Tagine is both the name of a cooking vessel and also the dish that is cooked within it. In fact, some might say tagines are the national dish of Morocco. These slow-cooked stews and braises, often combining meat, vegetables, spices, and dried fruits, have a character unlike anything I've ever eaten.

I love pomegranates. I don't even mind the mind-numbing task of picking out the arils (which is what those ruby-colored seed-like things in the pomegranate are called). However, I'm always on the lookout for new, easy ways to peel it that don't make my kitchen look like a crime scene.

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

I am an English major physically allergic to all algebraic formulas, so you're unlikely to get any help from me when it comes to solving any expressions. But in the glorious technological age we live in, there are plenty of apps that actually make math and problem solving fun, even a little bit addictive.

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

Only a handful of food products are impervious to spoilage—dried rice, salt, sugar—but even among those, honey is unique in that it remains edible without any preparation necessary. It's like this: if you came across honey in an Egyptian tomb, as archaeologists have, you could taste it and never guess it was thousands of years old.

Voicemails are like chores for me. I have to listen to them, but never really feel like doing it. When I finally do, most of them get deleted right away, but every so often they'll be one I save and listen to over and over again, whether it's a cute birthday wish from grandma or a hilarious joke from my friend.

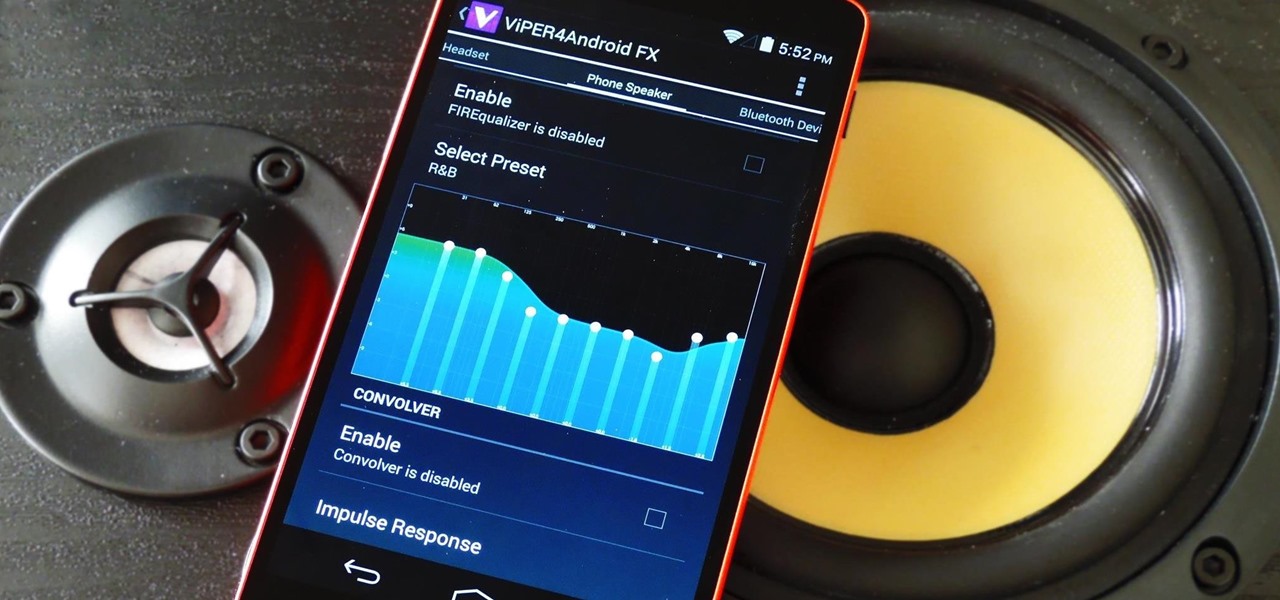
There's a never-ending selection of app launchers that want a permanent spot on your Android device. While some keep the stock-Android look with beefed-up versions of Google's launcher, Blur is relatively new on the scene, with a unique approach to app management that sets it apart.

When a Houston mom got tired of her kids seemingly refusing to return her calls, she decided that she'd take action. Sharon Standifird's vision was to create an app that would somehow force children to get into contact with their parents. Having no experience with app development, Standifird quickly taught herself the ropes and hired an experienced developer to help with coding.

If you're using iOS 10 or lower, there is no built-in way to record an iPad, iPhone, or iPod touch screen, and Apple doesn't allow any third-party apps to screen record either. If malicious, an app could theoretically continue recording even after you think it's off, allowing it to capture account and password information that you enter on your device. This changes in iOS 11, which introduces native screen recording, but what do you do if you're still running iOS 10 or lower?

Everything you thought you knew about cooking pasta is wrong. When I took cooking classes in Italy, they taught me to bring a large volume of salted water to a rolling boil, add a drop of olive oil so that the noodles wouldn't stick together, and wait several minutes until it was al dente (which literally means "to the tooth," i.e., firm and not mushy when bitten).

Welcome back, my apprentice hackers! In this series on password cracking, I have been attempting to develop your skills in the age-old art of password cracking. Although it might seem like a simple and straightforward exercise, those of you who have attempted password cracking know that there are many subtleties to this art.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

Welcome back, my greenhorn hackers! Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It enables us to crack multiple types of hashes, in multiple ways, very fast.

It seems like custom Google Now commands are a dime a dozen these days. With Commandr for Google Now giving non-rooted users their first taste of custom voice commands just a couple weeks ago, you may wonder why we're covering this subject again.

Update: After playing around with our new iPhone 6 and 6 Plus over the last couple weeks, it occurred to me to see if my DIY stylus would work with these new devices. I'm happy to report that it does, just as expected.

For some, there's nothing more thrilling than carrying an armful of bags while wandering the mall; for others, there's nothing more annoying. No matter what category of shopper you fit into, the truth is that you aren't always in control of what you buy.

Welcome back, my novice hackers! In a recent tutorial, I showed you how to use shikata_ga_nai to change the signature of a payload to evade detection by security devices (firewalls, IDS, etc.) and AV software.

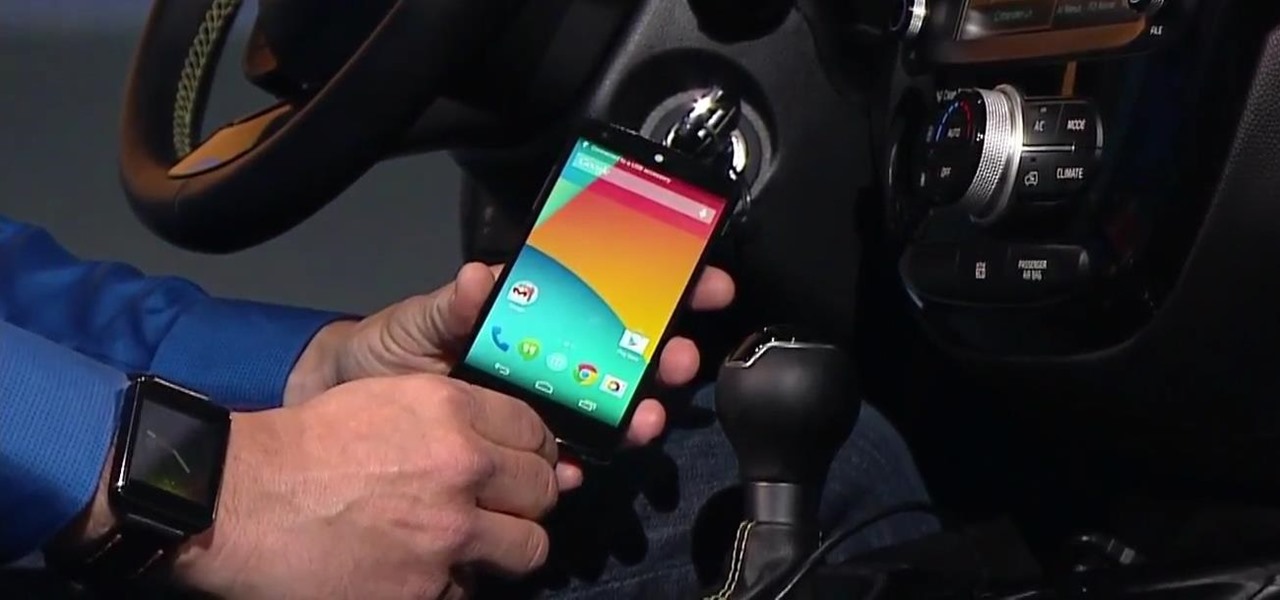
This year's I/O was all about bringing Android into the future and onto new devices. On top of announcing the upcoming "L" release of its mobile OS, Google showcased Android Wear, Android Auto, and Android TV.

The Nexus line of devices consistently offer the most bang for your buck. It's why many of us purchased a Nexus 5—at a $350 entry price, it's half the cost of any other phone with similar specs.

Apple just unveiled iOS 8 at the Worldwide Developer's Conference, and it has a lot of exciting features to play around with. Unfortunately, it won't be available to the public until this coming fall—but that doesn't mean you can't get it right now.

Have you ever fallen victim to a clever Jedi mind trick? Don't worry. It happens. There are evolutionary reasons as to why our brains sometimes give into the oldest tricks in the book. Fortunately, the more you understand the tricks of a salesman, the easier it is to avoid their gripping psychological influence. Clue #1: Too Much Specificity

I used a plastic water filter for years. Who wouldn't? It cuts down on buying bottled water, which, as it turns out, is pretty much the same as unfiltered tap water. Plus, bottled water is terrible for the environment and your wallet, too. Water that costs only pennies a day and actually was purified as opposed to just saying it was? That's a no-brainer.

Most people give their fruits and veggies a cursory rinse under the faucet before eating or cooking them, but is that few seconds under running water really enough to remove any remaining dirt, pesticides, or wax clinging to the surface?

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.

Garlic—it stinks so good! It's one of nature's most wondrous foods, being both delicious and incredibly healthy. What's not to love? Well, it is kind of a pain to prep, whether you're peeling a couple of cloves for a sauce or a whole head and trying to mince it finely. One way to get around the whole peeling and mincing issue every time you want garlic in a dish is by buying pre-made garlic-infused olive oil, except that stuff is pretty pricey. Learn to make it at home and you'll get all the ...

LastPass is a password manager that's been around for some time, and has finally made its way over to Android for use with apps, not just websites.

Let's be honest, most of us buy the bottom-shelf vodka either because we're broke or because we're going to disguise the gag-inducing taste of it with juice or something fizzy. If you're cooking or baking with vodka (ice-cold vodka works wonders in pie crust), what's the point of buying Belvedere?

A picture is worth a thousand words, and depending on what you're taking a picture of, it could be worth a lot more. Our phone's camera can easily capture high quality photos, scan barcodes, and make us Instagram famous. You can compare prices of items and download applications just by scanning a QR code. Of course, we can always do this stuff a little bit better on our iPhones.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

From personal photos and videos to online banking passwords saved in your web browser, your phone has all kinds of sensitive data that needs to be protected. One of the best things you can do for your Samsung Galaxy S4's data is have a lock screen with a hard-to-guess PIN or password.

Here's a routine that I'm sure all of us smartphone users go through at least several times a day. You notice your Samsung Galaxy S4's notification LED blinking, grab your phone to see what it is, and enter your PIN. Only instead of anything important, you find that it's just some online store enticing you with sales promotions, or some other email that you could have easily done without.

WhatsApp is one of the most well-known and most utilized cross-platform chat applications available today. It's free for one year, and only $0.99 a year after, which is chump change when you realize there are no hidden costs like international charges. Basically, it creates an easy to use forum for you and your friends to chat, regardless if they're an Android or iPhone user.

To steal a quote from Mean Girls, Halloween is the one night when a girl can dress like a total slut and no one can say anything about it—but why do girls get to have all the fun?

Former Vice President Dick Cheney was so fearful of attacks, he had his heart defibrillator re-calibrated to block incoming wireless signals so that highly skilled hackers couldn't send him into cardiac arrest.

I've never understood the phrase "smooth as a baby's bottom" to describe a really close shave. I mean, have you ever touched a baby's cheek? It's even smoother and a lot more sanitary. It just doesn't spew off the tongue as nice.

If you've got a birthday party to plan for a young budding scientist coming up, a little nitrogen should do the trick. In this project, I'll show you 10 "super cool" tricks with liquid nitrogen that you could try, but probably shouldn't!

If you're a Twitter user, it's a safe bet to assume that you've used a hashtag. On all social networking sites that have the capability, such as Instagram, Facebook, and Google+, the pound (#) symbol is used to mark and designate specific keywords or topics in order to make it effortless for users to connect with one another.