
Apple AR: Assisting the Technically-Challenged Is Easier With Vuforia's New App
If you're a regular reader of this site, there's a good chance friends and family turn to you as their volunteer technical support staff.


If you're a regular reader of this site, there's a good chance friends and family turn to you as their volunteer technical support staff.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

Typing out thirty hashtags on Instagram is always such an annoying process. Figuring out the best hashtags to use to get more likes is also tricky. You can't just keep copying and pasting the same hashtags on every post — that's like attacking the same tribe every time. You got to diversify, which takes a lot of conscious effort to be on top of the current best hashtags to use.

Nike's newest app is changing the way we shop. Called SNKRS, it uses augmented reality to sell the limited edition Nike SB Dunk High Pro "Momofuku" sneakers.

Dramatic new research may change the fate of the hundreds of people who wait for a kidney transplant every year. The study hinged on the ability to cure hepatitis C infections, a possibility that became a reality in 2014.

Microsoft Research has published a technical paper reviewing their work with near-eye displays for virtual and augmented reality to project phase-only holograms.

Kik is an extremely popular messaging app, but it has a few annoying features that we all just sort of put up with. You can't turn off read receipts, nor can you hide when you're typing, and the photos you take with Kik's camera show up differently than ones you send from your gallery app. At least a couple of these features should be subject to change, but they aren't — well, not without some tinkering.
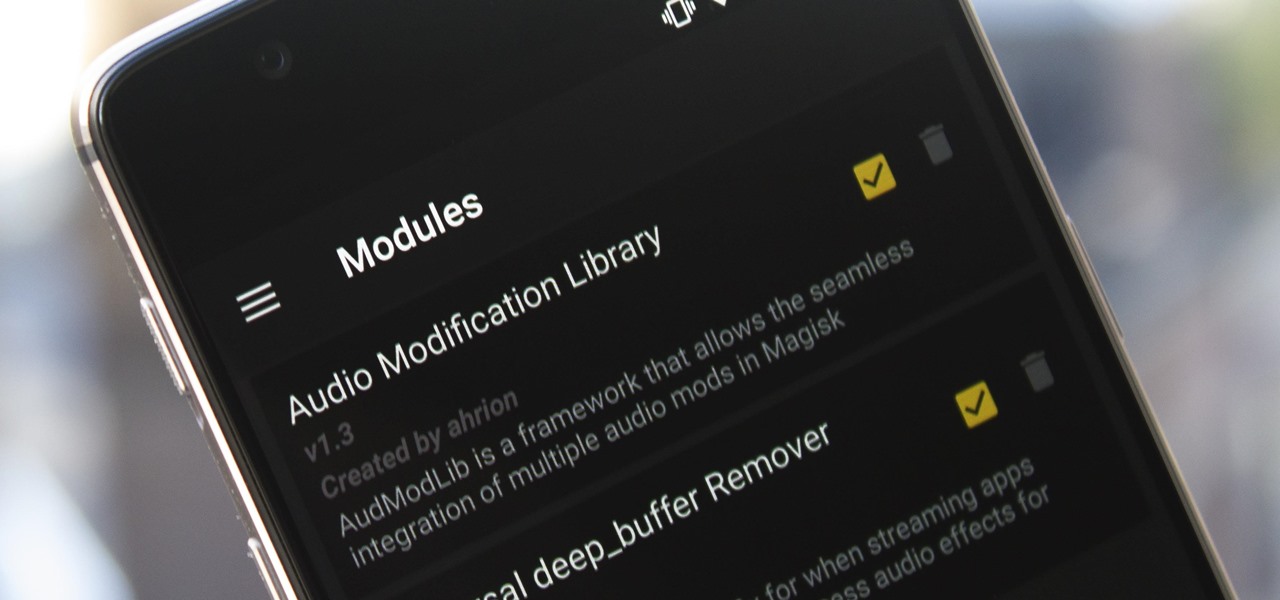
Most music streaming services will either use the stock Android equalizer or their own built-in equalizer. A couple of apps, such as Spotify, bring both to the table. Spotify has a built-in equalizer which kicks into play when a system or third-party equalizer isn't detected. However, other apps such as SoundCloud and Pandora don't use the installed equalizer even if it's a system-wide one.

While there are many good reasons to update to Apple's newest mobile software, a bug has made it to where you may want to double-check your iCloud settings after doing so.

The newest version of Snapseed features three awesome new tools for you photo-editing enthusiasts. The 2.17 update for the editing app was rolled out on Tuesday, March 21, and its new additions are something to behold.

As many as 700 species of bacteria live on our teeth and in our mouth, and just like the microbiomes inhabiting other parts of our bodies, they change in response to diseases and other health conditions.
Android is a highly customizable operating system. Sometimes, we use these capabilities to add core functionality or streamline the user experience, but there are other times when customization is just about having fun and making your smartphone's interface more enjoyable.
As we first reported here on Gadget Hacks, Google's new Pixel and Pixel XL smartphones come with an unlockable bootloader, with the exception of models sold by Verizon.
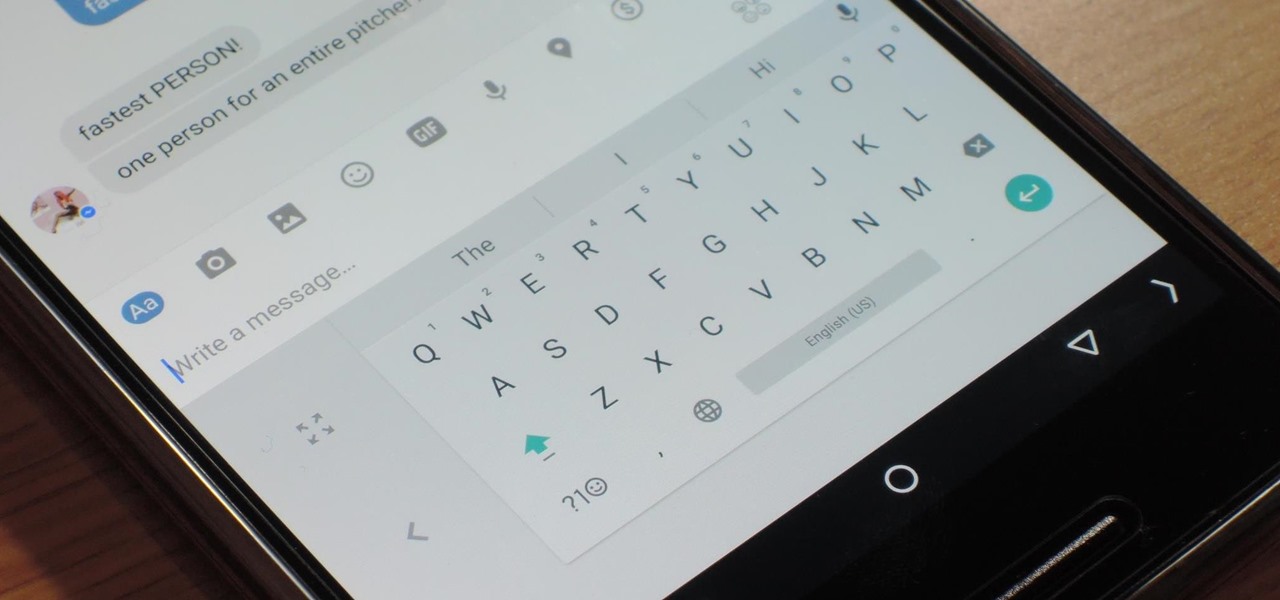
Google has added a number of new features in the latest update to Google Keyboard including a one-handed mode and a setting that lets you adjust the height of the keys. The update hasn't gone live on the Play Store yet, but you can download the APK right now for both 32-bit and 64-bit phones.

According to sources, Google has been working on a travel app for some time, and now it has a name: Google Trips. Google Trips aims to be the all-in-one place to go for travel information about your trip. It hasn't been officially announced, but from the leaks that have come out so far, think of it like Yelp, TripAdvisor, and your itinerary in one.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

Google Maps, once considered superior to Apple Maps, has contributed to a terrible mistake for one woman. A group of demolition workers in Texas were using the service to find a worksite, and to the dismay of homeowner Lindsay Diaz, Google was entirely inaccurate.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

I saw an amazing video with a great idea on how to create claws when you have longer nails. I want to go as a Vampire this year, but those claws that you buy look terrible on me, because my nails are long and you can see them under the fake claws. The video was in German, which kinda "spooked" me at first, but the girl added English subtitles (thank god). Here is the video and the instructions she gives:

In this video and food hack tutorial, you will learn how to open a Hershey's Kiss The Right Way . The correct way to open Hershey's kisses is probably not what you think.

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.
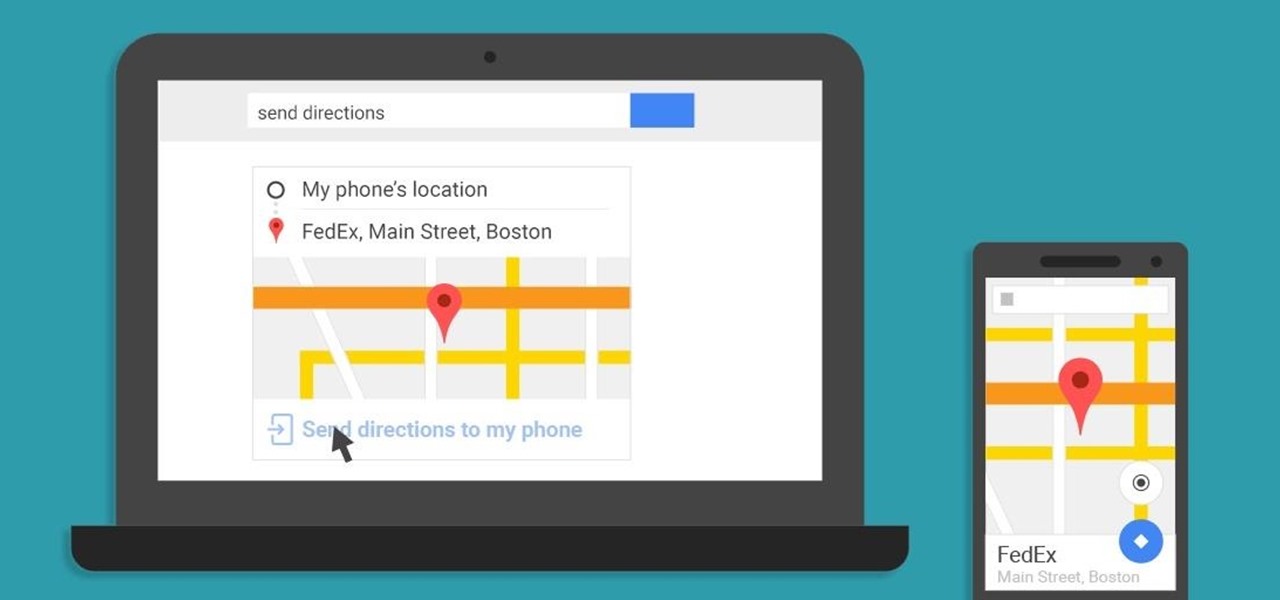
A set of cool new Android-related Google Search functions made their debut this week, which will allow you to locate your phone, send directions to your mobile device, set alarms and reminders, and send notes from any web browser.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.

The Nexus 6 is one of the few devices on the market that sports a 1440p "QHD" display. This means that the amount of pixels displayed is higher than almost any other smartphone, which sounds great on the surface, but is not without its drawbacks.
So, you wan't to become a Xbox Community Ambassador? Wan't to give support to other Xbox Customers and Earn loot doing it? Want to be different from a "normal" Xbox Customer? Want to share your knowledge to others who want it? Come on over here, friend! In this How-To, I will tell you how to become a Xbox Community Ambassador in the most correct way possible! In 3 Easy Steps! Here is the Link to the Website : http://ambassadors.xbox.com/
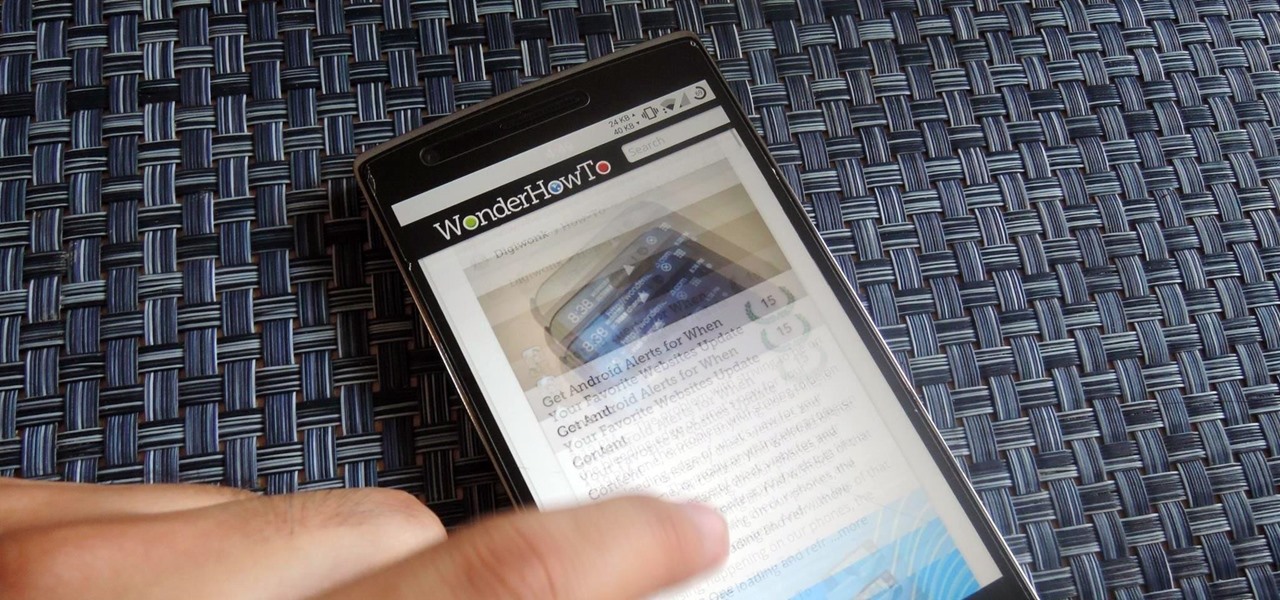
The hardware running your One is nothing short of powerful, but the people at OnePlus can't control how developers choose to utilize that power—or rather, not utilize it. Most popular developers have removed all signs of lag from their apps, but others still have archaic lines of code that can make your shiny, new device feel like a first-generation smartphone.
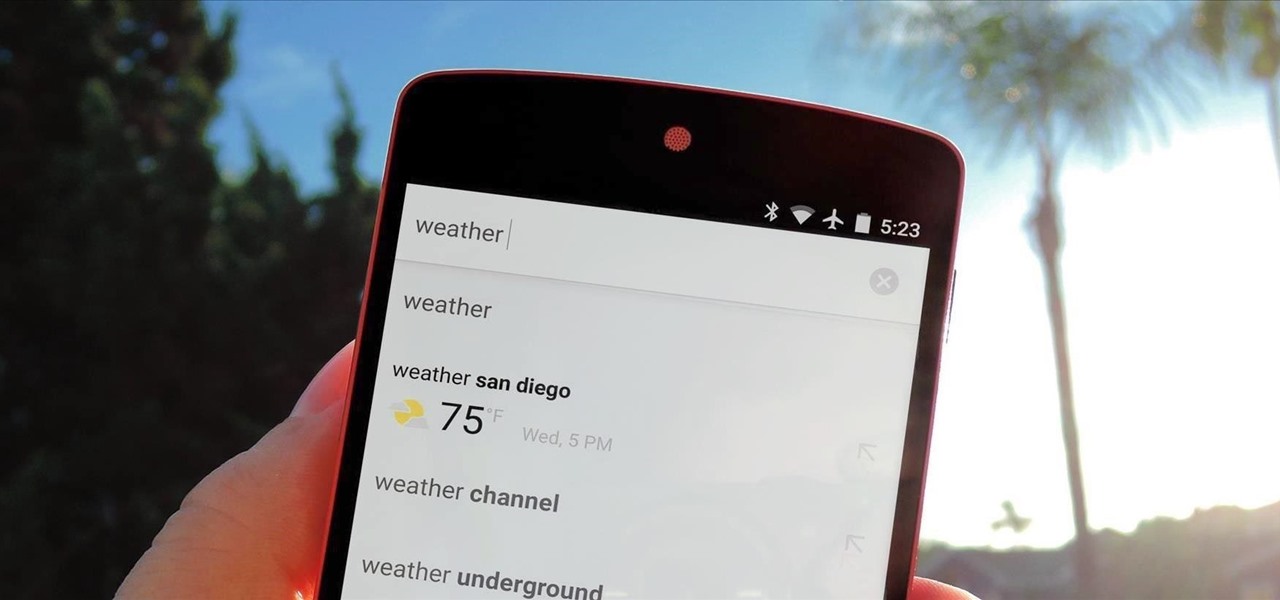
Google continues to be the most commonly-used search engine for a reason. While continuing to stay ahead of the pack with advanced semantic search functions, Google even introduced Knowledge Graph results that offer key information without ever having to click a search result.

The Touch ID fingerprint scanner on the iPhone 5S was one of the phone's biggest selling points. Now, the Touch ID system can do more than just unlock your phone, like pay for stuff, and is even present on the new iPads (as well as iPhone 6 models, of course).

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

Maybe it is narcissistic to take selfies, but it has become a socially accepted norm, no matter how stupid you might look doing it. Since so many people are seemingly in love with themselves and mobile photography, I thought it was about time to show you how to step up your selfie game.

Throughout history, the idea of the future has always promised better days, advanced technology, and of course—hover cars. Although we were correct about the better days (depending on who you ask) and advanced technology, we are still without hover cars, or pretty much any hovercraft vehicles—The Jetsons and Back to the Future were a lie!

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"
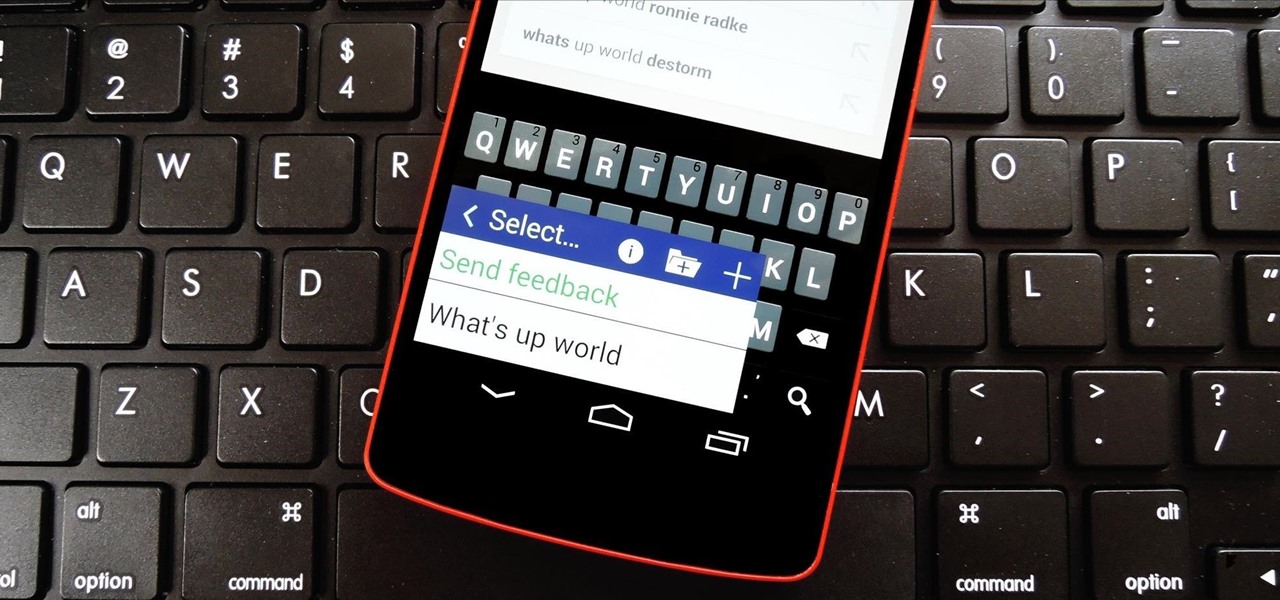
There are a lot of instances where we find ourselves typing virtually the same phrase that we've typed many times before. Whether it's the standard spousal reply of "I'll be home in a few", or a work-related phrase like "I'll have that to you by the end of the day", typing phrases like these can feel very redundant at times.
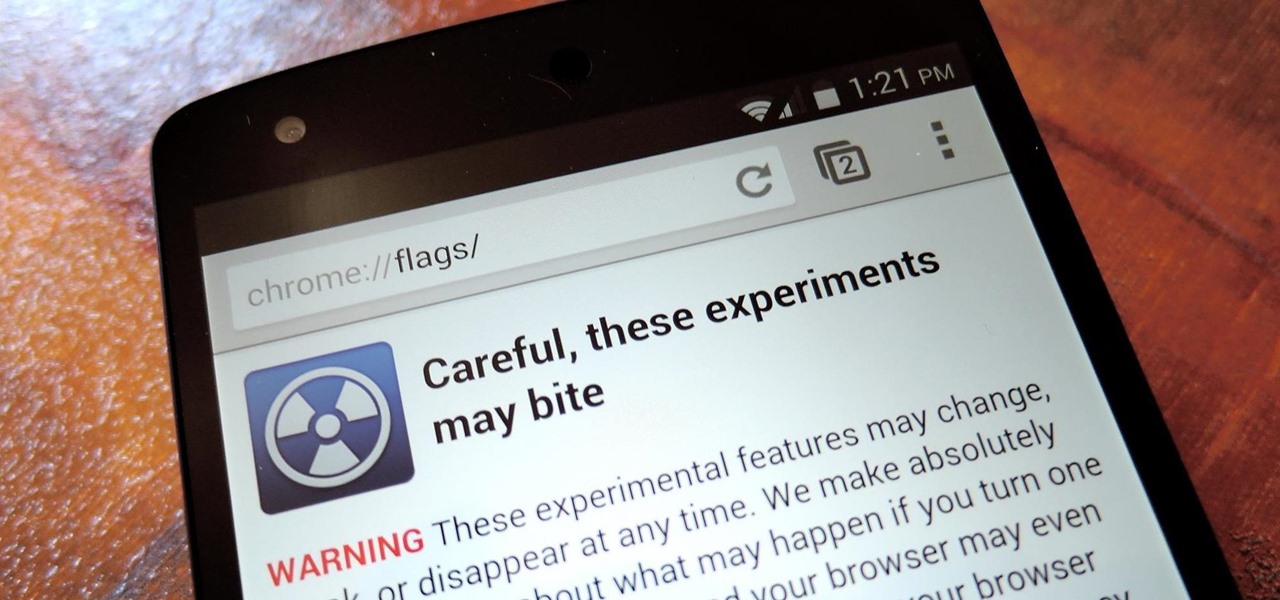
With the release of Jelly Bean, Chrome became the default web browser on Android. The wildly successful desktop browser was now fully entrenched in the world's largest mobile operating system.

There are thousands of fonts you can download online. Some are free, some you have to pay for, but they all have something in common—if you can get them, so can everyone else. If you want a truly unique font that no one else is using, you have to make your own, and what's more unique than your own handwriting?

Snapchat is like that very attractive girl at the bar that has one too many shots and ends up slobbering on the bouncer as she gets led out. Of course she can still recover since she is hot, but you only get so many chances before you just become a complete failure. And that's where Snapchat has been treading these past few weeks.

There are already hundreds of glitches out there for Grand Theft Auto 5 Online, but most of them are useless. Most of them don't do anything to benefit your gameplay, but they're still pretty fun to mess around with. One such glitch, shown off by YouTuber AquibTV below, lets you inside any building in Los Santos. Los Santos is a big ass city and there are tons of buildings that you cannot get into without using a glitch like this one.

The space on your phone is extremely valuable, so getting the most out of your screen real estate can help you out when multitasking or for just making your device feel bigger. One thing that is often overlooked when it comes to saving space on the screen is the keyboard.