Download Greenpois0n and firmware 4.1! You can download greenpois0n and firmware version 4.1 from JailbreakAndUnlock. If you didn't update to 4.1 you'll need to restore to 4.1 firmware. Don't update to firmware 4.1 if your iPhone is unlocked.

Having a website people can easily navigate is common sense. It can save taxpayer dollars & help your agency achieve its mission. Here's how to dramatically improve your website by focusing on your customers' needs & adopting some basic usability techniques.

There are many different types of countertops, but of all those available, post-form countertops are probably the quickest and easiest to install. Post-form countertops consist of a laminate surface that is glued to a particleboard base. Typically, the base is shaped so that there is a curved front edge and an integrated backsplash with either squared off or 45-degree angle ends available.

Are you interested in selling your products at the local Farmers Markets? Many small mom and pop food crafters get started selling their artisan breads, homemade cakes, cookies, pies, biscotti, candy, seasoning mixes or regional barbecue sauces direct to customers who visit local farmers markets and farm stands. What better way to start than with those visiting the local farmers market; a captive audience expecting a wide variety of seasonal fruits and veggies; along with specialty products t...

Last Friday's mission was to accomplish solving HackThisSite, Realistic 5, the fifth and last in my series of realistic hacking simulation missions. This time, telemarketers are invading people's privacy, and it was up to us to stop them! The job was to get root on the site and delete the contact database in order to return the right of privacy to its victims.

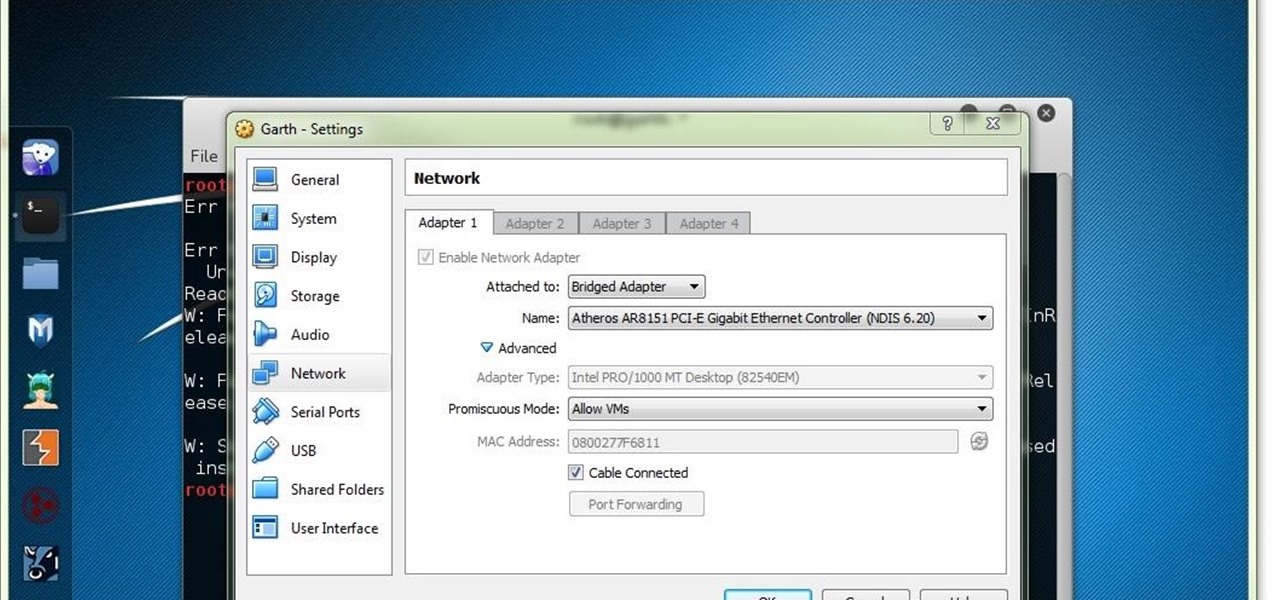
Many users of the virtualization software VirtualBox may have noticed that the USB system has been pretty buggy for quite a long time. I've had my USB randomly duck out on me way too many times to count. This can really be difficult to deal with when you require access to the devices and files from the host system.

What Is Hypoglycemia Hypoglycemia is the medical term used to describe a state of lower level of blood glucose. It produces different symptoms and effects resulting from inadequate supply of glucose to the brain and it leads to impairment of brain function.

You've seen the felt mouse, which made computer clicking comfortable and chic, now brace yourself for something a little more interactive—DataBot.

Homemade nourishing creams are easy and very simple to make. The ingredients are harmless and natural. It costs a fraction of what you would pay in the market. You also know exactly what goes into the product you make. Since homemade nourishing creams do not contains any preservatives, it's better to produce in small quantities and store it in the fridge to avoid waste.

I had so much fun planning my daughter's first birthday with a Candyland theme. Check out all of the beautiful decorations, party favors, cupcakes, and yummy treats. Have a look at all of the companies and people who contributed and helped make it so wonderful. who contributed to the birthday girls special day. Ellie Bellie contributed the adorable crown the birthday girl wore for the cake and “birthday” song, she truly was a princess. Sugar Mohawk contributed delicious treats for the party f...

What's harder than returning Nadal's serve, hitting a Clemens fastball or tossing a Manning bros. level touchdown pass?

Time to call up Guinness. Professors of Notre Dame University have supposedly invented the shortest possible game of Monopoly. Over in four turns (that's just nine rolls).
FrontierVille reminds me of FarmVille's land design, Treasure Isle's collectibles, Mafia Wars energy consumption all wrapped up with an Oregon Trail theme. I like very much that when I need energy, it's actually available to find or earn and that there's really very little to wait for. The 5 and 15 minute crops keep you coming back to harvest. The bonus meter keeps you clicking on things as quickly as you can. There's a bit of strategy involved with your space plan and game play. You can real...

Self-driving vehicles may be the apex of safe driving, taking human error out of the equation. Until then, augmented reality can help reduce accidents by improving driver awareness.
Recently, I decided to install Kali 2016 as dual boot on my laptop. Everything install perfectly up until the installer gave me the option to set up the package distribution mirror. No matter what setting I provided, no mirror would set up correctly. I was forced to continue the install without setting up the mirror. If you do not know what this means, I will explain it. Basically, you will not be able to update or install any tools onto your Kali distribution.

As you all know, the first Null Byte Technical Excellence Tutorial Contest ends this coming Monday, Feb. 15, 2016. If you are working on another great article or your first article, try to complete it and submit it before midnight Pacific Standard Time (PST) to be considered in this contest. The winner of this contest will not only receive a certificate verifying the technical excellence of their tutorial, but they will also receive a free copy of the Professional version of the Exploit Pack ...

Hello everyone. As many of you know, we've successfully launched the Null Byte Suite for our wonderful community. In addition to the prepackaged tools, there is a dedicated GitHub repository where tools submitted by the community will be pushed to for distribution in the suite. There have only been a couple submissions, and out of them, only one fit the requirements. So, out of anticipation, we've added it to the suite!

Hello y'all! I apologize if this question has been solved somewhere else, but I have looked around on Google, Yahoo, and Null Byte and have not been able to find any working solutions.

Almost everyone uploads their very personal photos in facebook trusting facebook's privacy settings. But question is - is facebook's privacy settings really that trustworthy? Few months ago, while browsing facebook, I found that one can easily access your private photos using the same browser you used to browse facebook.

I can't tell you how many times I've force-closed or restarted Chrome due to it freezing or loading pages incorrectly. And don't even get me started on that obnoxious "Aw, Snap!" error. I guess you could say I have a love-hate relationship with my most used browser.

In this how-to I will show you how to get Google Music in Canada (or any other country) without a VPN or Proxy. And it will only take 5 minutes

Over the last few months I have been getting more and more into computers over the last few months, and I discovered my new favorite thing to do..... notepad stuff!

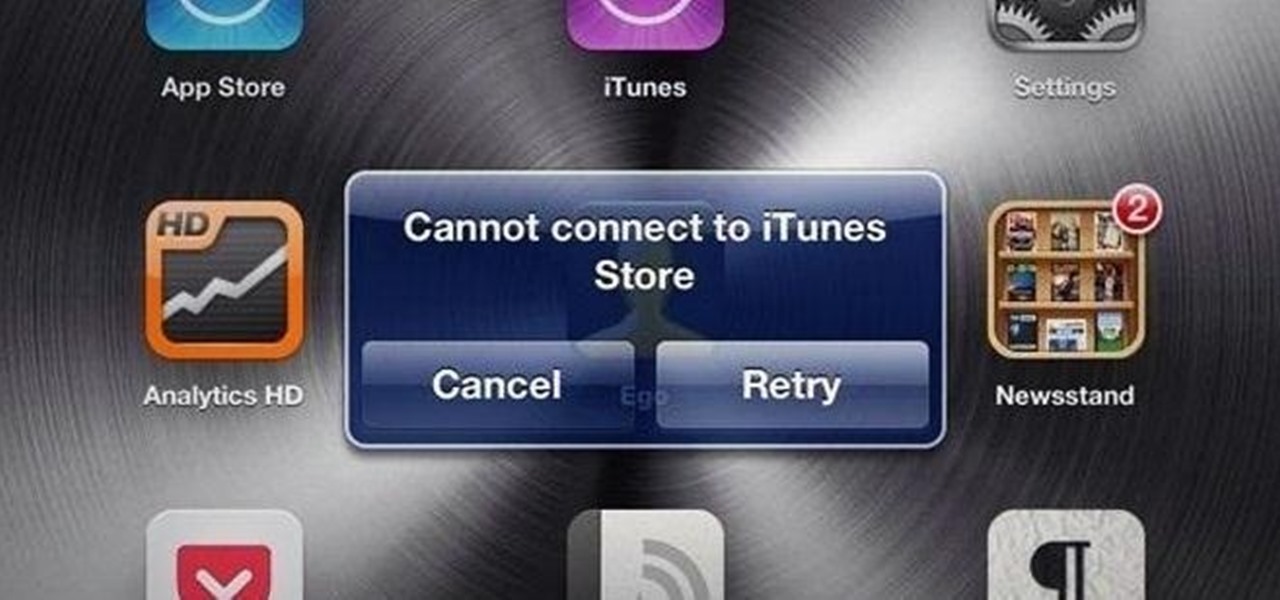
Since iOS 6 was officially released yesterday, several bugs have been reported, including issues with Wi-Fi, Passbook, and battery life (although Apple has apparently fixed the Wi-Fi bug). Some users are also having problems connecting to the iTunes Store, which is probably insanely frustrating because the first thing you want to do with a new OS is try out new apps. Luckily, there's a way to fix this by tweaking the date and time settings. Open Settings, then go to General >> Date and Time. ...

Introduction I will not go into some time-waster of a story about how I came to build this app. It was a prerequisite in a bigger project I am still tinkering with from time to time.

In Google definitions a macro is defined as "a single computer instruction that results in a series of instructions in machine language". Basically a macro is a programming script that tells the computer what to do. You can tell a computer (via a macro) to move a mouse, click, type or do any task that a computer can do with automation. There are also many (primitive) computer viruses that are coded entirely in a macro script. There are many ways to create a macro script but I will only go ove...

STANDP'S WINDOWS 7 "ASTON-2" CUSTOMIZED DESKTOP IT ROCKS COMPLETELY!. DEC

So, you're all excited you went ahead and 'upgraded' your iPhone 3G to IOS 4.0X so you could reap all the benefits of all the new features.

You know it's crazy out there when governments start blocking social websites like Facebook, Twitter and even YouTube. But that's what happened in Egypt, when tens of thousands of anti-government protesters took to the streets on Tuesday (January 25th) in hopes of ending President Hosni Mubarak's 30 years of authoritarian power.

Let's face it— most people don't understand Shakespeare's language. If they say they do, they're probably lying. The poetic words of the world's most famous playwright continue to plague school children and college lit. majors alike, but not anymore.

I write this post as an afterthought on the recent mass burnings of the Quran by U.S troops. Let me lay down the facts first to clear any misunderstandings:

Sometimes, paying for the whole Xbox LIVE service might seem like a waste of money. You're constantly experiencing lag, you've got people modding and cheating, kids are being loud and obnoxious over the mic, and your kill-to-death ratio is getting dumped on. Basically, the whole multiplayer experience just isn't cutting it anymore—you want to go back to the classic world of single player. Well, there's always downloadable content—simply known as DLC.

In this article, I'll show you how to create a simple yet accurate demonstration of the "rising ionized gas" principle. In other words, a transformer, two metal prongs and lots of evil laughter. Remember those large "towers" in the background of Frankenstein movies with a "lightning bolt" rising upwards every few seconds? That's called a Jacob's Ladder; one of the coolest awe-inspiring demonstrations of high voltage. Here's a video of the final product: Materials and Tools

Cell phone jammers, a DIY endeavor for the darker crowd. I'm pretty sure we've all considered having one at some point: whether the obnoxiously loud woman next to you is announcing private bedroom stories to a crowd on the subway, or your kids are grounded from using the phone (and consequently snagged a hidden prepaid phone), sometimes having a cell phone jammer comes in handy.

If you're on a tight budget for food, whether you're in college, or someone just starting out living on their own, you're probably low on money and sick of ramen noodles. Don't get me wrong, ramen can be tasty and filling, and there is almost nothing cheaper.

Your BIOS, or Basic Input Output System, is the firmware on your motherboard responsible for initializing your computer's hardware when it is first powered on. It probes for video adapters, RAM, the whole works. The BIOS provides a small library of basic input/output functions used to operate and control the peripherals such as the keyboard, text display functions and so forth, and these software library functions are callable by external software such as the OS and system software within sai...

Gamers like myself who have switched back and forth between Skyrim on PC and Xbox lack the ability to share game saves. This really sucks. I love playing Skyrim on a console. It's a very comfortable, easy and relaxed gaming experience. You don't have to worry about your frame rate being optimized, or wrist pains from using a keyboard. However, gaming on the PC can allow you to use texture enhancing mods and get an overall smoother experience due to a lack in glitches and bugs that plague the ...

Our mission for this week's Community Byte was to create a Python program to crack web-based passwords, like the ones you would see on an email or router login. I wanted it to be universal in the sense that it could be easily modified and adapted to another website just by changing a few variables. That was a success! Even though people weren't on time to the coding session, everything went well.

FEAZING 70 points (20 points without the bingo) Definition: fazing; disturbing the composure of [present participle of feaze]

Dead Island is known for having the most successful trailer of any game ever. It was a beautiful cinematic experience. But sadly, as details of the game itself emerged, and after it was shown at conventions around the world, doubt began to set in about whether this five-year-long project would live up to the hype.

This article describes the very basics of compiling a program on Linux. It is targeted at the absolute beginner. Sometimes beginners search for programs on the web for their Linux systems, and is faced with the reality that they have to compile the program themselves, either because there exists no binary for their architecture, or the author of the program just doesn't release any binaries at all, but only sources.