Hair products can work wonders, but the good stuff is usually super expensive. Plus, most of the major brands use a ton of ingredients you can't even pronounce, so it's safe to say a lot of us have no idea what we're putting in our hair. The good side is that most products can be made at home using basic ingredients for a fraction of the cost of commercial brands. Hairspray is no exception, and actually one of the easier ones to make.

Legal Services A group of lawyers refused to provide legal services to needy AARP members for $30 per hour, but when asked to do it for free, they readily agreed.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

A couple of months ago we showed you Foldify, an iOS app that allows you to create your own custom, foldable, 3D papercraft files. Your designs could then be sent to your printer, cut out, and assembled.

As our society and population grows, more developments such as housing and restaurants are built. While this is beneficial for us, it's not so great for the environment and the animals that occupy it. Some of the victims of our prosperity have been the birds, forced from their natural habitats.

Since the emergence of GoPro, the company's cameras have been been on a steady incline for the past several years. Adventure enthusiasts had difficulty recording their extreme activities without a huge price tag before the GoPro came along in 2002.

When most people think of stained glass, the first thing that comes to mind is a church, but it's become more popular in home decor as well. The biggest downside is that high quality stained glass pieces can be insanely expensive—and it's not an easy project to take on yourself.

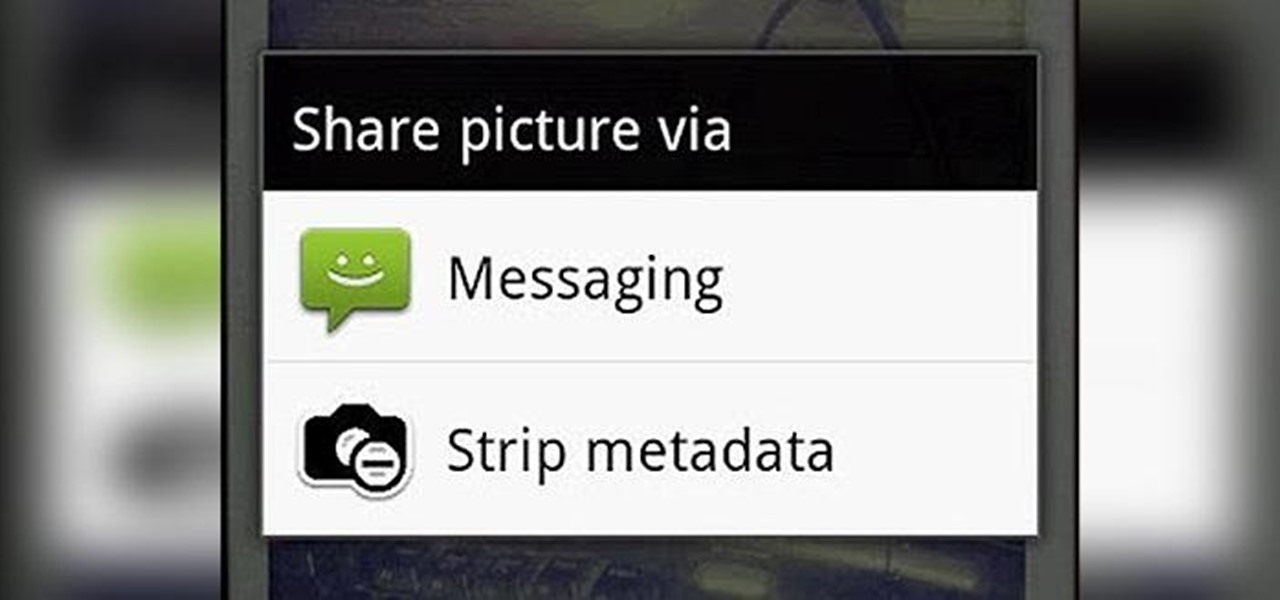
We've talked before about EXIF data—or metadata—attached to photos and how it can expose information about your location, what type of device you're using, and even the device or camera's unique identification number.

Unfortunately, there are plenty of situations where having a can of pepper spray could come in handy. Even worse, in most of those situations your state of mind isn't really conducive to remembering important details like the facial features of the person who's trying to mug you, which means the police will have a harder time catching the culprit.

Tons of people listen to music while going to sleep, but some don't like to leave it playing all night. If you hate waking up in the middle of the night and having to turn off your music, why not make your smartphone do it for you?

As someone who writes an extreme amount, it's a necessity for me to have an organized and multifunctional text editor. The stock iPhone Notes application is useful to an extent, but it sorely lacks in features and design. Writing and text editing applications are nothing new to the iPhone, but many of them are overloaded on features, making it even harder to keep organized. Here are just a few alternatives that I find helpful in my day-to-day writing.

LEGO has not attempted a blimp, zeppelin, or similar airship since 1999, the 5956 Expedition Balloon which used highly specialized parts. This is unfortunate as these vessels are well and truly part of the pulpy adventure and steampunk scene.

When it comes to the quality of a photo, lighting can make or break it. Too much light, and your subject looks washed out. Too little, and you can't even tell what your subject is.

These three videos will show you how to build a rustic, distressed kitchen table. I'll be walking you through the process of selecting some recycled timber from a junk pile, and with a little care and some simple joinery techniques, transform that waste timber into a distressed timber kitchen or dining table. In fact, you could use the table for whatever you wanted really.

Feelings can get hurt on Twitter as fast as an update. Everything is fine and dandy because two people are mutually following each other, then out of nowhere, one person has unfollowed the other out for seemingly no reason. Twitter doesn't notify users when someone has unfollowed them, so there are millions of people out there who get used for their follow! Well, now you can find out who unfollows you on Twitter with these mobile apps.

A faulty or broken thermostat can be one of the most annoying things to ever happen to your house. It's always too hot or too cold, and you can end up wasting money on your electricity bill.

Playing advanced games on your phone can be pretty frustrating sometimes. Touchscreen devices are great for everyday apps and games designed solely for them, but when it comes to games that require multiple actions in conjunction with directional movement, it gets ugly.

What do Justin Bieber, Kim Kardashian, Chris Brown, Rihanna, and Soulja Boy all have in common? They suck at Instagram.

Here's a way you can turn a mousetrap into a fun little handgun that shoots up to 40 feet! This is a great project because it can be made with simple materials, very basic tools, and in just a few minutes!

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

A few weeks ago, we saw a simple 128 inch DIY Projector Screen that looked like a pro built it—and it only cost $200. But this one is even cheaper, and looks just as good. It's also simpler because it's painted right onto the wall. In the video below, How To Lou shows us how to make it with just some white or silverscreen paint, a few pieces of casement molding, and some black velvet for the trim.

The worst part of moving into a new place is, well...moving. It's tedious, a lot of hard labor, and it can take forever, and don't even get me started on all those labels. It's also one of the only times in your life when everything you own can be stolen at once, since it's sitting in a movable container. Rather than risk losing everything, try this DIY Moving Truck Alarm System by Tim Flint that lets you know when the loading door is opened so you can catch would-be thieves red handed.

Christopher Nolan's Batman trilogy has been one of the most successful film series of all time, so it comes as no surprise that everyone wants their own real-life versions of the Dark Knight's gadgets and vehicles.

No one likes to think about the possibility of natural disasters, but we all know they could happen at any time. Some of us are a little more paranoid than others, but wouldn't it be nice to know that you'd be protected if anything really crazy ever happened? Like the zombie apocalypse?

As deeply as smartphones are integrated into our daily lives, it's no surprise that people are finding ways to use them to stay healthy. From detecting cancer and radiation to diagnosing STDs, phones have come a long way, baby.

Want an electric car without the price tag? You could always build your own, or maybe just hack your old gas guzzler into an eco-friendly electric machine... This weekend at Defcon, security consultant David Brown showed off his "Voltswagon" project, a 1974 Beetle named Shocky that he converted to electric for only $6,000. He removed the old combustion engine, radiator, and a few other unneeded parts to make it lighter. Then he loaded it with batteries front and back, ten Interstate DC-29, 12...

Stop me if you've heard this one before. A man walks into a bicycle shop, hears about a canoe made of cardboard and is inspired to make an awesome, fully-functional cardboard bicycle. Sound far-fetched? Wait until you hear how his guy actually did it. Israeli entrepreneur Izhar Gafni says that the idea for his method came from Japanese origami. Folding the cardboard increases its strength by 2-3 times, making the material much more durable. Essentially, he made the basic shape for each part w...

Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with friends and make purchases can also put you at risk. Photo by sam_churchill

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

So, your buddy's getting married and it's time for that age-old tradition the "bachelor party". Make sure the party goes off with out a hitch by remembering the goal is to have fun and not to ruin the wedding, get a DUI or destroy the reputation of your friends. Plan accordingly.

As a Boy Scout, when the First Class rank is attained, a scout has learned all the basic camping and outdoors skills of a scout. He can fend for himself in the wild, lead others on a hike or campout, set up a camp site, plan and properly prepare meals, and provide first aid for most situations he may encounter. A First Class scout is prepared.

With the list of available mobile apps for moviegoers constantly expanding and improving, seeing a film at your local theater has never been better. With the right apps for your iPhone or Android phone, you can research movies, find out if showings are sold out, reserve seats, save money on tickets and concessions, preorder popcorn and soda, and even find dull bathroom-worthy scenes.

The transcribing app can be an invaluable tool, especially if you're a student or are in a profession that relies on audio journals or interviews. These apps can convert important recordings like lectures and meetings into text for you to carefully read through to better comprehend.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Your best chance of getting to a destination on time during rush hour is to drive through relatively empty HOV lanes. Thankfully, if you're using Waze to navigate through traffic, you can easily locate HOV or HOT routes to optimize travel times by adding your toll passes in the app's settings.

Say you're on a train to work, but you forgot your headphones. You'd normally listen to music to pass the time, but given the circumstances, your choices are to sit silently like a considerate adult, or to blare songs out of your phone's main speaker like a jerk. Thankfully, there's now a third option.

Vodafone India has merged with telecom company Idea Cellular to become India's largest mobile player this week.

Sky Zhou, also know as Matrix Inception on YouTube, is no stranger here on NextReality. We loved his Pokémon concept game for HoloLens, as well as his D3D Keyboard that lets HoloLens users leave notes around the house. He just can't seem to stop creating cool mixed reality apps, and he's already got another one in the works.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Five Phases of Hacking:- The five phases of Hacking are as follow: