
News: The HoloLens Might Have a Small Field of View, but That's Actually a Good Thing
Microsoft's HoloLens is certainly a leap into the future of mixed reality interfaces, but it's not without drawbacks.


Microsoft's HoloLens is certainly a leap into the future of mixed reality interfaces, but it's not without drawbacks.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

When you place your iPhone over a card reader for Apple Pay, it'll always pull up your default card. That might work fine for you, but perhaps that isn't the card you want to use. The problem is, you don't have time to switch cards before the payment goes through. That might result in using your rewardless debit card to buy groceries when you could've snagged 2% back by using your Apple Card.

For all that money spent on a new Watch, Apple could've given us more than just a charger and its case. I mean, the case is nice and all, but what realistic use is there for it? In all honesty, it'll probably find its way onto a shelf high above in the closet—but it doesn't have to.
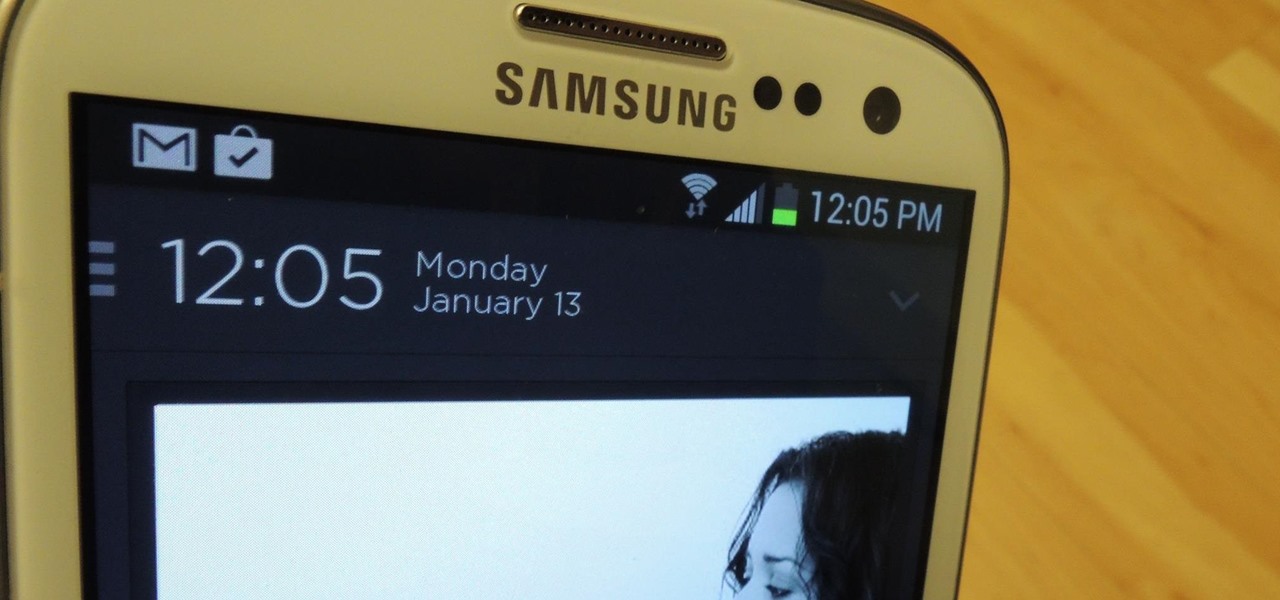
The sensors in your mobile device are integral for gaming (try to beat my Temple Run 2 score), as well as many of the basic Galaxy S3 features like Smart Stay and other fancy additions. But sometimes those sensors can become overly sensitive or just downright unusable.
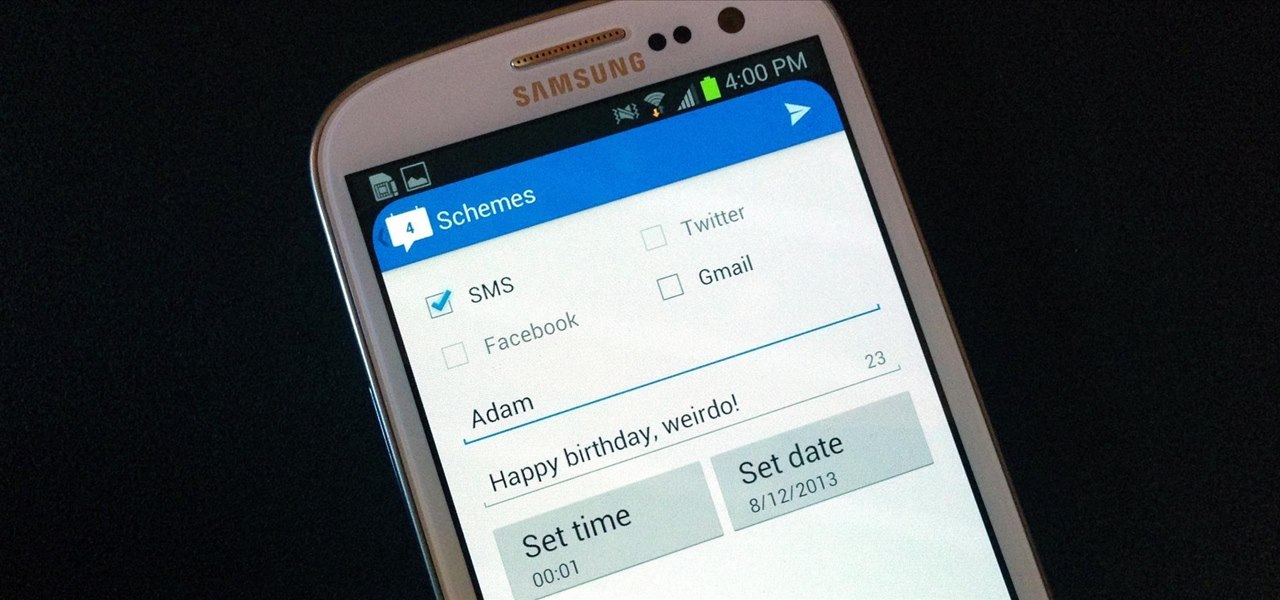
I'm sorry your mom hates you now, but it's pretty hard to forgive someone who forgets to say "Happy Mother's Day." Your poor ole ma could've spent anywhere from 10 to 20 hours popping you out, so the least you could do is set aside two minutes every year to say thanks. If you live to be 90 years old, that's only 3 hours over your entire lifetime!

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

It's finally that time. Stranger Things 2 dropped today, just days before Halloween. And to get you in the mood, Snapchat has quietly launched a spooky new filter that lets you immerse yourself in the world depicted in the hit Netflix series.

NBA star Andre Iguodala, of the Golden State Warriors, got to try out a Magic Leap demo in Florida and started dishing out some pretty revealing details about the upcoming mixed reality headset to CNET's Brian Tong.

The shooting of Walter Scott (who was unarmed) has been dominating the news these past few weeks. Scott, who ran away from police officer Michael Slager after a routine traffic stop, was shot in the back and pronounced dead shortly thereafter. Unlike similar cases where a cop shoots an unarmed person, the police officer involved in this particular shooting is currently in jail, facing a potential murder charge.
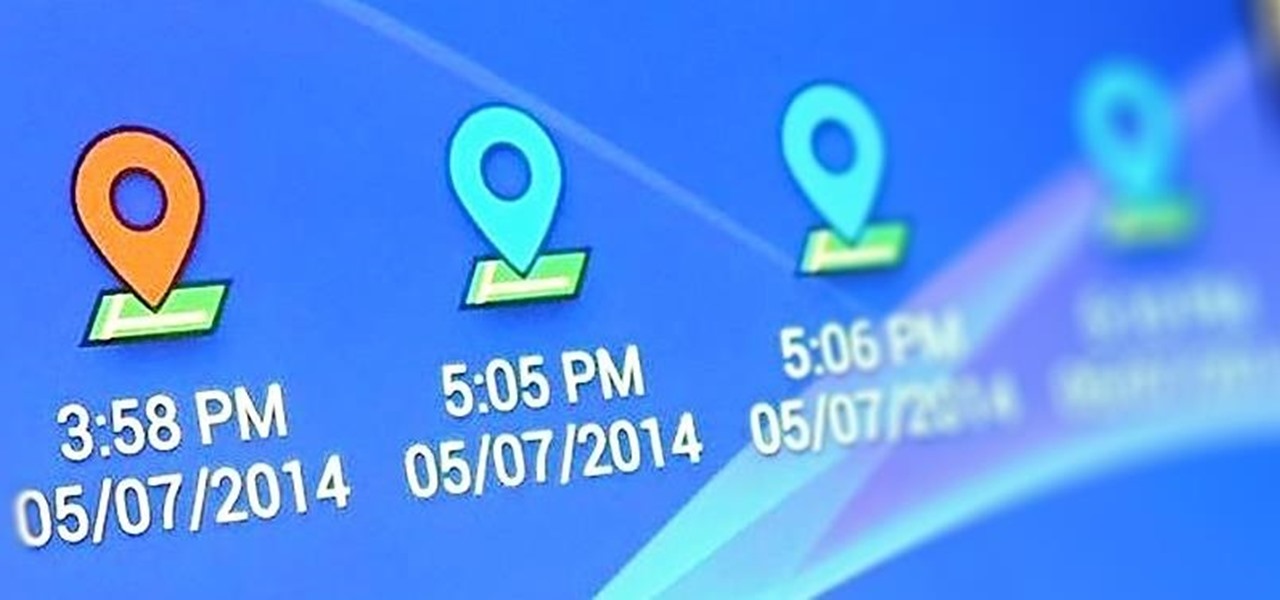
I passed a cool looking bar the other day that I wanted to check out. When the weekend came around, I was ready to go, but for the life of me couldn't remember where it was. Not wanting to retrace my steps or drive around aimlessly, I gave up.

You know that feeling when your cell phone gets stolen and you figure it is pretty much lost forever. You could've used one of the millions of device managers and trackers, but ya didn't. And the Good Samaritan is not coming to your rescue.

There are so many things in life I wish I could've canceled without any repercussions, and I'm mostly talking about text messages.

Advancements to Android's open source OS come in the form of ROMs and mods, available all over the web for anyone to find. Installing any of these modifications tends to wipe your phone clean, causing you to lose all of the precious data on your device.

It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.

You may have noticed improved photo quality in the Android Snapchat app in recent months. Believe it or not, this is because Snapchat only just recently started using a decade-old camera API that predates every Android phone in existence.

Plastic wrap is, arguably, man's greatest invention—or at least, the 2000 Year Old Man thought so. Its primary use is to protect food from getting dried out in the fridge or on the counter; but if that's all you're only using it for, you're missing out.

If you struggle with deciding which wine you should buy for an intimate dinner, or the type of beer with the highest alcohol content that doesn't taste like tree bark, then check out some of these great alcohol-friendly apps to make better booze decisions.
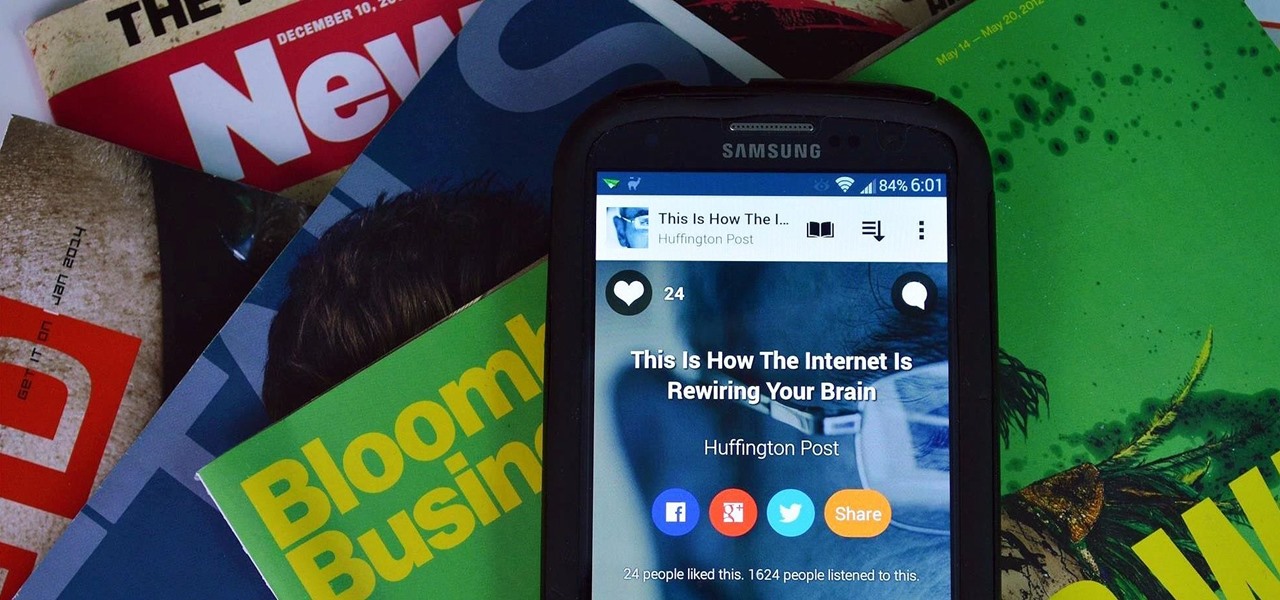
Keeping up with current events is a good step towards becoming a well-informed person, but sometimes it's a chore. In-between work, school, commuting, social lives, and hobbies, it can be extremely hard to find time to pick up a newspaper or browse CNN to find out what's going on in the world.

The great thing about competition is it drives innovation. But when a company tries to one-up its competitor, it's not always with something brand new. Sometimes, one party will draw heavy inspiration from the other — but hey, it's still all good, because the consumers benefit either way.

Nintendo set the internet ablaze Wednesday night with two big announcements. First, Nintendo revealed that the Switch's paid online service will begin in September (boo), but it was the other report that really got fans excited — Mario Kart is coming to your iPhone.

Google just bought a huge chunk of HTC for $1.1 billion. They're bringing in around 2,000 employees, mostly from the hardware division, and these folks will presumably work under hardware chief Rick Osterloh. There's a massive patent portfolio involved, too, so stop me if you've heard this before — Motorola, anyone?

Fast food is a guilty pleasure in which we all indulge. When you're short on time and long on hunger, being able to whiz through the drive-thru or run 'in and out' of a fast food joint can be a real lifesaver.

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

What's your top pet peeve? Open-mouthed chewing? Nail biting and knuckle cracking? The sound of silverware scraping? Or perhaps it's a bigger behavior, like leaving the toilet seat up?

I may be in the minority when I say this, but I love leftovers. Whenever I'm cooking for less people than the recipe calls for, I cook the full yield anyway. And when I go to a restaurant, I order whatever I want—regardless of how much I can actually eat in one sitting.
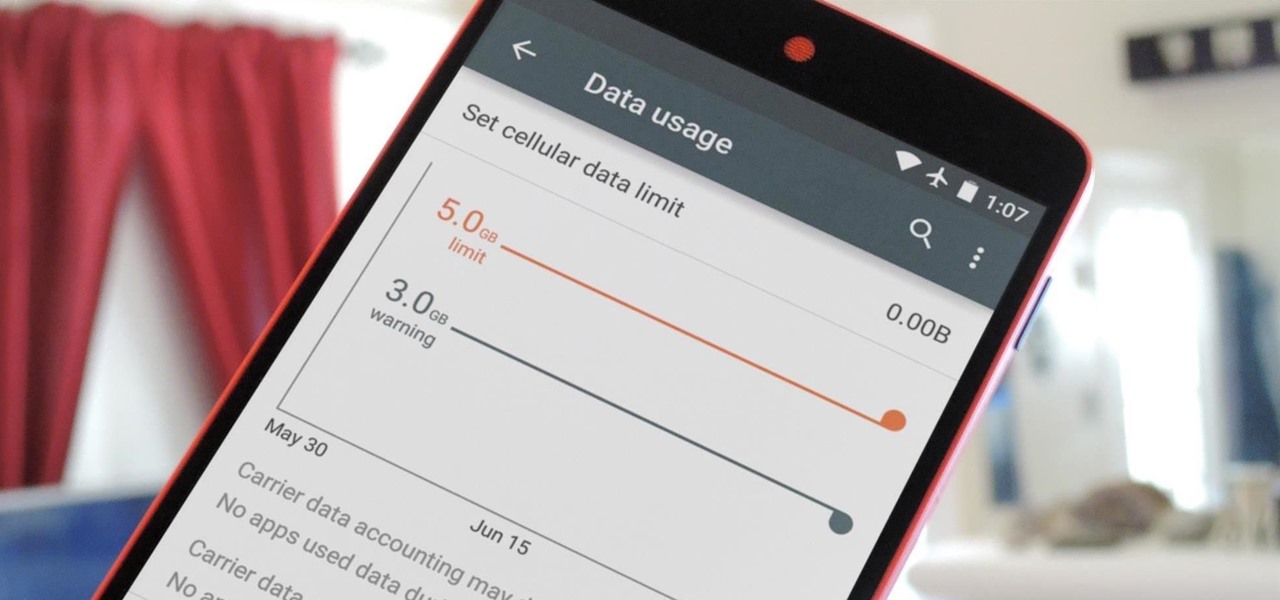
Ever watched Netflix on your phone only to realize an hour later that you forgot to turn Wi-Fi on? That's a whole lot of data used.

Your waffle maker might just be the most underutilized tool in your kitchen. This one appliance can make bacon, eggs, hash browns, cupcakes, falafel, mac and cheese, and cinnamon rolls much more quickly and with less mess than traditional methods. Plus, the results all come out waffle-shaped—what's not to love?

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

PUBG is currently taking the mobile world by storm, and it's easy to see why. The game has breathed much-needed life to the multiplayer shooting genre, primarily by adding an element of sheer terror as you scavenge for weapons in a hostile environment. With new players continually joining in on the fun, many players are looking for ways to gain an edge.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

Even the most seasoned cook is always looking for ways to make cooking easier and cleaning up after meal prep a breeze. There are a million and one tricks and tips out there to simplify your kitchen routines, but some of them are more valuable than others.

I have a personal rule when it comes to an app's interface: If it doesn't follow Android's design guidelines, it was probably written with Apple's iOS in mind first and foremost.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

One of the only things I remember from watching Nickelodeon as a kid is the epic green slime. Looking back, I don't know what was so great about it, but every kid my age thought that being drenched in slime would be the coolest thing on earth.

In this Null Byte, we are going to be installing Packet Injection capable drivers in Linux. These are the open-source drivers required to sniff wireless traffic, inject packets to crack a wireless access point, and go into "monitor-mode". These drivers are superior because they are the fastest available drivers.

Del The Funky Homosapien ft. Khaos Unique "Proto Culture" Chorus:] Let me tell you about the Proto Culture

I can't tell you how many times I've force-closed or restarted Chrome due to it freezing or loading pages incorrectly. And don't even get me started on that obnoxious "Aw, Snap!" error. I guess you could say I have a love-hate relationship with my most used browser.