The fortunes of ARKit and ARCore are still in the hands of developers, who have been increasing the number of mobile augmented reality apps on the market, but perhaps not as fast as companies like Apple might have expected. But one new product is looking to literally kickstart mobile AR gaming by introducing a few key components that harness the traditional board game model.
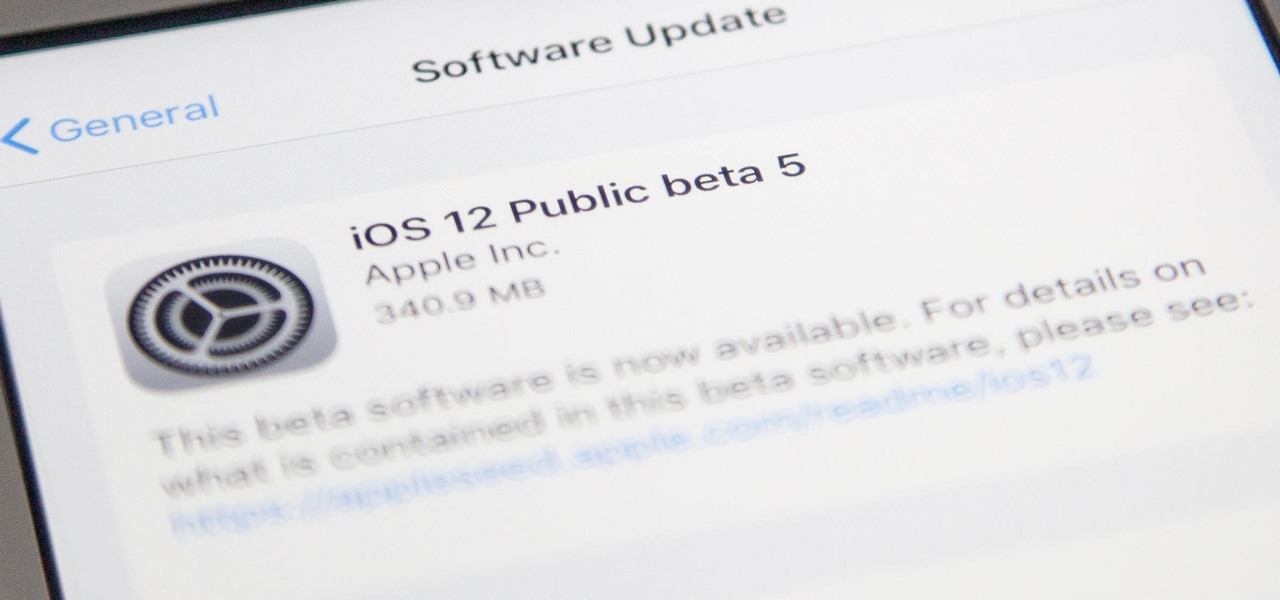
Well, that was unexpected. Apple released the fifth iteration of the iOS 12 public beta on Monday, August 6, just hours after iOS 12 developer beta 6. The company sometimes releases developer and public betas on the same date, sometimes even at the same time, but has not done so during iOS 12's beta period until now.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

When it comes to mass adoption, augmented reality is still primarily a mobile world, so Google is pitching its own ARCore flavor of mobile AR to the education and marketing segments.
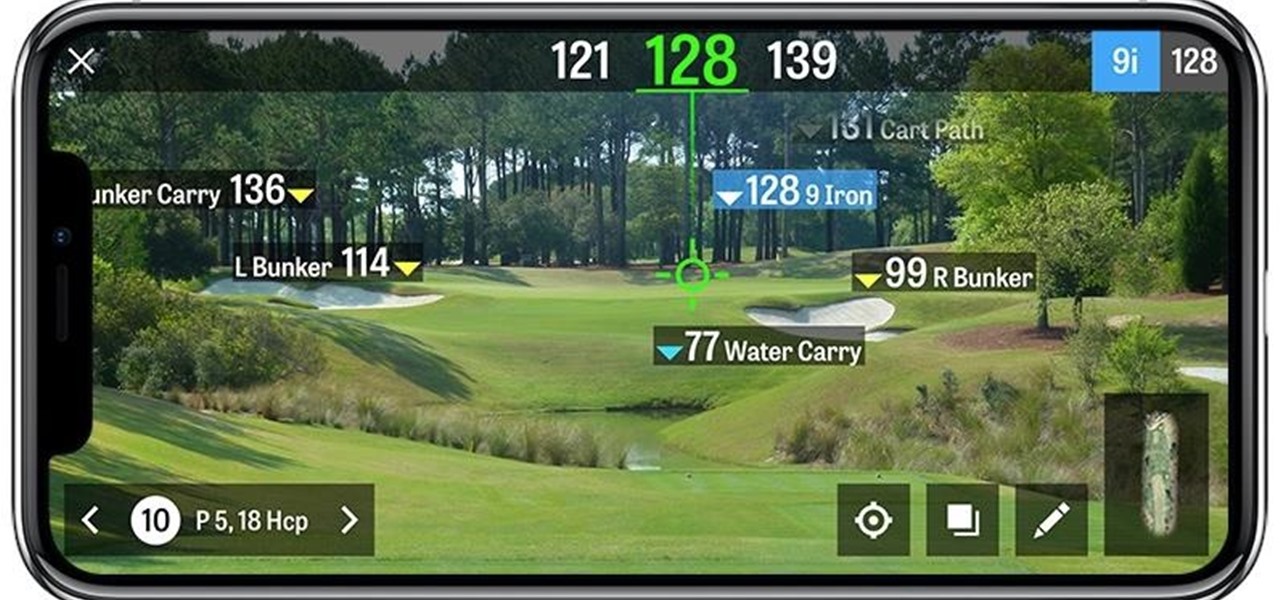
Although some look to golf for some quick off-the-grid time, the scenic hills and blue skies of your local putting green are not immune from the ever-expanding reach of augmented reality. A new update to the Golfshot mobile app brings new AR features to iPhones and iPads designed to help golfers determine shot distances during course play.

With all the talk about the impending release of the Magic Leap One, some have forgotten a very important, competing release on the near horizon: the HoloLens 2.0. Well, now we have new information that tells us when (roughly) the device will be released, as well as a few other exciting tidbits.

Usually, the camera adds 10 pounds, but with a new augmented reality effect in Like's mobile app, the camera can actually make you look slimmer.

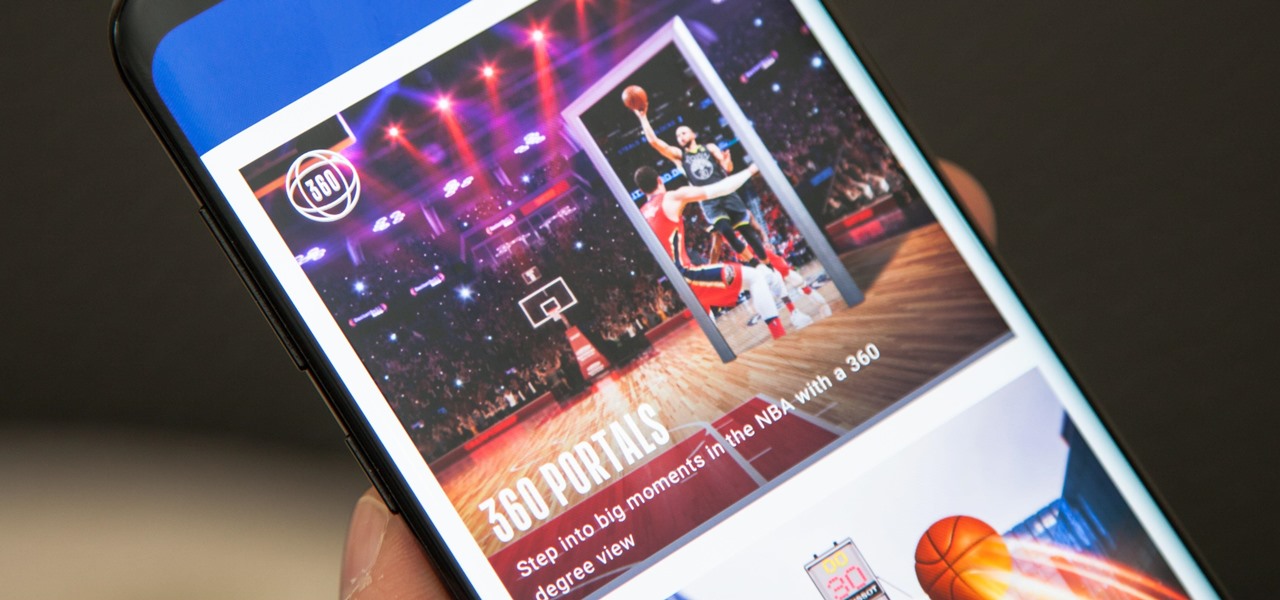
The NBA Finals is underway, and now basketball fans with iPhones and Android devices can get closer to the action for free than they ever could with expensive courtside tickets.

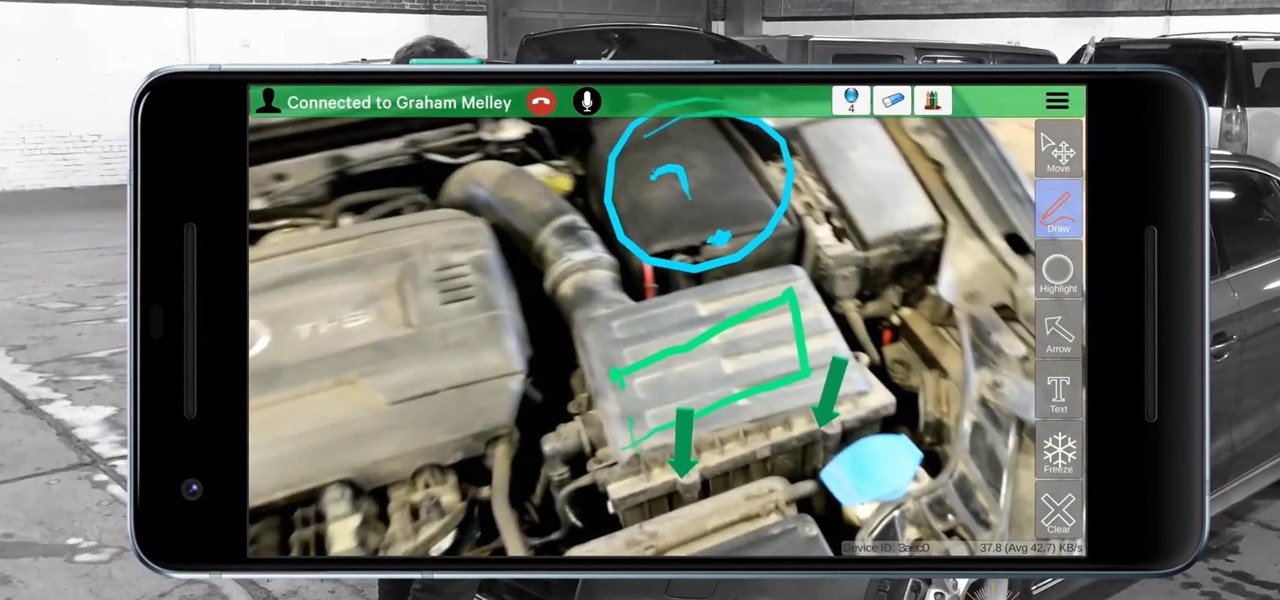
Germany-based Augmented reality software maker Re'flekt has added a new tool to its enterprise app development platform that makes it simpler to link AR content to physical objects.

Defcon is the largest hacker conference with something for everyone, whether it be the talks, parties, villages, or any of the hundreds of events. In this guide, we'll take a holistic view at everything that goes into attending the con for the first time, from securing your electronics and making the most of your time to the logistics of getting there and finding the right place to stay.

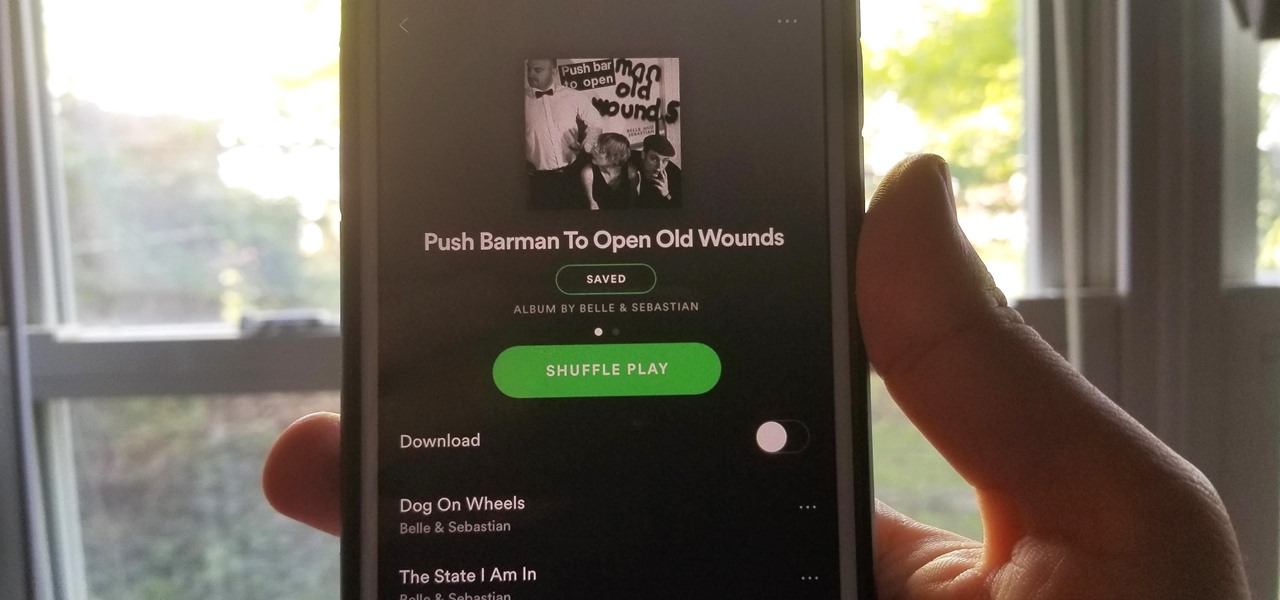
While I love Spotify, I don't like it devouring my data plan when streaming music away from a Wi-Fi network. If you have the foresight or time to download Spotify tracks for offline playback later, great. For those of you who like to listen to your music more randomly like I do, based on your current mood, streaming is the only way to go, and there are settings you can tweak to use up less data.

Microsoft's Monday keynote introduced the fourth generation of the company's Kinect sensor during Build 2018 in Seattle.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

Scope AR has decided to take its live remote assistance enterprise application, Remote AR, further into the mobile augmented reality realm by harnessing the powers of Google's recently released ARCore.

Just weeks after officially launching its mobile augmented reality toolkit, Google can now claim one of its first Android and ARCore app exclusives with the Curate app from Sotheby's International Realty.

The Galaxy S9 is now in the hands of millons of excited users. Getting a new phone is always fun, but it's important to think about protecting your device. Perhaps the most popular cases for the Galaxy S9 are the official OEM options from Samsung. There are a plethora of cases, whatever your preference and needs may be. Let's take a look at each case individually, along with the pros and cons.

What many thought was inevitable, based on recent hints, has been revealed to be in the planning stages: Snapchat is working on smartglasses. The surprising information came out on March 2 in a report that also claims Snap Inc. is planning to release version two of its Spectacles product in the third quarter of 2018.

Apple CEO Tim Cook's most recent tech prophecy is that "AR will change everything." And now, that includes Apple's own website.

Snapchat just fast-tracked the majority of its app user base into the world of augmented reality production by making its Lens and Filter tools available to anyone with a web browser.

After Vuzix's scorching hot week at CES, the future of AR is so bright, we have to wear (smart) shades. Luckily, Vuzix is making it easier for consumers to grab a pair.

While the mainstream consumer market waits for cool augmented glasses to arrive from Magic Leap, or maybe even Snap Inc. (Spectacles 2.0??), AR headset maker DAQRI and its business customers are finding new, money-saving and time-saving use cases for the technology today.

After hosting millions of free 3D models online, Sketchfab is betting that augmented reality and virtual reality developers and creators will be willing to pay for premium 3D content.

Shanghai-based Realmax is introducing the crowds at CES to the Realmax Qian, an augmented reality headset capable of a field of view (FoV) that topples anything available on the market today.

On Tuesday, original design manufacturer (ODM) Flex used the CES spotlight to help introduce a smartglasses reference design aimed at companies interested in bringing their own enterprise AR headsets to market.

The knee-jerk reactions to Magic Leap's long-awaited augmented reality device, the Magic Leap One: Creator Edition, range from pent-up joy to side-eyed skepticism. That's what happens when you launch the hype train several years before even delivering even a tiny peek at the product.

To promote Star Wars: The Last Jedi, Disney and Lucasfilm released virtual porgs into the wilds of Snapchat via a Sponsored Lens on Sunday.

Drama seems to follow red smartphones. The internet nearly blew a gasket when Apple released a red iPhone 7 with a white front, and now OnePlus is taking some heat. The new Lava Red 5T comes with black bezels, not repeating Apple's mistake, so why are people mad at the Shenzhen-based company? Because Lava Red is only available in China.

Just as the Transformers animated TV series of the '80s were basically half-hour commercials for toys, a new Transformers AR app for iOS similarly functions as a promotion for the latest installment in the film franchise.

After years of tantalizing drone video, and then brief glimpses from special guests sharing photos on social media, the Apple Park Visitor Center finally opened to the public on Friday, Nov. 17.

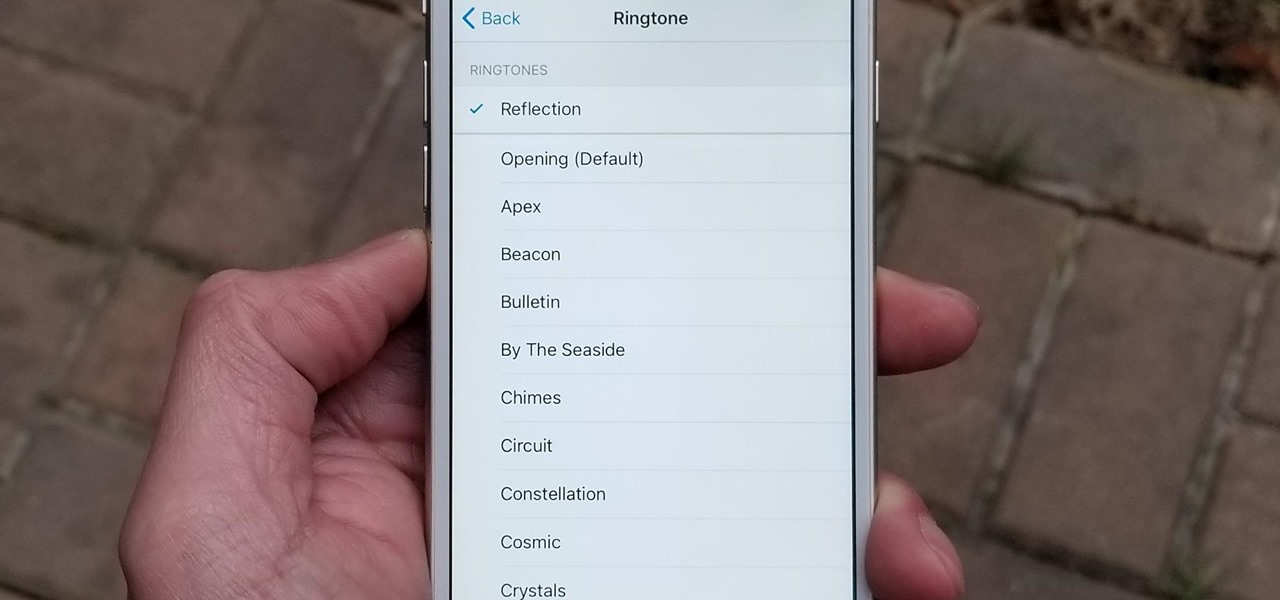
The new iPhone X sets itself apart from its predecessors not only as the first Apple smartphone to use an AMOLED screen, but also as the first iPhone to cost over $1,000. True to form as an exclusive device, Apple's latest flagship also features a distinct ringtone. With a little tinkering, however, you can make the new "Reflection" ringtone your very own, regardless of which iPhone you may have.

Just days after announcing the launch of two new mixed reality studio facilities, Microsoft is extending its mixed reality reach even further with the announcement that the HoloLens will now be offered in 29 new markets.

The Pixel 2 has a number of new unique features. One of the most interesting is the Now Playing option to identify songs you hear on a daily basis. Now Playing displays the artist and title of songs playing in the background of your day and shows this information on the lock screen. While this functionality is incredibly useful, the song history is not saved anywhere on your phone.

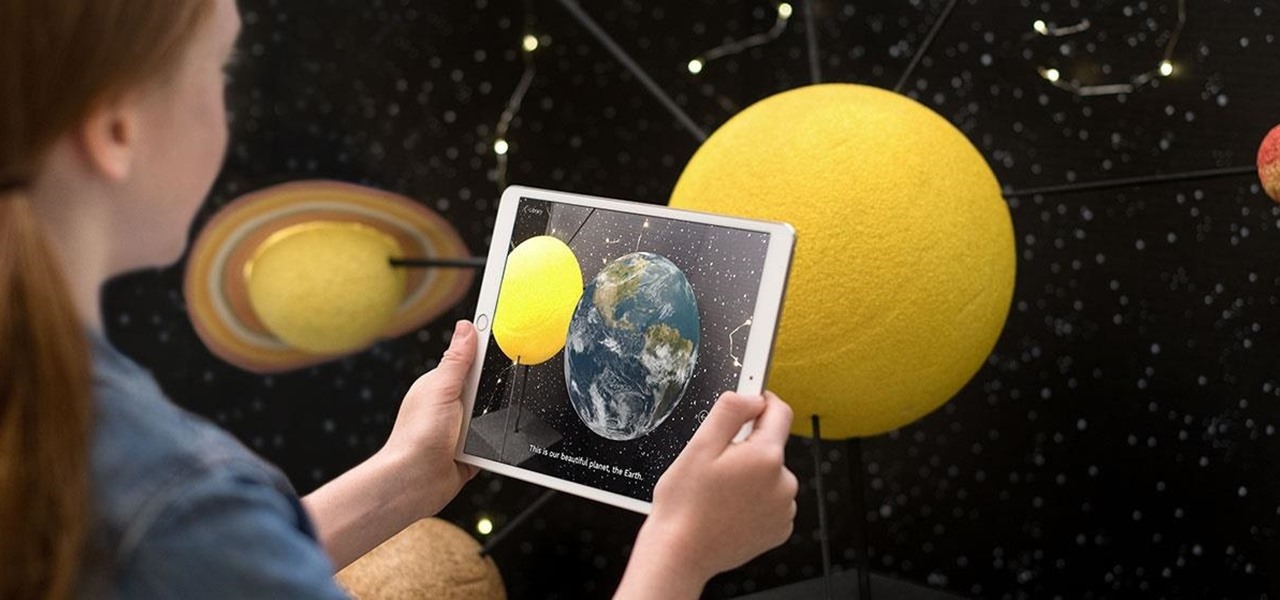
As interest in augmented and virtual reality continues to grow, so does the need to bring objects from the real world into virtual space. With that, there's also now an increased need for solutions that bypass the time-consuming process of producing handmade 3D models.

Augmented reality software maker Upskill has released the latest version of their Skylight platform, adding a number of new tools to ease implementation and improve functionality for enterprises, including a new application builder.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

Last week, I tried out StackAR, a puzzle app updated to support ARKit where the AR features felt mostly unnecessary.

Every other year, Apple comes out with "S" model iPhones that enhance and speed up their main series models from the previous year. This year, however, because of the highly-anticipated 10th anniversary iPhone, aka the iPhone X, Apple has dropped the "S" and moved straight to the iPhone 8 and 8 Plus.

The ride-sharing firm Lyft and Faraday Future, a troubled electric carmaker and potential Tesla competitor, have quietly appointed new top executives, but like the rest of the industry, they struggle to find talent for their driverless programs.

Drones are a fairly new craze to hit the nation. While they are accessible to the general population, good drones still typically cost a ton of money and despite all the fun they are, it's sometimes not worth it to actually buy one. If you're one of those people who would love to play around with drones — but don't want to have to buy one — Arcane Reality is developing the app for you thanks to Apple's ARKit.

Faraday Future's all-electric super sports car concept attracted a lot of attention at CES earlier this year, but now it is struggling to replace key driverless engineers and program directors who left the company amid its recent financial troubles.