Termite poop and biofuels — what's the connection? New research into termites' intestinal comings and goings describes a process that may speed the development and lower the cost of fuels made from plant matter.

While the numbers may not always seem to agree, the message remains the same: augmented reality is a growth segment. This week's edition of Market Reality starts with two new reports outlining the expected good fortunes for the industry and concludes with an example of a company capitalizing on their own growth.

The battle of the budget phone is well and truly underway, as both T-Mobile and ZTE have launched affordable new devices simultaneously.

As much as you try to safeguard your personal information, you may have made a small mistake by giving your phone number to the wrong entity, and now you're being bombarded with dozens of spam calls every day. To help parse your call log and reject the proper numbers without answering or trudging through voicemail, a good reverse phone lookup app is needed.

Apple staff will be put through their paces now that the company's "Automated System" for driverless cars is in motion.

It seems nowadays there's no limit to what type of companies are looking to invest in augmented reality. Given both the positive outlook on the future of AR, and its reported benefits for efficiency in employees, this makes sense. Safran, an international corporation with three main sectors—aerospace, defense, and security—is one such company taking the plunge into incorporating AR in their business.

The squiggly guys in this article's cover image are Propionibacterium acnes. These bacteria live in low-oxygen conditions at the base of hair follicles all over your body. They mind their own business, eating cellular debris and sebum, the oily stuff secreted by sebaceous glands that help keep things moisturized. Everybody has P. acnes bacteria—which are commonly blamed for causing acne—but researchers took a bigger view and discovered P. acnes may also play a part in keeping your skin clear.

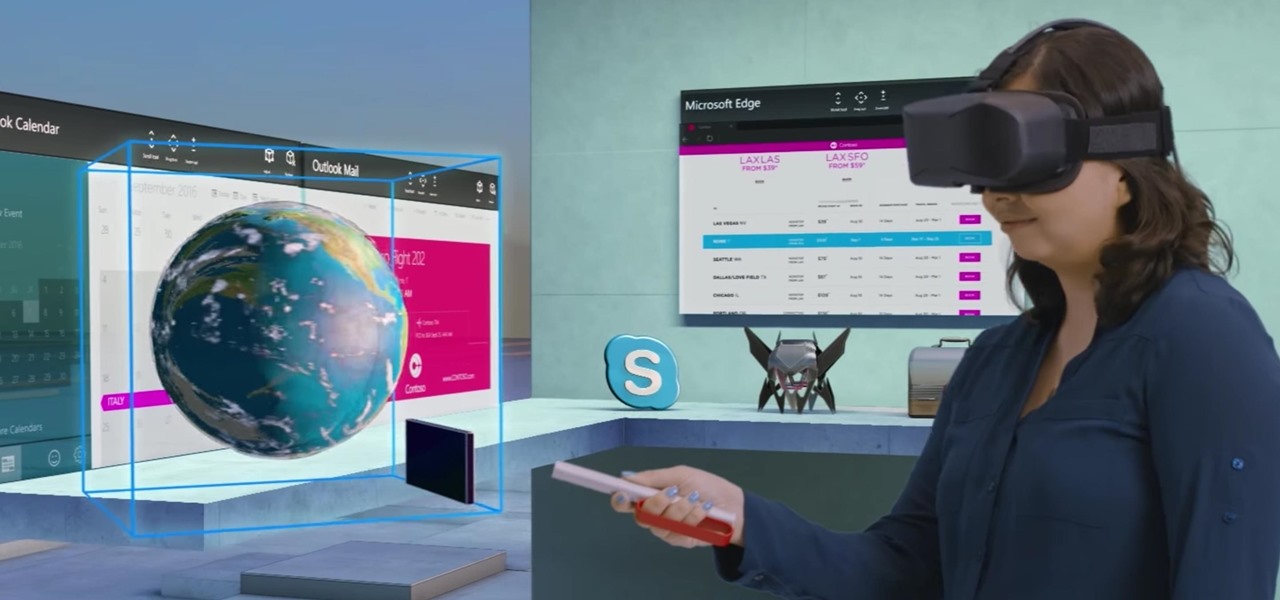
Soon, users will no longer need an expensive headset or even a smartphone to experience mixed reality. The new Microsoft update will be bringing mixed reality applications to every Windows computer next month. This new upgrade to Windows 10 named the Windows 10 Creators Update.

LOOOK, a Seattle-based mixed reality and development studio, can now peer into the future with their new geotechnical engineering visualization application for Microsoft HoloLens.

If you have stuck volume buttons, it can be a real pain to adjust sound levels since your only other option is to use the volume menu in Settings. But even if your volume rocker is working fine, it's still a little weird to have to click a mechanical button to control one of the most central aspects of an operating system that is otherwise entirely touch-based.

Late last year, two surgeons from the Instituto de Ortopedia e Traumatologia de Jaraguá do Sul in Brazil started using a combination of 3D printing and the Microsoft HoloLens to help plan spinal surgeries. And now, with the rest of their team, they've successfully performed a surgical procedure on their first international patient using their 3D impression planning and augmented reality process.

SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting for newbies to get down, and that's where Punchabunch comes in.

Transmitted by a sandfly one-third the size of a mosquito, parasitic Leishmania protozoa are responsible for a flesh-destroying disease that kills an estimated 20,000 people per year. Two new studies offer understanding of how the parasite provides immunity through persistence and why some people suffer more virulent forms of the disease.

Merge VR, a company mostly known for its virtual reality experiences, is moving into and creating an augmented reality experience that combines an iPhone or Android smartphone, a set of goggles to put your phone in, and a box about the size of a Rubik's Cube which looks more akin to the Lament Configuration seen in the Hellraiser film series. When used in concert with the smartphone and goggles, the toy cube, called Holo Cube, becomes one of many AR experiences.

YouTube is a great place for all your mainstream audio and video needs. But you can't simply plug in your headphones, choose a playlist, and put your phone back in your pocket without subscribing to YouTube Red, which costs $9.99/month for ad-free and background playback. If you can't afford that for just background playback, there are other ways.

When developing for the HoloLens, keeping a constant 60 fps (frames per second) while making things look beautiful is a challenge. Balancing the processing power to display complex models and keeping the frame rate where it needs is just a straight up painful process, but a solution seems to be on the horizon.

Pennies may only be worth $0.01, but if you want a coin with everyone's favorite donut-eating dad on it, you're going to need to shell out a little bit more.

A new contender has entered the mixed reality ring. San Fransisco-based Occipital has just released an "Explorer Edition" of Bridge—an iPhone-based mixed and virtual reality headset that uses their popular Structure Sensor. At a fraction of the cost of a HoloLens developers kit, this could be a place many curious people use to find their NextReality.

It's been little over a month since the official release of LG's latest flagship phone, the LG V20. Despite a few minor hiccups, the V20 has been attracting attention from all over for being an amazing phone. But like with most Android phones, there's no better feeling than rooting and taking complete ownership of it.

While Leap Motion and Microsoft are looking to capture natural human motion with cameras, Enflux figured out how to do it with a shirt and pants that feel completely natural.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

LG announced their latest high-end device on September 6 and its specs are pretty amazing: The new V20 sports three cameras, two displays, three microphones, four DACs for high-end sound, and it's all powered by a removable battery.

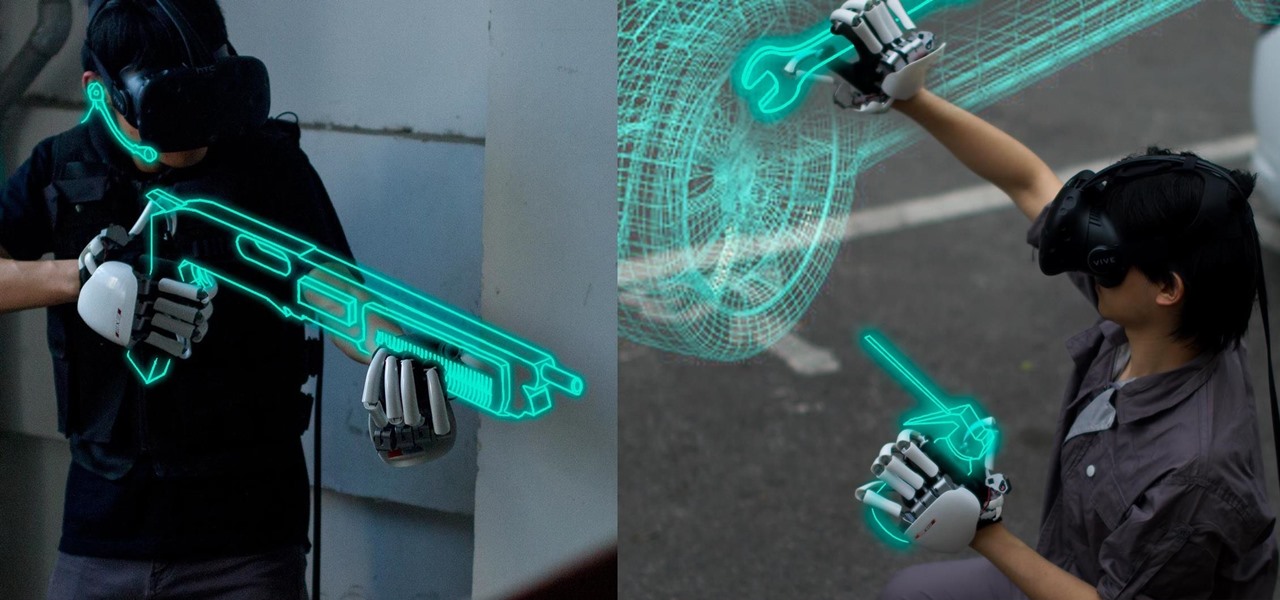
One of the disadvantages of the digital world is that you can't pick it up and touch it. While that can feel like less of a problem in virtual reality, where you're already holding controllers, mixed reality environments—like the one you'd experience in Microsoft's HoloLens—suffer from a lack of physical connection with the digital objects that appear in your real world. Dexmo aims to solve that problem with a relatively intimidating new controller that encompasses your hands.

Although professional sports has been no stranger to emerging technology, it still seems hard to think about how a football player might benefit from strapping on a VR headset. While it won't do much in an actual game, many athletes can improve by using virtual reality as a training tool.

We're inching closer towards the singularity—that point where technology advances to the steepest slope of the logistic function S-curve and simply skyrockets at a rate we've never seen before. Somewhere along the way, the line between humans and the tech we rely on will become blurred, and MIT's latest project might very well be a step in that direction.

Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact.

Mochi seems to be everywhere these days: as a topping at your local frozen yogurt shop, in ice cream balls (the green tea ones are heaven), and as colorful treats all over Instagram. It seems like mocha mania is in full force!

Pokémon GO made waves as the first augmented reality game to gain popular adoption. In fact, it was so popular that it only took a few days to uncover some the benefits and serious issues with combining physical and digital worlds.

How do you safely store your augmented, virtual, or mixed reality headset when you're not using it? Cybust hopes you're willing to shell out $89 to display it like a sculpture around your house.

Smartphones tend to struggle when it comes to recording video in low light situations. Danish phone manufacturer Lumigon included a good camera capable of shooting 4K video on its latest phone, The T3, but the real interest lies in the second camera, which is a dedicated night vision shooter.

We tend to think of Google Play as Android's app store—but there's far more to it than that. Not only does it allow you to purchase apps and games, but you can also buy movies, music, books, and even devices, plus there's always those pesky in-app purchases that it also handles.

Logan's Run is one of my favorite movies of all time. The dialog is cheesy, the set design and special effects are wonky, and the main villain looks like he was conceived and built by an eighth grader in shop class—oh, and his name is Box.

Six Flags is teaming up with Samsung to make riding a roller coaster a little more thrilling, and quite possibly a little more nauseating as well.

While it's been rumored for a few months, Apple finally unveiled its new 4-inch iPhone SE at the Apple Special Event on March 21st.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.

Most wood furniture is long-lasting, durable, and resistant to great wear and tear over the years. However, set a single sweaty, wet cup or bottle on the surface of your favorite wood dining table, or your prominently placed wooden coffee table, and you'll end up with a round water ring stain that is difficult to get rid of.

Three smart devices shown at CES 2016 are making it easier for you to make stupid decisions. PicoBrew, Somabar, and 10-Vins demonstrated their systems for beer, mixed cocktails, and wine, respectively, and each one is attempting to change the way we enjoy our favorite potent potables at home.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.