
How To: Separate Your Recycling
Recycling your garbage is noble and, in many places, mandatory. But it also can be very confusing. This guide will clear up the rules.


Recycling your garbage is noble and, in many places, mandatory. But it also can be very confusing. This guide will clear up the rules.

One you understand how a subnetwork works on an Internet Protocol (IP) network, creating one becomes very easy. In this five-part video, you'll learn about IP address and subnets, along with creating an IPv4 (IP version 4) address using Class C, which leaves each network with 256 local addresses. If you're new to subnetting, this is where you start!

You either love politics, or you don't, but office politics are entirely different than your local elections. It could mean respect, raises, or could even mean your job. Just staying out of it could stunt your career. Here’s how to jump in and get ahead – without getting burned.

Show the world just how resourceful you are next time you get a flat bike tire. With the help of some local plant life and some gusto you too can ride your bike to safety without the help of a standard repair kit.

With a little bit of planning, you can avoid a lot of blood-pressure-raising traffic messes. You Will Need

Get tips for picking fresh pineapples, tomatoes, mushrooms, meats, and much more at your local grocery store in this free video series from a gourmet chef.

This video series gives you expert knowledge on growing orchids and finding help in your local area. Bill Hutchinson talks with you about breeding and crossbreeding orchids, the importance of naming new orchids, and how to research your plants. He also gives you advice on taking the next step, how to connect with other orchid growers in your area and find support.

It's that time a year when winter storms begin causing havoc across the United States, and when "rotating outages" are common to help sustain the electrical grid during intense cold periods. That means pretty much anybody with snow and ice in their backyard can succumb to power outages. And no electricity means no electric heat.

Jerky is not only delicious but it is a great way to bring a protein rich energy snack with you anywhere. This video will how you how to make a great beef jerky at home. You will want a think slice of meat and you can create your own fantastic flavoring.

The video describes how to replace the fill valve, the rubber flapper, and an older plastic water fill line with a stainless steel one so that the toilet will no longer leak. Purchase a fill valve kit at your local hardware store before beginning. Start by turning water compression valve off, and then flushing the toilet to remove the water. Next, remove the fill valve by loosening the bottom, then top nut with a pair of pliers. Remove the plastic water fill line. Next, loosen the nut on the ...

Treasure may be buried as close as your own backyard. If you have some time to kill, try the art of treasure hunting. You’ll be sure to discover lots of interesting thing after learning how to use a metal detector to look for treasure.

It takes more than a kicky costume to become a professional wrestler. Start young to build up your basic wrestling skills and athleticism. To turn pro you’re going to need some acting flare, love for performing and a little luck.

Summer is almost here and you’re looking forward to that exotic vacation but you are going to need a passport and photos to go in it. There are a few simple ways to get a photo for your application. Find the method that is best for you and get traveling.

JB skating combines roller-skating with a variety of dance styles. If you’re board of your normal Friday nights or looking for a fun and funky way to exercise, grab a pair of skates, watch a few videos and then try it for yourself.

In this health video series, our experts are going to give you some techniques to use for pain relief that come from a branch of Chinese medicine called “acupressure.” Like acupuncture without needles, acupressure is a traditional therapy where one applies local pressure on the body at various strategic points.

Someday, maybe not today, maybe not tomorrow, but someday, you'll find yourself on the road in your car, maybe on the highway, and you'll hear something.

There's a quick way to see who you or somebody else has been chatting with the most in the Messages app for iOS and iPadOS. More specifically, it shows which conversations have the most attachments, such as photos and videos, giving you an idea of which chats are the most active visually.

Wireless charging is pretty much ubiquitous among modern iPhones and Android smartphones, but the technology has brought a lot of clutter with it.

The fight to wrest control of apps from Apple's revenue-focused grip just took a major turn in favor of Epic Games.

The enterprise-focused category of augmented reality doesn't often get the headlines due to its relatively sedate profile as a mostly factory floor and training-based tool.
When you're a writer with work published across various online platforms, building a portfolio of your work can be pretty time-consuming. That's where Authory comes in.
Learning a new language as an adult isn't just hard because your brain works differently from when you were a kid. You also have to contend with having less time and energy to practice. However, if you're looking to add another language to your repertoire at a pace you decide, then the Babbel Language Learning: Lifetime Subscription for All Languages: 2-Pack will be a useful tool for you.

Keeping your home clean is an endless battle with time, motivation, and the easy availability of cleaning supplies. That's where the Hard Surface Floor Cleaning Robot Vacuum comes in. This magical device will save you time by automatically keeping your floors clean, never requires motivation, and doesn't require additional supplies beyond occasionally emptying the dust bin.

Your sensitive personal data should be strongly protected, and it's never more vulnerable than when you are online. The internet connection is a prime avenue of exposure, and email is one of the least secure forms of communication. Fortunately, there is an easy solution to both of those problems.
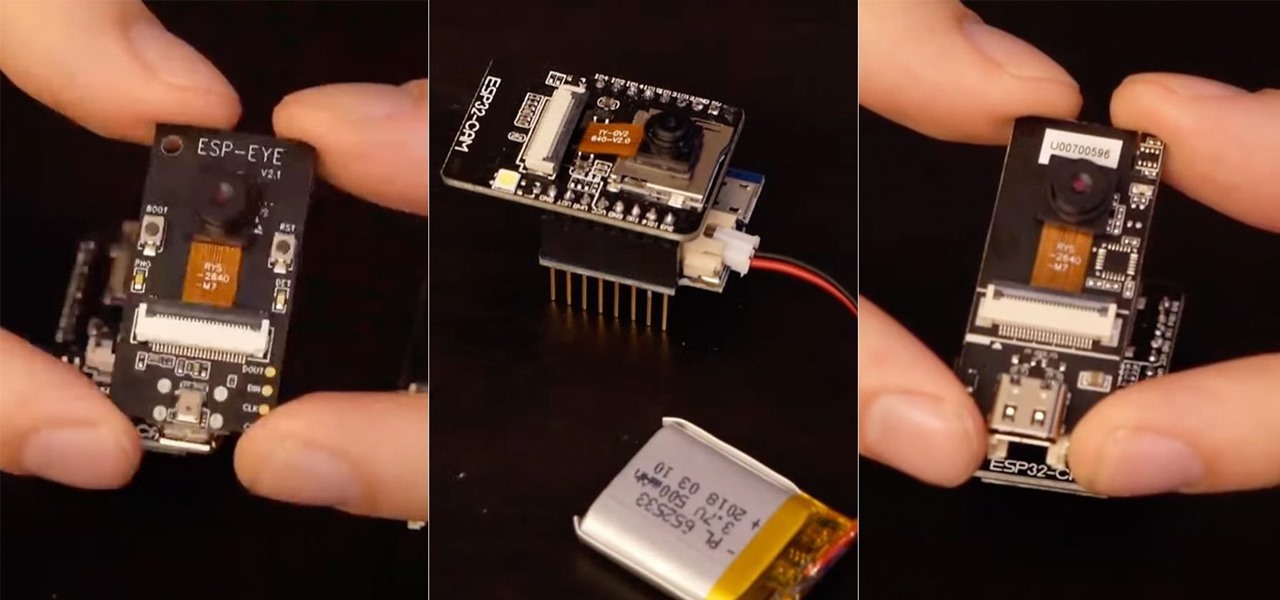
An ESP32-based microcontroller with a camera is an amazing platform for video, but not all modules are created equal. We'll go over the pros and cons of some of the popular low-cost camera modules you can use with ESP32-based development boards, as well as what features they support.

Now that 3D display maker Looking Glass Factory is closing in on $2.2 million raised in its crowdfunding campaign for the consumer-grade Looking Glass Portrait device, the company now has a 3D content generator to go with it.

Finding an instrumental or karaoke version of a song can be pretty easy unless you're dealing with a song that isn't popular. That leaves you with just the full version of the song, complete with vocals. So how do you convert it into an instrumental or karaoke track?

Wherever life takes you, knowing how to successfully manage both large-scale projects and teams will undoubtedly serve you well. Whether you're eyeing a promotion at work or looking to switch to an entirely different field, having the skills to innovate products, inspire people, and solve problems will make you stand out to your current and future employers.

With so many competing outlets to reach people, accessing inboxes remains one of the most effective forms of communication. Yet newsletter creators run into a constant problem: bounced emails.

While sheltering at home orders are lifting, companies are still conducting most business online. Case in point, hackers have been having a field day over the last few months. Securing your identity has always been important, but never as much as it is at this moment.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.
The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

With thousands of people across the country protesting, you might be thinking about joining the march. But as is too often the case, law enforcement has been called to oversee the protests, and interactions aren't always peaceful or lawful.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

A modern iPhone is capable of running sophisticated, exquisitely-rendered games that rival titles on current-generation consoles. However, there is some value in classic video game titles, whether you grew up playing games on the Atari 2600, Nintendo Entertainment System, and Sega Genesis or not.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.