprocessed whole foods, save money, and maintain a healthy weight.

Getting on the phone for customer service can be extremely frustrating. First you've got to find the correct phone number for your region (good luck trying to get customer service from a sales department), then you have to listen to the annoying automated system to navigate your way to the department you want. More often than not, you'll be stuck with some elevator music while you wait to speak to an actual human.

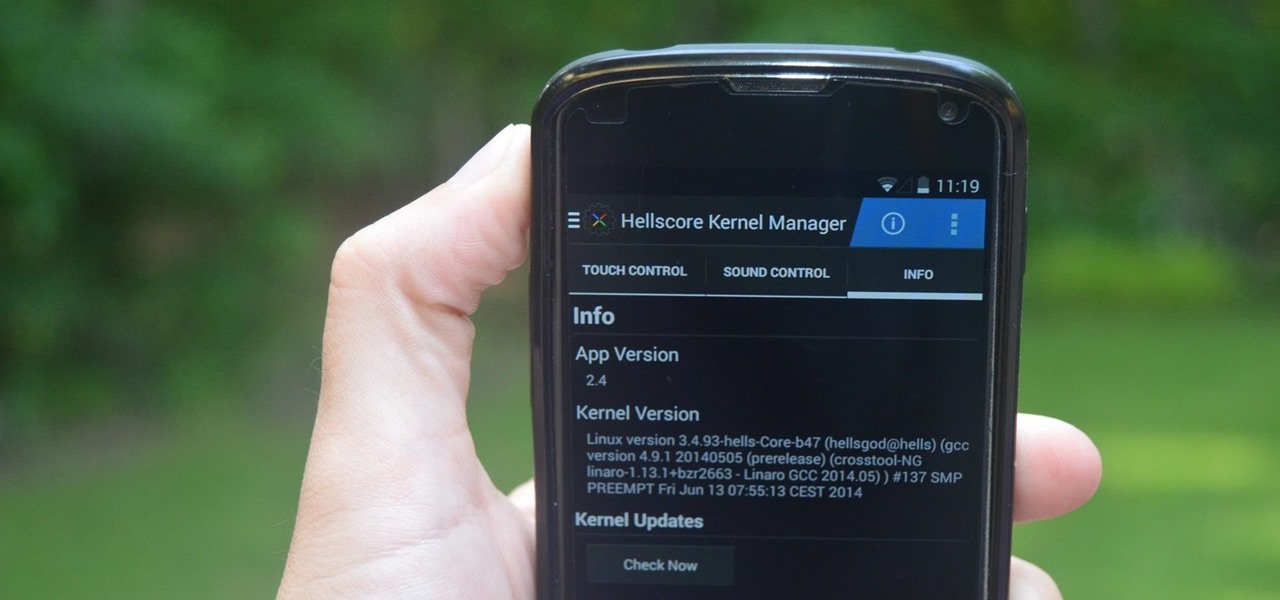
Increased battery life is easily one of the most sought after improvements to a device and often drives intrepid users to root their phones, flash new ROMs, and try out experimental kernels.

When it comes to passwords, the longer and more complex they are, the better the security. Even professional hackers say so. But if you've ever tried to type in such a password, you've surely noticed that it can be a bit of a pain. Mistype one character, and you're probably going to have to clear the field and start all over again.

Welcome back, my greenhorn hackers! Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It enables us to crack multiple types of hashes, in multiple ways, very fast.

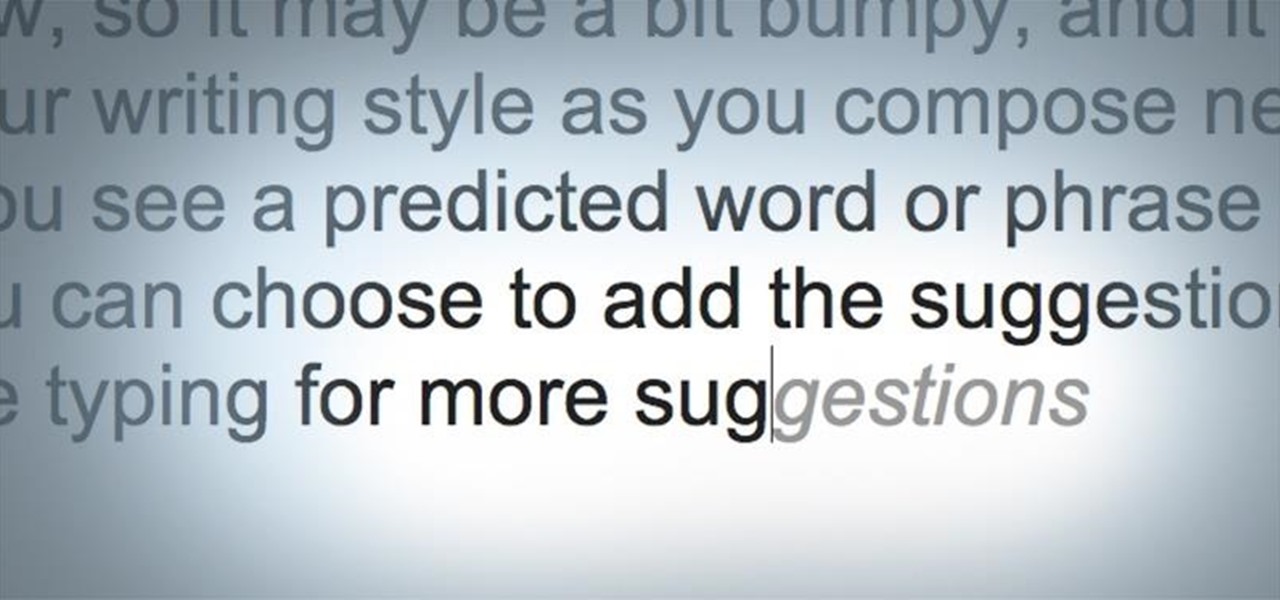
Android has had predictive text for a while now, both with stock and third-party keyboards such as Fleksy, SwiftKey, TouchPal, et al. Apple is even getting on board, with stock predictive text and third-party keyboards for iOS 8, slated for public release later this year.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Welcome back, my greenhorn hackers! Congratulations on your successful hack that saved the world from nuclear annihilation from our little, bellicose, Twinkie-eating dictator. The rest of world may not know what you did, but I do. Good job! Now that we hacked into the malevolent dictator's computer and temporarily disabled his nuclear launch capability, we have to think about covering our tracks so that he and his minions can't track our good works back to us.

With the use of Terminal, anyone can run multiple instances of the same application on a Mac. When you have multiple windows open in a web browser, the windows are all running under the same Process ID (PID). But, with multiple instances, each has its own unique PID. So why would you want to run multiple instances of the same app? There are several reasons a person may run clones of the same application, but the most popular would be so that the user could multitask. Some applications, like t...

Texting is a godsend to mobile devices, but it also has its caveats. Sending a text to someone requires visual, manual, and cognitive attention—looking at what you're typing, holding the phone steady, and thinking about what you're trying to say. So, texting while doing pretty much anything else is not a wise move.

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.

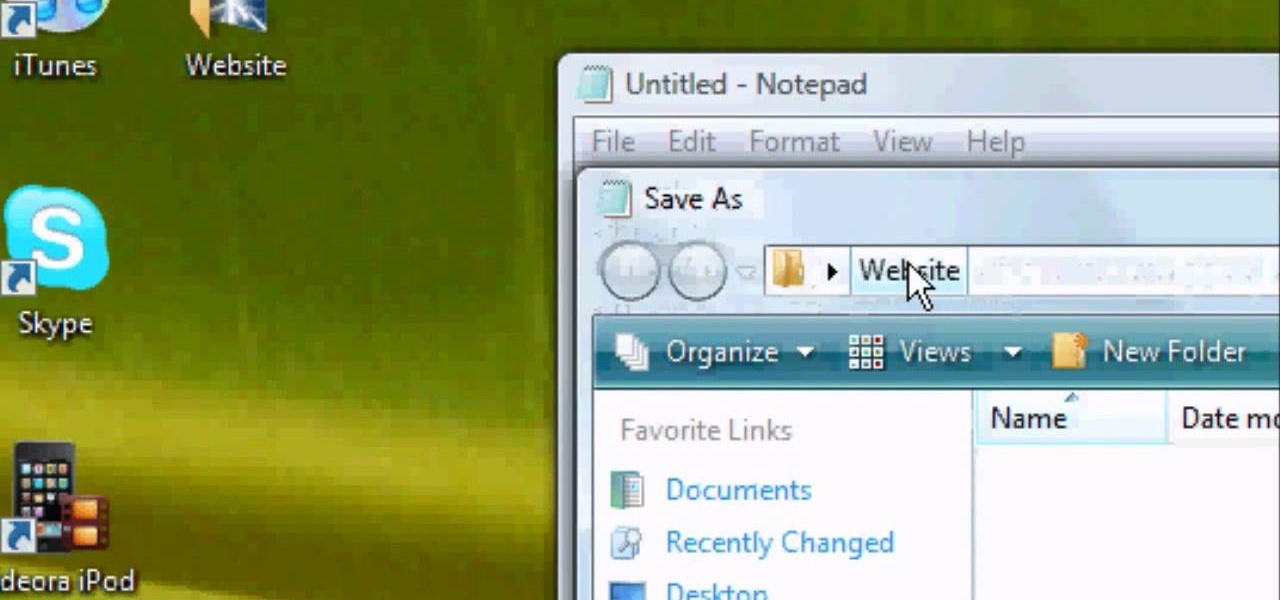
It's like magic. Creating a .LOG file has never been easier. And all you need is Notepad on your Windows PC. After creating this LOG file, Notepad automatically inserts the current date and time after the last line. Check it out. If you've ever wondered about LOG file types, this Notepad trick is must.

Have you ever gotten the error message, "BOOTMGR is missing" on your PC? Well, if you have check out this video. In this tutorial, learn how to remedy and fix this problem in no time.

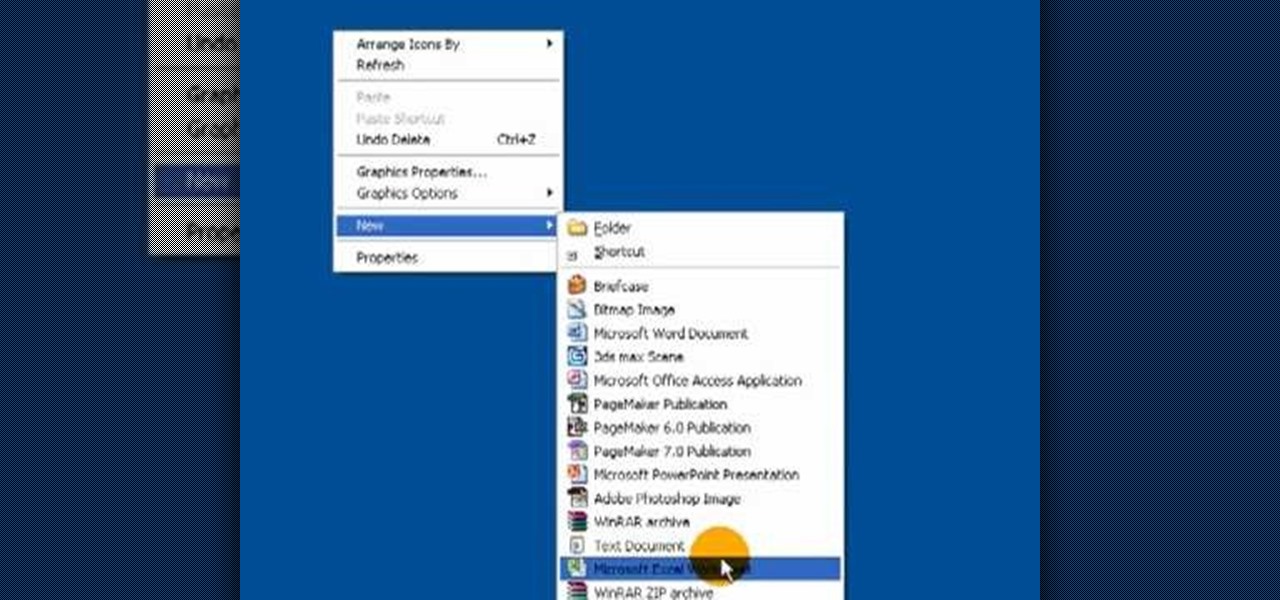
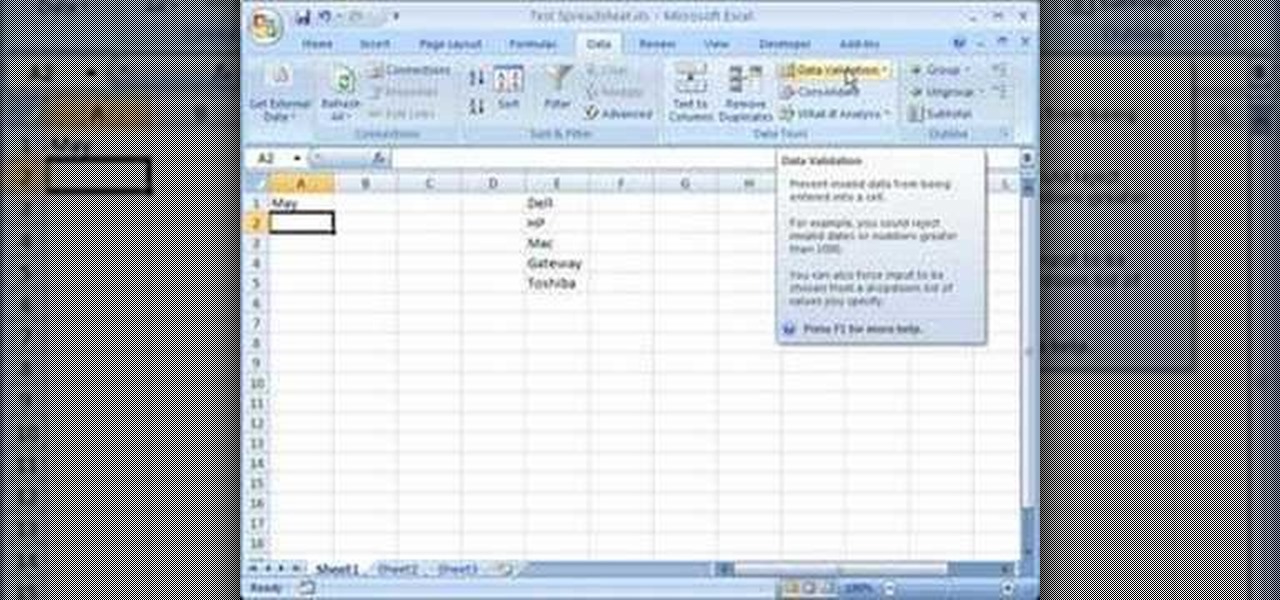
This video is a tutorial on how to create drop-down menus in Excel 2007. Select a cell on your spreadsheet and click on the “Data” tab. Go to the “Data Tools” section and select “Data Validation”. In the window that opens select "Allow" and choose "List". You will create a list of the values you want to allow. Type in the values, separated by commas, and click OK. Now you will see your selected cell has an icon to right that indicates there is a drop-down menu containing the value...

In this Software video tutorial you will learn how to make your own Adobe CS4 logo in Photoshop. Open Photoshop and click ctrl+O to open a new document. Set the height and width to 500 pixels, select ‘transparent’ under background contents and click OK. Create a new layer and with the rectangle tool draw a rectangle. Right click on the shape layer > rasterize layer. Hold ctrl and click on the thumbnail of shape1 layer. Open gradient tool and make a light to dark gradient as shown in the v...

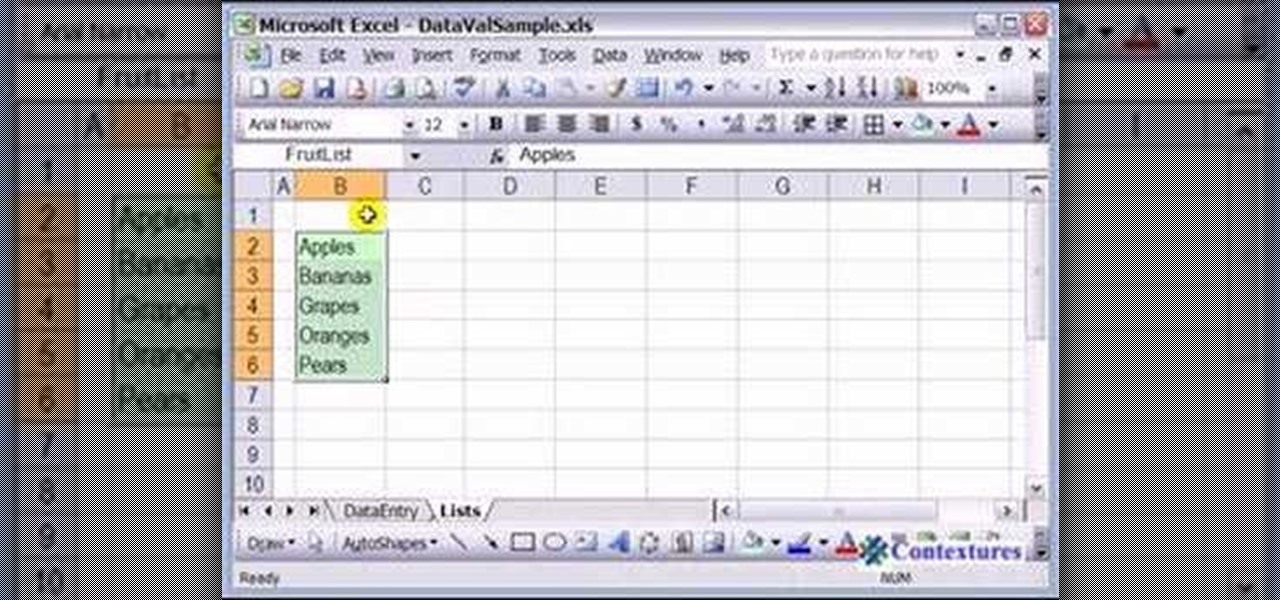
This how to video shows you how to use drop down lists in Microsoft Excel. This will be useful for stores and avoiding people ordering items that are not available. First, type the items in a column. Select them and then click in the name box. Type the name of the list. Note that it must be one word. Now, go back to the order sheet. Select the cell where you want the list to be placed. Go to data and select validation. On the settings tab, choose list and type in = and list name. You can pres...

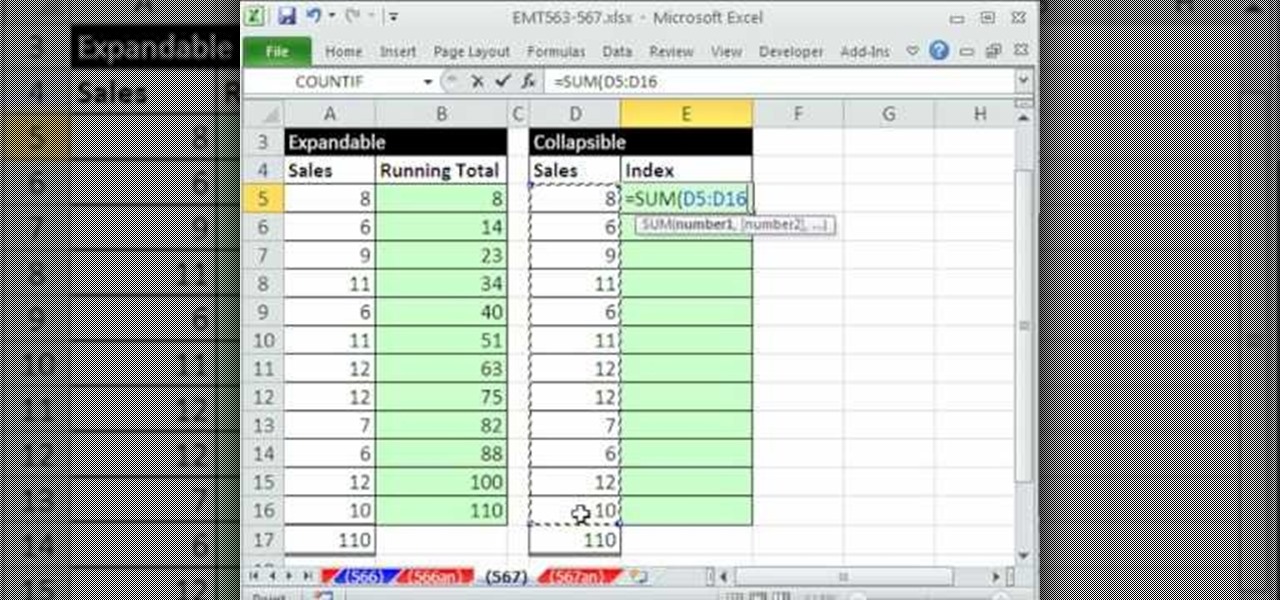
This video demonstrates how to create collapsible and expandable cell ranges in Excel. The first thing that you will have to is to prepare your Excel worksheet that contains the data which you need to be expandable and collapsible. On the first cell under your Running Total column, type in the function, "=SUM". Select the Sales cell corresponding to that cell then type in Shift+Colon. Click on the first value and hit the F4 key to lock your row reference. The result will automatically show. Y...

This video tutorial shows how to open a port for torrent downloading on your computer. Click Start menu, type cmd command in Search area. In cmd window type ipconfig and press Enter. Remember or write down your IP adress. Type exit and press Enter to close cmd window.

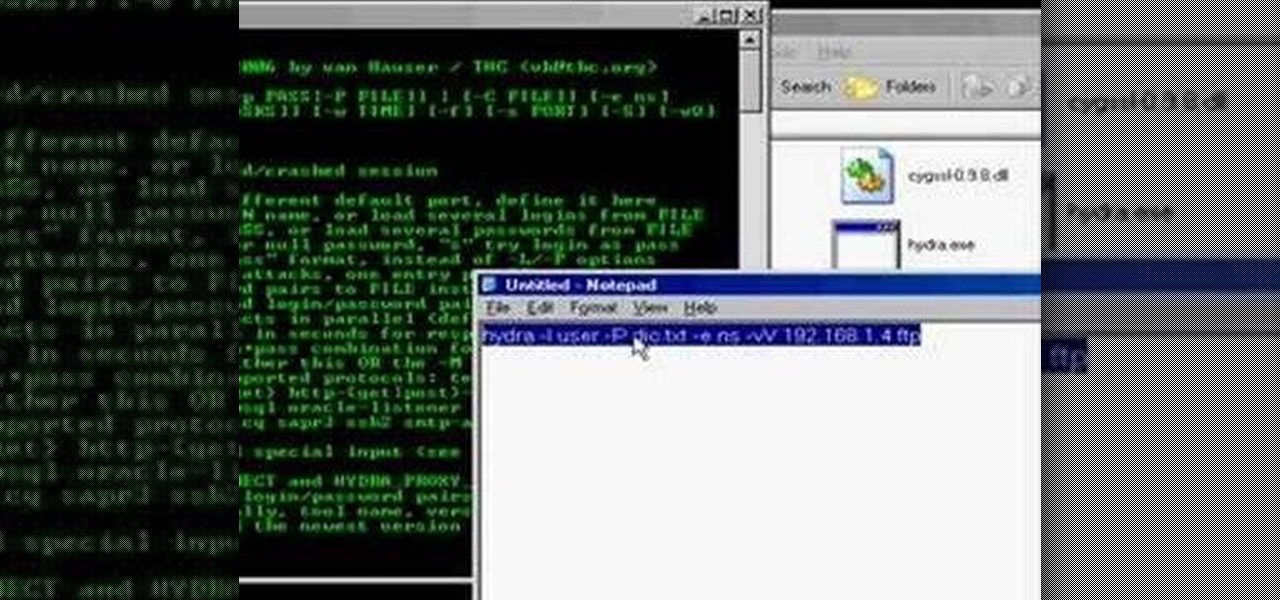
This is a how-to –video on using hydra 5.4 to crack FTP passwords. This video is intended for educational purpose only. It reveals the basics of hacking a FTP server using dictionary search technique. Here are the steps involved.

Open up dreamveiwer and click HTML on creat new. If the new page opens then go to design view and then go to insert and then layout object and then diff tag in that then click ok for that. There we have to create a scrollbar content. Then we have to right click there and go to css styles and then go to new. There go for selector type and click class and then name it as you want. Here he just named it as scrolldivstyle then go to go define in and take this document only and then click. Next yo...

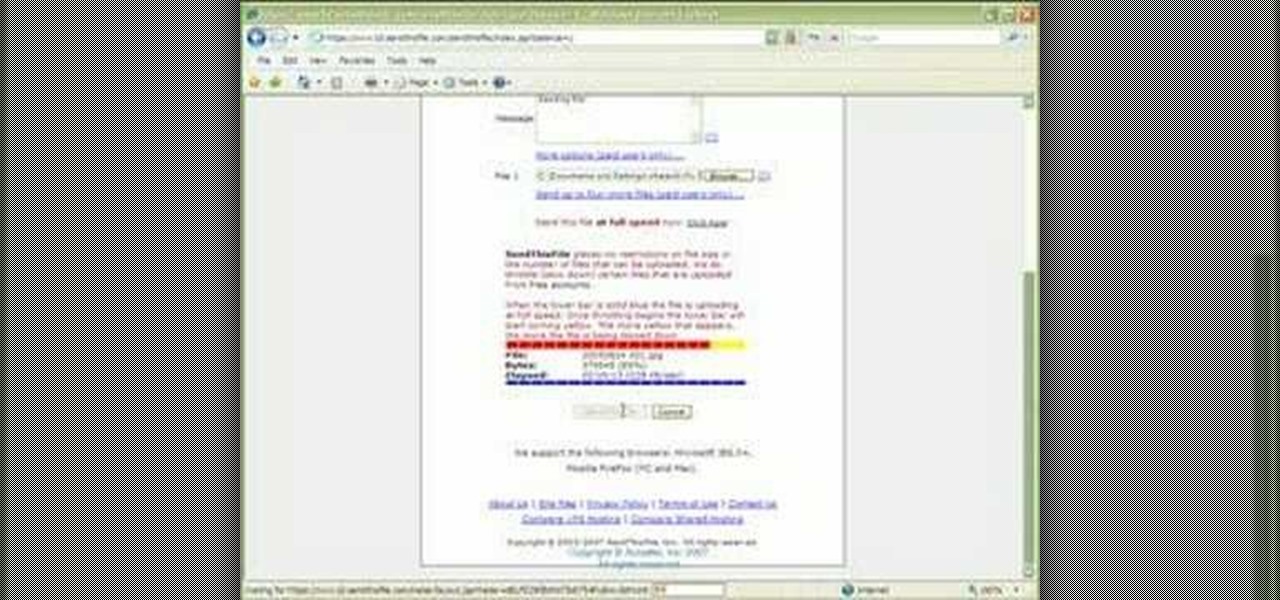
1. Type in WWW.sendthisfile.com in the web toolbar and press enter 2. Click on Register found on the top right side

In this how to video, you will learn how to speed up your Azureus Vuze program. First, open up Azureus Vuze. Next, go to advanced, option, and click preferences. Select preferences and change the port to a number between 49152 to 65535. Once it is changed, go to transfer and make sure that these are set to zero. Once that is done, open your web browser and type in your default gateway. To find this out, go to system preferences, network, and router. Next, enter your user name and password to ...

First of all you have to open the 'notepad'. Now you have to type in "<html>" in first line. Write "<head> in second line. Write "<title>this website contains text wrapped around images</title>". In the fourth line you have to type '<body bgcolor="#999999">'. This shall add a light orange color. Now find out the name of the image. Here the name of the file is 'image.png'. Then in the next line you have to type in "<img src="image.png">this text should hopefully wrap around the outside of the ...

HighQuality Tutorials demonstrates how to change your iPod Touch alpine default password. Changing the default password is useful when using your iPod Touch in a public setting to make it less vulnerable to hacking. To change the default password, first open up your internet connection and search for Putty. Download the Putty program. Open and run the Putty program. Your host name will be your IP address for your iPod Touch. Select port 22 and SSH and open up the program. Log in as root and c...

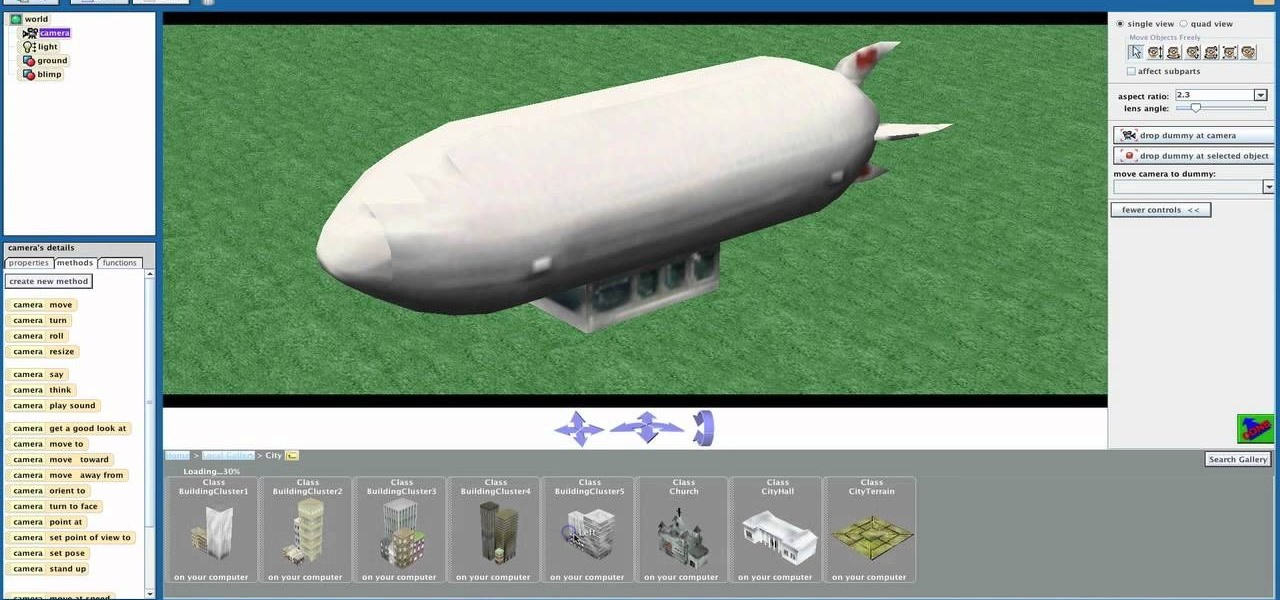
Shaun will teach us how to create a 3D video game compatible with MAC or PC with no prior programming knowledge. First download Alice, a 3D World program that can be turned into a video game. Open Alice, click on "add objects", click on "more controls" and select your choice of aspect ratio such wide screen. Now you can import your own 3D models that Shaun will show you at the end of the tutorial or choose from a wide selection that comes with Alice. In addition, if you click on "home," "web ...

This video shows how to change the advanced settings to make Firefox faster on Mac and PC.

Not sure how to balance a chemical equation? According to the rules of chemistry, matter must be conserved in chemical reactions. When you balance a chemical equation, you account for all of the matter in the reaction.

There has been an update with the NES emulator, so you have to put the ROMs in the /var/mobile/Media/ROMs/NES folder, and not the /var/root/Media/ROMs/NES folder.

This video from ESPN walks you through the different draft modes available for picking a fantasy football team using the ESPN fantasy football site. The different draft modes available are:

You don't need to pay a stylist or even get a friend to help you with this hairstyle! It's easy, elegant and looks good with nearly any type of long hair. Here's how to create an elegant bow updo for your next formal event!

New to shooting video with a DSLR? In this video tutorial from renowned DSLR cinematographer Philip Bloom and the staff of Vimeo, we receive some tips on how to work with different lenses when using a DSLR like the a Canon 7D, T2i (550D) or 5D Mark II.

Add text and titles with Windows Live Movie Maker. There are three options for adding text in Movie Maker. This tutorial provides an overview for each type: title (which goes before the selected clip), caption (which is superimposed over the selected clip) and credits (which goes after the selected clip).

This is perfect for someone who wants to keep their hands warm but still work with their hands (such as typing, sewing or crafting). Start with medium weight worsted yarn and a size I crochet hook to make these fun wrist warmers.